brutexploiter
@brutexploiter
Security Researcher | Bug Bounty Hunter | Mechanical Engineer
You might like
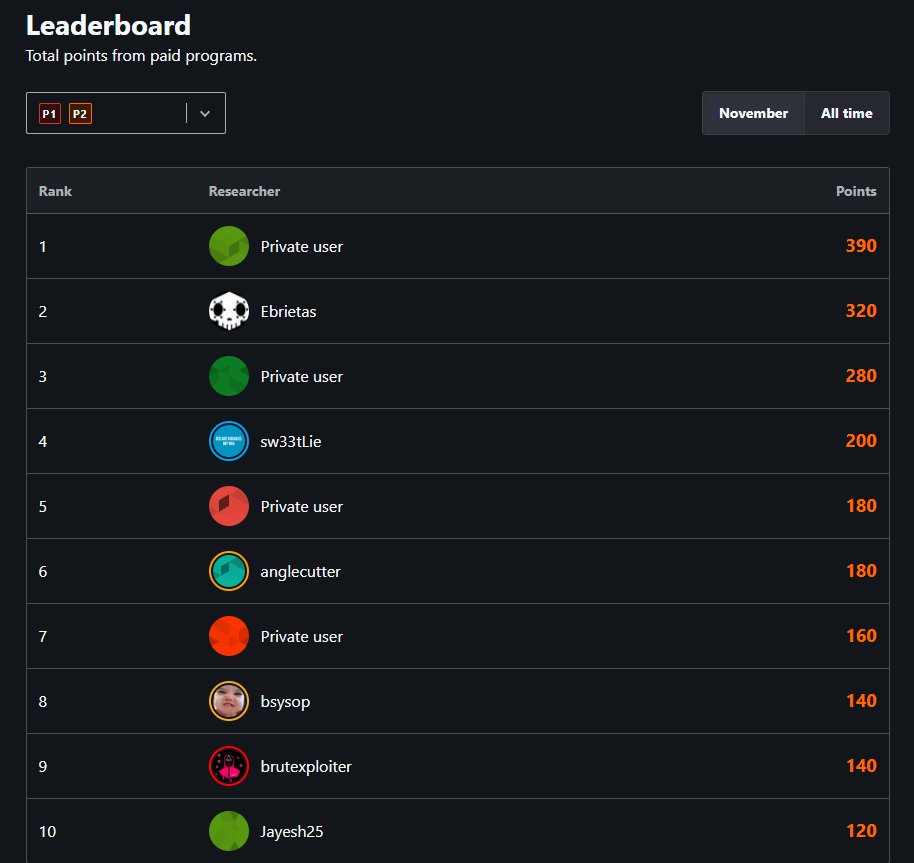
Secured 9th place on the November P1-P2 leaderboard at @Bugcrowd! 🎯 A huge thanks to @_zwink, @zseano, @NahamSec, @Jhaddix, @ctbbpodcast and @GodfatherOrwa for sharing invaluable knowledge 🙏 #ittakesacrowd #BugBounty #bugcrowd #CyberSecurity
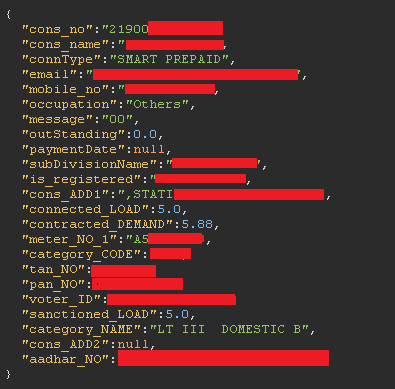
I just published IDOR + Account Takeover: How I Secured Personal Information (PII) of 5.17M Electricity Consumers Link: infosecwriteups.com/idor-account-t… #bugbounty #cybersecurity #infosec #readteam #websecurity #cloud #india #pentesting
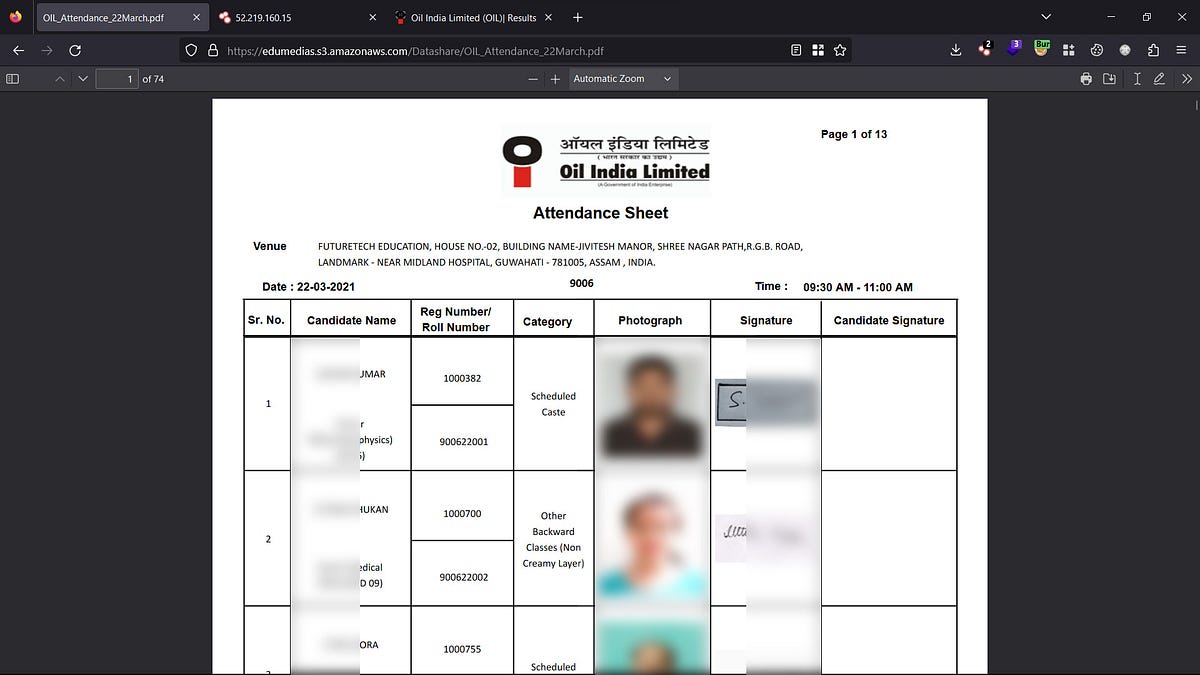
I published my first write-up. Please give it a read. Kudos to the @OilIndiaLimited team for effectively mitigating the identified vulnerability. Link: infosecwriteups.com/aws-s3-bucket-… #BugBounty #Cybersecurity #infosec #readteam #websecurity #CloudComputing #india #Pentesting
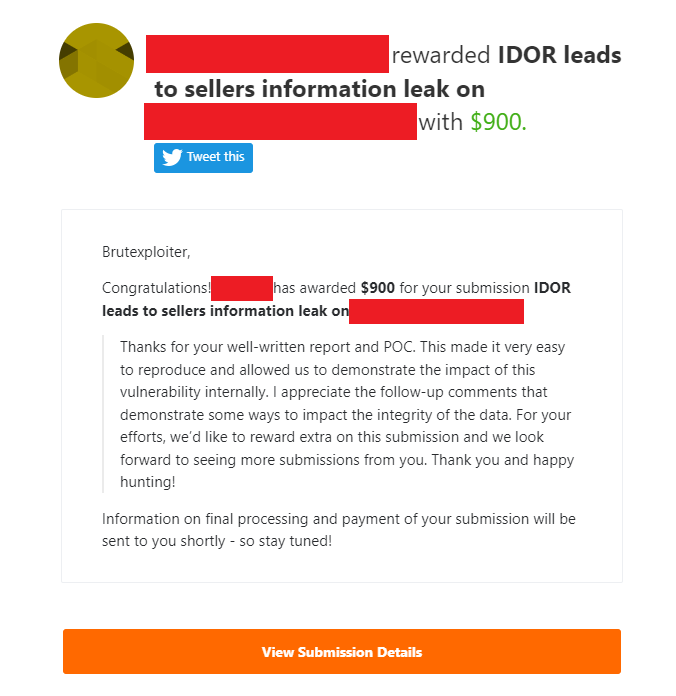
I earned $900 for my submission on @bugcrowd It's truly motivating to receive such positive feedback from the customer team, and it gives motivation to work hard. #ItTakesACrowd #bugbounty #bugcrowd
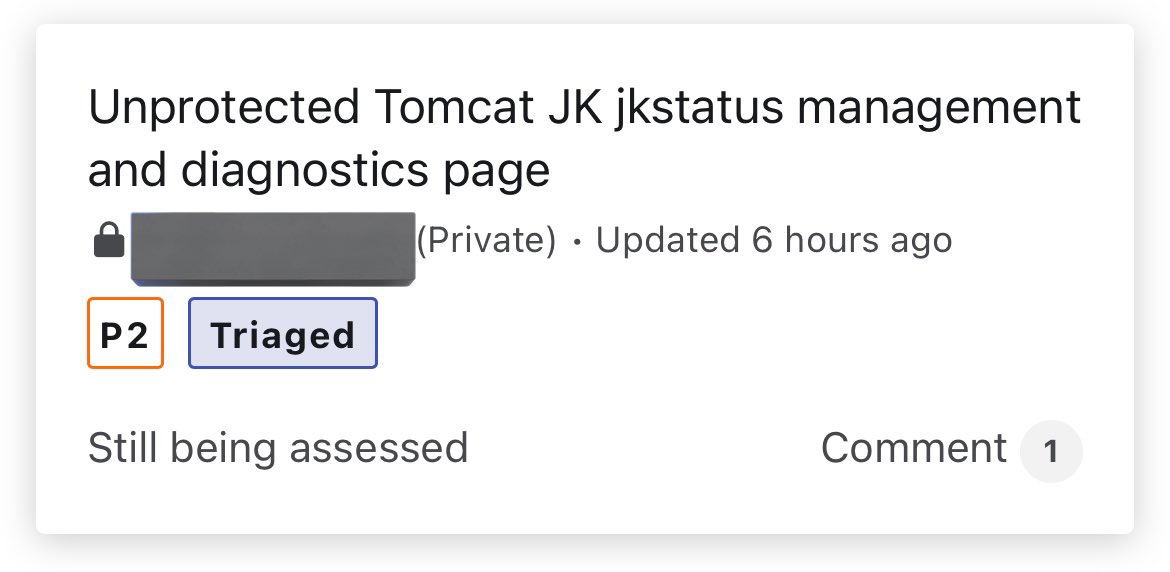
Ok, let’s discuss this 1- fuzz website 2- found this path /jk_status?cmd=dump = dump data 3- search more about this misconfigure 4- found /jk_status?opt=0 = read and write privilege #BugBounty #bugbountytips
Today Finally received my first valid bug &Bounty on @Bugcrowd .Thank you to the community for giving knowledge and mentors who always guide throgh their knowledge @zseano @theXSSrat @_zwink @NahamSec @codingo_ @InsiderPhD @GodfatherOrwa #bugbounty #bugcrowd #ItTakesACrowd
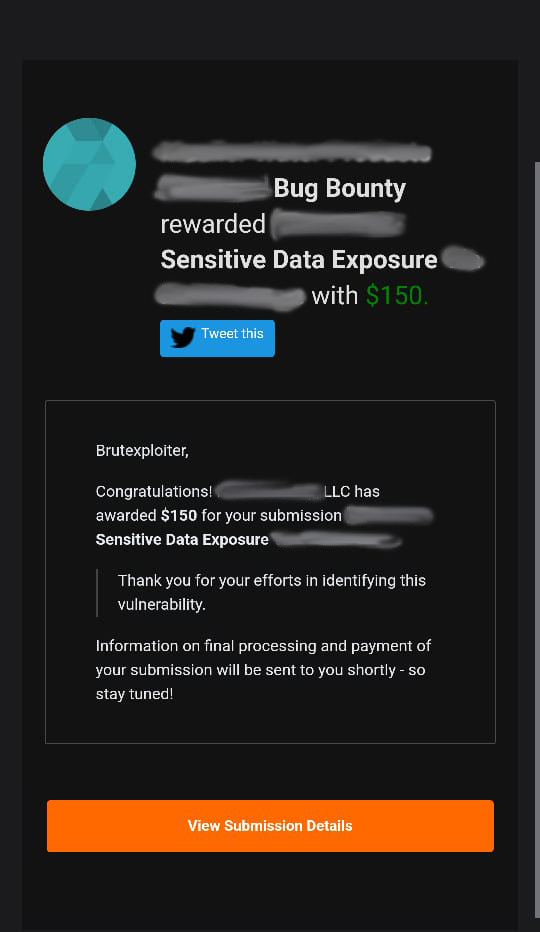
I'm uncomfortable tweeting stuff like this out, but... I found a critical vulnerability in @opensea this weekend and reported it through @Hacker0x01. They fixed the issue within 3 hours of reporting and I just got this notification👏🫢
SSRF Story | Scan The Network 1. Found SSRF and get Cloud Metadata. 2. Common high risk with disclosed cloud metadata is about security credential, but not found at this point :( 3. Found the instance public IP in latest/meta-data/public-ipv4, access the IP and got 404 response



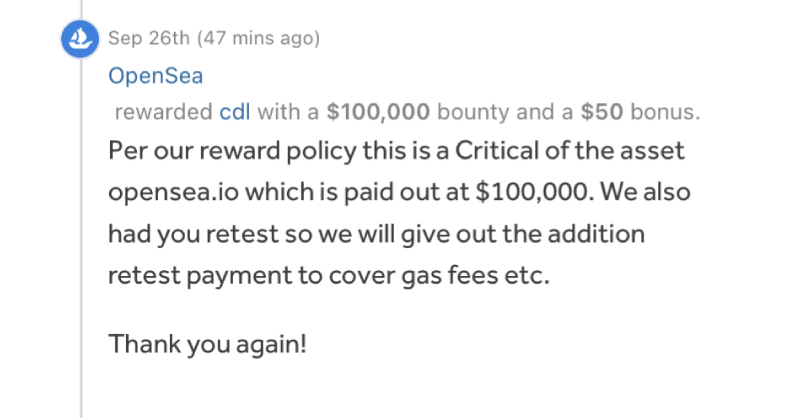
It's been a little over 3 weeks since Google randomly sent me $249,999 and I still haven't heard anything on the support ticket. Is there any way we could get in touch @Google? (it's OK if you don't want it back...)
Thread about hunting on the main application 🧵 1. Check the login process - Do they allow signup with email or Google etc - Do they allow you to signup with the @company email - what is the content-type of the signup/login page - when you enter valid cred, on which page you
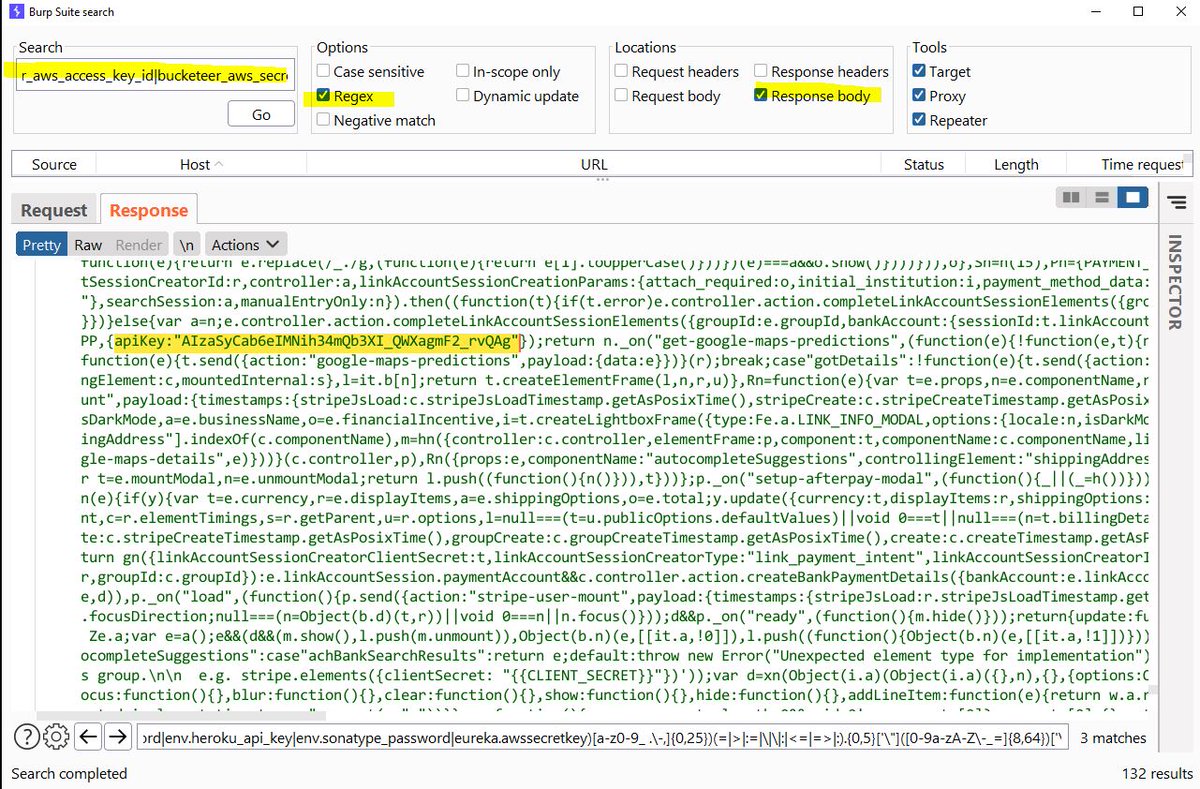
Search for all leaked keys/secrets using one regex! regex: gist.github.com/h4x0r-dz/be69c… #BugBounty #bugbountytip
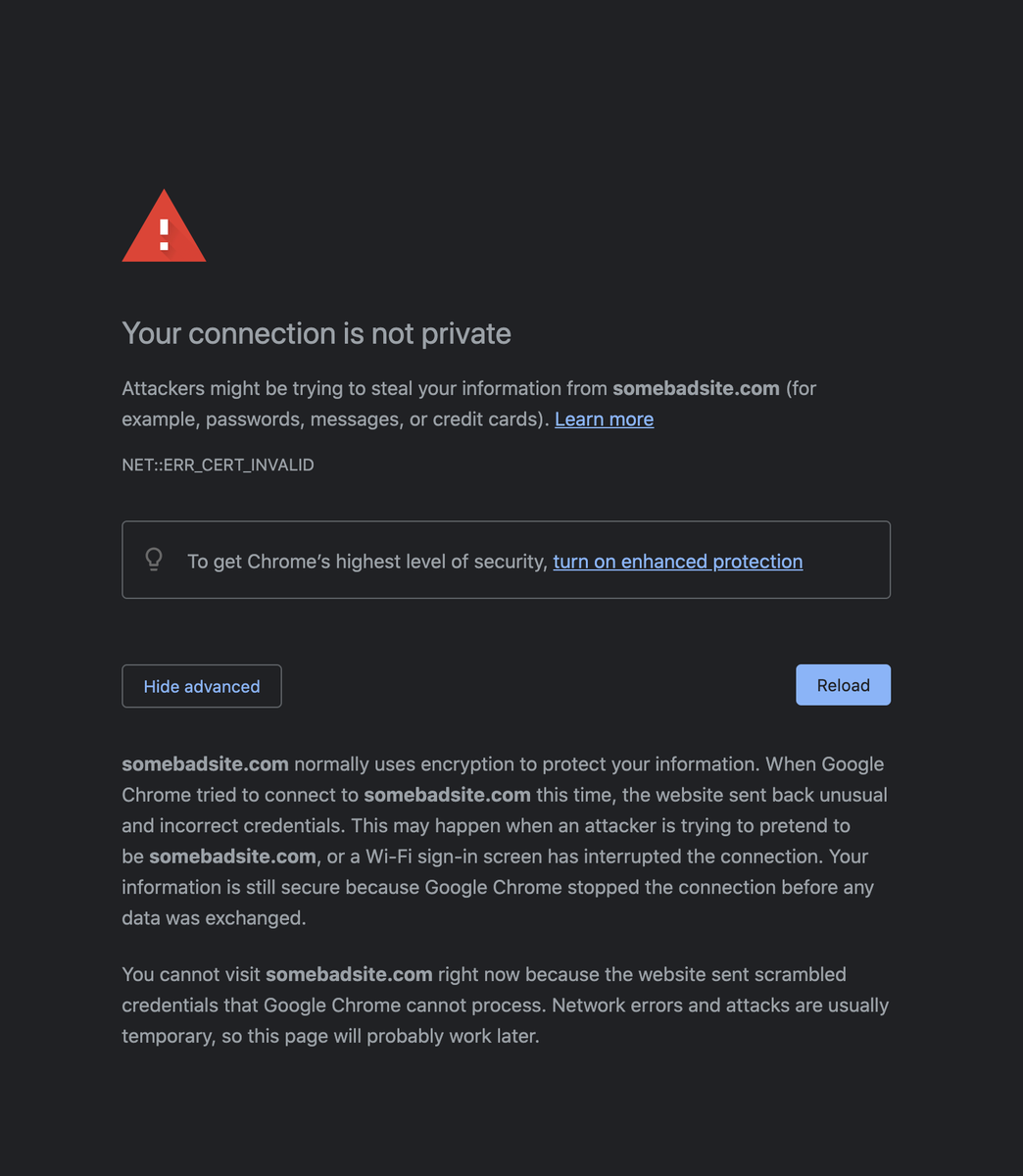
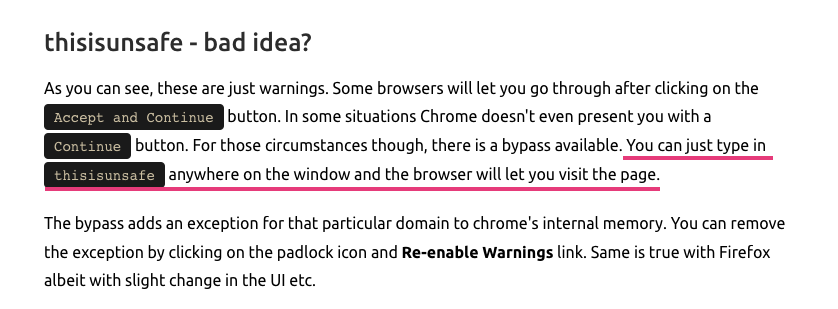
TIL whenever you see an SSL certificate error and the browser doesn't let you continue - even on your own risk, you can just type 'thisisunsafe' to bypass the protection cybercafe.dev/thisisunsafe-b…
I drew this bird with mathematical equations.

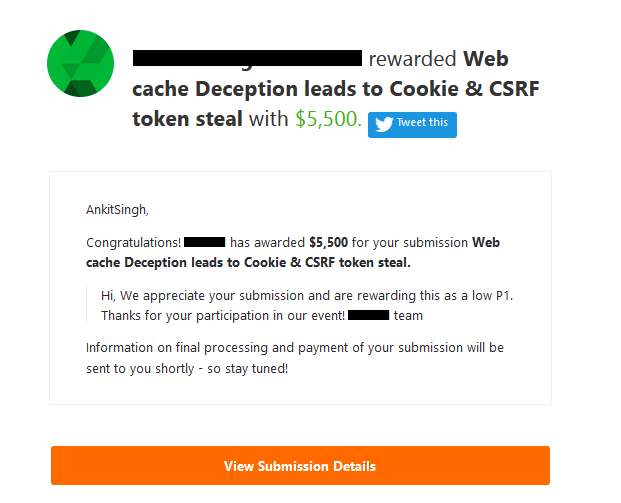
I earned $5,500 for my bug on @bugcrowd This was one of the most unique "Web Cache Deception" I found on one of the oldest public program which led me to a "Mass Account Takeover with ZERO user interaction" scenario. READ the thread.. 1/7 #cybersecurity #infosec #bugbountytips
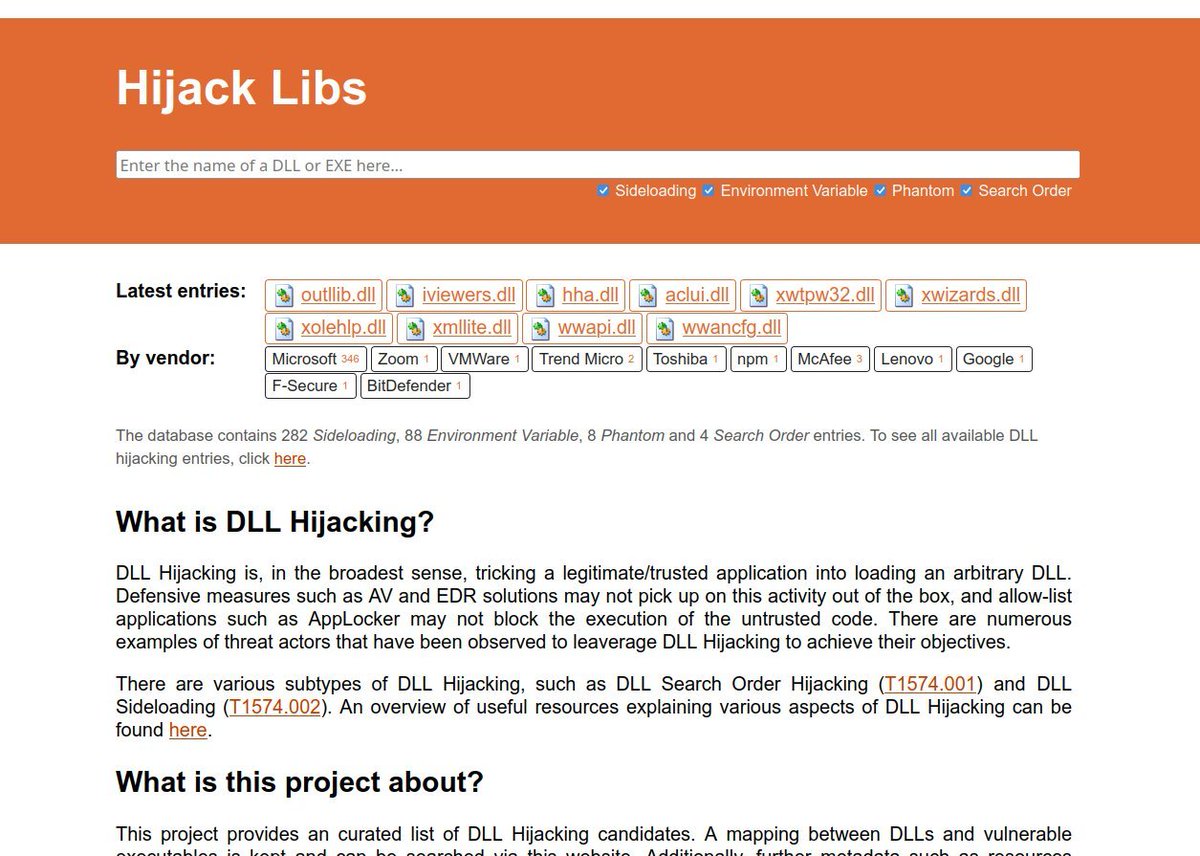
Today I'm launching #HijackLibs, an open-source, community-driven project tracking DLL Hijacking opportunities in in Windows 🌍 LIVE on hijacklibs.net 👈 🆕 Currently comprising over 350 unique DLLs that can be targeted 🤝 Contribute via github.com/wietze/hijackl…
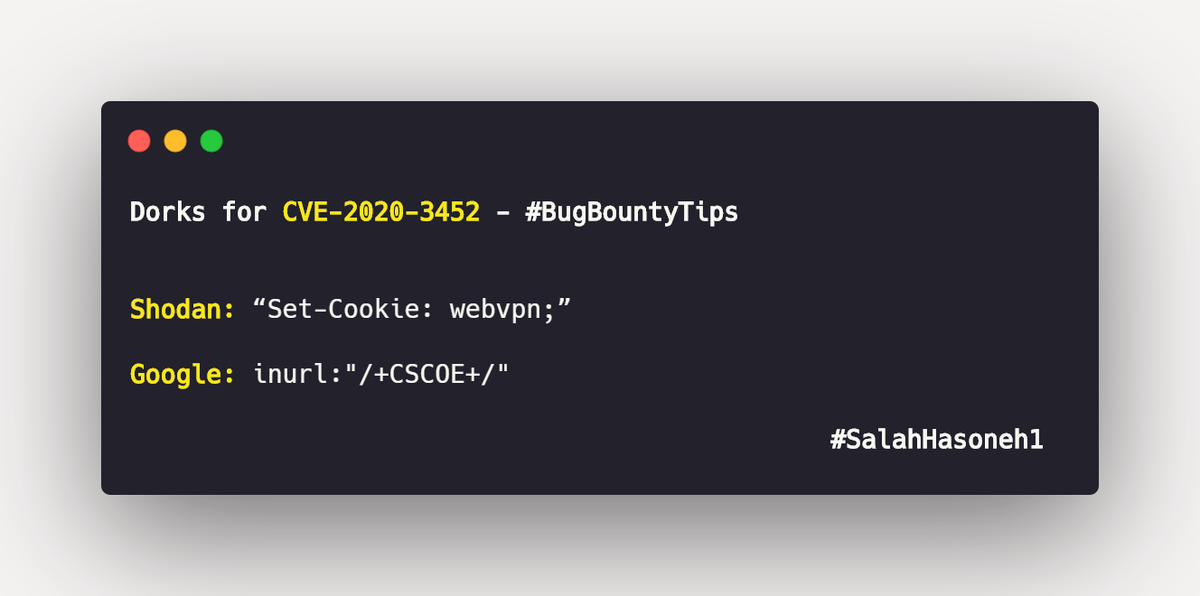
🛡️ Dorks for CVE-2020-3452 🛡️ #cybersecurity #infosec #ethicalhacking #bugbounty #bugbountytips #bugbountytip #hackerone
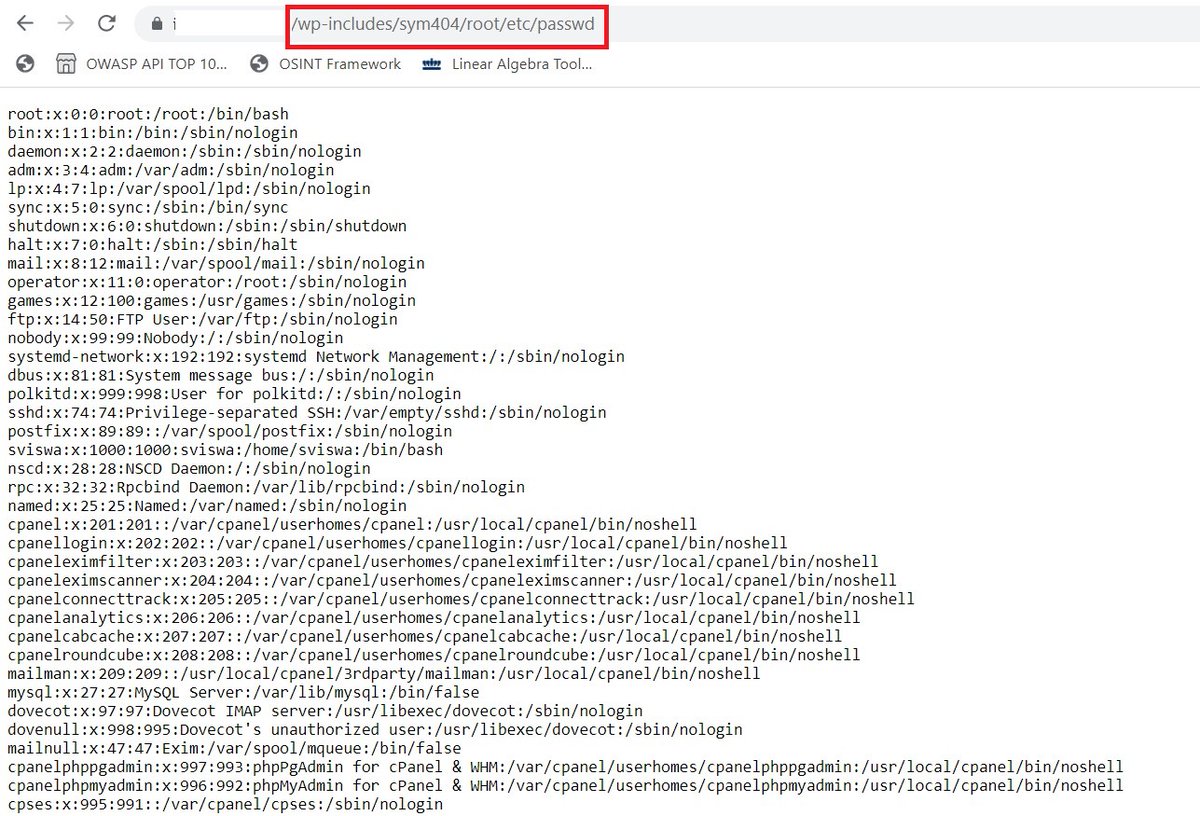
WordPress Never Fails to Surprise !!🤩🤩 A Low hanging Bug with High Impact. You can access the whole disk on the Browser and see sensitive files. Dorks : "inurl: /sym404/root/" or "inurl: /sym404/" @GodfatherOrwa @theXSSrat #WordPress #hacking #cybersecurity #bugbounty
Based on my last comment with @GodfatherOrwa and @eslam3kll , This is the template of SQLi Detection github.com/0xElkot/My-Nuc… Steps: 1- Catch all requests of parameters. 2- Grep reflected parameters with gf and Kxss 3- Fire this template #happy_hacking #bugbounty
United States Trends
- 1. Good Wednesday 18.6K posts
- 2. Hump Day 8,709 posts
- 3. Lakers 96.1K posts
- 4. #wednesdaymotivation 3,683 posts
- 5. Luka 73.2K posts
- 6. Froot N/A
- 7. Pharos 9,898 posts
- 8. Ayton 16.1K posts
- 9. #MLBS6Spoilers 10.4K posts
- 10. Talus Labs 15.4K posts
- 11. Warriors 97.2K posts
- 12. $BYND 121K posts
- 13. Steph 35.1K posts
- 14. Shai 34.6K posts
- 15. #MOST_WANTED_IN_OAKLAND N/A
- 16. Usha Vance 8,967 posts
- 17. Marcus Smart 8,982 posts
- 18. Jen Psaki 9,700 posts
- 19. Kuminga 11.2K posts
- 20. Sengun 26.7K posts
You might like
-
 Dharshan (JPD)
Dharshan (JPD)
@JPD_1206 -
 aasim
aasim
@BhatAasim9 -
 𝑹𝒂𝒔𝒆𝒍 𝑹𝒂𝒏𝒂
𝑹𝒂𝒔𝒆𝒍 𝑹𝒂𝒏𝒂
@0xraselrana -
 Md Maruf Hosan 🇵🇸
Md Maruf Hosan 🇵🇸
@0xMaruf -
 Suyash Sharma
Suyash Sharma
@SuyashS91823422 -
 Czeppo
Czeppo
@Czeppo1 -
 Badder_Ashif
Badder_Ashif
@badderashif -
 S7a6k
S7a6k
@s7a6k -
 Manoj Sharma 🇮🇳
Manoj Sharma 🇮🇳
@predator_97x -
 JW
JW
@jwilhelmi -
 Greed
Greed
@0xGreed_ -
 Hemant Kashyap
Hemant Kashyap
@Herry51130182 -
 Mehraj
Mehraj
@m3hrajbhat -
 cyborg
cyborg
@LULZ74049089 -
 Rakesh
Rakesh
@deephunt3r
Something went wrong.
Something went wrong.