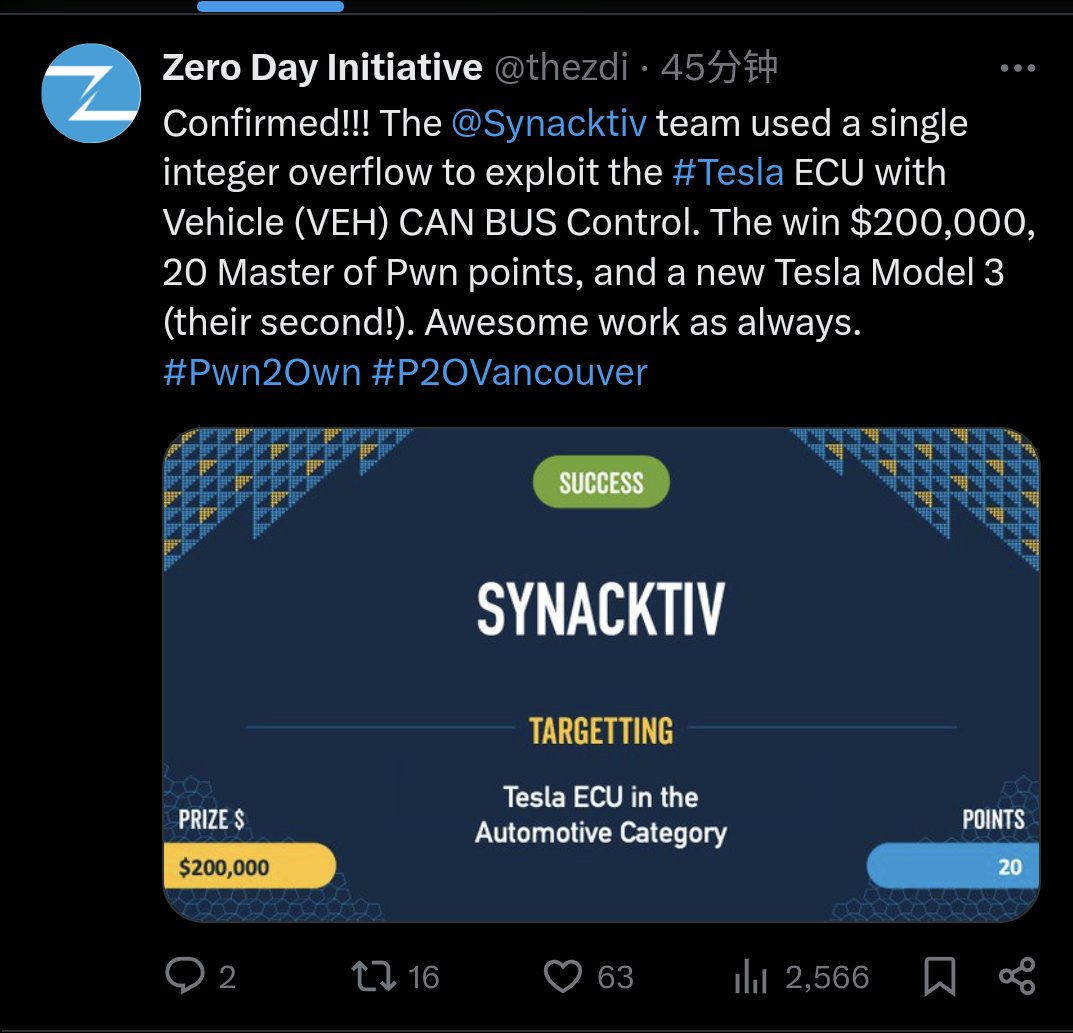
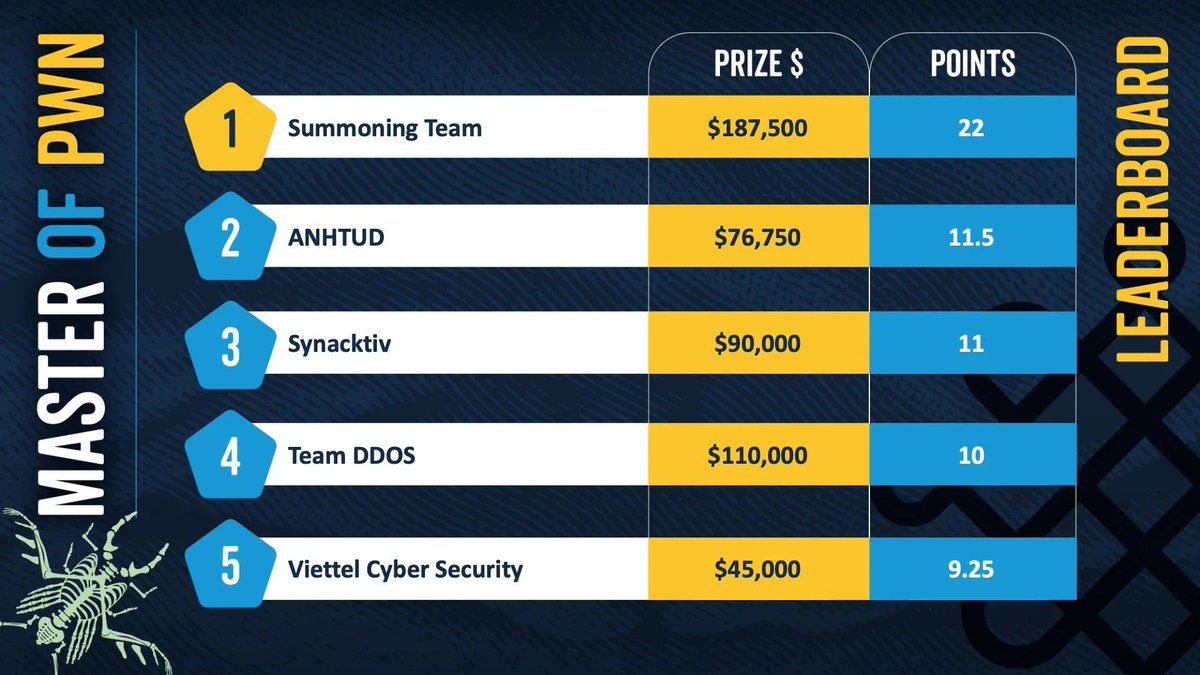
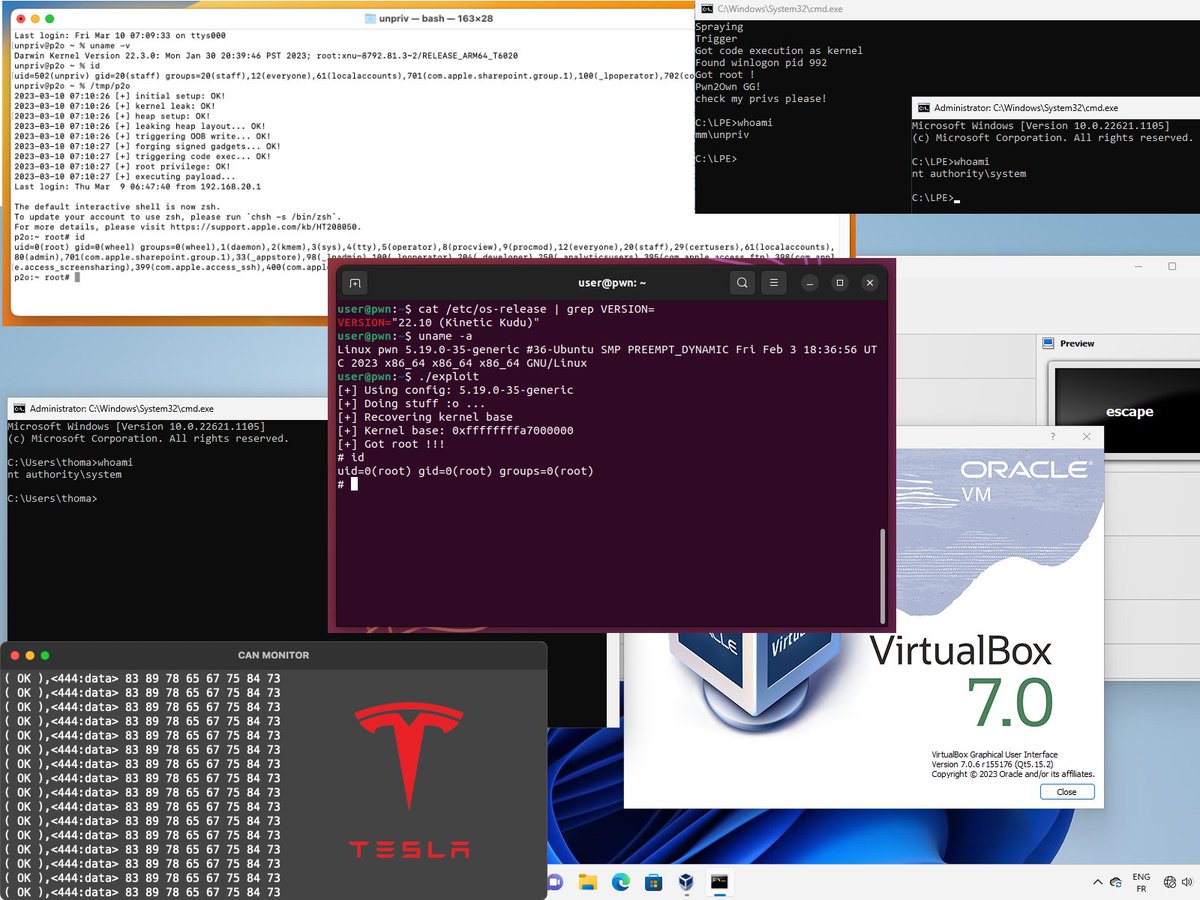
#pwn2own search results
Confirmed (with style!) - Interrupt Labs combined a path traversal and an untrusted search path bug to exploit the Lexmark CX532adwe. They got a reverse shell and loaded Doom on the LCD. We couldn't play it though :-[ Still awesome to see. #Pwn2Own


Seconds to spare and $40,000 on the line: @SinSinology of @SummoningTeam and the @theZDI team celebrate his successful exploit of Synology DiskStation DS925+ in the Network Attached Storage category at Pwn2Own Ireland. trendmicro.com/en_us/zero-day… #Pwn2Own
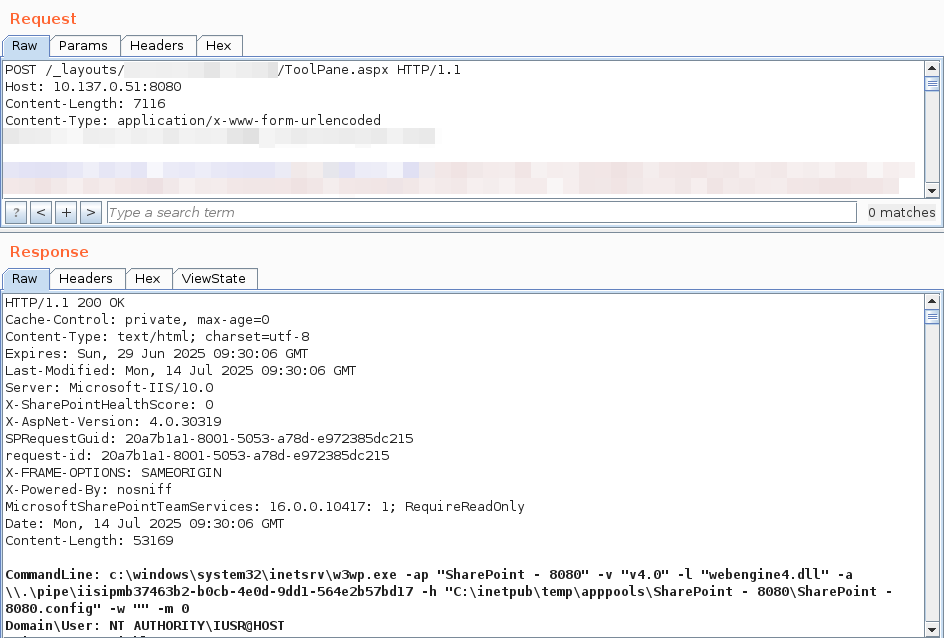
We have reproduced "ToolShell", the unauthenticated exploit chain for CVE-2025-49706 + CVE-2025-49704 used by @_l0gg to pop SharePoint at #Pwn2Own Berlin 2025, it's really just one request! Kudos to @mwulftange
Confirmed! Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) used a hard-coded cred and an injection to take over the QNAP TS-453E. These unique bugs earn him $20,000 and 4 Master of Pwn points. #Pwn2Own


Confirmed! David Berard of @synacktiv used a pair of bugs to exploit the Ubiquiti AI Pro in the Surveillance Systems category. The impressive display (incl. a round of Baby Shark) earns him $30,000 and 3 Master of Pwn Points. #Pwn2Own


Confirmed! namnp of Viettel Cyber Security used a crypto bypass and a heap overflow to exploit the Phillips Hue Bridge. They earn $20,000 and 4 Master of Pwn points, which catapults them in the Top 5. It also puts us over $1,000,000 for the contest! #Pwn2Own


Had an awesome time presenting the PoolParty research at @CanSecWest Great talks and people! Also super cool watching Pwn2own in person, big congrats to the contestants! #CanSecWest #Pwn2Own

We have another collision! Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS used a single bug to exploit the QNAP TS-453E, but the bug has been previously seen in the contest. Their work still earns them $10,000 and 2 Master of Pwn points. #Pwn2Own


Another amazing #Pwn2Own in the books! 💪 Our team pulled off some great hacks: 🖨️ HP Printer — $20K / 2 MoP 🏠 Home Assistant — $15K / 3 MoP 🔌 Smart Plug — $20K / 2 MoP 📸 Canon — $10K / 2 MoP Total: $65K / 9 MoP So proud of what we achieved together! 🧠⚡


For the past 3 years, participating in #Pwn2Own had been a dream for me. I could have never asked for a better debut! All of that would not have been possible without my teammate -and buddy - @kiddo_pwn. His work throughout this time has been outstanding! A huge thanks to all of…

🎉 Big win at #Pwn2Own Cork! @_p0ly_ of @Synacktiv successfully breached the @Ubiquiti AI Pro surveillance system 🦈🎶 What a way to wrap up the challenge - congrats, @_p0ly_ 💪

🔥 First time at #Pwn2Own, first win — and $15,000 later, we’re just getting started. Last week at @OffensiveCon, we trained, fuzzed, and pwned hard. Here’s the story 👇

#Pwn2Own and #F1 have a lot in common: Professionals at the top of their game, doing what few people can do.
If a zero-day exploit hits your @Sonos smart speakers and nobody is around to hear it, will they really make a sound? 👀 Find out next week at #Pwn2Own Ireland! #RCE #exploit #0day


Targeting the CHAR-X SEC-3150 controller for Pwn2Own automotive 2025 ? We released tooling to do full system emulation last year so you can work on your ROP chain while sipping Mate away from the lab :) github.com/onekey-sec/BHE… #Pwn2Own #Pwn2OwnAutomotive



Currently on stage at @sth4ck , @_cryptocorn_ with her colleague @Mad5quirrel for sharing their research on firmware done for #pwn2own 🤩 #proudfather ❤️

A big shout-out to the @Synacktiv team for their strong performance at the latest #Pwn2Own competition in Cork! They proudly secured third place overall 👏 Next stop: Tokyo for the upcoming edition 🇯🇵 👀 More details on the targets and participants here ℹ️…

Congrats on the win! #Pwn2Own is no joke. What was the most interesting vuln you guys hit?
Pwn2Own event revealed 73 zero-day vulnerabilities, awarding participants a total of $1 million for identifying significant cybersecurity issues. #CyberSecurity #ZeroDay #Pwn2Own #VulnerabilityResearch techday.asia/story/pwn2own-…
سینا خیرخواه بهمراه تیمش، پادشاه Pwn2Own Ireland 2025 شد. در این پست نگاهی به مسابقات Pwn2Own Ireland 2025 انداختیم که با قهرمانیSummoning Team، گزارش 73 زیرودی و بانتی 1,024,750 دلاری تمام شد. onhexgroup.ir/pwn2own-irelan… #Pwn2Own #Pwn2OwnIreland2025 #ZDI #0day
onhexgroup.ir
سینا خیرخواه بهمراه تیمش، پادشاه Pwn2Own Ireland 2025 شد
در این پست نگاهی به مسابقات Pwn2Own Ireland 2025 انداختیم که با قهرمانیSummoning Team، گزارش 73 زیرودی و بانتی 1,024,750 دلاری تمام شد.
A #Pwn2Own event with a humanoid category would be wild. Threat model: compromised update server, malicious motion planning commands, or just good old buffer overflow in the vision processing stack. Pick your vector and OWN the humanoids. 🤖
فريق Z3 حصل على أكبر جائزة في حدث #Pwn2Own وقدرها مليون دولار بعد ان اكتشف ثغرة خطيرة “0click 0day” في الواتساب تسمح بإدخال وتنفيذ كود ضار على جهاز الضحية دون أي تفاعل من المستخدم الغريب بالأمر ان الفريق انسحب ولم يستلم الجائزة بحجة ان العرض غير جاهز!! #CTF #0day

Proběhla hackerská soutěž #Pwn2Own Ireland 2025 organizována @thezdi a @TrendMicro. Vyplaceno bylo 1 024 750 dolarů za 73 unikátních zranitelností nultého dne (0-day). Vítězný Summoning Team @SummoningTeam pod vedením @SinSinology si odnesl 187 500 dolarů.
For the past 3 years, participating in #Pwn2Own had been a dream for me. I could have never asked for a better debut! All of that would not have been possible without my teammate -and buddy - @kiddo_pwn. His work throughout this time has been outstanding! A huge thanks to all of…

3 years of work — released. Respect to the researcher. 🔥 #Pwn2Own
It took 3 years but finally I feel ready to release my Pwn2Own 2021 exploit code. 💖 Video talk covers my full research workflow, from attack surface modeling and reverse engineering, to vulnerability discovery and systematic exploit engineering, enjoy! #Pwn2Own
#Pwn2Own and #F1 have a lot in common: Professionals at the top of their game, doing what few people can do.
Another #Pwn2Own in the books. These events showcase the best vulnerability research happening right now, and watching the community come together around it never gets old. Congrats to everyone who participated. #P2OIreland
Wrapping up #Pwn2Own Ireland 2025. The three day event saw some amazing exploits and traumatic failures. We laughed, we cried, we shouted. Check out the highlights and see who won Master of Pwn. #P2OIreland youtu.be/ruxOpC-b-yM?si…

youtube.com
YouTube
Wrapping Up Pwn2Own Ireland 2025
At Hacking event if they had demonstrated it, they might have won 1 Million Dollars 💵 but they didn’t demonstrated. Why was that ? Does Meta giving more than this or there is something else, blackmarket game or what ? 🙄🙄 @whatsappzeroday #pwn2own #trendmicro #zerodayexploit
HackRead: Hackers racked up over $1 M at #Pwn2Own 2025 in Ireland, breaching everything from printers to NAS devices and smart home gear as #SummoningTeam claimed the Master of Pwn title. 💥🔐 Read the full breakdown: hackread.com/pwn2own-irelan… #Cybersecurity #Infosec #0day #I…
Hackers racked up over $1 M at #Pwn2Own 2025 in Ireland, breaching everything from printers to NAS devices and smart home gear as #SummoningTeam claimed the Master of Pwn title. 💥🔐 Read the full breakdown: hackread.com/pwn2own-irelan… #Cybersecurity #Infosec #0day #Ireland
💥 73 zero-daye i ponad 1 mln USD nagród. Wczoraj zakończyło się #Pwn2Own Ireland 2025 – rekordowa liczba exploitów w routerach, NAS-ach, drukarkach i smart home. Najczęstsze wektory: buffer overflow, command injection, SSRF, format string.

انسحاب تكتيكي لteam z3 من عرض كشف تغرة 0click في واتساب بقيمة مليون دولار في p2o #pwn2own اشهر ضحية كانت هاتف سامسونج s25 .. انتظروا الترقيعات لتغرات 😁😎
#Pwn2Own WhatsApp Hacker Says Exploit Privately Reported to Meta securityweek.com/pwn2own-whatsa…
Confirmed (with style!) - Interrupt Labs combined a path traversal and an untrusted search path bug to exploit the Lexmark CX532adwe. They got a reverse shell and loaded Doom on the LCD. We couldn't play it though :-[ Still awesome to see. #Pwn2Own


We have reproduced "ToolShell", the unauthenticated exploit chain for CVE-2025-49706 + CVE-2025-49704 used by @_l0gg to pop SharePoint at #Pwn2Own Berlin 2025, it's really just one request! Kudos to @mwulftange

Confirmed! David Berard of @synacktiv used a pair of bugs to exploit the Ubiquiti AI Pro in the Surveillance Systems category. The impressive display (incl. a round of Baby Shark) earns him $30,000 and 3 Master of Pwn Points. #Pwn2Own


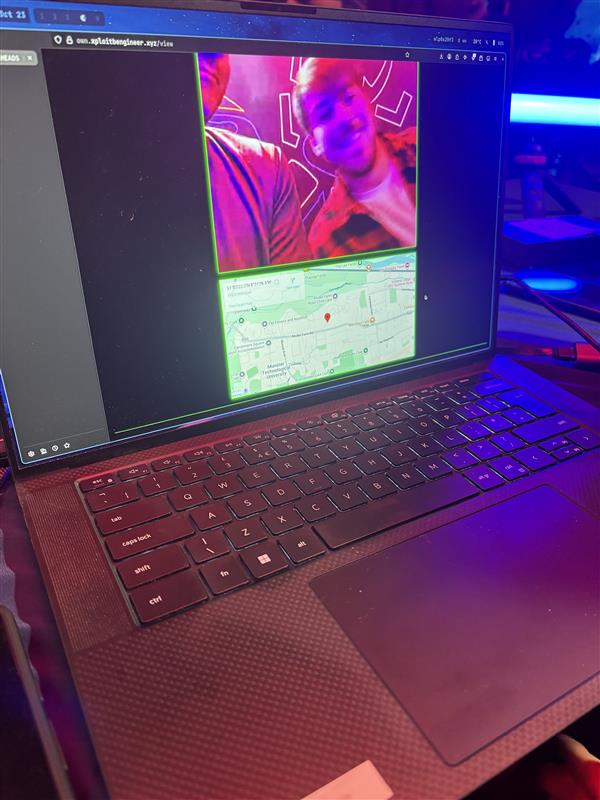
Another big confirmation! Ben R. And Georgi G. of Interrupt Labs used an improper input validation bug to take over the Samsung Galaxy S25 - enabling the camera and location tracking in the process. They earn $50,000 and 5 Master of Pwn points. #Pwn2Own

Here we are! 🥷 Masters of pwn for the third time 🎉 Congratulations to all the ninjas involved! #Pwn2Own



Wow!! Thank you ALL for so much support on my first #Pwn2Own win!! I’m very lucky to have a team and leadership that believes in me. I’m really proud of this bug; this is one of hardest exploits I’ve ever written. I can’t wait to share the details with you once it’s patched!

Confirmed! namnp of Viettel Cyber Security used a crypto bypass and a heap overflow to exploit the Phillips Hue Bridge. They earn $20,000 and 4 Master of Pwn points, which catapults them in the Top 5. It also puts us over $1,000,000 for the contest! #Pwn2Own


Competing in #Pwn2Own 2021 Austin: Icarus at the Zenith by @0vercl0k doar-e.github.io/blog/2022/03/2…


Confirmed! Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) used a hard-coded cred and an injection to take over the QNAP TS-453E. These unique bugs earn him $20,000 and 4 Master of Pwn points. #Pwn2Own


Confirmed! Chris Anastasio of Team Cluck used a single type confusion bug to exploit the Lexmark CX532adwe printer. He earns himself $20,000 and 2 Master of Pwn points. #Pwn2Own


Had an awesome time presenting the PoolParty research at @CanSecWest Great talks and people! Also super cool watching Pwn2own in person, big congrats to the contestants! #CanSecWest #Pwn2Own

For the past 3 years, participating in #Pwn2Own had been a dream for me. I could have never asked for a better debut! All of that would not have been possible without my teammate -and buddy - @kiddo_pwn. His work throughout this time has been outstanding! A huge thanks to all of…

Something went wrong.
Something went wrong.
United States Trends
- 1. #AEWDynamite 18.4K posts
- 2. Will Richard 3,873 posts
- 3. #Survivor49 3,041 posts
- 4. #SistasOnBET 2,204 posts
- 5. #ChicagoPD 1,024 posts
- 6. Klay 6,559 posts
- 7. #AmphoreusStamp 2,398 posts
- 8. Godzilla 29.6K posts
- 9. Unplanned 4,713 posts
- 10. Nico Harrison N/A
- 11. Binnington 2,335 posts
- 12. Podz 1,342 posts
- 13. Harrison Barnes N/A
- 14. Jovic 1,030 posts
- 15. Spencer Knight N/A
- 16. Kent State 1,328 posts
- 17. Athena 10.2K posts
- 18. Savannah 5,451 posts
- 19. Pat Spencer N/A
- 20. Cade 30.6K posts