#cybersecurityguidelines نتائج البحث
Safeguarding Your Corporate Environment from Social Engineering twi.li/rllWCK #UI #CyberSecurityGuidelines

Spinbackup provides the ultimate solution to allow businesses to have the tools and capabilities they need to meet today’s stringent #Cloudsecurity objectives found on the this checklist. #CyberSecurityGuidelines #EnterpriseSecurity #RiskMitigation spinbackup.com/blog/cloud-sec…

You are not alone if you find the #CybersecurityGuidelines at work confusing and unhelpful. A new study highlights a major issue with creating these guidelines and outlines simple steps that could improve them. #Cybersecurity tiny-link.io/ccNgi1jTzQOiAE…

Safeguarding Your Corporate Environment from Social Engineering twi.li/fHTc5A #UI #CyberSecurityGuidelines

You are not alone if you find the #CybersecurityGuidelines at work confusing and unhelpful. A new study highlights a major issue with creating these guidelines and outlines simple steps that could improve them. #Cybersecurity tiny-link.io/CY070gszAcp2WE…

Info seputar update kebijakan dan kegiatan OJK lainnya, kunjungi kanal Youtube Otoritas Jasa Keuangan (OJK TV). youtube.com/shorts/tXXxQiH… #OJK #CyberSecurity #cybersecurityguidelines #cybercrime #DigitalFinancial #TeknologiKeuangan #ojktv

youtube.com
YouTube
OJK Luncurkan Cyber Security Guidelines untuk Inovasi Teknologi...
Upcoming federal cybersecurity guidance is likely to address the recent software supply chain concerns. Insights via @FuturumResearch Principal analyst @ShellyKramer . bit.ly/3vYiPtz #Cybersecurity #CybersecurityGuidelines #SupplyChain

🔌 Learn about the draft cybersecurity guidelines designed to ensure the security of EV charging infrastructure: [hubs.la/Q01-Z1yZ0] #EVCharging #CybersecurityGuidelines #ElectricVehicles #InfrastructureSecurity #TechnologySafety #CyberProtection #FutureMobility
𝗡𝗜𝗦𝗧 𝗨𝗽𝗱𝗮𝘁𝗲𝘀 𝗣𝗿𝗶𝘃𝗮𝗰𝘆 𝗙𝗿𝗮𝗺𝗲𝘄𝗼𝗿𝗸, 𝗧𝘆𝗶𝗻𝗴 𝗜𝘁 𝘁𝗼 𝗥𝗲𝗰𝗲𝗻𝘁 𝗖𝘆𝗯𝗲𝗿𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗚𝘂𝗶𝗱𝗲𝗹𝗶𝗻𝗲𝘀 Read article: buff.ly/wPh3s23. #cybersecurity #cybersecurityguidelines #dataprivacy #itsystems
🔌 Learn about the draft cybersecurity guidelines designed to ensure the security of EV charging infrastructure: [hubs.la/Q01-Z8-m0] #EVCharging #CybersecurityGuidelines #ElectricVehicles #InfrastructureSecurity #TechnologySafety #CyberProtection #FutureMobility
livemint.com
U.S. Issues Draft Cybersecurity Guidelines for EV Charging Networks | Mint
Guidance for electric-vehicle industry aims to protect charging payment systems and links to wider grid
@silexlab 8 WordPress tips to make your website secure thecybersecurityplace.com/8-wordpress-ti… … via @cybersecuritypl #CyberSecuirtyTips #CyberSecurityGuidelines #DataBreach #GDPR #SoftwareSecurity #WebSecurity #WebsiteSecurity #Wordpress #CyberSecurity #Infosec #TCSP #TheCyberSecuritySS
Cyber Security Today thecybersecurityplace.com/cyber-security… via @cybersecuritypl #Android #AndroidApps #CyberSecurityGuidelines #CyberSecurityReport #CyberSecuritySolutions #DataPrivacy #MobileApplicationSecurity #MobileApps #MobileSecurity #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace
#CybersecurityGuidelines for ports and port facilities launched 📃 ow.ly/gyW350G3ILU
SOAR thecybersecurityplace.com/soar-vs-securi… via @cybersecuritypl #CyberIncident #CyberInvestigation #CyberSecurityGuidelines #SecurityOperations #SOAR #SoftwareSecurity #SpearPhishing #ThreatIntelligence #VulnerabilityManagement #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace
Now thecybersecurityplace.com/google-confirm… via @cybersecuritypl #CyberInvestigation #CyberSecurityGuidelines #CyberSecurityPolicy #Google #GooglePlay #GoogleSecurity #JokerMalware #MaliciosAttack #Malware #MalwareAttack #SoftwareSecurity #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace
Cyber Security Roundup for April 2019 thecybersecurityplace.com/cyber-security… via @cybersecuritypl #CyberAttack #CyberSecurityEvolution #CyberSecurityGuidelines #CyberSecurityReport #Malware #PasswordSecurity #Ransomware #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace
How To Block DDoS Attacks Using Automation thecybersecurityplace.com/how-to-block-d… via @cybersecuritypl #Automation #AutomationSecurity #CyberSecurityGuidelines #CyberSecurityStrategy #DDOS #DDoSAttacks #NetworkSecurity #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace
5 Questions to Help Chart thecybersecurityplace.com/5-questions-to… via @cybersecuritypl #CyberSecurityGuidelines #CyberSecurityTips #EmployeeSecurity #IoTDevices #MFA #MultifactorAuthentication #NetworkSecurity #ZeroTrust #ZeroTrustSecurity #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace
🔌 Learn about the draft cybersecurity guidelines designed to ensure the security of EV charging infrastructure: [hubs.la/Q01-Z7YX0] #EVCharging #CybersecurityGuidelines #ElectricVehicles #InfrastructureSecurity #TechnologySafety #CyberProtection #FutureMobility
livemint.com
U.S. Issues Draft Cybersecurity Guidelines for EV Charging Networks | Mint
Guidance for electric-vehicle industry aims to protect charging payment systems and links to wider grid
8 WordPress tips to make your website secure thecybersecurityplace.com/8-wordpress-ti… via @cybersecuritypl #CyberSecuirtyTips #CyberSecurityGuidelines #DataBreach #GDPR #SoftwareSecurity #WebSecurity #WebsiteSecurity #Wordpress #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace
Our🆕guidelines provide Critical Infrastructure entities with the tools to implement #AI safely and securely. Make your operations robust against emerging risks. go.dhs.gov/iXo

🔐 Cybersecurity Tips: Use strong, unique passwords; enable multi-factor authentication; think before clicking on emails/links; keep your software updated; back up your data. Stay proactive and protect what matters! #Cybersecurity #StaySafeOnline #DataProtection #PasswordSafety
Cybersecurity best practices. #indiancert #cyberswachhtakendra #StaySafeOnline #cybersecurity #besafe #staysafe #mygov #Meity #onlinefraud #cybercrime #scamming #cyberalert #CSK #CyberSecurityAwareness

Cybersecurity: Protect systems & data from threats. Use firewalls, antivirus, strong passwords, & multi-factor authentication. Key tools: Nmap, Wireshark, Metasploit. Stay vigilant! #cybersecurity
💻 #CyberMonday is the perfect day to make sure your Cybersecurity habits are locked in. •Update old passwords •Use a password manager to help keep track of passwords •Unsubscribe from any sites you no longer use •Update software •Think before clicking on suspicious links…

🖥️ Shopping online this #CyberMonday? Stay cyber-safe with these tips: ✔️ Limit the personal info you share & check your privacy settings ✔️ If the deal is too good to be true—it probably is ✔️ Use secure, trusted Wi-Fi networks Visit Ready.gov/Cybersecurity for more!

Navigating #Cybersecurity compliance can be challenging, so we've simplified everything for you. Download the essential guide by @PhilMuncaster and take the first step toward streamlined, robust cybersecurity #Compliance: isms.online/downloads/cybe…

Protect your enterprise from ransomware 💻🔒 Learn how to stay safe from WannaCry and other threats! #CyberSecurity #WannaCryPrevention 🛡️ Check out the guidance here: ncsc.gov.uk/guidance/ranso…
This guide emphasizes the importance of operational security, offering teenagers and others practical advice to enhance their digital safety. Implementing these measures can significantly reduce the risk of online threats and data breaches. Defenders should review and implement…
🛍️Cyber Monday brings great deals, but it’s also a time to be extra mindful of your online security. To help you stay safe, we created a simple guide on helping to protect your digital footprint. Access it here: tinyurl.com/CybersecurityB…

Today’s self-study covered key Cybersecurity principles and practices. Security principles (Confidentiality, Integrity, Availability), states of data (in transit, at rest, in process), cybersecurity countermeasures, policies, standards, guidelines & procedures. @ireteeh @OnijeC
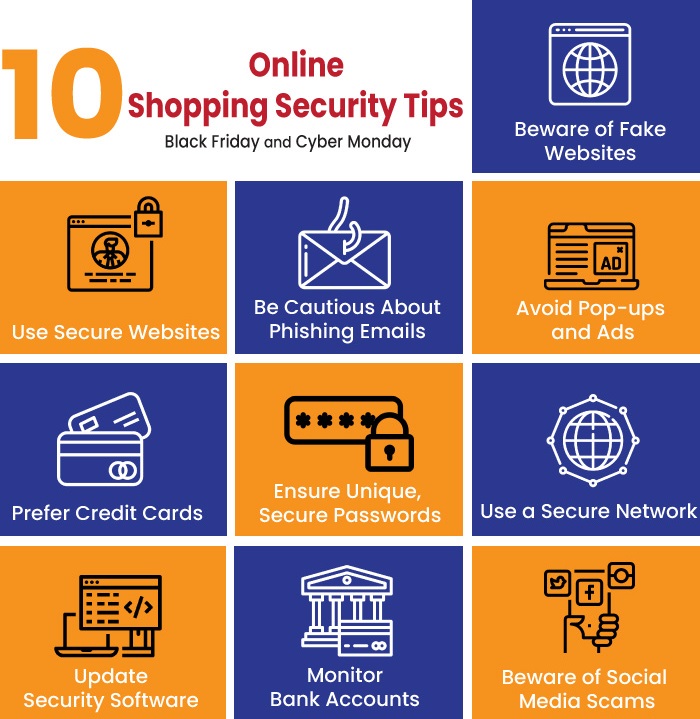
Hey #DPOs! #CyberMonday is almost here 🛍️ Before you dive into deals, here are some quick safety tips! Stay smart, shop safe! #CyberSafety
Common cybercrime practices that can help you stay safe and alert online: 🔗 Don’t click on unknown links ❌Never share passwords, PINs, or OTPs 📲Report suspicious activity immediately Call the cyber helpline at 1800 233 0332 #CyberSecurity #CyberCrime
Cybersecurity best practices. #indiancert #cyberswachhtakendra #StaySafeOnline #cybersecurity #besafe #staysafe #mygov #Meity #onlinefraud #cybercrime #scamming #cyberalert #CSK #CyberSecurityAwareness

Le linee guida NIS: misure di sicurezza e specifiche di base dell’Agenzia per la Cybersicurezza Nazionale dlvr.it/TPVsvX

Cybersecurity best practices. #indiancert #cyberswachhtakendra #StaySafeOnline #cybersecurity #besafe #staysafe #mygov #Meity #onlinefraud #cybercrime #scamming #cyberalert #CSK #CyberSecurityAwareness

🔐 Small mistakes, big breaches. Hackers wait for a click, weak password, or fake link. 💡 5 quick habits: ✔️ Think before you click ✔️ Verify before sharing ✔️ Strong, unique passwords ✔️ Enable 2FA ✔️ Stay updated Stay aware, stay safe. #CyberSecurity #InfoSec #StaySafe 🚀




BIMCO releases first… dlvr.it/DBHnld #CyberRisk #cybersecurityguidelines #shippingindustry #GetUrRiskOn

Upcoming federal cybersecurity guidance is likely to address the recent software supply chain concerns. Insights via @FuturumResearch Principal analyst @ShellyKramer . bit.ly/3vYiPtz #Cybersecurity #CybersecurityGuidelines #SupplyChain

Safeguarding Your Corporate Environment from Social Engineering twi.li/rllWCK #UI #CyberSecurityGuidelines

Spinbackup provides the ultimate solution to allow businesses to have the tools and capabilities they need to meet today’s stringent #Cloudsecurity objectives found on the this checklist. #CyberSecurityGuidelines #EnterpriseSecurity #RiskMitigation spinbackup.com/blog/cloud-sec…

End of SMS-based 2-Factor… rd.cempal.com/Lv7LDb #2factorauthentication #cybersecurity #cybersecurityguidelines

Safeguarding Your Corporate Environment from Social Engineering twi.li/fHTc5A #UI #CyberSecurityGuidelines

You are not alone if you find the #CybersecurityGuidelines at work confusing and unhelpful. A new study highlights a major issue with creating these guidelines and outlines simple steps that could improve them. #Cybersecurity tiny-link.io/CY070gszAcp2WE…

You are not alone if you find the #CybersecurityGuidelines at work confusing and unhelpful. A new study highlights a major issue with creating these guidelines and outlines simple steps that could improve them. #Cybersecurity tiny-link.io/ccNgi1jTzQOiAE…

Something went wrong.
Something went wrong.
United States Trends
- 1. Giannis 62.4K posts
- 2. Spotify 1.68M posts
- 3. Tosin 65.7K posts
- 4. Bucks 39.5K posts
- 5. Leeds 102K posts
- 6. Steve Cropper 1,498 posts
- 7. Milwaukee 17.9K posts
- 8. Andrews 9,848 posts
- 9. Poison Ivy 2,115 posts
- 10. Isaiah Likely N/A
- 11. #WhyIChime 2,087 posts
- 12. Brazile N/A
- 13. Miguel Rojas 2,621 posts
- 14. Phantasm 1,671 posts
- 15. Maresca 49.9K posts
- 16. Danny Phantom 7,296 posts
- 17. Purple 54.1K posts
- 18. Knicks 26.5K posts
- 19. #cthsfb N/A
- 20. Sunderland 48.2K posts

































