#c2servers نتائج البحث
During the op—#HKPF analysed ≈3 million pieces of intel about: 👾#C2servers 🤖#BotNets 🎣#phishing websites which led to the discovery of: 🚨170K+ serious Internet safety loopholes ⚠️≈40K #CyberThreats in HK We then demanded remedial action from 80 Internet service providers.

New Blog Post! 🚨 hunt.io/blog/tracking-… We’ve tracked #PyramidC2, an open-source post-exploitation tool now being used to establish stealthy #C2servers. Read more about what we found in our latest blog post. #CyberSecurity #ThreatIntel
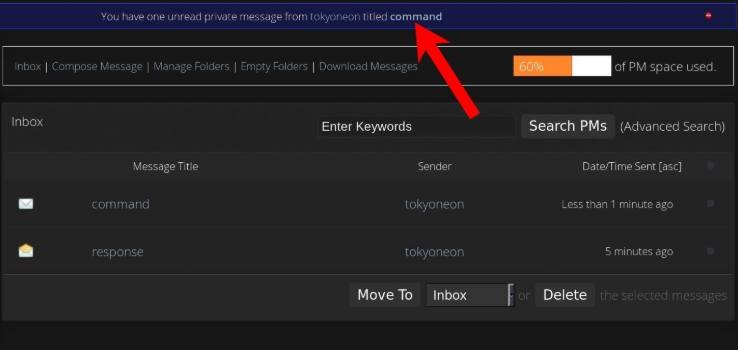
#CyberAttacks: Turn #Forums into #C2Servers To Control #MacBooks - bit.ly/3ds01rl-Ttx @tokyoneon_ via @NullByte 🔁 #Enterprises #Organizations #macOS #MyBBForum #CyberRisks #WebSites #InfoSec #CyberThreats #CyberSecurity #CommandAndControl #ITsecurity #CyberDefense
Understanding #C2servers is crucial in #cybersecurity as they are the central hub for threat actors, enabling them to steal data, control compromised systems, and spread malware across devices. Stay informed to fight against #cyberattacks with Hunt! hunt.io/glossary/c2-fr…
Let's Learn: In-Depth Reversing of Qakbot "qbot" Banker Part 1 #C2servers #Yara vkremez.com/2018/07/lets-l…
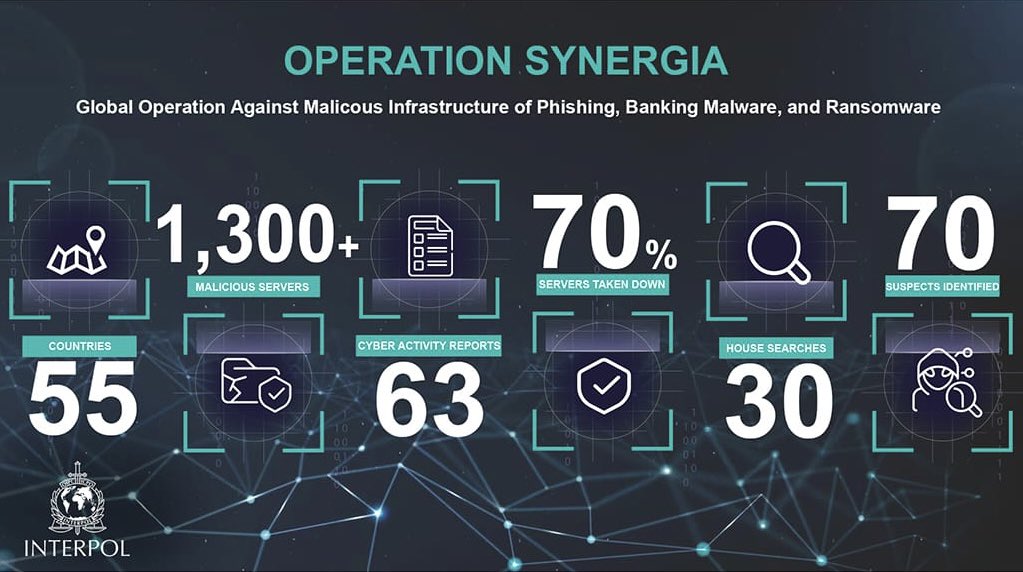
🌏Joint effort to restore #CyberHygiene SEP-NOV 2023: #HKPF successfully removed all the 153 #C2servers identified locally—the greatest raid among the 55 members countries/regions that took down a total of 900+ such malicious servers during @INTERPOL_Cyber’s Operation Synergia🌐
#C2Tracker Live Feed Of #C2Servers, Tools, And Botnets kitploit.com/2024/04/c2-tra…
🔐 #C2Servers: Attackers use custom GPT models to generate command and control (C2) server scripts, enabling remote control of compromised systems. Our proactive #threatintelligence helps detect and mitigate such threats, protecting your organization from unauthorized access.
A bug in #Mirai code allows crashing #C2servers pos.li/2bxh50
VenomRAT zloupotrebljava VHD datoteke sajberinfo.com/2025/03/31/ven… #c2servers #emailbaiting #hvnc #maliciousattachments #malwareattack #pastebincom #phishingemails #powershellabuse #ratmalware #remoteaccesstrojan #venomrat #vhdexploit
sajberinfo.com
VenomRAT zloupotrebljava VHD datoteke - Sajber Info Security
VenomRAT zloupotrebljava slike virtuelnog diska (eng. virtual hard disk image – VHD), pokazuje istraživanje sigurnosnih istraživača kompanije Forcepoint
Android bankarski trojanac TgToxic ažuriran sajberinfo.com/2025/03/19/and… #bankingtrojan #c2servers #domaingenerationalgorithm #emulatordetection #genymotion #malwareevolution #mobilesecurity #phishingcampaigns #qemu #tgtoxic #threatactoradaptation
sajberinfo.com
Android bankarski trojanac TgToxic ažuriran - Sajber Info Security
Android bankarski trojanac TgToxic pretrpio je značajna poboljšanja svoje zlonamjerne funkcionalnosti. Detaljna analiza sigurnosnih istraživača kompanije
• #Malicious communications or network traffic may be taking place. These include: • Known patterns of #exploitkits • Connections to (known) #C2servers • Unusual #networktraffic or web browsing activity • #Emails with links to #suspicious or malicious websites
I just published Intro to Command and Control (C2) Servers: How Attackers Maintain Access medium.com/p/intro-to-com… #EthicalHacking #CyberSecurity #C2servers
#Emotet using #CobaltStrikebeacons to communicate with #C2servers through a fake 'jquery-3.3.1.min.js' file. When CS communicates with C2, it will attempt to download the #jQuery file, which will have a variable changed with new instructions each time. bleepingcomputer.com/news/security/…
VenomRAT zloupotrebljava VHD datoteke sajberinfo.com/2025/03/31/ven… #c2servers #emailbaiting #hvnc #maliciousattachments #malwareattack #pastebincom #phishingemails #powershellabuse #ratmalware #remoteaccesstrojan #venomrat #vhdexploit
sajberinfo.com
VenomRAT zloupotrebljava VHD datoteke - Sajber Info Security
VenomRAT zloupotrebljava slike virtuelnog diska (eng. virtual hard disk image – VHD), pokazuje istraživanje sigurnosnih istraživača kompanije Forcepoint
Android bankarski trojanac TgToxic ažuriran sajberinfo.com/2025/03/19/and… #bankingtrojan #c2servers #domaingenerationalgorithm #emulatordetection #genymotion #malwareevolution #mobilesecurity #phishingcampaigns #qemu #tgtoxic #threatactoradaptation
sajberinfo.com
Android bankarski trojanac TgToxic ažuriran - Sajber Info Security
Android bankarski trojanac TgToxic pretrpio je značajna poboljšanja svoje zlonamjerne funkcionalnosti. Detaljna analiza sigurnosnih istraživača kompanije
New Blog Post! 🚨 hunt.io/blog/tracking-… We’ve tracked #PyramidC2, an open-source post-exploitation tool now being used to establish stealthy #C2servers. Read more about what we found in our latest blog post. #CyberSecurity #ThreatIntel
Understanding #C2servers is crucial in #cybersecurity as they are the central hub for threat actors, enabling them to steal data, control compromised systems, and spread malware across devices. Stay informed to fight against #cyberattacks with Hunt! hunt.io/glossary/c2-fr…
🔐 #C2Servers: Attackers use custom GPT models to generate command and control (C2) server scripts, enabling remote control of compromised systems. Our proactive #threatintelligence helps detect and mitigate such threats, protecting your organization from unauthorized access.
#C2Tracker Live Feed Of #C2Servers, Tools, And Botnets kitploit.com/2024/04/c2-tra…
🌏Joint effort to restore #CyberHygiene SEP-NOV 2023: #HKPF successfully removed all the 153 #C2servers identified locally—the greatest raid among the 55 members countries/regions that took down a total of 900+ such malicious servers during @INTERPOL_Cyber’s Operation Synergia🌐

During the op—#HKPF analysed ≈3 million pieces of intel about: 👾#C2servers 🤖#BotNets 🎣#phishing websites which led to the discovery of: 🚨170K+ serious Internet safety loopholes ⚠️≈40K #CyberThreats in HK We then demanded remedial action from 80 Internet service providers.

• #Malicious communications or network traffic may be taking place. These include: • Known patterns of #exploitkits • Connections to (known) #C2servers • Unusual #networktraffic or web browsing activity • #Emails with links to #suspicious or malicious websites
#CyberAttacks: Turn #Forums into #C2Servers To Control #MacBooks - bit.ly/3ds01rl-Ttx @tokyoneon_ via @NullByte 🔁 #Enterprises #Organizations #macOS #MyBBForum #CyberRisks #WebSites #InfoSec #CyberThreats #CyberSecurity #CommandAndControl #ITsecurity #CyberDefense

During the op—#HKPF analysed ≈3 million pieces of intel about: 👾#C2servers 🤖#BotNets 🎣#phishing websites which led to the discovery of: 🚨170K+ serious Internet safety loopholes ⚠️≈40K #CyberThreats in HK We then demanded remedial action from 80 Internet service providers.

🌏Joint effort to restore #CyberHygiene SEP-NOV 2023: #HKPF successfully removed all the 153 #C2servers identified locally—the greatest raid among the 55 members countries/regions that took down a total of 900+ such malicious servers during @INTERPOL_Cyber’s Operation Synergia🌐

Something went wrong.
Something went wrong.
United States Trends
- 1. #DWTS 4,030 posts
- 2. Elaine 8,020 posts
- 3. Kentucky 13K posts
- 4. #USMNT 1,803 posts
- 5. Uruguay 20.3K posts
- 6. Peggy 10.4K posts
- 7. Mark Pope N/A
- 8. Michigan State 9,056 posts
- 9. #WWENXT 3,395 posts
- 10. #NXTGoldRush 3,117 posts
- 11. Alex Freeman N/A
- 12. Berhalter 1,281 posts
- 13. Clay Higgins 33.5K posts
- 14. Carrie Ann N/A
- 15. Grisham 5,949 posts
- 16. Garrison 2,324 posts
- 17. Dearborn 108K posts
- 18. Oweh N/A
- 19. Poch N/A
- 20. Saudi 300K posts