#firmwareanalysis wyniki wyszukiwania
Unlock the complexities of automotive ECU reverse engineering. Martin Petran demonstrates AUTOSAR Classic firmware techniques and introduces a Binary Ninja plugin to enhance your automotive RE workflow. re-verse.sessionize.com/session/759122 #REverse2025 #AUTOSAR #FirmwareAnalysis

Streamline firmware analysis with inter-image call graphs! Robin David (@RobinDavid1) showcases graph-based methodologies for mapping cross-binary dependencies and integrating decompiled code. Expand your reversing toolkit. re-verse.sessionize.com/session/783646 #REverse2025 #FirmwareAnalysis…
Fragmented Workflows = Human Error EXPLIoT Platform helps you perform security assessments of your devices in just a few clicks. Get Started for FREE: expliot.io #EXPLIoT #xIoTSecurity #FirmwareAnalysis #SBOM #DevSecOps #SecurityAutomation

Exciting news! Edwin Shuttleworth is speaking at @GrrCon on Sept 26 on "Breaking Down Binaries: Navigating the Labyrinth of IoT Firmware Analysis." Don't miss it! #IoTSecurity #FirmwareAnalysis #GrrCon #FiniteState

Curious about firmware reversing, hardware hacking, and how real experts break (and build) devices? 🔧 Tools, techniques, and hands-on demos—straight from the field. 📺 Watch now → youtube.com/watch?v=tLn6qr… #HardwareHacking #FirmwareAnalysis #IoTSecurity #CTF #HackerMindset
youtube.com
YouTube
Firmware Analysis Expert Answers Your Questions | Ask the Expert |...
binwalk – Reverse engineer firmware like a boss. Maintained by ReFirm Labs. 🌐 github.com/ReFirmLabs/bin… #FirmwareAnalysis #RE
Syscall hijacking via kernel memory writes on a MIPS router. Matias Ramirez shows how embedded tools can become attack vectors. Full write-up: versprite.com/blog/the-shell… #FirmwareAnalysis #SecurityResearch #LinuxKernel
UEFI rootkits grant attackers persistence even after OS reinstallation, surviving wipes and reinfecting at startup. Detecting them requires SPI flash dumps and firmware reverse engineering. #DigitalForensics #FirmwareAnalysis
Python remains a go-to for reverse engineering and embedded defence. Catch up on our latest webinar where we explore how Python supports firmware security workflows. 🎥 Watch here: youtu.be/VlAOYtHk8OA #PythonSecurity #ReverseEngineering #FirmwareAnalysis #Cybersecurity

youtube.com
YouTube
Protecting Python Applications: Safeguard Your IP
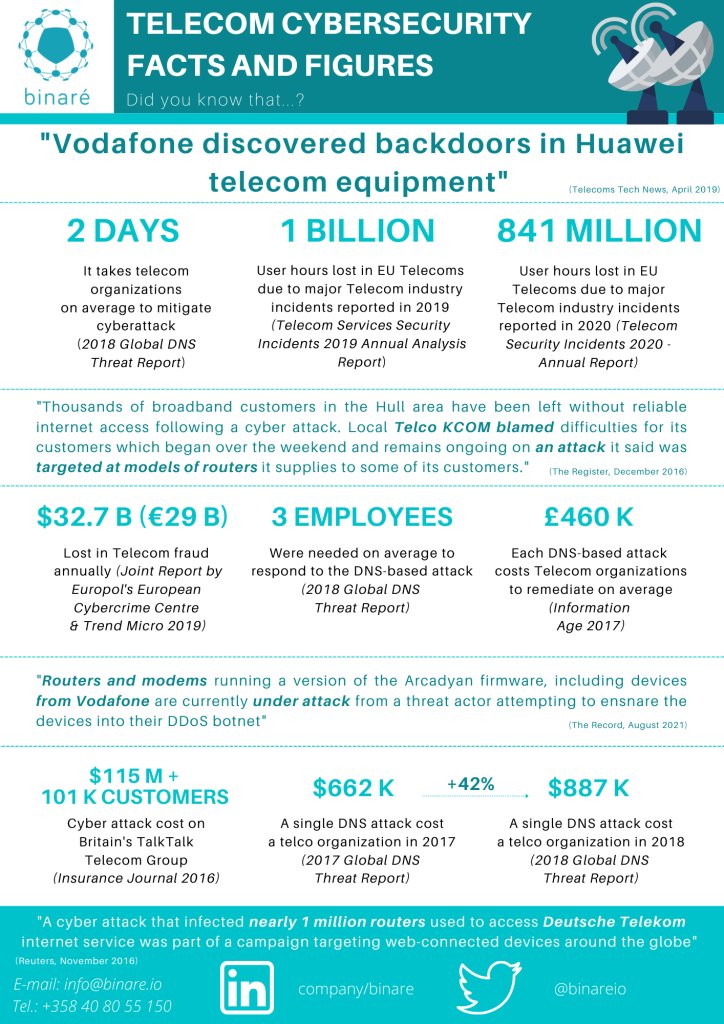
How #Binare helps Telecom Companies with #FirmwareAnalysis & monitoring!🔍📡 Our platform delivers significant value in ensuring device security and reliability. Learn more here: blog.binare.io/resources/bina… 💡 #CyberSecurity #IoT #Telecom #CaseStudy #IoTSecurity #TechInnovation
"Unlocking the secrets of firmware analysis: a crucial step in identifying and mitigating vulnerabilities in embedded systems." stratosally.com/offensive-secu… #FirmwareAnalysis #CyberSecurity #EmbeddedSystems #VulnerabilityManagement #TechInsights #DataProtection #ThreatDetection
stratosally.com
Firmware Analysis - Stratos Ally
**Note: The content in this article is only for educational purposes and understanding of cybersecurity concepts. It should enable people and organizations to have a better grip on threats and know...
Dai uno sguardo al mio ultimo articolo: Il colosso della sicurezza informatica CISCO è davvero così sicuro? linkedin.com/pulse/il-colos… via @LinkedIn #CyberSecurity #Cisco #FirmwareAnalysis #PenetrationTesting #EthicalHacking #networksecurity
linkedin.com
Il colosso della sicurezza informatica CISCO è davvero così sicuro?
1. Introduzione Cisco Systems è una delle aziende leader nel settore delle reti e della sicurezza informatica.
🔐 Master IEC 62443 Compliance with ONEKEY! 🚀 Join #ONEKEY's 45-minute online seminar on February 6th at 11:00 AM (CET) and discover how #binary #firmwareanalysis and the ONEKEY #Compliance Wizard™ can simplify your security strategy. app.livestorm.co/onekey/unveili…
app.livestorm.co
Unveiling IEC 62443: Navigating Component Requirements with Binary Firmware Analysis and the ONEKEY...
Are you striving to align with IEC 62443 standards and searching for effective ways to ensure compliance in industrial cybersecurity? Join us for this engaging online seminar designed to simplify t...
📢New vulnerability Insights: OpenSSL released a patch for high severity vulnerabilities ⚠️ Do operators and vendors of connected devices need to worry? Read the whole post👇 onekey.com/blog/onekey-vu… #firmwareanalysis #sbom #securesoftwaresupplychain #cybersecurityservices #IoT
onekey.com
OpenSSL released a patch for high severity vulnerabilities – do operators and vendors of connected...
OpenSSL released a patch for high severity vulnerabilities – do operators and vendors of connected devices need to worry? Read more!
Firmware Analysis Part-1 dlvr.it/Rq49hQ #pentesting #iotsecurity #firmwareanalysis
Congratulations to our faculty member, Dr. Tuba Yavuz! Dr. Yavuz specializes in improving security and privacy of #IoT through behavioral #firmwareanalysis and automated model extraction. #NelmsInstitute #NSFcareeraward
Despite uncertain times, fantastic news: Dr. Tuba Yavuz was just notified of her receipt of a 2020 NSF CAREER Award for her project, “Towards a Secure and Reliable Internet of Things through Automated Model Extraction and Analysis.” More at the link: ow.ly/xzZV50yWvA4

Chong, Daniel; Automatically Inferring Image Bases of ARM32... #ImageBase #FirmwareAnalysis rave.ohiolink.edu/etdc/view?acc_…
Python remains a go-to for reverse engineering and embedded defence. Catch up on our latest webinar where we explore how Python supports firmware security workflows. 🎥 Watch here: youtu.be/VlAOYtHk8OA #PythonSecurity #ReverseEngineering #FirmwareAnalysis #Cybersecurity

youtube.com
YouTube
Protecting Python Applications: Safeguard Your IP
Syscall hijacking via kernel memory writes on a MIPS router. Matias Ramirez shows how embedded tools can become attack vectors. Full write-up: versprite.com/blog/the-shell… #FirmwareAnalysis #SecurityResearch #LinuxKernel
Curious about firmware reversing, hardware hacking, and how real experts break (and build) devices? 🔧 Tools, techniques, and hands-on demos—straight from the field. 📺 Watch now → youtube.com/watch?v=tLn6qr… #HardwareHacking #FirmwareAnalysis #IoTSecurity #CTF #HackerMindset
youtube.com
YouTube
Firmware Analysis Expert Answers Your Questions | Ask the Expert |...
binwalk – Reverse engineer firmware like a boss. Maintained by ReFirm Labs. 🌐 github.com/ReFirmLabs/bin… #FirmwareAnalysis #RE
Fragmented Workflows = Human Error EXPLIoT Platform helps you perform security assessments of your devices in just a few clicks. Get Started for FREE: expliot.io #EXPLIoT #xIoTSecurity #FirmwareAnalysis #SBOM #DevSecOps #SecurityAutomation

Streamline firmware analysis with inter-image call graphs! Robin David (@RobinDavid1) showcases graph-based methodologies for mapping cross-binary dependencies and integrating decompiled code. Expand your reversing toolkit. re-verse.sessionize.com/session/783646 #REverse2025 #FirmwareAnalysis…

Unlock the complexities of automotive ECU reverse engineering. Martin Petran demonstrates AUTOSAR Classic firmware techniques and introduces a Binary Ninja plugin to enhance your automotive RE workflow. re-verse.sessionize.com/session/759122 #REverse2025 #AUTOSAR #FirmwareAnalysis

Dai uno sguardo al mio ultimo articolo: Il colosso della sicurezza informatica CISCO è davvero così sicuro? linkedin.com/pulse/il-colos… via @LinkedIn #CyberSecurity #Cisco #FirmwareAnalysis #PenetrationTesting #EthicalHacking #networksecurity
linkedin.com
Il colosso della sicurezza informatica CISCO è davvero così sicuro?
1. Introduzione Cisco Systems è una delle aziende leader nel settore delle reti e della sicurezza informatica.
🔐 Master IEC 62443 Compliance with ONEKEY! 🚀 Join #ONEKEY's 45-minute online seminar on February 6th at 11:00 AM (CET) and discover how #binary #firmwareanalysis and the ONEKEY #Compliance Wizard™ can simplify your security strategy. app.livestorm.co/onekey/unveili…
app.livestorm.co
Unveiling IEC 62443: Navigating Component Requirements with Binary Firmware Analysis and the ONEKEY...
Are you striving to align with IEC 62443 standards and searching for effective ways to ensure compliance in industrial cybersecurity? Join us for this engaging online seminar designed to simplify t...
How #Binare helps Telecom Companies with #FirmwareAnalysis & monitoring!🔍📡 Our platform delivers significant value in ensuring device security and reliability. Learn more here: blog.binare.io/resources/bina… 💡 #CyberSecurity #IoT #Telecom #CaseStudy #IoTSecurity #TechInnovation

UEFI rootkits grant attackers persistence even after OS reinstallation, surviving wipes and reinfecting at startup. Detecting them requires SPI flash dumps and firmware reverse engineering. #DigitalForensics #FirmwareAnalysis
Exciting news! Edwin Shuttleworth is speaking at @GrrCon on Sept 26 on "Breaking Down Binaries: Navigating the Labyrinth of IoT Firmware Analysis." Don't miss it! #IoTSecurity #FirmwareAnalysis #GrrCon #FiniteState

📢New vulnerability Insights: OpenSSL released a patch for high severity vulnerabilities ⚠️ Do operators and vendors of connected devices need to worry? Read the whole post👇 onekey.com/blog/onekey-vu… #firmwareanalysis #sbom #securesoftwaresupplychain #cybersecurityservices #IoT
onekey.com
OpenSSL released a patch for high severity vulnerabilities – do operators and vendors of connected...
OpenSSL released a patch for high severity vulnerabilities – do operators and vendors of connected devices need to worry? Read more!
Chong, Daniel; Automatically Inferring Image Bases of ARM32... #ImageBase #FirmwareAnalysis rave.ohiolink.edu/etdc/view?acc_…

Unlock the complexities of automotive ECU reverse engineering. Martin Petran demonstrates AUTOSAR Classic firmware techniques and introduces a Binary Ninja plugin to enhance your automotive RE workflow. re-verse.sessionize.com/session/759122 #REverse2025 #AUTOSAR #FirmwareAnalysis

Streamline firmware analysis with inter-image call graphs! Robin David (@RobinDavid1) showcases graph-based methodologies for mapping cross-binary dependencies and integrating decompiled code. Expand your reversing toolkit. re-verse.sessionize.com/session/783646 #REverse2025 #FirmwareAnalysis…

Fragmented Workflows = Human Error EXPLIoT Platform helps you perform security assessments of your devices in just a few clicks. Get Started for FREE: expliot.io #EXPLIoT #xIoTSecurity #FirmwareAnalysis #SBOM #DevSecOps #SecurityAutomation

Exciting news! Edwin Shuttleworth is speaking at @GrrCon on Sept 26 on "Breaking Down Binaries: Navigating the Labyrinth of IoT Firmware Analysis." Don't miss it! #IoTSecurity #FirmwareAnalysis #GrrCon #FiniteState

How #Binare helps Telecom Companies with #FirmwareAnalysis & monitoring!🔍📡 Our platform delivers significant value in ensuring device security and reliability. Learn more here: blog.binare.io/resources/bina… 💡 #CyberSecurity #IoT #Telecom #CaseStudy #IoTSecurity #TechInnovation

Something went wrong.
Something went wrong.
United States Trends
- 1. Texans 38K posts
- 2. World Series 113K posts
- 3. CJ Stroud 6,788 posts
- 4. Blue Jays 97.3K posts
- 5. Mariners 93.5K posts
- 6. Seahawks 37K posts
- 7. Springer 68.3K posts
- 8. Nick Caley 2,678 posts
- 9. White House 316K posts
- 10. StandX 4,830 posts
- 11. Dan Wilson 4,337 posts
- 12. Nico Collins 2,150 posts
- 13. Dodgers in 5 2,265 posts
- 14. LA Knight 8,420 posts
- 15. #WWERaw 62.1K posts
- 16. Kenneth Walker 2,596 posts
- 17. Sanae Takaichi 39.3K posts
- 18. Bazardo 3,202 posts
- 19. Demeco 1,829 posts
- 20. Sam Darnold 4,380 posts