#win32k search results

Win32k that we lost. In details writeup about CVE-2023-29336 (written by Sergey Tarasov @immortalp0ny) : deadprogrammers.club/posts/in-detai… #win32k #vulnerability #exploitation #exploit #informationsecurity
This month's #Microsoft Patch Tuesday (again) addresses: Two "important" #Win32k Elevation of Privilege bugs under active attack

A step-by-step walkthrough of a proof-of-concept for #CVE-2022-21882 gives the chance for a deep dive into the inner structure of #Win32k and exactly how CVE-2022-21882 and CVE-2021-1732 operate. bit.ly/43Lnqha

An analysis of the Win32 #API that creates #GUI objects such as windows and menus begins with the background of #Win32k. From there, we dive into callbacks and how they function, and why these callbacks can be exploited by threat actors. #MicrosoftWindows bit.ly/3Jffxsb

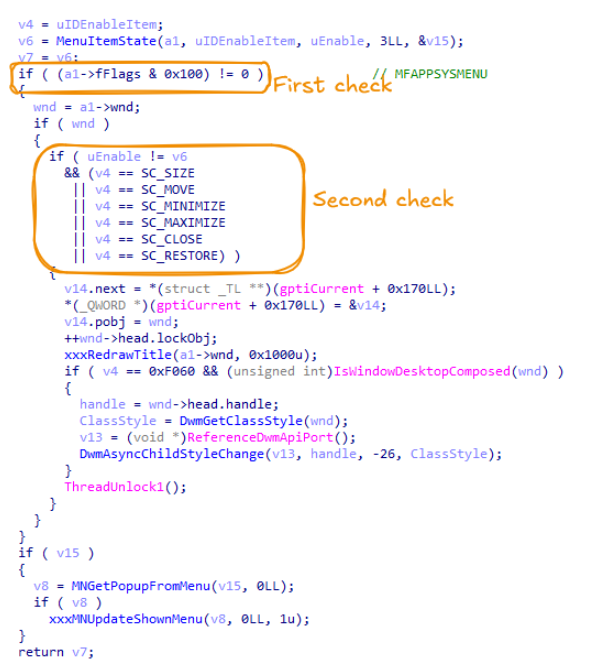
📌#Win32k Smash the Ref - New Bug Class and #Exploitation Techniques by Gil Dabah ⚙️[SRC]:github.com/gdabah/win32k-… 📕[PDF]:github.com/gdabah/win32k-… 📝[BLOG]:ragestorm.net/blogs/?p=502 #windows #Security
![ntlmrelay's tweet image. 📌#Win32k Smash the Ref - New Bug Class and #Exploitation Techniques by Gil Dabah
⚙️[SRC]:github.com/gdabah/win32k-…
📕[PDF]:github.com/gdabah/win32k-…
📝[BLOG]:ragestorm.net/blogs/?p=502
#windows #Security](https://pbs.twimg.com/media/EUrhW2zUMAIEKJW.png)
In the 2023 OpenTRS #3 📡 CTF Team GYG and Theori VR team explores #MacOS, #Win32k vulnerabilities. And our CTO @andrewwesie takes you through #Web3 ZK proof-based @RelicProtocol On July 6th, live on theori.tv This seminar will be conducted in English.

⚠️ #MysterySnail progresse via une vulnérabilité zero-day. Nos technologies de sécurité ont détecté l’exploitation d’une vulnérabilité jusqu’alors inconnue dans le pilote #Win32k. Pour en savoir plus 👉 kas.pr/tbg2

Our newest research is an evaluation of two specific #Win32k PoC exploits. CVE-2021-1732 is analyzed with a proof of concept walkthrough and its similarities to CVE-2022-21882. #MicrosoftWindows bit.ly/43Lnqha

Guys & girls! Exactly a year ago I promised over 15 bugs in win32k. You're welcome to read and find out about my biggest research so far: #win32k #SmashTheRef bug class - github.com/gdabah/win32k-… Check out the paper and the POCs, there are some crazy stuff going on. Promise!
CVE-2015-1701 / MS15-051 source and demo. Test successfull on win7 #win32k #lpe #apt #infosec github.com/hfiref0x/CVE-2…

⚠️ Pour ceux qui ont raté l'info... #Microsoft a sorti un correctif pour lutter contre un #0day #Win32k 🔥 darkreading.com/vulnerabilitie… ➡️ CVE-2021-1732, exécution de code avec élévation de privilèges 💣 Exploitations détectées en Chine 🇨🇳 A vos marques, prêts... patchez !!

‘#Zombie’ #Windows #win32k bug reanimated by researcher: Dozens of bugs in a core #Windows API could… dlvr.it/RTR03q @RedSeal_co

#win32k handle validation local dos #0day (which MS decided not to release bulletin for), in 'IsHandleEntrySecure()': pastebin.com/we0ZSQC0
A serious Windows LPE flaw in DirectComposition allows local attackers to gain SYSTEM privileges by exploiting a type confusion bug leading to a controlled out-of-bounds write in kernel memory. #WindowsLPE #Win32K #Cybersecurity #PatchTuesday securityonline.info/researcher-rel…
#CiberAlertas_EcuCERT vulnerabilidad de @Microsoft @Windows, permite a un atacante local autenticado, obtener privilegios de administrador a través de una vulnerabilidad en el controlador #Win32k.sys. Detalles al respecto en: ecucert.gob.ec/alertas/

⚠️ALERTA ⚠️ #Vulnerabilidad #Win32k Compartimos un informe con las últimas alertas críticas detectadas por nuestro #CSVD: boletín de #ciberseguridad, Vulnerabilidad de elevación de privilegios de Win32k. hubs.ly/Q0157V2v0

Win32k that we lost. In details writeup about CVE-2023-29336 (written by Sergey Tarasov @immortalp0ny) : deadprogrammers.club/posts/in-detai… #win32k #vulnerability #exploitation #exploit #informationsecurity

Analysis of CVE-2023-29336 #Win32k Privilege Escalation #privesc #Vulnerability (with #POC) numencyber.com/cve-2023-29336…
[OpenTRS 2023 #3] Session 3 #Vulnerability in Desktop #WindowManager (#Win32k Exploit in User Land) Theori Vulnerability Research @kkokkokye youtu.be/QvpWofwhPps
youtube.com
YouTube
[OpenTRS 2023 #3] Vulnerability in Desktop Window Manager (Win32k...
In the 2023 OpenTRS #3 📡 CTF Team GYG and Theori VR team explores #MacOS, #Win32k vulnerabilities. And our CTO @andrewwesie takes you through #Web3 ZK proof-based @RelicProtocol On July 6th, live on theori.tv This seminar will be conducted in English.

Our newest research is an evaluation of two specific #Win32k PoC exploits. CVE-2021-1732 is analyzed with a proof of concept walkthrough and its similarities to CVE-2022-21882. #MicrosoftWindows bit.ly/43Lnqha

Unit 42's newest research is an evaluation of two specific #Win32k PoC exploits. CVE-2021-1732 is analyzed with a proof of concept walkthrough and its similarities to CVE-2022-21882 #MicrosoftWindows sprou.tt/137SFTeByZQ
A step-by-step walkthrough of a proof-of-concept for #CVE-2022-21882 gives the chance for a deep dive into the inner structure of #Win32k and exactly how CVE-2022-21882 and CVE-2021-1732 operate. bit.ly/43Lnqha

CVE-2016-0165 Microsoft Win32k Privilege Escalation Vulnerability learn.microsoft.com/en-us/security… #Microsoft #Win32k #cisabot
Unit 42's newest research is an evaluation of two specific #Win32k PoC exploits. CVE-2021-1732 is analyzed with a proof of concept walkthrough and its similarities to CVE-2022-21882 . #MicrosoftWindows sprou.tt/137SFTeByZQ
unit42.paloaltonetworks.com
Inside Win32k Exploitation: Analysis of CVE-2022-21882 and CVE-2021-1732
We analyze two Win32k proof-of-concept exploits, CVE-2021-1732 and CVE-2022-21882. These data-only attacks target the Win32k kernel.
An analysis of the Win32 #API that creates #GUI objects such as windows and menus begins with the background of #Win32k. Then @Unit42_intel dives into callbacks and how they function, and why these callbacks can be exploited by TAs. #MicrosoftWindows sprou.tt/1LJYjQ29D4x
unit42.paloaltonetworks.com
Inside Win32k Exploitation: Background on Implementations of Win32k and Exploitation Methodologies
We analyze Microsoft Windows' GUI, how it functions and some of the history of research into its exploitation.
An analysis of the Win32 #API that creates #GUI objects such as windows and menus begins with the background of #Win32k. Then Unit 42 researchers dive into callbacks and how they function, and why these callbacks can be exploited by TAs. #MicrosoftWindows sprou.tt/1LJYjQ29D4x
unit42.paloaltonetworks.com
Inside Win32k Exploitation: Background on Implementations of Win32k and Exploitation Methodologies
We analyze Microsoft Windows' GUI, how it functions and some of the history of research into its exploitation.
An analysis of the Win32 #API that creates #GUI objects such as windows and menus begins with the background of #Win32k. Then Unit 42 researchers dive into callbacks and how they function, and why these callbacks can be exploited by TAs #MicrosoftWindows sprou.tt/1LJYjQ29D4x
unit42.paloaltonetworks.com
Inside Win32k Exploitation: Background on Implementations of Win32k and Exploitation Methodologies
We analyze Microsoft Windows' GUI, how it functions and some of the history of research into its exploitation.
An analysis of the Win32 #API that creates #GUI objects such as windows and menus begins with the background of #Win32k. From there, we dive into callbacks and how they function, and why these callbacks can be exploited by threat actors. #MicrosoftWindows bit.ly/3Jffxsb

Online muggers make serious moves on unpatched #Microsoft bugs theregister.com/2023/06/09/mic… Fixes available for 2 flaws under attack. #Win32k #CVE-2023-29336 & #VisualStudio CVE-2023-28299 #CyberSecurity #InfoSec #Vulnerability #BugFix
⚠️⚡🌐 #CyberSecurity Update: Unpatched Microsoft systems under attack! Flaws in #Win32k subsystem (CVE-2023-29336) & Visual Studio (CVE-2023-28299) exploited by attackers. How they gain control: 1️⃣ Win32k: Exploiting the flaw to gain system privileges, taking control of the…

Win32k that we lost. In details writeup about CVE-2023-29336 (written by Sergey Tarasov @immortalp0ny) : deadprogrammers.club/posts/in-detai… #win32k #vulnerability #exploitation #exploit #informationsecurity

This month's #Microsoft Patch Tuesday (again) addresses: Two "important" #Win32k Elevation of Privilege bugs under active attack

An analysis of the Win32 #API that creates #GUI objects such as windows and menus begins with the background of #Win32k. From there, we dive into callbacks and how they function, and why these callbacks can be exploited by threat actors. #MicrosoftWindows bit.ly/3Jffxsb

In the 2023 OpenTRS #3 📡 CTF Team GYG and Theori VR team explores #MacOS, #Win32k vulnerabilities. And our CTO @andrewwesie takes you through #Web3 ZK proof-based @RelicProtocol On July 6th, live on theori.tv This seminar will be conducted in English.

A step-by-step walkthrough of a proof-of-concept for #CVE-2022-21882 gives the chance for a deep dive into the inner structure of #Win32k and exactly how CVE-2022-21882 and CVE-2021-1732 operate. bit.ly/43Lnqha

Our newest research is an evaluation of two specific #Win32k PoC exploits. CVE-2021-1732 is analyzed with a proof of concept walkthrough and its similarities to CVE-2022-21882. #MicrosoftWindows bit.ly/43Lnqha

⚠️ #MysterySnail progresse via une vulnérabilité zero-day. Nos technologies de sécurité ont détecté l’exploitation d’une vulnérabilité jusqu’alors inconnue dans le pilote #Win32k. Pour en savoir plus 👉 kas.pr/tbg2

📌#Win32k Smash the Ref - New Bug Class and #Exploitation Techniques by Gil Dabah ⚙️[SRC]:github.com/gdabah/win32k-… 📕[PDF]:github.com/gdabah/win32k-… 📝[BLOG]:ragestorm.net/blogs/?p=502 #windows #Security
![ntlmrelay's tweet image. 📌#Win32k Smash the Ref - New Bug Class and #Exploitation Techniques by Gil Dabah
⚙️[SRC]:github.com/gdabah/win32k-…
📕[PDF]:github.com/gdabah/win32k-…
📝[BLOG]:ragestorm.net/blogs/?p=502
#windows #Security](https://pbs.twimg.com/media/EUrhW2zUMAIEKJW.png)
CVE-2015-1701 / MS15-051 source and demo. Test successfull on win7 #win32k #lpe #apt #infosec github.com/hfiref0x/CVE-2…

‘#Zombie’ #Windows #win32k bug reanimated by researcher: Dozens of bugs in a core #Windows API could… dlvr.it/RTR03q @RedSeal_co

#CiberAlertas_EcuCERT vulnerabilidad de @Microsoft @Windows, permite a un atacante local autenticado, obtener privilegios de administrador a través de una vulnerabilidad en el controlador #Win32k.sys. Detalles al respecto en: ecucert.gob.ec/alertas/

#Microsoft #Win32k: rilasciato un PoC per lo sfruttamento della CVE-2022-21882, che potrebbe permettere l’elevazione dei privilegi sui sistemi interessati Rischio: 🟠 Tipologia: Privilege Escalation 🔗 csirt.gov.it/contenuti/win3… 🔄 Aggiornamenti disponibili 🔄

⚠️ Pour ceux qui ont raté l'info... #Microsoft a sorti un correctif pour lutter contre un #0day #Win32k 🔥 darkreading.com/vulnerabilitie… ➡️ CVE-2021-1732, exécution de code avec élévation de privilèges 💣 Exploitations détectées en Chine 🇨🇳 A vos marques, prêts... patchez !!

⚠️ALERTA ⚠️ #Vulnerabilidad #Win32k Compartimos un informe con las últimas alertas críticas detectadas por nuestro #CSVD: boletín de #ciberseguridad, Vulnerabilidad de elevación de privilegios de Win32k. hubs.ly/Q0157V2v0

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Saturday 23.6K posts
- 2. #SaturdayVibes 3,646 posts
- 3. #MeAndTheeSeriesEP1 452K posts
- 4. PONDPHUWIN AT MAT PREMIERE 381K posts
- 5. #askdave N/A
- 6. Draymond 23.9K posts
- 7. Massie 68.4K posts
- 8. #saturdaymorning 1,655 posts
- 9. Caturday 5,235 posts
- 10. Wemby 46.9K posts
- 11. #Truedtac5GXWilliamEst 215K posts
- 12. Marjorie Taylor Greene 61.6K posts
- 13. Steph 87.4K posts
- 14. FAYE ATTENDS SILHOUETTE EFW 176K posts
- 15. IT'S GAME DAY 3,859 posts
- 16. Bubba 64.6K posts
- 17. Michelle 59.5K posts
- 18. Spurs 36.3K posts
- 19. Charlie Brown 2,970 posts
- 20. Warriors 62.6K posts































