
_D4Z3N_
@_D4z3n_
Malware Researcher 🙈
Tal vez te guste
#AllYourTorrentsBelongToUs #malware #torrent All Your Torrents Belong To Us reversingminds-blog.logdown.com/posts/7821320-…

Microsoft Incident Response – Detection and Response Team (DART) uncovered SesameOp, a new backdoor that uses the OpenAI Assistants API for C2. DART shared the findings with OpenAI, who identified and disabled an API key and associated account. msft.it/6012tGbpm SesameOp…
A new approach to static analysis with AI that turns days of research into hours. No MCP or live IDA required. Using GPT-5, we completely cracked XLoader v8, one of the most challenging malware families to analyze. #XLoader #MalwareAnalysis #AI research.checkpoint.com/2025/generativ…
This article explores a novel attack technique that combines Ghost SPNs and Kerberos reflection to elevate privileges on SMB servers, highlighting a critical gap in traditional detection methods. It details how attackers can exploit stale or misconfigured Service Principal Names…
new ppl here for malware content, check out my github page. c2, process injections, syscall libraries, etc... varying levels, as i've shared materials along my whole journey. lots new to drop still github.com/teach2breach
Great research from Mandiant, learned a lot from their analysis. cloud.google.com/blog/topics/th… Found more trojanized JavaScripts communicating with the same transaction hash. Sometimes it’s shocking how well DPRK actors understand blockchain mechanics and weaponize them.…
We first introduced the term “Premier Pass” during my talk at @pivot_con — describing a trend of advanced collaboration among China-aligned APT groups like Earth Estries & Earth Naga. Today, we published a blog post that explores the concept in depth. trendmicro.com/en_us/research…
#ESETresearch discovered a new wave of the well-known 🇰🇵 Lazarus campaign Operation DreamJob, now targeting the drone industry. @pkalnai @alexis_rapin welivesecurity.com/en/eset-resear… 1/9
#ElasticSecurityLabs joins forces with @tamusystem and discloses TOLLBOOTH, an IIS module used for SEO abuse that relies on publicly exposed ASP. NET machine keys: go.es.io/3L68p57
Unit 42 shares a step-by-step guide to cloud incident response. Learn how cloud investigations differ from traditional incidents, focusing on identities, misconfigurations and service interactions. bit.ly/46JEbxn

Elastic Security Labs introduces nightMARE, a versatile Python library for malware analysis, featuring static analysis tools and configuration extractors for various malware families, now available in version 0.16. #MalwareAnalysis #PythonLibrary elastic.co/security-labs/…
Unit 42 recently responded to a ransomware incident involving BlackSuit at a manufacturing client. This event illustrates how a single compromised VPN credential, obtained through a vishing attack, can lead to significant operational impact. bit.ly/42DUrO3

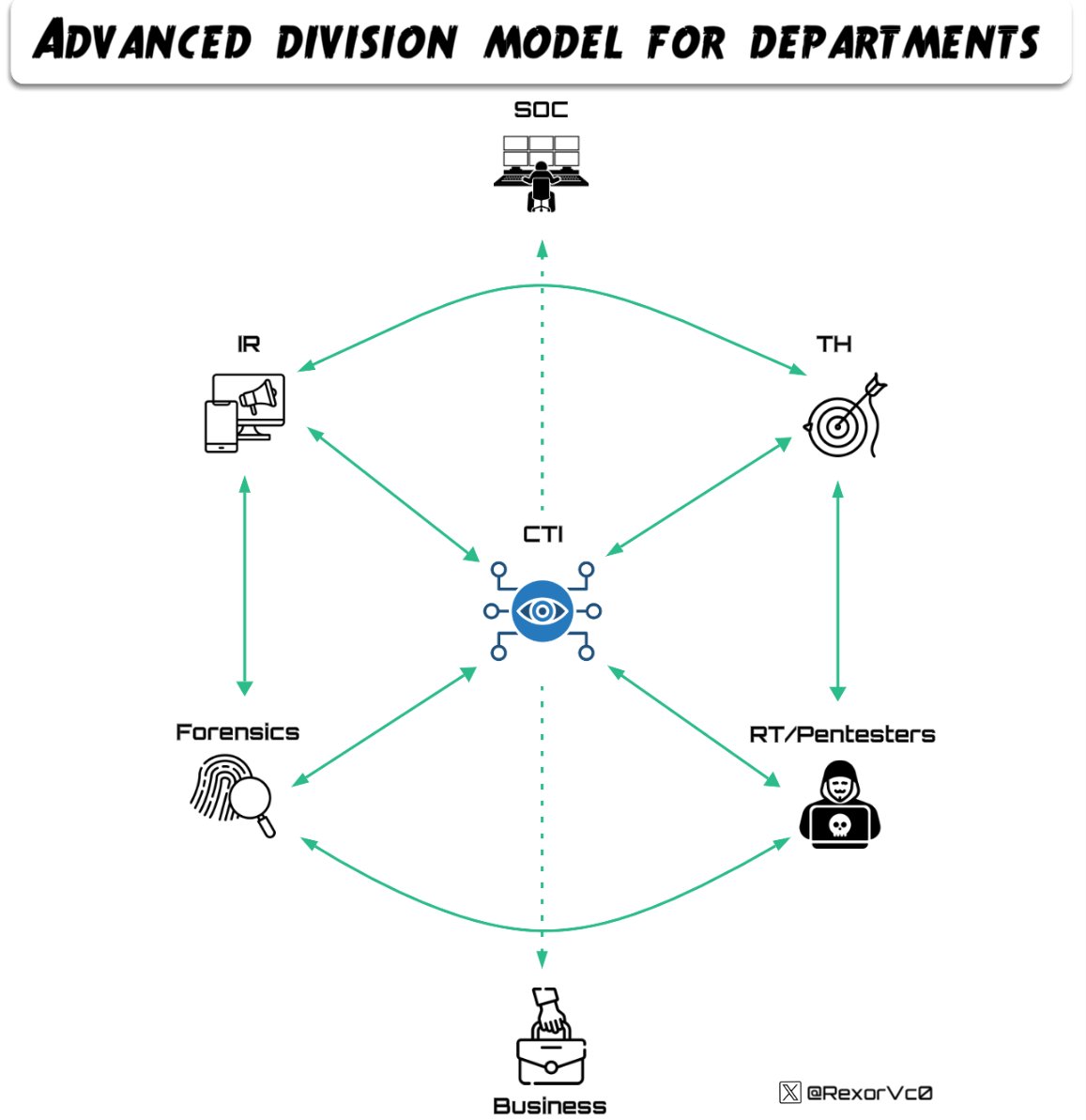
📡New blog about my talk "CTI: The Dark Cloak" where we explore how #intel teams collaborate to tackle real #TA 🕵️♂️ We analyze threats from #CTI, assisting other teams such as #TH and #DFIR, extracting max value from every piece of info 🔗Blogpost: rexorvc0.com #RE



Unit 42 presents a proof of concept on indirect prompt injection in AI agents. This method can store malicious instructions in an agent's memory, affecting future interactions. bit.ly/3L2ppcs
We at @emproofsecurity open-sourced a free firmware reverse engineering workshop for self-study. Topics: ELF analysis, cracking, malware triage, embedded-Linux, bare-metal, crypto-key extraction, anti-analysis. Docker setup and solutions included. github.com/emproof-com/wo…
🚀 We are proud to announce the availability of Threatray Release v2.1, bringing an exciting set of additions and improvements to the platform. 🤝 We’ve partnered with @nextronsystems, a pioneer in YARA and Sigma rule detection, to bring their industry-leading detection…

Relocatable - Write C-code that will be directly compiled into raw shellcode, which can be loaded into any process without the need for tools such as Donut or sRDI github.com/tijme/relocata…
Ever wondered how Process Explorer builds the process tree? I wrote a guide on how to code your own in C++. We cover PID reuse, parent vs. creator, recursion, and more. Read it here: trainsec.net/library/window…
Nice in-depth research! We took a look at the same loader a while back and shared a YARA rule to track it: threatray.com/blog/a-net-mul…
I updated the #Rhadamanthys custom format converter (for XS modules), to support the latest version (0.9.x): github.com/hasherezade/hi…
#ESETresearch has mapped the labyrinth of #AsyncRAT forks, identifying the most prevalent versions of this open-source malware. While some variants are mere curiosities, others pose a more tenacious threat. welivesecurity.com/en/eset-resear… 1/7
United States Tendencias
- 1. Lakers 78.3K posts
- 2. #Talus_Labs N/A
- 3. Luka 69.6K posts
- 4. Good Thursday 20.2K posts
- 5. Wemby 26.9K posts
- 6. Marcus Smart 6,196 posts
- 7. #LakeShow 5,720 posts
- 8. #AmphoreusStamp 7,175 posts
- 9. Blazers 8,880 posts
- 10. Russ 11K posts
- 11. Ayton 16.5K posts
- 12. Will Richard 6,602 posts
- 13. #RipCity N/A
- 14. #dispatch 64.7K posts
- 15. Unplanned 5,709 posts
- 16. Podz 2,432 posts
- 17. Nico Harrison 1,998 posts
- 18. Klay 8,547 posts
- 19. Shroud 5,684 posts
- 20. Deni 6,295 posts
Tal vez te guste
-
 d00rt
d00rt
@D00RT_RM -
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Valthek
Valthek
@ValthekOn -
 CAPE Sandbox
CAPE Sandbox
@CapeSandbox -
 S2
S2
@sisoma2 -
 Itay Cohen 🌱
Itay Cohen 🌱
@megabeets_ -
 Evilcry_
Evilcry_
@Blackmond_ -
 Herbie Zimmerman
Herbie Zimmerman
@HerbieZimmerman -
 J.A.R.V.I.S
J.A.R.V.I.S
@peppermalware -
 Philippe Lagadec @ hack.lu
Philippe Lagadec @ hack.lu
@decalage2 -
 void m4p()
void m4p()
@voidm4p -
 Catch all the Malwa
Catch all the Malwa
@MalwareCantFly -
 Drunk Binary
Drunk Binary
@DrunkBinary -
 Antelox
Antelox
@Antelox -
 sean
sean
@seanmw
Something went wrong.
Something went wrong.




















































































































































