#reverseengineering 검색 결과
Reverse Engineering WASM binaries, trace indirect calls, decode memory layouts medium.com/%40pnfsoftware… #WASM #ReverseEngineering #SecurityResearch
🧰 Beginners Guide: Comprehensive Reverse Engineering Tutorials for Beginners PDF: 0xinfection.github.io/reversing/reve… author: @0xInfection #infosec #reverseengineering

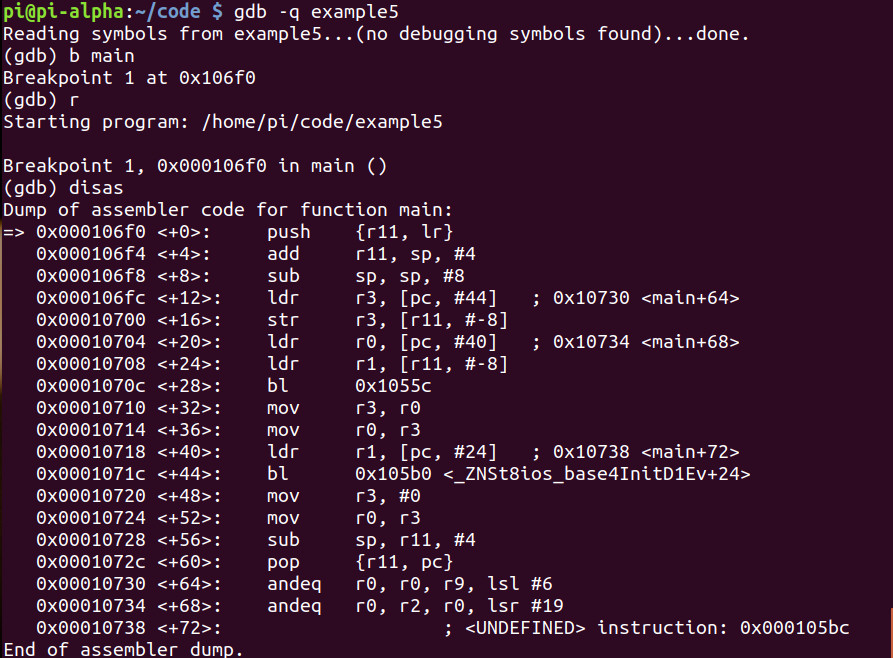
It just warms my heart ❤️ #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware
Exploit a Use-After-Free vulnerability in an ARM64 binary. Full breakdown here: 8ksec.io/arm64-reversin… #ARM64 #ReverseEngineering #Exploitation #CyberSecurity #MobileSecurity

Reverse engineering the Yaesu FT-70D firmware encryption #HamRadio #ReverseEngineering blog.adafruit.com/2025/11/13/rev…

♾ Reverse Engineering 101: Android App Reverse Engineering Guide Guide: ragingrock.com/AndroidAppRE/ author: @maddiestone #infosec #reverseengineering


Check out this awesome project on GitHub: Frida Gadget. A powerful tool that automates APK patching to integrate Frida Gadget by downloading the library and injecting code into the main activity🛠️ #Frida #ReverseEngineering github.com/ksg97031/frida…

You've never seen an optical coordinate system like this. This is the MaxSHOT 3D from Creaform, and it's a game-changer to your 3D scanning process. Check out the full specs and see if the MaxSHOT 3D is built for you: hubs.la/Q03Pb0dj0 #reverseengineering #metrology
🔥 A week after release and thank God, MAoS – Malware Analysis on Steroids is officially a #1 Best Seller on Amazon! Get your copy today: amazon.com/gp/aw/d/B0FQDL… #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware


Been working on a side project during my free time for a while 👀...Here’s a tiny peek — can’t say much yet... besides that it’s so f***ing useful 😅 #Android #Security #ReverseEngineering

New Android BEERUS framework for dynamic analysis & reverse engineering BEERUS brings Frida auto-injection, sandbox exfiltration, memory dumps, Magisk integration and more for on device app analysis by @HakaiOffsec #AndroidSecurity #Frida #ReverseEngineering #MalwareAnalysis


Payment card terminals analysis and reverse engineering (Worldline Yomani XR terminal) stefan-gloor.ch/yomani-hack #embedded #reverseengineering


🕵️♂️ @reivilo_t at #hw_ioNL2025 is breaking down circuit behaviour and scrambling techniques like engineers in a heist movie planning the big reveal. Know More: hardwear.io/netherlands-20… #integratedcircuits #reverseengineering #ROM

I got a request to make an PURE Assembler driver in RISC-V so here it is. No SDK as it will teach you the basics of a RISC-V chip specifically the ESP32-C3. #Embedded #ReverseEngineering github.com/mytechnotalent…

👨💻 Want to work at @epieos? Meet us at @hexacon_fr 2025! 🛡️ Hexacon is a world-class event for enthusiasts of #OffensiveSecurity and #ReverseEngineering. 🤝 We’ll be there to meet exceptional talents, curious, rigorous, and driven by the desire to use their technical #skills,…

Lesson 21: x86 Course (Part 21 - How To Compile A Program) - This tutorial will address how to compile a basic x86 Assembly Program. #ReverseEngineering github.com/mytechnotalent…
Example: IDA + DIE — Decode XOR data directly in DIE’s data convertor. A fast workflow for efficient malware analysis. #MalwareAnalysis #XOR #ReverseEngineering #DIE #IDA
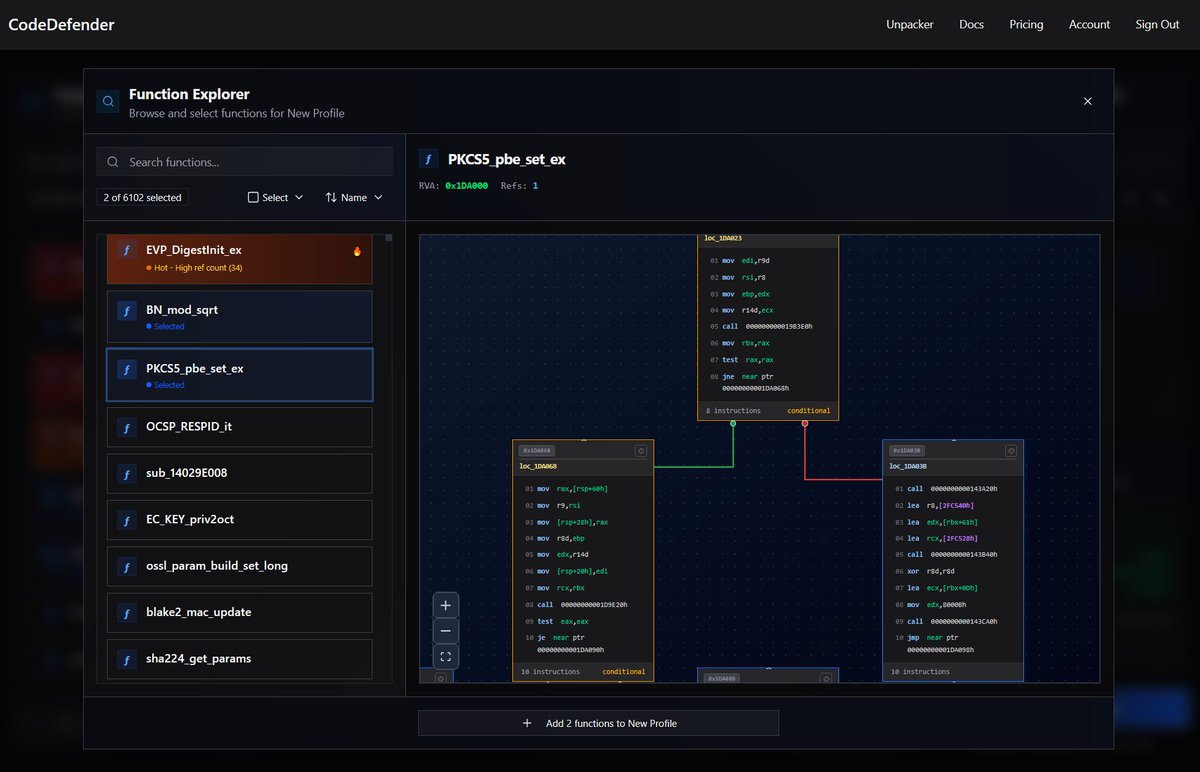
Our CodeDefender SaaS has received a major update which includes the following: 🛠️Our new and improved compiler framework 💥SSE hardened mutations 🚀New UI/UX interface 💪Custom obfuscation pass configuration 🔗Register now: app.codedefender.io #reverseengineering…

Accurate measurement of large-sized workpieces requires no compromise Web: 3dscan.cn/en #3DScanner #Metrology #ReverseEngineering #3DScannerSolution #Handheldscanner #3Dinspection #3Dmodelingl #3Dlaserscanner #engine #Windturbine #3Dprinting #metal #energy #Mining

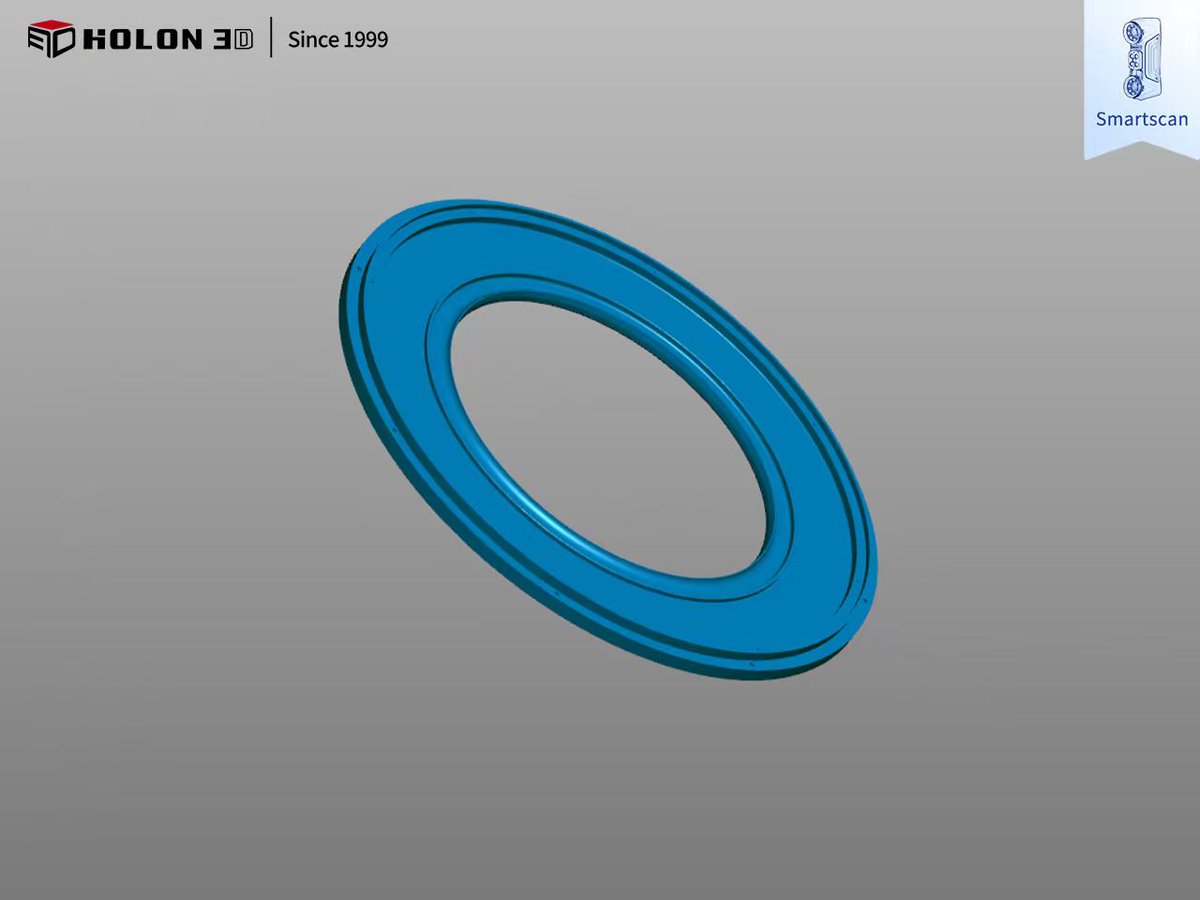
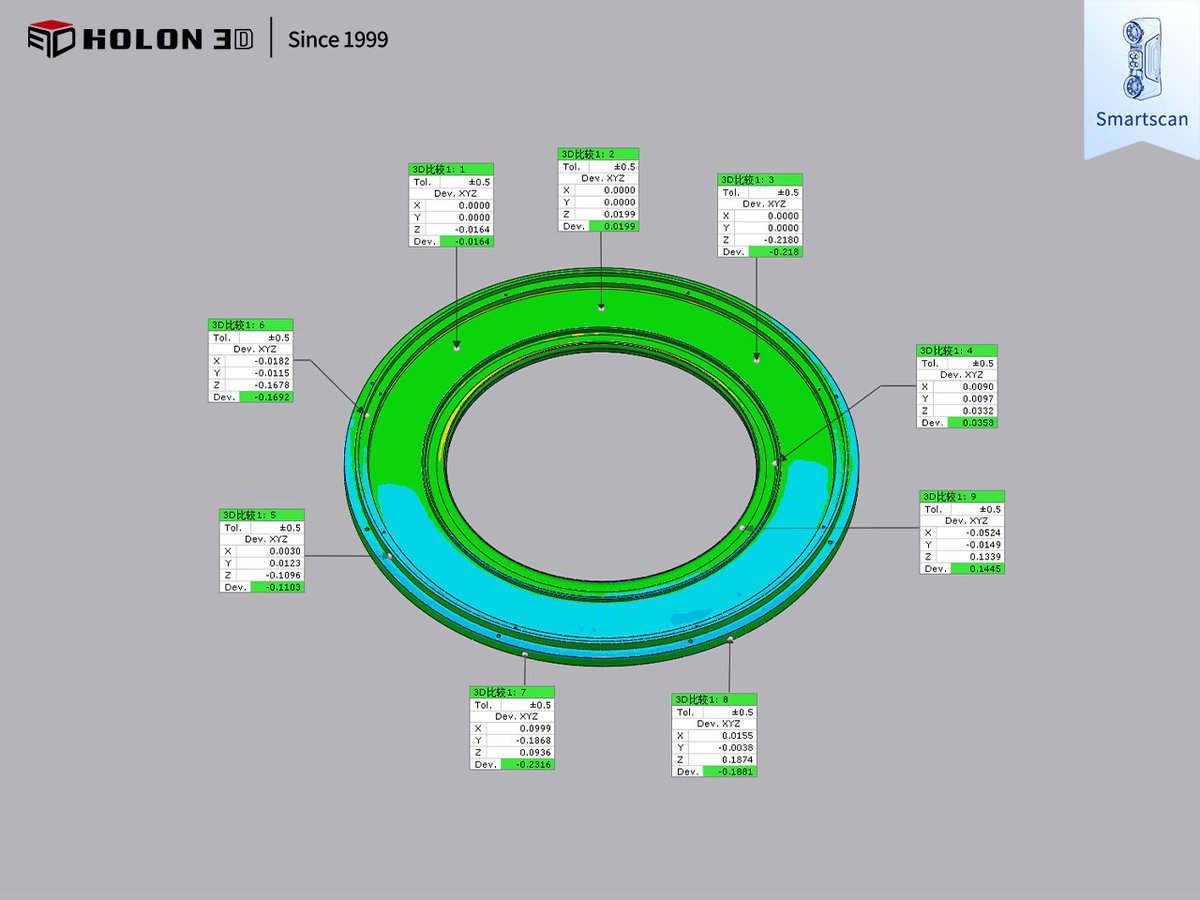
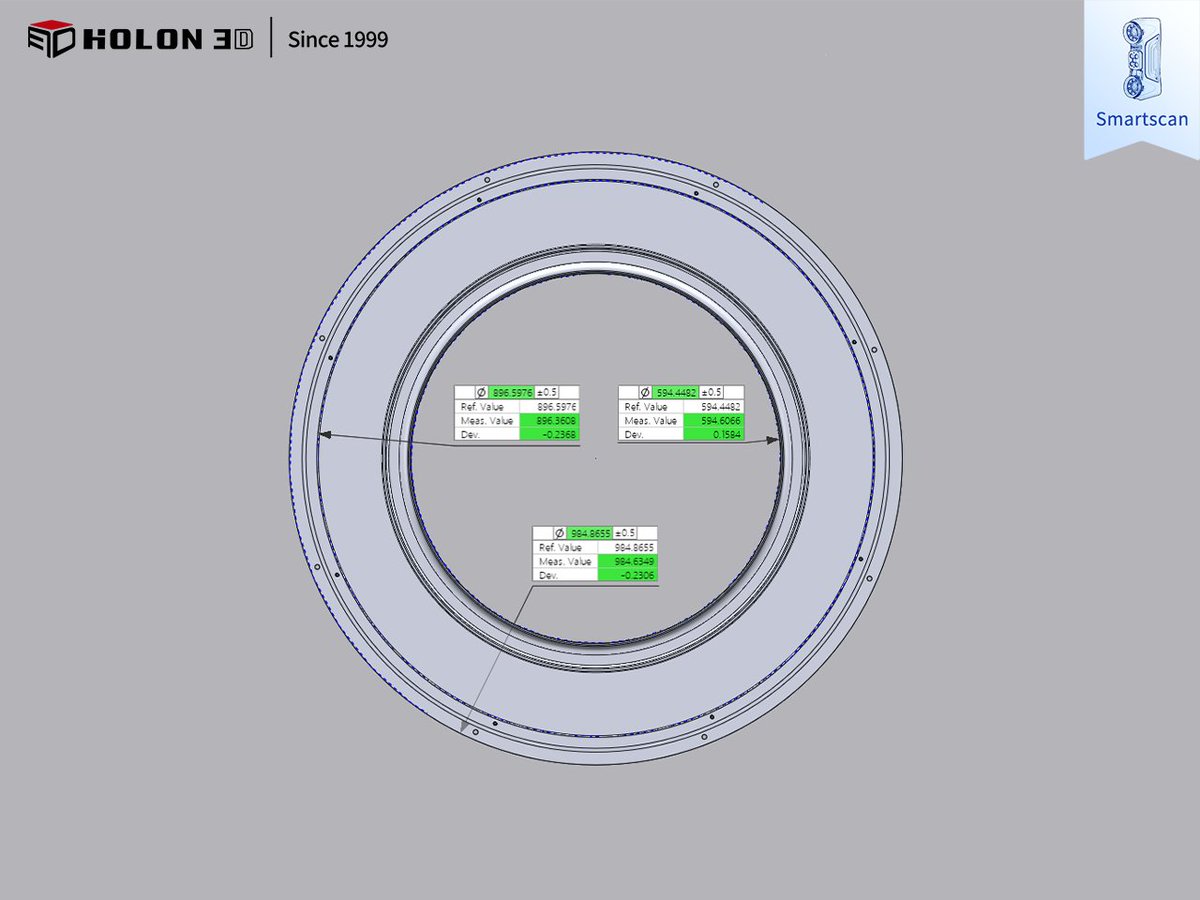
Think of trading like reverse engineering. Study the methods of successful traders and adapt their strategies to your own style. Don't reinvent the wheel! #TradingEducation #LearningFromOthers #ReverseEngineering
Day 19/100 — New Chapter: Reverse Engineering بدأت أذاكر Reverse Engineering وبدأت كمان أحل لابات PortSwigger Tiny moves, massive growth. #100DaysOfCybersecurity #ReverseEngineering #PortSwigger #OmarCyberJourney
Day 18/100 — PrivEsc Win Completed خلصت سيناريوهات Windows Privilege Escalation الحمدلله. اليوم كان مرهق جدًا…

QUICKSURFACE 2026 is now live. Explore everything that’s new quicksurface.com/whats-new-qs20… If you’re at FORMNEXT this week, come see QUICKSURFACE 2026 in action (Hall 12.1 — F21). #QUICKSURFACE #ScanToCAD #ReverseEngineering #Parasolid #SOLIDWORKS #FORMNEXT #Manufacturing #3DScanning
Reverse Engineering WASM binaries, trace indirect calls, decode memory layouts medium.com/%40pnfsoftware… #WASM #ReverseEngineering #SecurityResearch

Meet DefinSight MODEL — our next-gen scan-to-CAD software. Turn complex 3D scans into clean, editable CAD models faster than ever. AI-powered features, precise alignment, hybrid modeling, and an intuitive workflow. Step into the next era of #reverseengineering. #ScanToCAD #CAD

🕵️♂️ @reivilo_t at #hw_ioNL2025 is breaking down circuit behaviour and scrambling techniques like engineers in a heist movie planning the big reveal. Know More: hardwear.io/netherlands-20… #integratedcircuits #reverseengineering #ROM

No official API? That’s just an invitation! Your browser’s Network tab is your map. Reverse engineering isn’t magic—it’s patient sleuthing. Ever tried this with a site you love? Read more: iam.slys.dev/p/no-official-… #ReverseEngineering #WebDev #APIs
🤝 ✨ Laughter, questions, and “wait, what?!” Moments ripple through the rooms as participants tackle FPGA inner workings like a collaborative heist team. @JulianSpeith, René Walendy & Simon Klix at #hw_ioNL2025 Know More: hardwear.io/netherlands-20… #FPGA #reverseengineering

Lesson 29: x86 Course (Part 29 - ASM Debugging 3 [Moving Data Between Memory And Registers]) - This tutorial will address how to debug our third real Assembly Program by moving between memory and registers. #ReverseEngineering github.com/mytechnotalent…
By seeing the physical object, a 3D CAD model can be generated! #3DScanner #Metrology #ReverseEngineering #3DScannerSolution #Handheldscanner #3Dinspection #3Dmodelingl #3Dlaserscanner #engine #Windturbine #3Dprinting #metal #energy #Mining #Automobileindustry #qualitycontrol
@SamsungCanada How could u not know & tell Canadians? @MarkJCarney When we're in privacy of our home,our privacy must be protected. This has to stop. We need to debug our country. #PegasusSpyNetworksNeedToBeDismantledWorldwide. #ReverseEngineering. #RightToPrivacy.
“Life feels messy? We fix that.” Most problems aren’t huge they just stack up. SolvProb builds simple digital tools that clean up your day so life flows better. One solved problem at a time. #solvprob #reverseengineering #problemsolving
GhidraMCP enables autonomous reverse engineering by providing an MCP server that lets LLMs interact with core Ghidra tools. Powerful step toward automated analysis. Repo: github.com/LaurieWired/Gh… #Ghidra #ReverseEngineering #CyberSecurity #MCP #AItools
🛠️ JUST DROPPED: How I reverse-engineered a BatToExe malware & extracted its FULL.BAT source using x32dbg! 🔍 Watch the full breakdown 👇 #MalwareAnalysis #ReverseEngineering #CyberSec @petikvx
Lesson 28: x86 Course (Part 28 - ASM Program 3 [Moving Data Between Memory And Registers]) - This tutorial will address how to create our third real Assembly Program by moving between memory and registers. #ReverseEngineering github.com/mytechnotalent…
🔒 Just finished my first reverse engineering project! Spent 28 hours analyzing a WoW 3.3.5a client's cryptography (SRP6 + RC4). As a beginner, I'd love feedback from the #ReverseEngineering community. Project: github.com/Kyworn/wow-335…
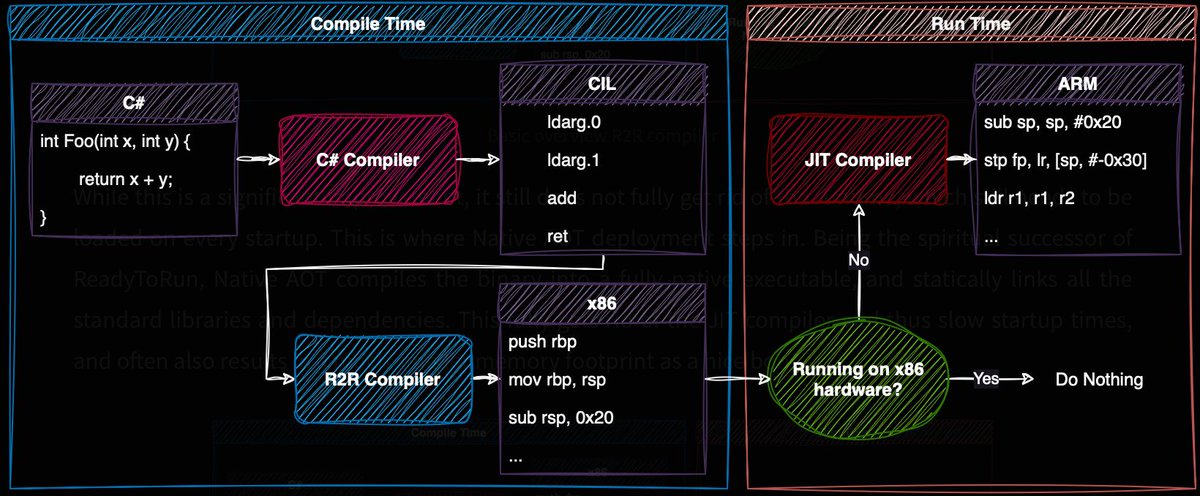
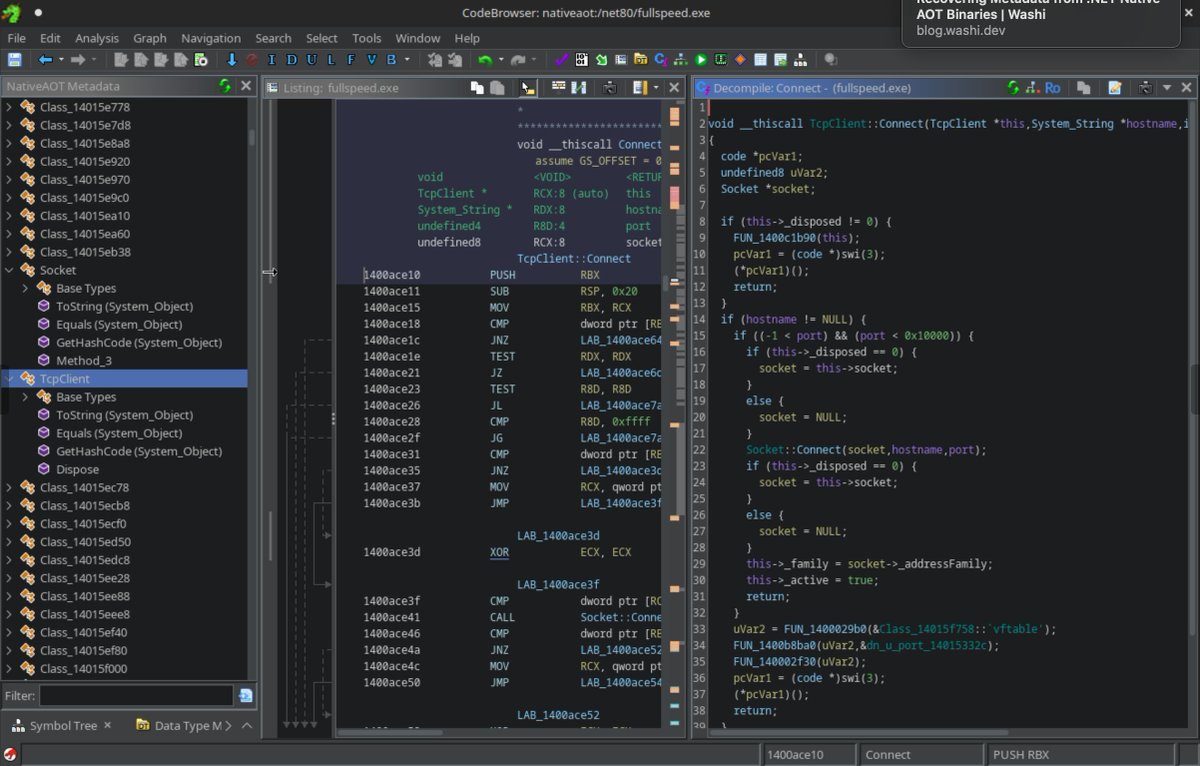
Reverse engineering .NET Native Ahead-Of-Time (AOT) compiled binaries blog.washi.dev/posts/recoveri… #infosec #reverseengineering
RE tip of the day: At runtime, Windows Loader parses the import directory to get all the required imports by their names/ordinals, loads the corresponding DLLs into the process's address space and writes the imports' addresses into the IAT. #infosec #malware #reverseengineering


🧰 Beginners Guide: Comprehensive Reverse Engineering Tutorials for Beginners PDF: 0xinfection.github.io/reversing/reve… author: @0xInfection #infosec #reverseengineering


Reverse Engineering 101: Android App Reverse Engineering Guide Guide: ragingrock.com/AndroidAppRE/ #infosec #reverseengineering


Exploit a Use-After-Free vulnerability in an ARM64 binary. Full breakdown here: 8ksec.io/arm64-reversin… #ARM64 #ReverseEngineering #Exploitation #CyberSecurity #MobileSecurity

Valve Anti-Cheat (VAC) solution reverse engineering codeneverdies.github.io/posts/gh-2/ #infosec #reverseengineering


Valve Anti-Cheat (VAC) reverse engineering codeneverdies.github.io/posts/gh-2/ #infosec #reverseengineering


Excellent blog post on reverse engineering the Valve Anti-Cheat (VAC) solution codeneverdies.github.io/posts/gh-2/ #infosec #reverseengineering


Check out this awesome project on GitHub: Frida Gadget. A powerful tool that automates APK patching to integrate Frida Gadget by downloading the library and injecting code into the main activity🛠️ #Frida #ReverseEngineering github.com/ksg97031/frida…

⚡️New free reverse engineering challenge on ACEResponder.com! Analyze a Windows executable and recover the password. #Malware #ReverseEngineering

It just warms my heart ❤️ #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware

"DisARMing" code - an exploration into systems programming, #debugging & #reverseEngineering on #Linux/#Android/#Darwin and #Aarch64! 510+ pages #book in COLOR(!) NewDebuggingBook.com for details, because there's more to detail than the margins of a Twitter message can hold.

🆓New free reverse engineering challenge on ACEResponder.com! Analyze a Windows executable and recover the password. #Malware #ReverseEngineering

Reverse Engineering WASM binaries, trace indirect calls, decode memory layouts medium.com/%40pnfsoftware… #WASM #ReverseEngineering #SecurityResearch

Payment card terminals analysis and reverse engineering (Worldline Yomani XR terminal) stefan-gloor.ch/yomani-hack #embedded #reverseengineering


Our CodeDefender SaaS has received a major update which includes the following: 🛠️Our new and improved compiler framework 💥SSE hardened mutations 🚀New UI/UX interface 💪Custom obfuscation pass configuration 🔗Register now: app.codedefender.io #reverseengineering…


Pretty cool website by @0x6D6172636F! 🔥 Not much content yet, but it's a great starter for learning more about RE. Even better if you're into fancy ASCII art! 🤩 #ReverseEngineering #PE 👉 x86re.com

Reverse engineer payment card terminals (Worldline Yomani XR terminal) stefan-gloor.ch/yomani-hack #embedded #reverseengineering


New Android BEERUS framework for dynamic analysis & reverse engineering BEERUS brings Frida auto-injection, sandbox exfiltration, memory dumps, Magisk integration and more for on device app analysis by @HakaiOffsec #AndroidSecurity #Frida #ReverseEngineering #MalwareAnalysis



Something went wrong.
Something went wrong.
United States Trends
- 1. LeBron 79.3K posts
- 2. #DWTS 53K posts
- 3. #LakeShow 3,797 posts
- 4. Whitney 15.8K posts
- 5. Peggy 18.3K posts
- 6. Reaves 8,141 posts
- 7. Keyonte George 1,862 posts
- 8. Jazz 27K posts
- 9. Orioles 6,928 posts
- 10. Macklin Celebrini 2,434 posts
- 11. Elaine 17.3K posts
- 12. Taylor Ward 3,517 posts
- 13. #TheFutureIsTeal 1,522 posts
- 14. Grayson 6,982 posts
- 15. Dylan 25K posts
- 16. Tatum 16.2K posts
- 17. #Lakers 1,596 posts
- 18. tDUSD N/A
- 19. #WWENXT 17.1K posts
- 20. Angels 31.9K posts