#itsecuritybestpractices search results
When was the last time your business had an IT Security Audit? Top 3 areas our experts recommend focusing on & how often you should have one done. Need help with an IT Security Audit? Contact Cortrucent: [email protected] #cybersecurity #itsecuritybestpractices #itaudit
So nice to host our GJM Manufacturing Roundtable in person this week. Guest panelists offered valuable info on IT security for manufacturing businesses. #manufacturing #itsecuritybestpractices

The Bilbo Baggins Threat to PLM Assets senticore.com/the-bilbo-bagg… #productlifecyclemanagement #itsecurity #itsecuritybestpractices #dataprotection #engineering #databasesecurity #cybersecurity #ipprotection

Health systems need to protect patient data, even if sometimes patients don't see the need for such measures, said Jacki Monson during a recent Webinar with @AnahiSantiago and David Ting. lnkd.in/eUm-Srit #itsecuritybestpractices #riskmanagement #patientsafety #tausight
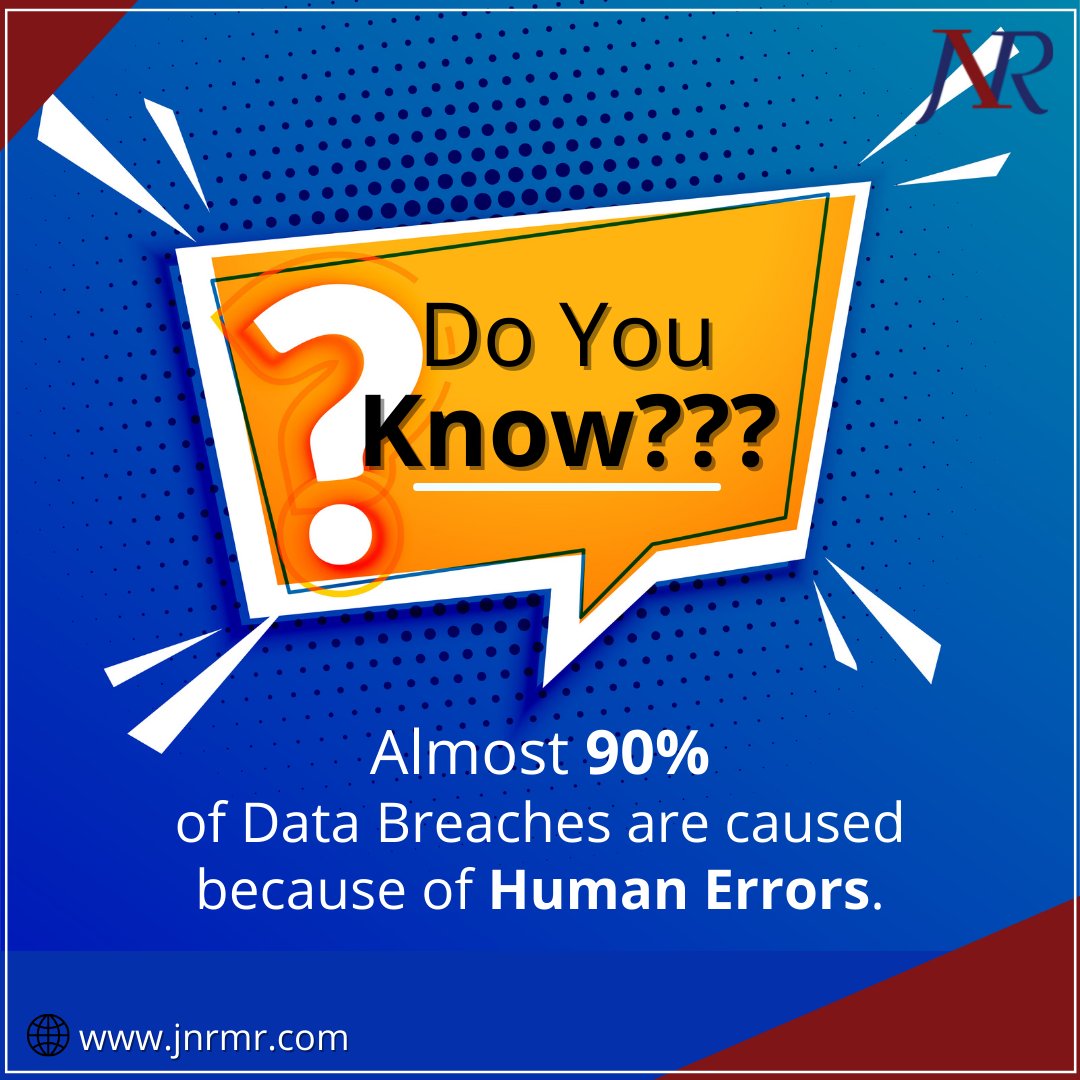
Make your business error free and secured from online hackers with us JNR Management. Our Website: jnrmr.com Call us @ +91–9643834775 #onlinesecurity #itsecurity #itsecuritybestpractices #cyberattack #cybersecurity #cybersecurityawareness #datasecurity #databreach
Read our Guest Blog from @lp_networks read what you should be including in your formal employee exit checklist to protect your IT. bit.ly/3jgvyPz #itchecklist #itsecurity #itsecuritybestpractices #guestblog #employeeexit #leaverschecklist

MBC Security Tip: Educate Your Users. Educating employees about security policies helps avoid security breaches. Cyber attackers often target employees because they are more vulnerable than the IT infrastructure. mbccs.com/it-business-so… #itsecurity #itsecuritybestpractices #itsec

Making IT Security First a Prime Directive for Your Business- Nine Elements bit.ly/3dsONo1 #itsecuritybestpractices #itsecurity #businessstrategy #latinbiztoday @TheresaKushner @drmghernandez @drlizrios @Elainelovespapi @careerchatter @BigIdeas4SB

Could 60% of IT leaders be wrong? Check out our latest blog. #itsecuritybestpractices #endpointsecurity #endpointprotection promisec.com/endpoint-secur…

Managing vulnerabilities is an ongoing process, not a one-time task. Our guide breaks down the 6 essential steps to keep your organization protected. ⬇️ bit.ly/4d9Wo7i #VulnerabilityManagement #ITSecurityBestPractices #RiskManagement #Cybersecurity #NetworkSecurity
Maybe your business is expanding, or your startup has grown to a point where its time to get serious about IT. But where do you start in the search for IT support? #micropac #itsecuritybestpractices micropactech.com/main/searching…

BPOs need to revisit, reassess and strengthen their #ITsecurity policies. Connect with our security experts to know more: inknowtech.com/time-to-revisi… #itsecuritybestpractices #vulnerabilityassessment #secureit #cyberattacks #infosec #datasecurity #compliance #dataprotection

No matter who wins the election, protecting your business from cyber threats is critical! #itsecuritybestpractices Schedule a meeting today: bit.ly/3j6N897https:/…

Is your business ready for #AI-powered cyberattacks? From robust firewalls to advanced endpoint protection, preparing your defenses is non-negotiable. Don't wait for "Judgment Day." #CyberPreparedness #ITSecurityBestPractices #BusinessProtection
Managing vulnerabilities is an ongoing process, not a one-time task. Our guide breaks down the 6 essential steps to keep your organization protected. ⬇️ bit.ly/4d9Wo7i #VulnerabilityManagement #ITSecurityBestPractices #RiskManagement #Cybersecurity #NetworkSecurity
Remember, protecting your IT goes beyond firewalls and advanced software solutions. #TipTuesday #ITSecurityBestPractices #ITSecurity #PhysicalSecurity
Cloud security best practices for 2023 🔒 This article discusses #cloudsecurity best practices to assist organizations in protecting their data and infrastructure. 👉 Read to learn more: buff.ly/3m3Gl6c #itsecuritybestpractices #mspartner

Cloud security best practices for 2023 🔒 This article discusses #cloudsecurity best practices to assist organizations in protecting their data and infrastructure. 👉 Read to learn more: buff.ly/3m3Gl6c #itsecuritybestpractices #mspartner

Join our Experts for Free 1 hour Session on Network Time Protocol. Request a Demo at lnkd.in/dP9SiuMh Learn more at: lnkd.in/dWpYDwY3 #cyberattack #networksecurity #itsecuritybestpractices #networkarchitecture

Join our Experts for Free 1 hour Session on Network Time Protocol. Do the booking directly : lnkd.in/fewvpPv Learn more at: lnkd.in/dWpYDwY3 #cyberattack #networksecurity #itsecuritybestpractices #networkarchitecture
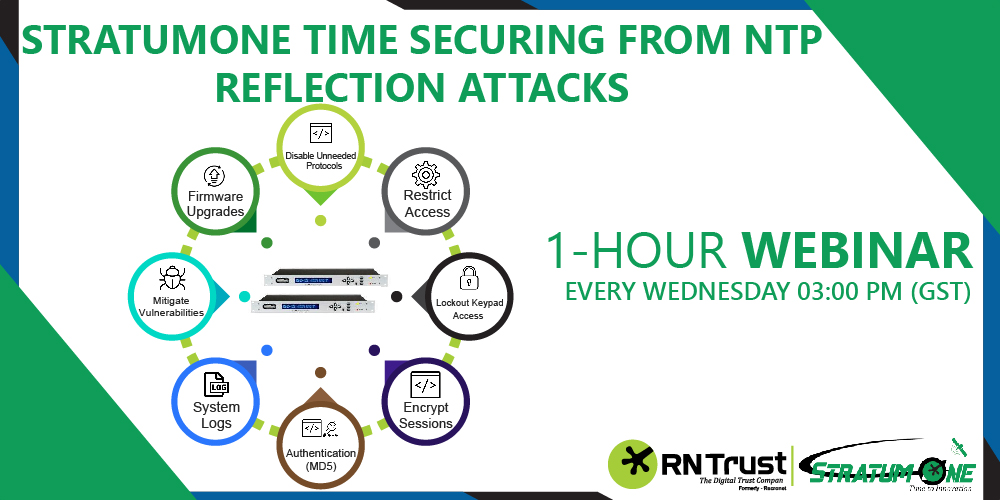
Join our Experts for Free 1 hour Session on Network Time Protocol to know how to handle DDoS attacks. Do the booking directly: lnkd.in/fewvpPv Learn more at: lnkd.in/dWpYDwY3 #cyberattack #networksecurity #itsecuritybestpractices #networkarch

Join our Experts for Free 1 hour Session on Network Time Protocol to know how to handle DDoS attacks. Do the booking directly: lnkd.in/fewvpPv Learn more at: lnkd.in/dWpYDwY3 #cyberattack #networksecurity #itsecuritybestpractices #networkarch

Health systems need to protect patient data, even if sometimes patients don't see the need for such measures, said Jacki Monson during a recent Webinar with @AnahiSantiago and David Ting. lnkd.in/eUm-Srit #itsecuritybestpractices #riskmanagement #patientsafety #tausight
Join our Experts for Free 1 hour Session on Network Time Protocol. Do the booking directly : lnkd.in/fewvpPv Learn more at: lnkd.in/dWpYDwY3 #cyberattack #networksecurity #itsecuritybestpractices #networkarchitecture

When was the last time your business had an IT Security Audit? Top 3 areas our experts recommend focusing on & how often you should have one done. Need help with an IT Security Audit? Contact Cortrucent: [email protected] #cybersecurity #itsecuritybestpractices #itaudit
Join our Experts for Free 1 hour Session on Network Time Protocol to know how to handle DDoS attacks. Do the booking directly: lnkd.in/fewvpPv Learn more at: lnkd.in/dWpYDwY3 #cyberattack #networksecurity #itsecuritybestpractices #networkarch

Take a look at this article that explains why using spreadsheets to manage risk can actually increase your business exposure. infosecurity-magazine.com/white-papers/s… #RiskManagement #DataProtection #ITSecurityBestPractices

So nice to host our GJM Manufacturing Roundtable in person this week. Guest panelists offered valuable info on IT security for manufacturing businesses. #manufacturing #itsecuritybestpractices

MBC Security Tip: Educate Your Users. Educating employees about security policies helps avoid security breaches. Cyber attackers often target employees because they are more vulnerable than the IT infrastructure. mbccs.com/it-business-so… #itsecurity #itsecuritybestpractices #itsec

Join our Experts for Free 1 hour Session on Network Time Protocol. Do the booking directly : lnkd.in/fewvpPv Learn more at: lnkd.in/dWpYDwY3 #cyberattack #networksecurity #itsecuritybestpractices #networkarchitecture

Making IT Security First a Prime Directive for Your Business- Nine Elements bit.ly/3dsONo1 #itsecuritybestpractices #itsecurity #businessstrategy #latinbiztoday @TheresaKushner @drmghernandez @drlizrios @Elainelovespapi @careerchatter @BigIdeas4SB

The Bilbo Baggins Threat to PLM Assets senticore.com/the-bilbo-bagg… #productlifecyclemanagement #itsecurity #itsecuritybestpractices #dataprotection #engineering #databasesecurity #cybersecurity #ipprotection

Read our Guest Blog from @lp_networks read what you should be including in your formal employee exit checklist to protect your IT. bit.ly/3jgvyPz #itchecklist #itsecurity #itsecuritybestpractices #guestblog #employeeexit #leaverschecklist

Make your business error free and secured from online hackers with us JNR Management. Our Website: jnrmr.com Call us @ +91–9643834775 #onlinesecurity #itsecurity #itsecuritybestpractices #cyberattack #cybersecurity #cybersecurityawareness #datasecurity #databreach

So nice to host our GJM Manufacturing Roundtable in person this week. Guest panelists offered valuable info on IT security for manufacturing businesses. #manufacturing #itsecuritybestpractices

Do the booking directly : lnkd.in/fewvpPv Follow our page for more updates : lnkd.in/fNdy-pr To Know more, visit rn-trust.com #cyberattack #networksecurity #itsecuritybestpractices #networkarchitecture

Could 60% of IT leaders be wrong? Check out our latest blog. #itsecuritybestpractices #endpointsecurity #endpointprotection promisec.com/endpoint-secur…

Network Time Protocol Do the booking directly : lnkd.in/fewvpPv Follow our page for more updates: lnkd.in/fNdy-pr Learn more at: lnkd.in/dWpYDwY3 Visit: rntrustdigital.com #cyberattack #networksecurity #itsecuritybestpractices #networkarchitecture

MBC Security Tip: Educate Your Users. Educating employees about security policies helps avoid security breaches. Cyber attackers often target employees because they are more vulnerable than the IT infrastructure. mbccs.com/it-business-so… #itsecurity #itsecuritybestpractices #itsec

Cloud security best practices for 2023 🔒 This article discusses #cloudsecurity best practices to assist organizations in protecting their data and infrastructure. 👉 Read to learn more: buff.ly/3m3Gl6c #itsecuritybestpractices #mspartner

Join our Experts for Free 1 hour Session on Network Time Protocol. Do the booking directly : lnkd.in/fewvpPv Learn more at: lnkd.in/dWpYDwY3 #cyberattack #networksecurity #itsecuritybestpractices #networkarchitecture

BPOs need to revisit, reassess and strengthen their #ITsecurity policies. Connect with our security experts to know more: inknowtech.com/time-to-revisi… #itsecuritybestpractices #vulnerabilityassessment #secureit #cyberattacks #infosec #datasecurity #compliance #dataprotection

Join our Experts for Free 1 hour Session on Network Time Protocol. Request a Demo at lnkd.in/dP9SiuMh Learn more at: lnkd.in/dWpYDwY3 #cyberattack #networksecurity #itsecuritybestpractices #networkarchitecture

ESARIS is a vendor-independent enterprise security architecture built as a sole reference for securing IT services. To find out more visit:zero-outage.com/the-standard/s… #ITquality #ZeroOutage #itsecuritybestpractices
Free 1 hour Session on Network Time Protocol Do the booking directly : lnkd.in/fewvpPv Follow our page for more updates: lnkd.in/fNdy-pr To Know more, visit rn-trust.com #cyberattack #networksecurity #itsecuritybestpractices #networkarchitecture

Ask most companies today about their IT security practices when it comes to preventing hacking and network intrusions - and then show them this article zero-outage.com/opinion/your-f… #ITquality #ZeroOutage #itsecuritybestpractices
Maybe your business is expanding, or your startup has grown to a point where its time to get serious about IT. But where do you start in the search for IT support? #micropac #itsecuritybestpractices micropactech.com/main/searching…

No matter who wins the election, protecting your business from cyber threats is critical! #itsecuritybestpractices Schedule a meeting today: bit.ly/3j6N897https:/…

Take a look at this article that explains why using spreadsheets to manage risk can actually increase your business exposure. infosecurity-magazine.com/white-papers/s… #RiskManagement #DataProtection #ITSecurityBestPractices

Something went wrong.
Something went wrong.
United States Trends
- 1. #StrangerThings5 232K posts
- 2. Thanksgiving 663K posts
- 3. BYERS 51.6K posts
- 4. robin 87.5K posts
- 5. Reed Sheppard 5,534 posts
- 6. Afghan 279K posts
- 7. Podz 4,248 posts
- 8. holly 62K posts
- 9. Dustin 88.2K posts
- 10. National Guard 654K posts
- 11. Vecna 55.5K posts
- 12. Jonathan 73.2K posts
- 13. Gonzaga 8,400 posts
- 14. hopper 15.3K posts
- 15. noah schnapp 8,677 posts
- 16. Erica 16.5K posts
- 17. Lucas 81.6K posts
- 18. Tini 9,188 posts
- 19. Nancy 66.4K posts
- 20. derek 18.3K posts


















