#apikeys resultados de búsqueda
Clay tables can get expensive fast, especially without the correct setup. Clients enriching millions of records might face costs upwards of $20-30k, or even $60-70k. API keys can significantly cut costs, sometimes reducing expenses from $60-70k to $7-10k. #APIkeys #datamanagement
Strategically using API keys can save a company up to $60K. Key advice: understand business issues first, then find the best tool. Don't hesitate to ask experts for recommendations on data for specific use cases. #CreditManagement #APIkeys
Free API Keys: Build Your LLM Portfolio! Learn to create and manage API keys with ease! This tutorial shows you how to generate your own API key and leverage Gemini's free tier for a powerful large language model portfolio. Watch now and unlock the potential! #APIKeys #GeminiAPI
Easily manage your API keys with Agent Forge. Track usage, check balance, and top up anytime with no mess, no hassle. Sign up at agents.aitech.io #AgentForge #APIKeys #AutomationTools #NoCodeAI #SecureAccess

API Key Secrets: Unleashing AI Image Generation Power! #APIKeys #ImageGeneration #Patreon #AI #LearningJourney #TechTutorial #OnlineCommunity #SoftwareDevelopment #DigitalArt #Innovation
API keys 'Used for Generating New Coins' #import #apikeys Some shameless brainless ghoose techs in online have been involved in reporting my developers wallet addresses as scam without evidence of scam, without trying their service writing negative reviews in trustpilot


Traders who know, use #APIkeys. 👀 Faster execution ⚡ Smarter strategies 📊 Secure automation 🔒 Automate your trading, connect tools, manage risk — all with #NioX’s secure integration. 🛡️
With #OWASP highlighting secrets security as the most important issue for mobile applications it's time to shift left with @approov_io and integrated runtime secrets management. #apisecurity #apikeys #appdev #mobileappdevelopment
🚨 Security alert: A series of hijacked npm packages, some over 9 years old, now exfiltrate sensitive data through obfuscated scripts. This highlights software supply chain vulnerabilities. #npm #APIkeys #USA link: ift.tt/N90Xzxp

I just published Unveiling Sensitive API Exposures: My Journey and the Lessons Learned link.medium.com/6fquNcyqzAb #APIkeys #Credentials #DataSecurity #BugBounty #Cybersecurity #Vulnerabilities #DataPrivacy #InformationSecurity #ResponsibleDisclosure #TechSecurity
HaveIBeenPwned Founder Compromised in Phishing Incident cysecurity.news/2025/04/haveib… #APIKeys #CredentialPhishing #CyberAttacks

Rise in Data-Stealing Malware Targeting Developers, Sonatype Warns cysecurity.news/2025/04/rise-i… #APIKeys #Cybersecurity #DataBreach

Reverse Engineer Android Apps for API Keys #ReverseEngineerAndroidApps #APIKeys #Tutorials #Forensics #Documentation pwn.guide/free/forensics…
Need an IP geolocation API key? Takes < 60 seconds to get started with IPinfo. Here’s how to: 🔑 Get your token 🌐 Call the API via cURL, JS, or browser 🧪 Test a response Step-by-step guide → ipinfo.io/blog/how-to-ge… #IPData #APIKeys #DevTools

As the adoption of blockchain technology continues to grow, the importance of API keys cannot be overstated. API keys are essential for developers who want to access and interact with blockchain networks through applications. #APIkeys blockchainmastery.co.uk/?p=203

Thousands of iOS Apps Expose Sensitive Data Through Hardcoded Secrets, Researchers Warn cysecurity.news/2025/03/thousa… #APIKeys #Appsecurity #cloudstorage

Tighten security, keep flexibility. 🔐 With Graph Access Control via RBAC, WunderGraph enables you to: ✅ Secure federated & sub-graphs ✅ Customize access ✅ Enhance collaboration ✅ Reduce security risks #APIKeys #GraphAccessControl #RBAC #DataSecurity #FederatedGraphs

🔑 Balancing security and efficiency just got easier! 🔑 Now, generate and manage your own API keys. No middleman, no vulnerabilities. Enhance security and streamline workflows with SoftLedger. Learn more: hubs.li/Q02B9KvV0 #SoftLedger #APIKeys #CustomerEmpowerment
Rob shows how to quickly enable live trades on the BotSpot platform. Learn to set up API keys and link your account. Not financial advice. Results may be simulated. #LiveTrading #BotSpot #APIKeys #AlgoTrading
Video : #Coinbase #APIKeys: Quick Guide & Secure Generation - rite.link/KihZ 👈🏼 #Gemini #HuggingFace & #Llama don't do it, so test RiteKit for #CompanyLogoAPI

youtube.com
YouTube
Coinbase API Keys: Quick Guide & Secure Generation
Video : #Coinbase #APIKeys: Quick Guide & Secure Generation - rite.link/KihZ 👈🏼 #Gemini #HuggingFace & #Llama don't do it, so test RiteKit for #CompanyLogoAPI #growthhacks

youtube.com
YouTube
Coinbase API Keys: Quick Guide & Secure Generation
📣 New Podcast! "The Unseen Storm: Securing APIs and Protecting Against Key Exposure" on @Spreaker #apikeys #apisecurity #appauthentication #approov #cybersecurity spreaker.com/episode/the-un…

spreaker.com
Spreaker Podcasts
The Unseen Storm: Securing APIs and Protecting Against Key Exposure
Stop storing sensitive keys in your workflows! Leverage n8n's built-in Credentials system for secure, reusable API access. Stay secure. 🔐 #n8nSecurity #APIKeys #Credentials #DataSafety #AutomationBestPractices #SecureWorkflow #DigitalSecurity #LowCodeCompliance #PrivateData…
Validin introduces YARA rules for retro hunting across virtual host responses, enabling discovery of indicators in historical web data. Over 5,000 exposed OpenAI API keys found in one week using custom searches. #YARARules #APIKeys #DataMonitoring ift.tt/FIjKzxL
hendryadrian.com
Introducing YARA Rules: Search and Monitor the Internet’s Infrastructure with YARA
Validin added YARA retro hunting across its large archive of virtual host responses, allowing enterprise users to write, run, and view matches from custom YARA rules to discover and track indicators...
Are you using Workflow Credentials? Never hardcode API keys or passwords into your nodes. Store them securely in n8n's dedicated credential manager. Security first! 🔒 #n8nSecurity #Credentials #APIKeys #SecureAutomation #DataSafety #WorkflowBestPractices #CyberSecurity…
Clay tables can get expensive fast, especially without the correct setup. Clients enriching millions of records might face costs upwards of $20-30k, or even $60-70k. API keys can significantly cut costs, sometimes reducing expenses from $60-70k to $7-10k. #APIkeys #datamanagement
The n8n credentials system is your key to security. 🔐 Use it to store your API keys safely, separate from your workflows. It's a simple step that makes a big difference. #APIkeys #n8nTips #Security #CyberSecurity #WorkflowAutomation #AutomationTools #n8n #DeveloperBestPractices
Strategically using API keys can save a company up to $60K. Key advice: understand business issues first, then find the best tool. Don't hesitate to ask experts for recommendations on data for specific use cases. #CreditManagement #APIkeys
The n8n credentials system is your key to security. 🔐 Use it to store your API keys securely, separate from your workflows. It's a small step that makes a big difference. #APIkeys #n8nTips #Security #CyberSecurity #WorkflowAutomation #AutomationTools #n8n…
Salesloft Integration Breach Exposes Salesforce Customer Data cysecurity.news/2025/09/salesl… #APIKeys #AWS #CyberAttacks

Traders who know, use #APIkeys. 👀 Faster execution ⚡ Smarter strategies 📊 Secure automation 🔒 Automate your trading, connect tools, manage risk — all with #NioX’s secure integration. 🛡️

Need an IP geolocation API key? Takes < 60 seconds to get started with IPinfo. Here’s how to: 🔑 Get your token 🌐 Call the API via cURL, JS, or browser 🧪 Test a response Step-by-step guide → ipinfo.io/blog/how-to-ge… #IPData #APIKeys #DevTools

@DannyLimanseta Hey Danny Need to buy an API Key to play around. Which is the best and most complicated for embedding models ? #APIKeys
India’s largest cryptocurrency exchange, CoinDCX, was hacked on July 19, 2025, resulting in a loss of approximately $44.2 million. . #CoinDCXHack #CryptoSecurity #APIKeys #DataBreach #CryptoRegulation #IndianCrypto #CyberAttack #SecurityMeasures
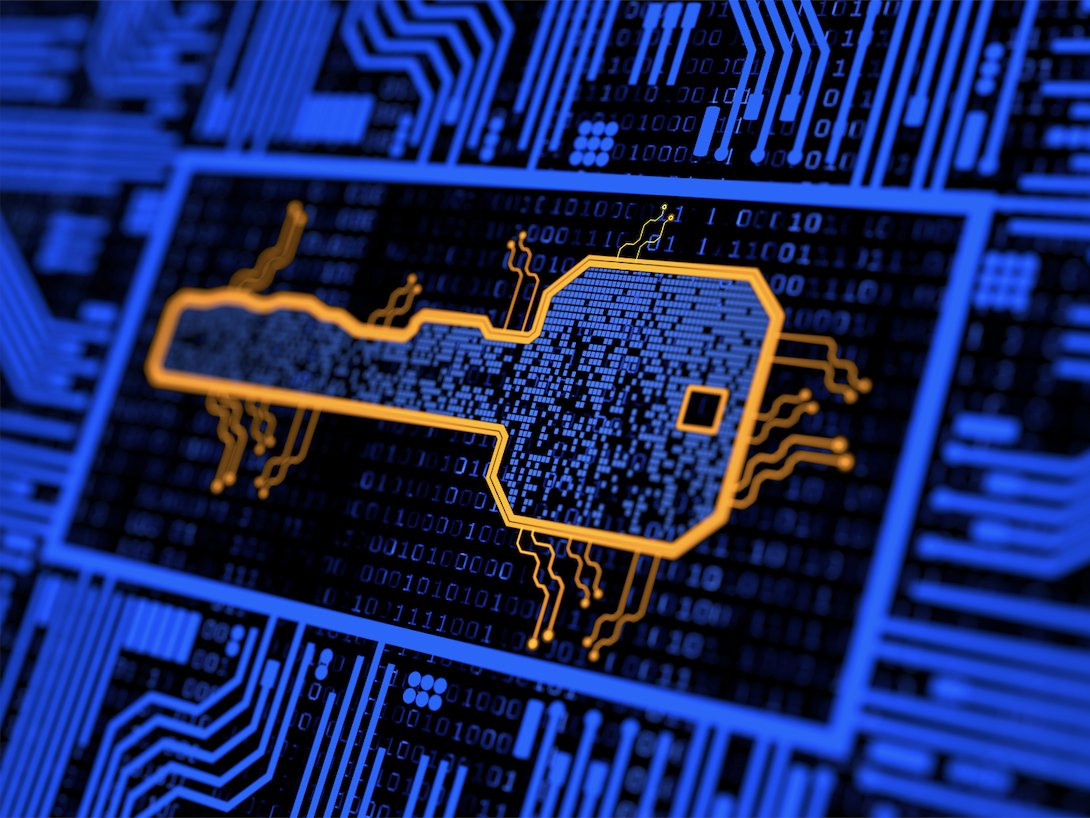
Secretx - Extracting API Keys And Secrets By Requesting Each URL At The Your List j.mp/3720EnM #APIKeys #Secretx
Vault - A Tool For Secrets Management, Encryption As A Service, And Privileged Access Management j.mp/2XUe16w #APIKeys #AWS

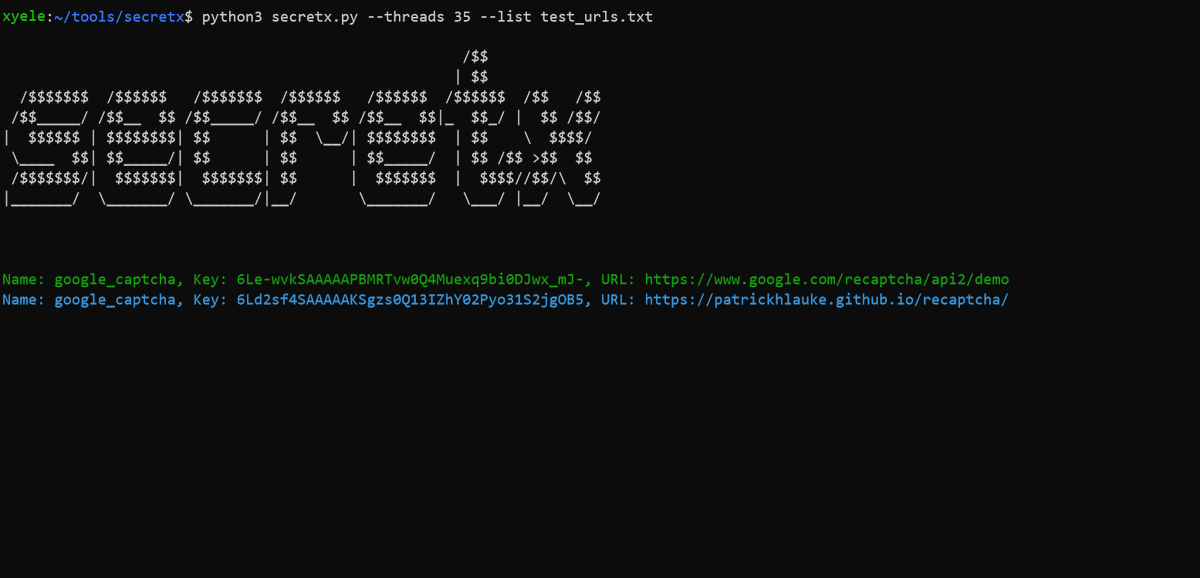
Should-I-Trust - OSINT Tool To Evaluate The Trustworthiness Of A Company j.mp/3eQGEcp #APIKeys #Chrome #ChromeExtension #EC2
earmas.ga - Taken - Takeover AWS Ips And Have A Working POC For Subdomain Takeover j.mp/2IVfMMZ #Access #APIKeys #Bugcrowd #EC2 #Linux #earmas
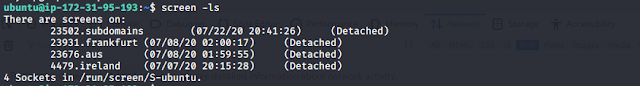
Kamerka GUI - Ultimate Internet Of Things/Industrial Control Systems Reconnaissance Tool j.mp/2tCECcs #APIKeys #Kamerka #Linux
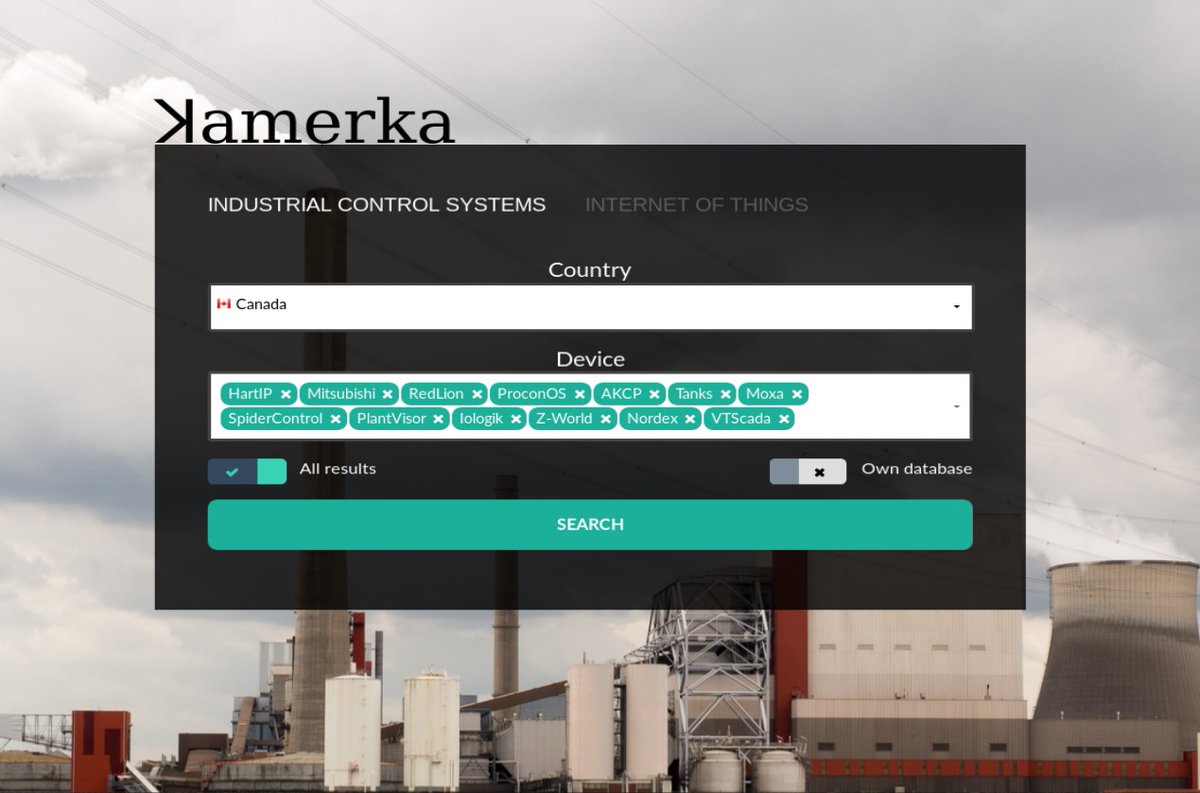
Subfinder - A Subdomain Discovery Tool That Discovers Valid Subdomains For Websites j.mp/2vuTDia #APIKeys #BugBounty #Dockerhub
Ioccheck - A Tool For Simplifying The Process Of Researching IOCs j.mp/3j6AE3C #Antivirus #APIKeys #Clamav #Fortinet #Hashes

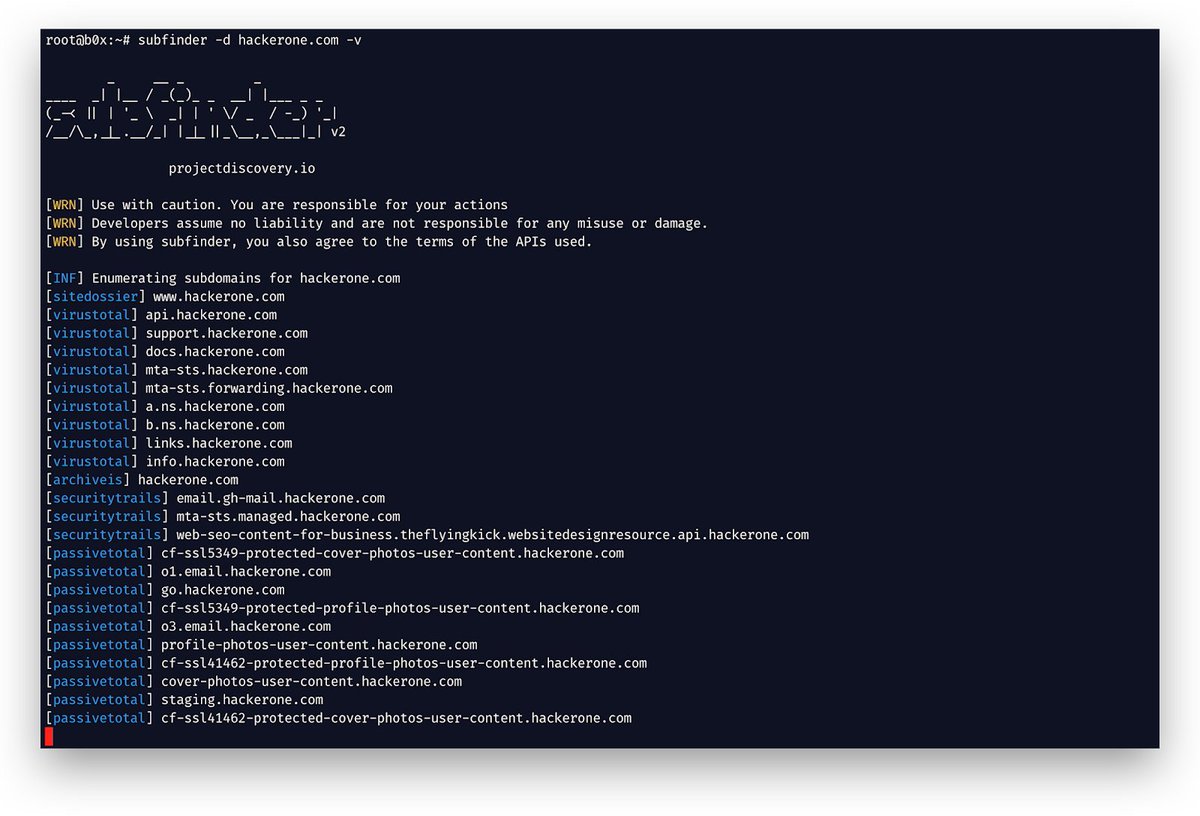
Sigurls - A Reconnaissance Tool, It Fetches URLs From AlienVault's OTX, Common Crawl, URLScan, Github And The Wayback Machine dlvr.it/RrPf2F #AlienvaultOtx #APIKeys #golang #Recon
Easily manage your API keys with Agent Forge. Track usage, check balance, and top up anytime with no mess, no hassle. Sign up at agents.aitech.io #AgentForge #APIKeys #AutomationTools #NoCodeAI #SecureAccess

Taken - Takeover AWS Ips And Have A Working POC For Subdomain Takeover dlvr.it/Rjr4hg #Access #APIKeys #Bugcrowd #EC2 #Linux
Ioccheck - A Tool For Simplifying The Process Of Researching IOCs dlvr.it/S39G7y #Antivirus #APIKeys #Clamav #Fortinet

A creative way demonstrating "API Key Management" (2/2) #API #APIKeys #APIKeyManagement #ApplicationProgrammingInterface #NileshRoy

earmas.ga - Taken - Takeover AWS Ips And Have A Working POC For Subdomain Takeover j.mp/2IVfMMZ #Access #APIKeys #Bugcrowd #EC2 #Linux #earmas
See how easy it is to create an API Key with your Pinata account 🔑 Watch here: youtu.be/l4vPAeBtdms #ipfs #APIkeys

Traders who know, use #APIkeys. 👀 Faster execution ⚡ Smarter strategies 📊 Secure automation 🔒 Automate your trading, connect tools, manage risk — all with #NioX’s secure integration. 🛡️

HaveIBeenPwned Founder Compromised in Phishing Incident cysecurity.news/2025/04/haveib… #APIKeys #CredentialPhishing #CyberAttacks

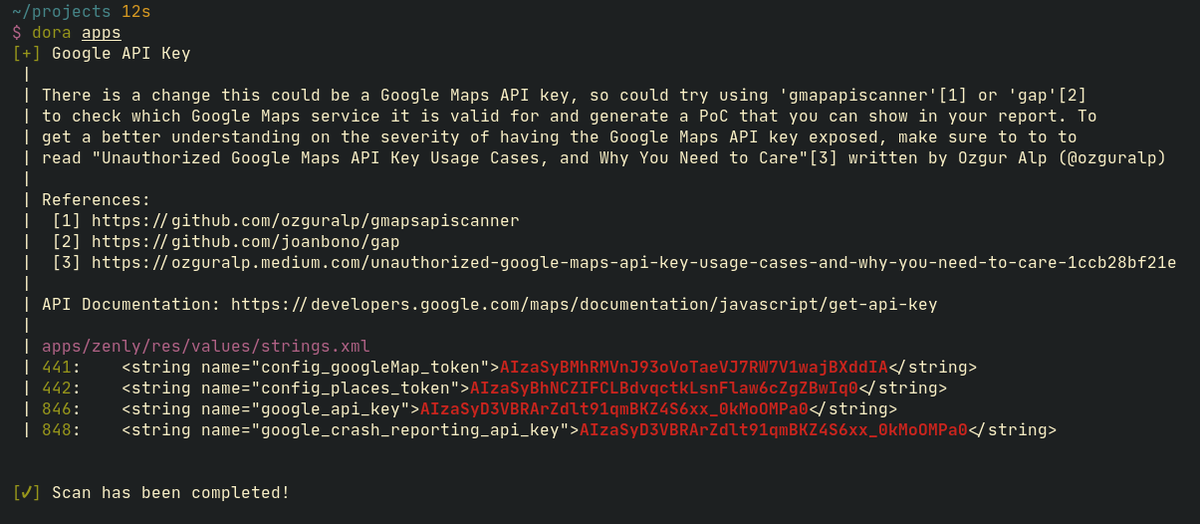
#Hacking #APIKeys #Dora #RegEx #Malware #Vulnerability #CyberCrime #CyberAttack #CyberSecurity Dora : Find Exposed API Keys Based On RegEx And Get Exploitation Methods. github.com/sdushantha/dora kalilinuxtutorials.com/dora/
"RT Should-I-Trust - OSINT Tool To Evaluate The Trustworthiness Of A Company j.mp/3eQGEcp #APIKeys #Chrome #ChromeExtension #EC2 https://t.co/A6ST81ZYN7"

Rise in Data-Stealing Malware Targeting Developers, Sonatype Warns cysecurity.news/2025/04/rise-i… #APIKeys #Cybersecurity #DataBreach

🔑 Secure your B2B SaaS integrations with the best authentication methods! Dive into this essential topic with us. #APIkeys and #OAuth2.0 provide robust security and seamless integrations. Let's discuss the key factors to consider. #SaaS #Authentication #DataSecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Doran 77.1K posts
- 2. Good Sunday 63.6K posts
- 3. #Worlds2025 118K posts
- 4. Max B 2,838 posts
- 5. Faker 90.9K posts
- 6. #T1WIN 66.1K posts
- 7. #sundayvibes 4,788 posts
- 8. #AskBetr N/A
- 9. SILVER SCRAPES 4,300 posts
- 10. O God 7,880 posts
- 11. #sundaymotivation 1,700 posts
- 12. Sunday Funday 2,754 posts
- 13. Guma 17.1K posts
- 14. Blessed Sunday 17.1K posts
- 15. The Wave 61.7K posts
- 16. Oner 28.7K posts
- 17. Keria 37K posts
- 18. Pence 21.8K posts
- 19. Option 2 4,675 posts
- 20. Jeanna N/A



































