#dockerapi ผลการค้นหา
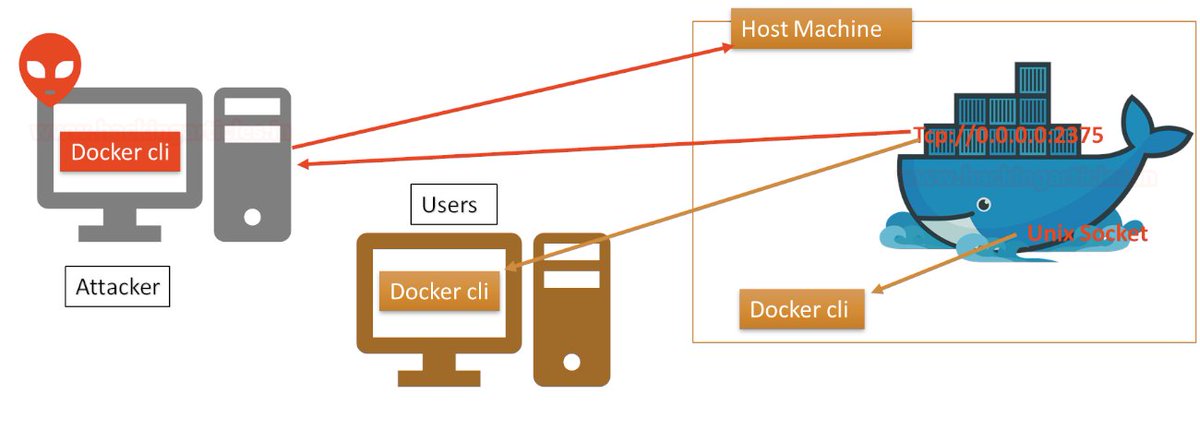
#Hacking #DockerAPI #UnixSocket #Vulnerability #CyberCrime #CyberAttack #CyberSecurity Docker for Pentester: Abusing Docker API. hackingarticles.in/docker-for-pen…
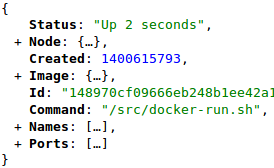
Open terminal windows using Go and Docker SDK stackoverflow.com/questions/7215… #dockerapi #terminal #xfce #go #docker

I'm trying to learn Docker API. I don't understand the difference between SSH and TLS. HELP #docker #dockerapi #programming #SSH #TLS #API #tech #JS #learning #coding #dockerdaemon #socket #daemon #protection #security
TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs reconbee.com/tor-based-cryp… #TOR #cryptojackingattack #DockerAPI #cyberattacks #CybersecurityNews #CyberSecurityAwareness
reconbee.com
TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs
employ similar tools to the original outbreak read more about TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs.
10.🐳 Docker API 📡 The Docker API is like the backstage pass for Docker Engine. It lets apps interact programmatically with Docker. You can use it to manage containers, images, and more, making automation a breeze! 💻🤖 #DockerAPI #Automation
New malware exploits misconfigured Docker APIs to spread and mine Dero cryptocurrency, creating malicious containers that infect other environments through worm-like propagation. Stay alert! 🚨 #DockerAPI #Cryptojacking #Russia ift.tt/e50yVM6
공격 표면에 노출된 도커 컨테이너 인증 없이 컨테이너에 접근 가능한 심각한 보안 이슈blog.criminalip.io/ko/2022/12/30/… #Docker #DockerRegistry #DockerAPI #DockerCompose #DockerSwarm #OSINT
🚨 Cybercriminals are exploiting #DockerAPI servers to deploy SRBMiner for crypto mining! Protect your systems with strong access controls and monitoring! #Cybersecurity #Cryptojacking
Thanks #DockerBoston for the tshirt and the talk! #dockerapi #ruby!
🐳 Did you know? Docker has a robust API, which enables you to automate container management and integrate Docker into your workflow seamlessly. Get hands-free! 🤖🚀🧰 #DockerAPI #Automation
teaching infrastructure to talk #dockerapi #Kubernetes #icp #vic so excited
🚨Attackers are exploiting exposed Docker APIs in a fresh campaign. Learn about their latest methods and how you can protect your systems. 🔗 Dive into the details: securitylabs.datadoghq.com/articles/attac… #CyberSecurity #DockerAPI
#dockerapi : docs.docker.com/engine/api/v1.… this tweet is only for myself or for the UX guys from #Docker: this page so hard to navigate I had to bookmark it here 🐬🤣
Docker container exposed to the attack surface! Serious security issue which malicious actors can access without authentication blog.criminalip.io/2022/12/30/doc… #Docker #DockerRegistry #DockerAPI #DockerCompose #DockerSwarm #OSINT
How #DockerAPI can be misused to plant #Malware #CyberSecurity searchcloudsecurity.techtarget.com/tip/How-Docker…
TeamTNT Botnet Updated to Steal Docker and AWS Credentials techdator.net/teamtnt-botnet… Hacking News #AWS #DockerAPI #LoginCredentials #TeamTNT
TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs reconbee.com/tor-based-cryp… #TOR #cryptojackingattack #DockerAPI #cyberattacks #CybersecurityNews #CyberSecurityAwareness
reconbee.com
TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs
employ similar tools to the original outbreak read more about TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs.
New malware exploits misconfigured Docker APIs to spread and mine Dero cryptocurrency, creating malicious containers that infect other environments through worm-like propagation. Stay alert! 🚨 #DockerAPI #Cryptojacking #Russia ift.tt/e50yVM6
Researchers discovered compromised containers due to an insecure #DockerAPI. The attack led to resource hijacking for #cryptomining and external #NetworkAttacks. #ThreatIntelligence #CyberSecurity securelist.com/dero-miner-inf…
"The #attacker first checked the availability and version of the #DockerAPI, then proceeds with requests for gRPC/h2c upgrades and #gRPC methods to manipulate Docker functionalities." trendmicro.com/en_us/research…
trendmicro.com
Using gRPC and HTTP/2 for Cryptominer Deployment: An Unconventional Approach
Using gRPC and HTTP/2 for Cryptominer Deployment: An Unconventional Approach
🚨 Cybercriminals are exploiting #DockerAPI servers to deploy SRBMiner for crypto mining! Protect your systems with strong access controls and monitoring! #Cybersecurity #Cryptojacking
Cybercriminals Exploiting Docker API Servers for SRBMiner Crypto Mining Attacks reconbee.com/cybercriminals… #cybercriminals #DockerAPI #Docker #SRBMiner #cryptominingattacks #cryptomining #CryptoNews #cryptomarket
reconbee.com
Cybercriminals Exploiting Docker API Servers for SRBMiner Crypto Mining Attacks
availability and version of the Docker API read more about Cybercriminals Exploiting Docker API Servers for SRBMiner Crypto Mining Attacks
New Malware Targets Exposed Docker APIs for Cryptocurrency Mining reconbee.com/new-malware-ta… #malware #DockerAPI #cryptocurrencymining #cryptocurrency #cybersecurity #cybersecuritynews #cyberattack
reconbee.com
New Malware Targets Exposed Docker APIs for Cryptocurrency Mining
launch a sequence of actions that include reconnaissance read more about New Malware Targets Exposed Docker APIs for Cryptocurrency Mining
🚨Attackers are exploiting exposed Docker APIs in a fresh campaign. Learn about their latest methods and how you can protect your systems. 🔗 Dive into the details: securitylabs.datadoghq.com/articles/attac… #CyberSecurity #DockerAPI
🐳 Did you know? Docker has a robust API, which enables you to automate container management and integrate Docker into your workflow seamlessly. Get hands-free! 🤖🚀🧰 #DockerAPI #Automation
10.🐳 Docker API 📡 The Docker API is like the backstage pass for Docker Engine. It lets apps interact programmatically with Docker. You can use it to manage containers, images, and more, making automation a breeze! 💻🤖 #DockerAPI #Automation
Docker container exposed to the attack surface! Serious security issue which malicious actors can access without authentication blog.criminalip.io/2022/12/30/doc… #Docker #DockerRegistry #DockerAPI #DockerCompose #DockerSwarm #OSINT
攻撃対象領域に漏えいされたドッカ―コンテナ、 認証なしでコンテナにアクセスできる深刻なセキュリティ問題 blog.criminalip.io/ja/2022/12/30/… #Docker #DockerRegistry #DockerAPI #DockerCompose #DockerSwarm #OSINT
공격 표면에 노출된 도커 컨테이너 인증 없이 컨테이너에 접근 가능한 심각한 보안 이슈blog.criminalip.io/ko/2022/12/30/… #Docker #DockerRegistry #DockerAPI #DockerCompose #DockerSwarm #OSINT
Open terminal windows using Go and Docker SDK stackoverflow.com/questions/7215… #dockerapi #terminal #xfce #go #docker

The Danger of Having an Exposed Docker API Port #dockerapi 🎬 youtu.be/6wGDS17YQo0
TeamTNT Botnet Updated to Steal Docker and AWS Credentials techdator.net/teamtnt-botnet… Hacking News #AWS #DockerAPI #LoginCredentials #TeamTNT
Open terminal windows using Go and Docker SDK stackoverflow.com/questions/7215… #dockerapi #terminal #xfce #go #docker

#Hacking #DockerAPI #UnixSocket #Vulnerability #CyberCrime #CyberAttack #CyberSecurity Docker for Pentester: Abusing Docker API. hackingarticles.in/docker-for-pen…

Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Halloween 887K posts
- 2. YouTube TV 52K posts
- 3. Dolphins 42.3K posts
- 4. #SinisterMinds 7,475 posts
- 5. Mary Ann N/A
- 6. Ryan Rollins 12.8K posts
- 7. #RUNSEOKJIN_epTOUR_ENCORE 117K posts
- 8. Lamar 53.8K posts
- 9. #T1WIN 8,457 posts
- 10. #Jin_TOUR_ENCORE 112K posts
- 11. YTTV N/A
- 12. Mike McDaniel 5,319 posts
- 13. Talbot 1,115 posts
- 14. Hulu 18.9K posts
- 15. Mindy 3,814 posts
- 16. Mork 1,830 posts
- 17. #TrickOrTreat 5,792 posts
- 18. frank iero 2,108 posts
- 19. Corey Perry N/A
- 20. toby fox 8,241 posts