Bill Tech
@_Bill_tech
Tech Enthusiast | Coding Ninja | cybersecurity Expert |
You might like
Your account has been hacked? Your account got disabled or terminated for no reason? You have problem getting into your account? You have come to the right page, I’ll help you resolve any kind of issues you may have with your account in no time! Your satisfaction is my priority
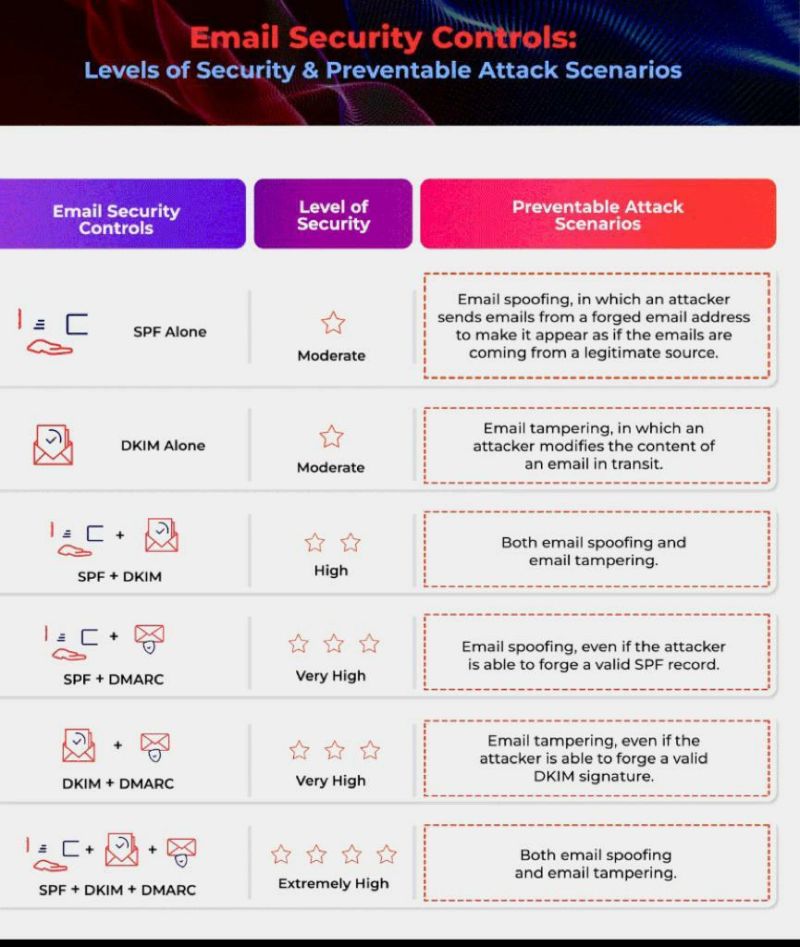
Email Security Controls #infosec #cybersecurity #cybersecuritytips #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips
It is important to always start from the basics

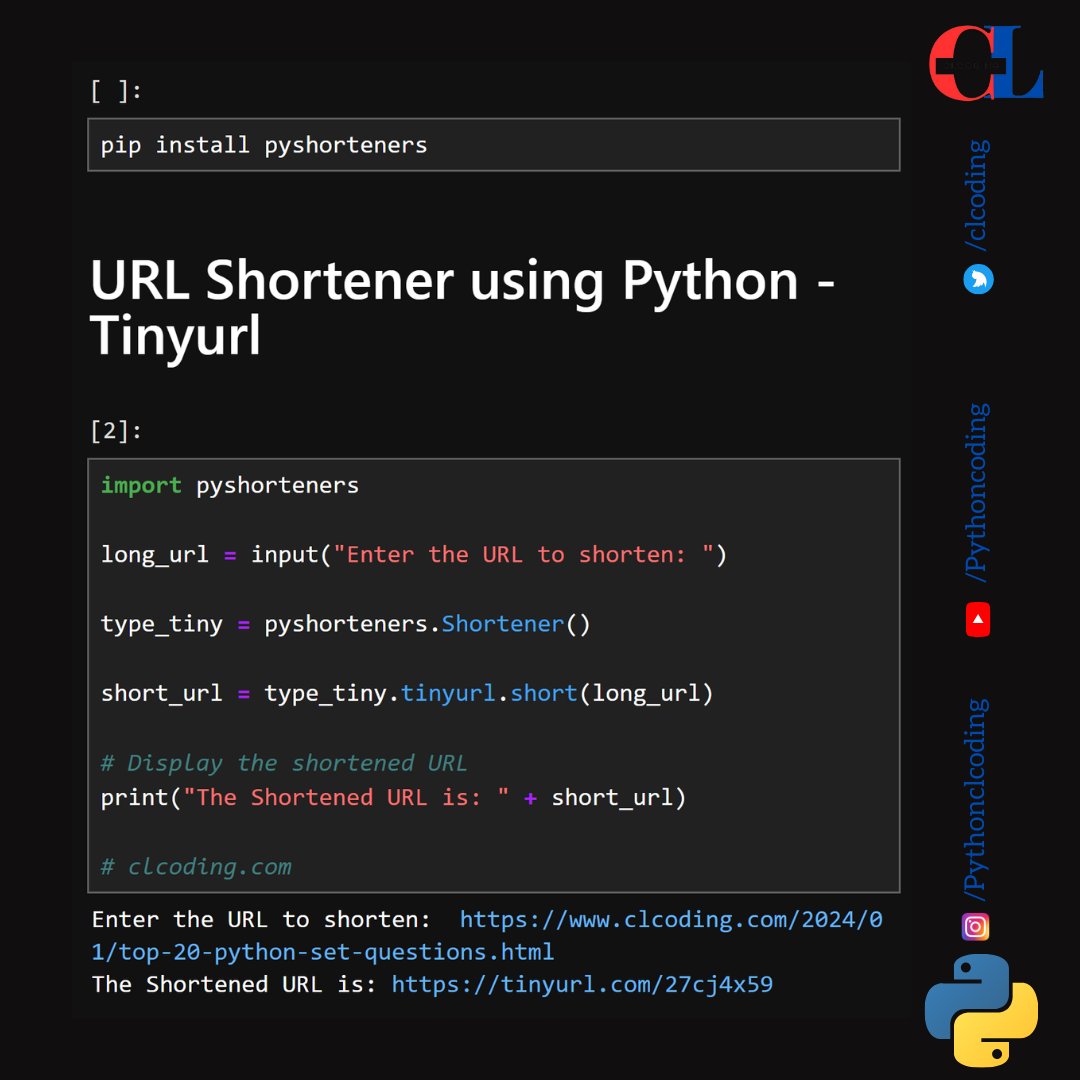
URL Shortener using Python - Tinyurl
This is how a Cybercriminal exploits phone calls to steal Data/OTP using IVR.
Now I don't mean to spread any o' dat cheesy FUD and "correlation is not causation" grumble grumble... but lines were certainly moving over on downdetector.com 😅

Fairly certain this has taken down multiple 911 centers in the US based on the timing 😬
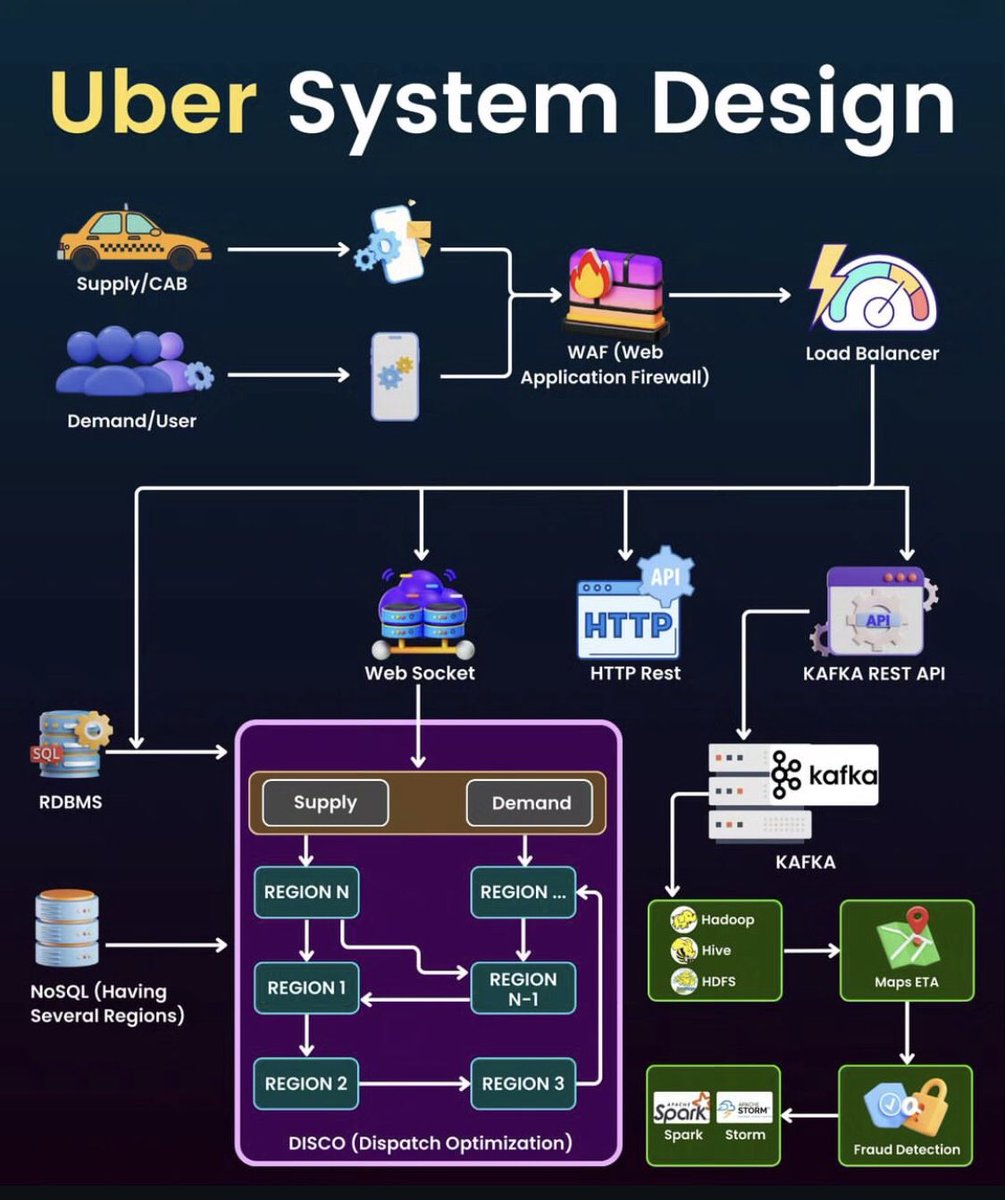
Uber system design
Networking Protocols

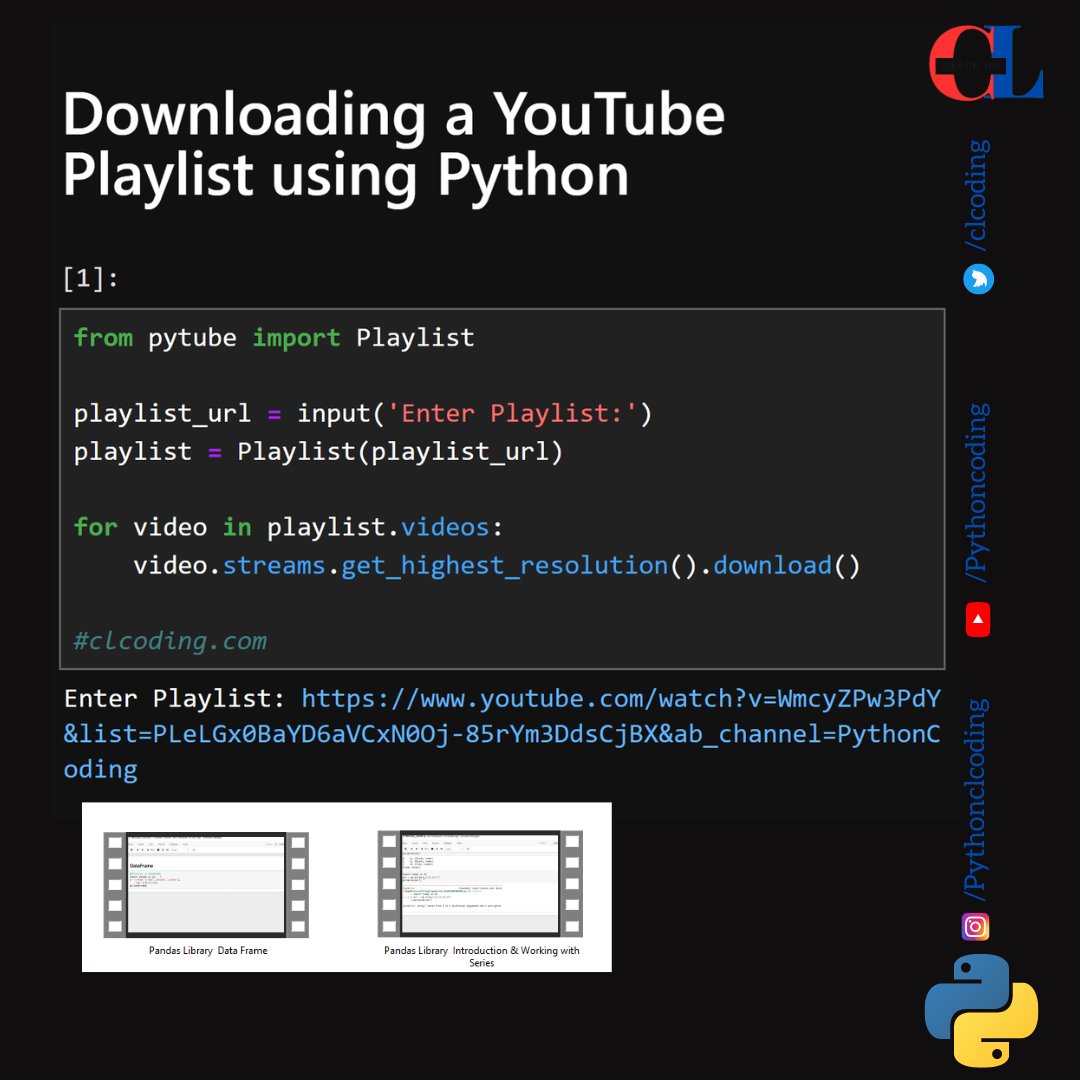
Downloading a YouTube Playlist using Python Code: clcoding.com/2024/06/downlo…
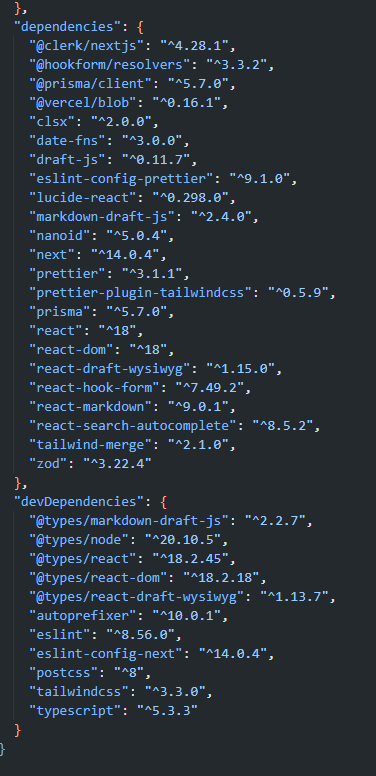
Why has create-next-app brought back the devDependencies separation? I thought it wasn't necessary in Next.js. Now it's not clear to me if I should separate dev dependencies or not.
challenges grow progressively complex, necessitating coding solutions due to large inputs Each challenge involves unique problems. For example navigating grids with blocked and free fields, prompting questions like the minimum steps to reach a goal.

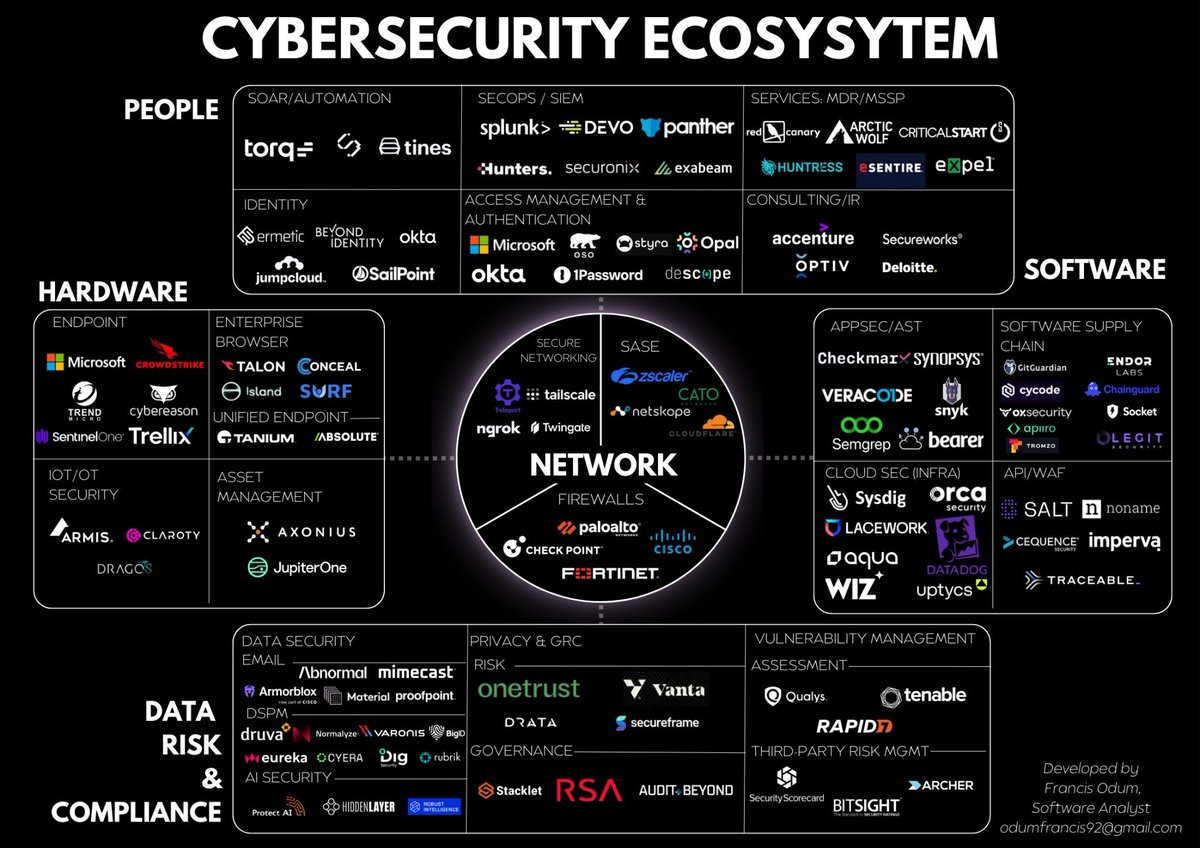
Cyber Security Ecosystem #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips
Learn how Corellium's magic can be used to practice and develop exploits without relying on vulnerabilities. ✨ corellium.com/blog/exploring… #unix #ios #hooking
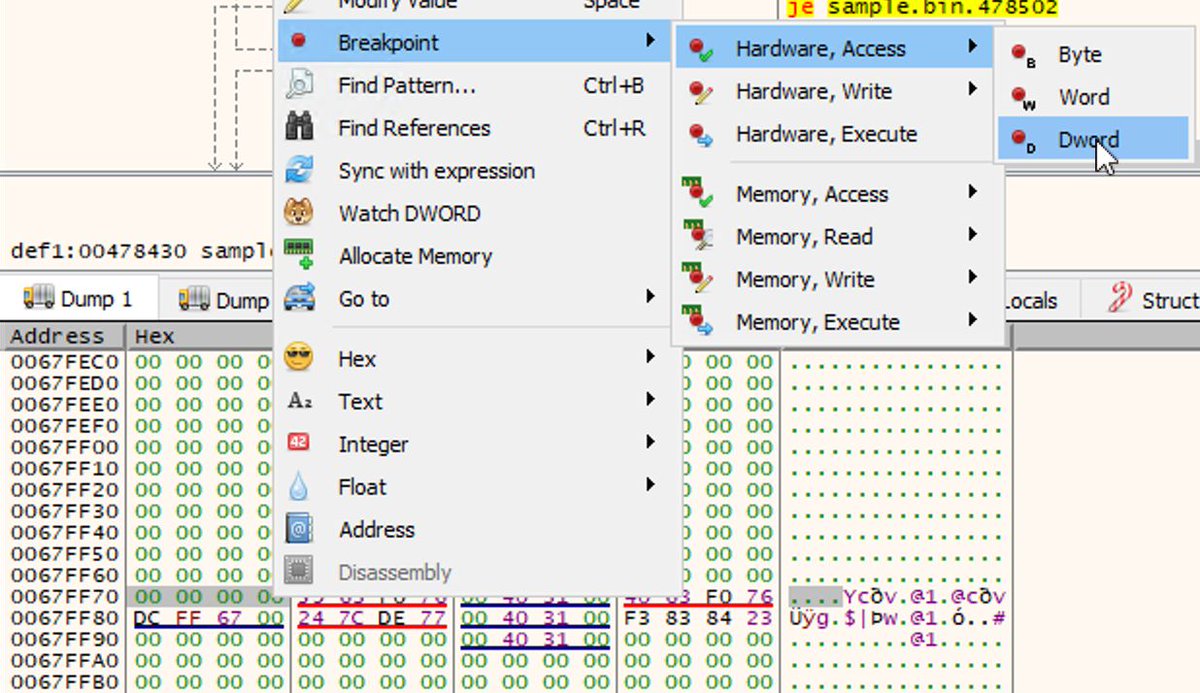
RE tip of the day: When performing manual unpacking, to set a breakpoint at ESP-4, use hardware breakpoint on access, not memory breakpoint. Memory breakpoints are imprecise as they modify protection flags for at least one memory page. #cybersecurity #malware #reverseengineering
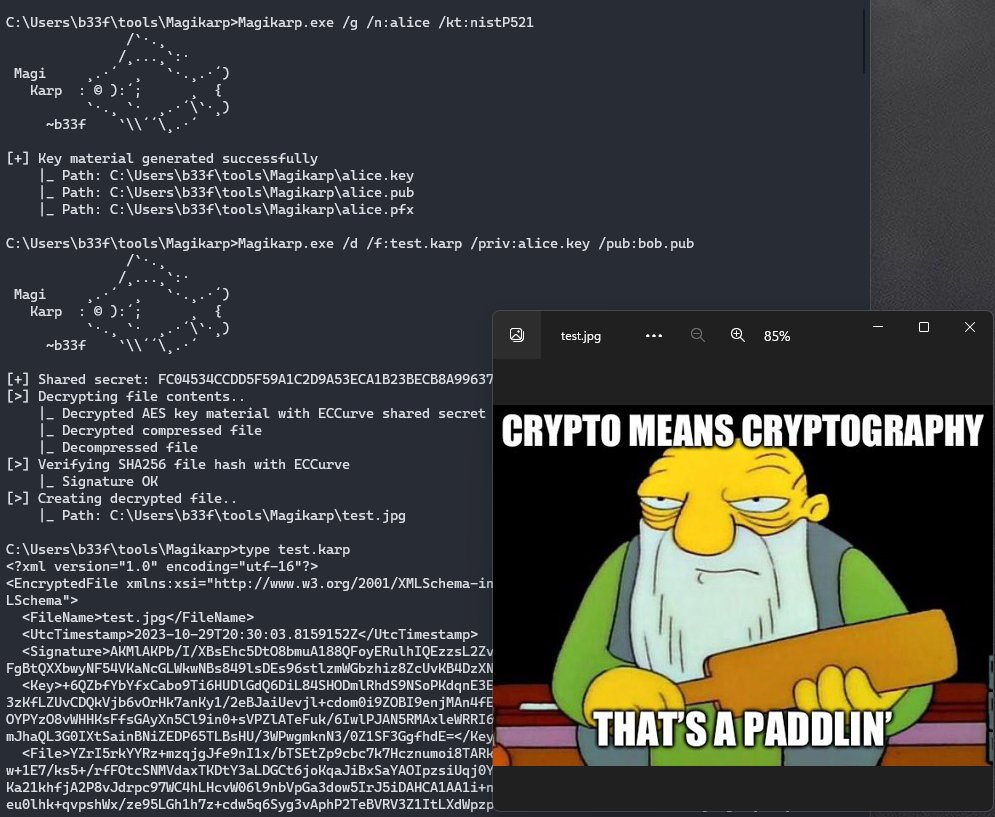
Magikarp A cryptographic command-line utility designed for secure file operations using Elliptic Curve Cryptography (ECC) github.com/FuzzySecurity/… #cybersecurity #infosec #pentesting #redteam #bugbounty
United States Trends
- 1. Tom Homan N/A
- 2. #OlandriaxRahulMishra N/A
- 3. #RahulMishraCouture N/A
- 4. Good Monday N/A
- 5. #MondayMotivation N/A
- 6. Ran Gvili N/A
- 7. #VenezuelaEsAmorYPaz N/A
- 8. $CRWV N/A
- 9. #PMSSuperBowlSZN N/A
- 10. CoreWeave N/A
- 11. Roval N/A
- 12. AirTag N/A
- 13. Scheelhaase N/A
- 14. Signal N/A
- 15. Udinski N/A
- 16. Cramer N/A
- 17. Tomodachi Life N/A
- 18. Browns HC N/A
- 19. IONQ N/A
- 20. $SKYT N/A
Something went wrong.
Something went wrong.