Saravanan
@svanank
DFIR Specialist
You might like
GitHub - CyberSecurityUP/Awesome-Red-Team-Operations github.com/CyberSecurityU…
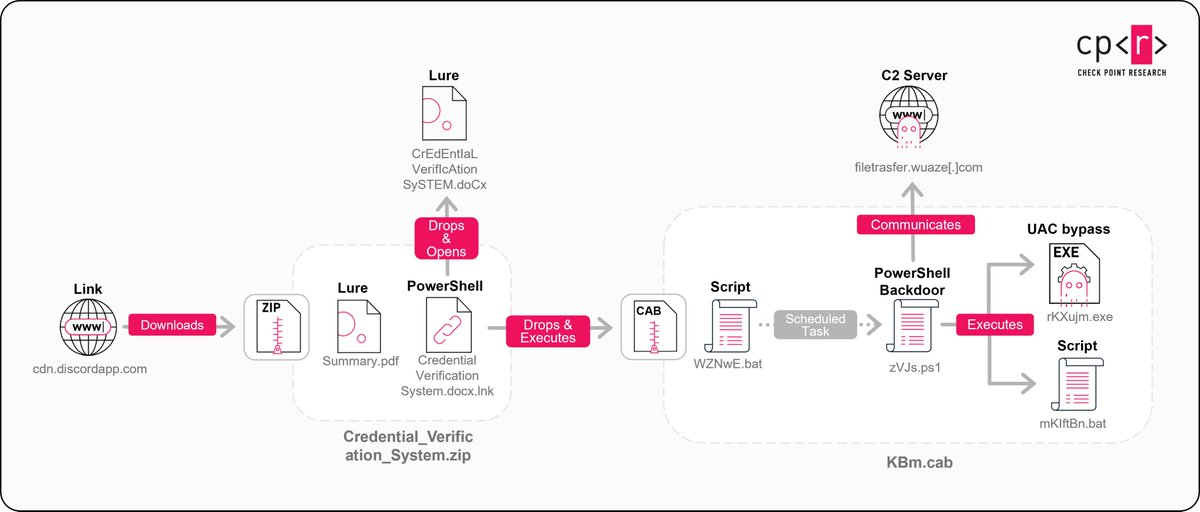
Check Point Research is tracking a phishing campaign linked to a North Korea–aligned threat actor known as KONNI. The attackers deploy an AI-generated PowerShell backdoor, highlighting the growing use of AI by threat actors. research.checkpoint.com/2026/konni-tar…
Zscaler ThreatLabz has published a technical analysis of the BlackForce phishing kit, designed to evade detection and bypass MFA using Man-in-the-Browser attacks. BlackForce employs techniques such as blocklists and a dual-channel communication architecture to separate the…

React2Shell is being exploited in the wild. Newsworthy post-exploit activity: We observed four Linux threats deployed post-exploitation: PeerBlight, CowTunnel, ZinFoq, and a Kaiji botnet variant. Each one is built for persistence, control, or disruption. huntress.com/blog/peerbligh…
⚠️NEWS ALERT⚠️ NEW POSTER | #Ransomware & #CyberExtortion poster authored by @4enzikat0r & @rj_chap releasing at the @SANSInstitute #CTISummit! Get your hardcopy by attending in person or download it by registering to attend via live online! 👉sans.org/u/1uc8

Saving passwords in your browser is super convenient. But should you? malwarebytes.com/blog/news/2023…
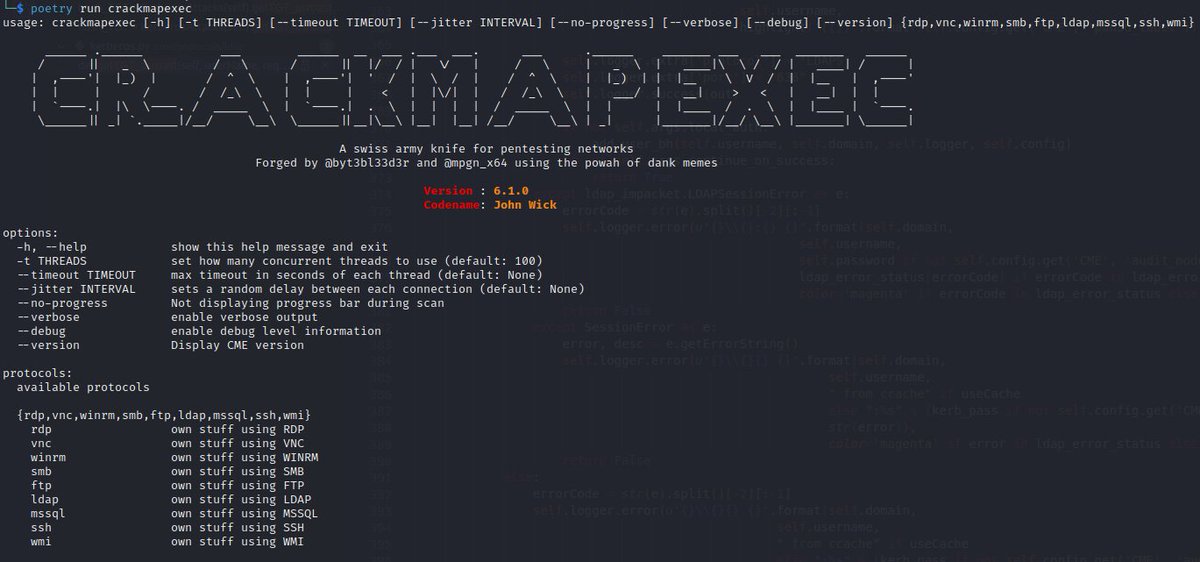
New release of crackmapexec is out ! 6.1.0🥳 This version now support of a new protocol : WMI by @Memory_before ! If the SMB port is filtered, you can still pwn3d everything !! 🔥 Quick list of improvements 🔽 - CME now works against Windows 2003 and Windows 7 (it was broken)…
Windows Directories For SOC Analysts
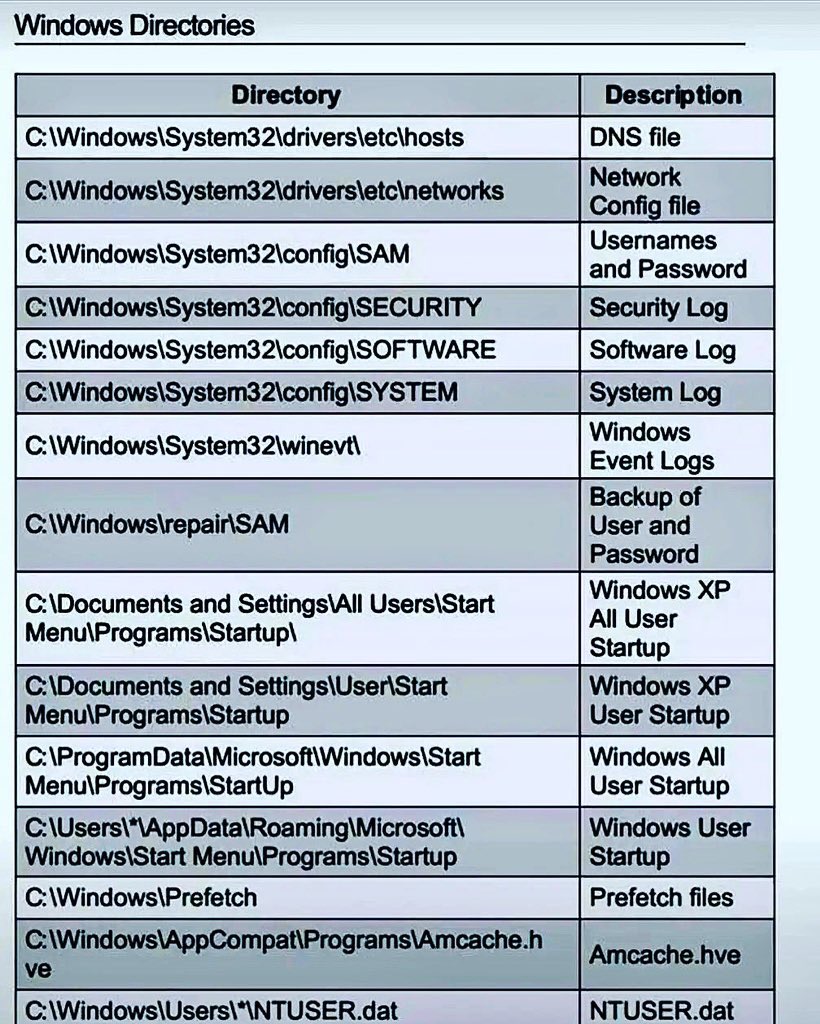
Just a friendly reminder that hacking doesn’t always require a terminal connection.
30 Search Engines for Cybersecurity Researchers: 1. AlienVault — An extensive threat intelligence feed for cybersecurity researchers. 2. Binary Edge — Scans the internet to gather threat intelligence data. 3. Censys — Assesses the attack surface of internet-connected devices. 4.…

Free Malware Analysis Course, covers malware concepts, malware analysis, and black-box reverse engineering techniques class.malware.re #cybersecurity #malware
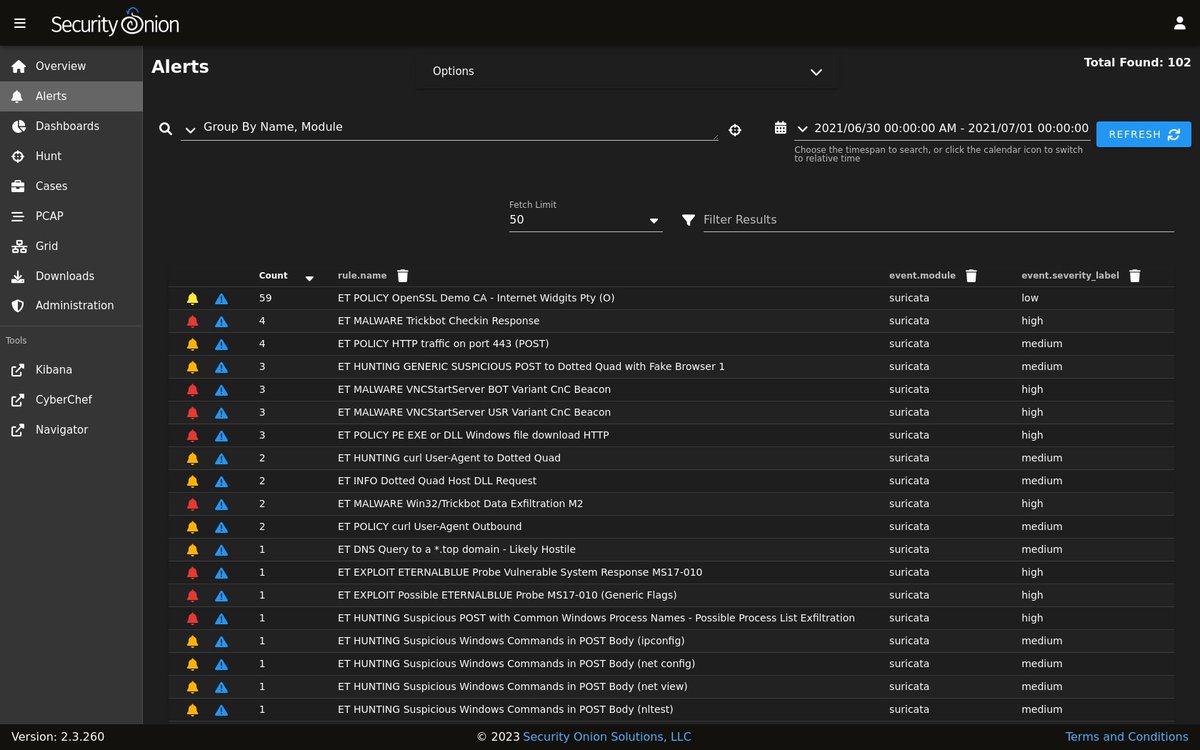
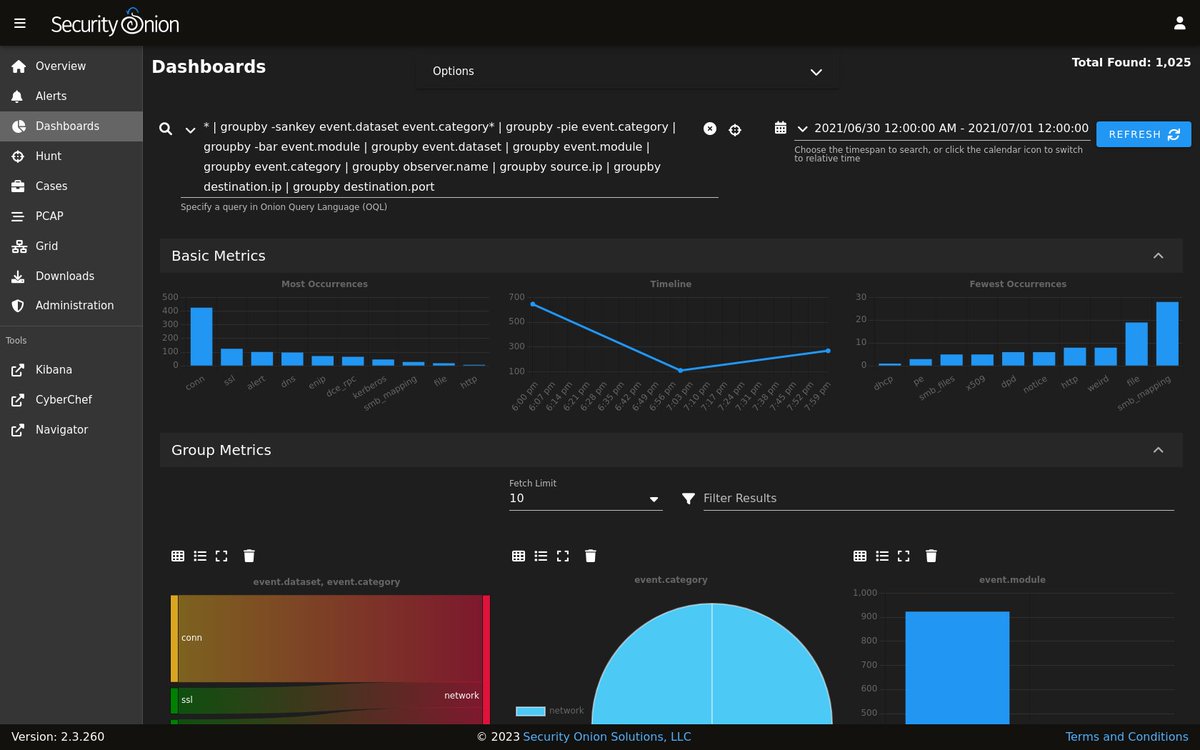
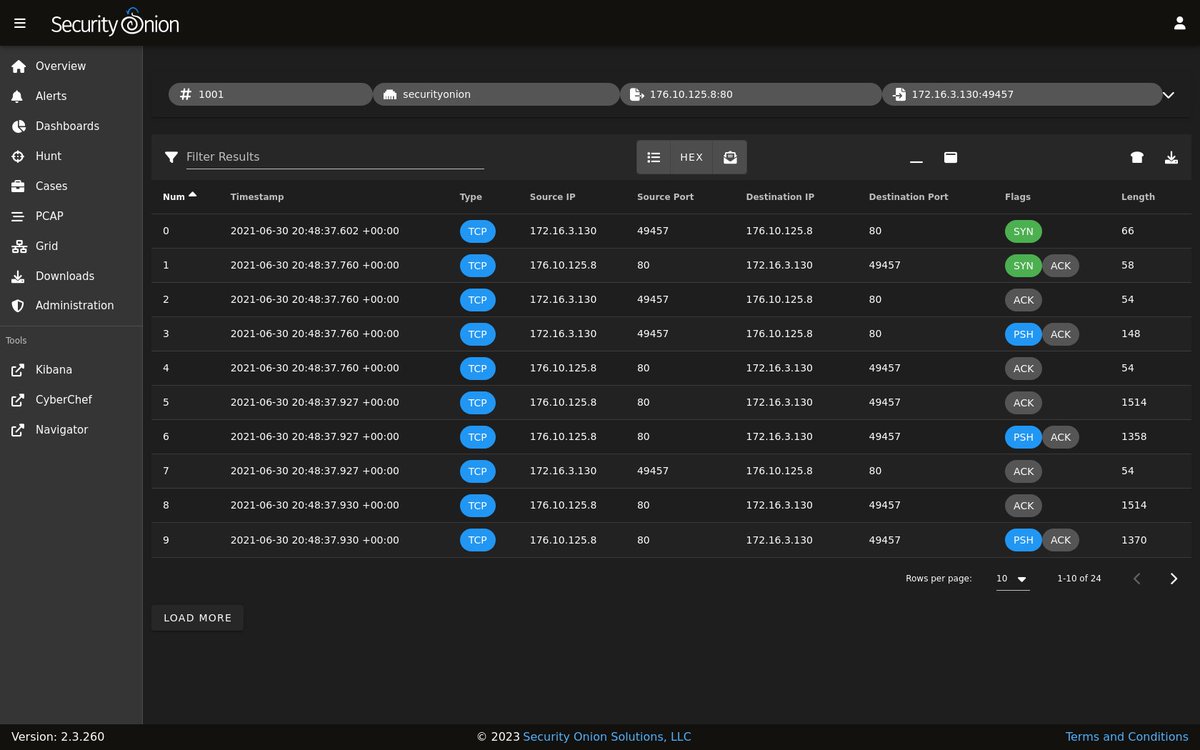
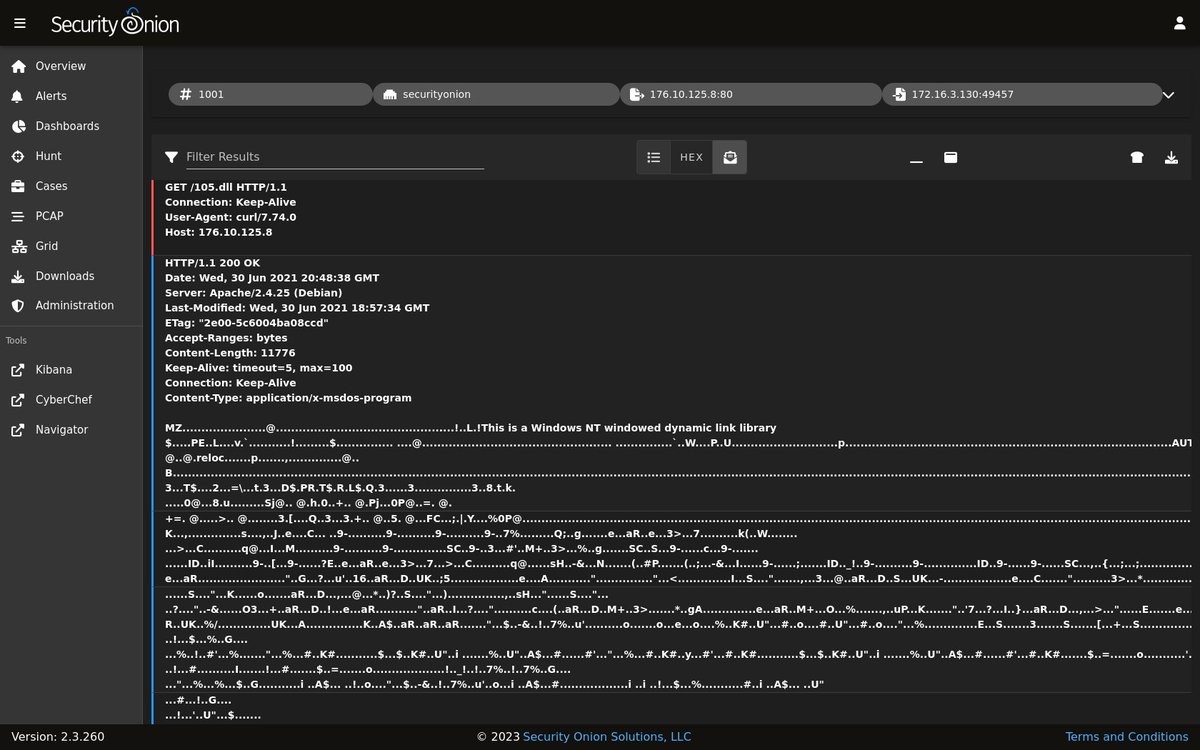
#SecurityOnion 2.3.260 now available including: ✅Suricata 6.0.13 ✅Grafana 9.2.19 ✅ CyberChef 10.4.0 and more! If you like #SecurityOnion, please like and retweet! blog.securityonion.net/2023/06/securi… #infosec #CyberSecurity #ThreatHunting #DFIR
Google Calendar RAT A PoC of Command&Control (C2) over Google Calendar Events, This tool has been developed for those circumstances where it is difficult to create an entire red teaming infrastructure. github.com/MrSaighnal/GCR… #infosec #pentesting #redteam
Windows Triaging with PowerShell: Part 1: Parsing Event Logs: aditya-pratap9557.medium.com/windows-triagi… Part 2: Artifacts Collection: aditya-pratap9557.medium.com/windows-triagi…
6 months ago, I started working on a way to better map the #ransomware ecosystem and its evolution, including rebrands.🔎 I am really happy to share this handmade cartography, which is based on @orangecyberdef resources, #OSINT and reverse engineering. ➡️ github.com/cert-orangecyb…

I’m excited to announce that my book, “Evasive Malware”, will soon be available for pre-order! The past 2.5 years of late nights, eye strain, and carpal tunnel is almost worth it 😎 Also excited to announce that my technical reviewer is the amazing @fr0gger_ ! Stay tuned! 👇

Radare2 Tutorial series of videos from BinaryAdventure youtube.com/watch?v=oW8Ey5…
United States Trends
- 1. Thune N/A
- 2. SAVE Act N/A
- 3. Bulls N/A
- 4. #DavidContraGoliat N/A
- 5. Simons N/A
- 6. Ivey N/A
- 7. Chelsea N/A
- 8. Celtics N/A
- 9. Vucevic N/A
- 10. Giannis N/A
- 11. Jazz N/A
- 12. Coby N/A
- 13. Tatum N/A
- 14. Kaitlan Collins N/A
- 15. Elmo N/A
- 16. Kai Havertz N/A
- 17. Mike Conley N/A
- 18. Vooch N/A
- 19. Utah N/A
- 20. Memphis N/A
Something went wrong.
Something went wrong.