#identitysecurity search results
AI agents don’t just complete tasks—they evolve. Kaitlin Harvey explains how chaos theory helps us understand unpredictable AI behavior and why identity security matters for safe innovation. Dive into the blog: spr.ly/60107qsQg #IdentitySecurity #AgenticAI #CyberSecurity

#AI agents are the new privileged #MachineIdentities. Are you ready to secure them? Catch our re:Invent session: “AI Agents – The New Face of Privileged Machine Identities” Builder’s Showcase @ 4pm: spr.ly/60167UiJp #IdentitySecurity #AWSreInvent #Cybersecurity

Watch the #Video. #IdentitySecurity reimagined. @OleriaSecurity. Protect what matters with the first adaptive identity security product to give full clarity and control of your access. @Rseewald, founder & Managing Partner @EvolutionEquity explains. youtu.be/OxizeJJLxVU
GO VEZA!! Thank you @FastCompany 💪🙏🙌 “As apps, databases, and agents proliferate, companies are hard-pressed to know who has access to what, what they can do with that access, and whether they should even have it ...” #CyberSecurity #IdentitySecurity

Our CEO, Matt Cohen, on CyberArk's seventh consecutive time as a Leader in the 2025 Gartner® Magic Quadrant™ for PAM and how that supports our vision for the Future of Privilege. spr.ly/60127Mcgr #IdentitySecurity #PAM #Cybersecurity
We are integrating Rubrik Identity Resilience with @CrowdStrike Falcon® Next-Gen Identity Security, advancing #IdentitySecurity by enabling customers to surgically rollback malicious identity changes and restore identity providers to a safe state. Learn more:…




🚨🚨 PROTECT YOUR IDENTITY 🚨🚨 Modern and affordable solutions to keep you safe and secure what you value most. 🔒 ℹ️ t1texas.acnibo.com/us-en/home-ser… #IdentitySecurity #Security
🚨🚨 PROTECT YOUR IDENTITY 🚨🚨 Modern and affordable solutions to keep you safe and secure what you value most. 🔒 ℹ️ t1texas.acnibo.com/us-en/home-ser… #IdentitySecurity #securitybreach
Securing access to data everywhere and anywhere. GO VEZA!! @vezainc #identitysecurity #CyberSecurity

🔐 Help shape the future of identity security! Share your insights in the 2026 SANS ITDR Survey and make your voice heard in one of the most critical areas of cybersecurity. Take the survey 👉 sansurl.com/itdr-survey #IdentitySecurity #SANS #Cybersecurity @secgreene

We’re excited to welcome Ajit Hatti & Atharva Chincholkar @ PureID as they explore how digital passkeys can be hijacked, creating risks for identity theft and unauthorized access. #CyberSecurity #IdentitySecurity #Infosec #Passkeys #DigitalSecurity

Cyber operations depend on robust identity governance that enforces least privilege and continuous verification. @SailPoint enables mission agility through strategic #identitysecurity frameworks. Read here to learn more: carah.io/SailPointCyber…

#Secrets sprawl is real... and it can quickly turn into a security nightmare. Join CyberArk experts as they share real-world horror stories and the 4 common pitfalls to avoid in secrets management. spr.ly/60167kHsk #IdentitySecurity #Cybersecurity

We’re excited to welcome Shebin John Mathew as he reveals how device code phishing and PRT theft can compromise cloud identities and grant unauthorized access to enterprise resources. #CyberSecurity #AzureAD #IdentitySecurity #Infosec #CloudSecurity

“Identity isn’t the sidekick anymore — it’s the superhero.” 🦸♂️ Dutch Schwartz explains why identity is now the cornerstone of cyber defense. 🎧 Listen now: eu1.hubs.ly/H0pmcdj0 #IdentitySecurity #Podcast #iProov
Poor situational awareness can undermine even the strongest systems. Retsef Levi shares how #AI can help us better understand and respond to dynamic environments. Listen to the full conversation on the #SecurityMatters podcast. spr.ly/60187370K #IdentitySecurity
AI agents don’t just complete tasks—they evolve. Kaitlin Harvey explains how chaos theory helps us understand unpredictable AI behavior and why identity security matters for safe innovation. Dive into the blog: spr.ly/60107qsQg #IdentitySecurity #AgenticAI #CyberSecurity

🔒🧪 Entra ID to block script injection attacks From Oct 2026, Microsoft will harden Entra ID sign-ins against external script injection. #Microsoft #EntraID #IdentitySecurity #ZeroTrust

Cyber operations depend on robust identity governance that enforces least privilege and continuous verification. @SailPoint enables mission agility through strategic #identitysecurity frameworks. Read here to learn more: carah.io/SailPointCyber…

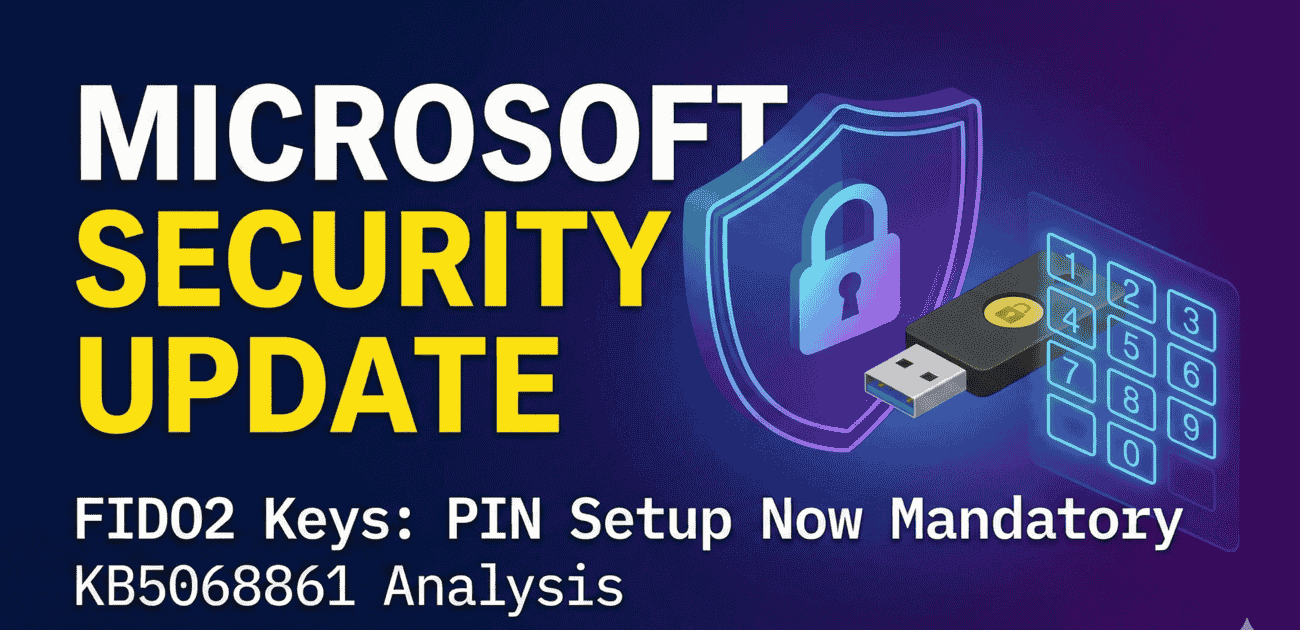
Passwordless just got stricter. Microsoft Entra ID now enforces PIN setup for FIDO2 keys to stop key-theft attacks. See the affected Windows Builds list inside: 🔗 cyberupdates365.com/microsoft-fido… #BlueTeam #IdentitySecurity #MFA #Windows11 #InfoSec #Windows
#AI agents are the new privileged #MachineIdentities. Are you ready to secure them? Catch our re:Invent session: “AI Agents – The New Face of Privileged Machine Identities” Builder’s Showcase @ 4pm: spr.ly/60167UiJp #IdentitySecurity #AWSreInvent #Cybersecurity

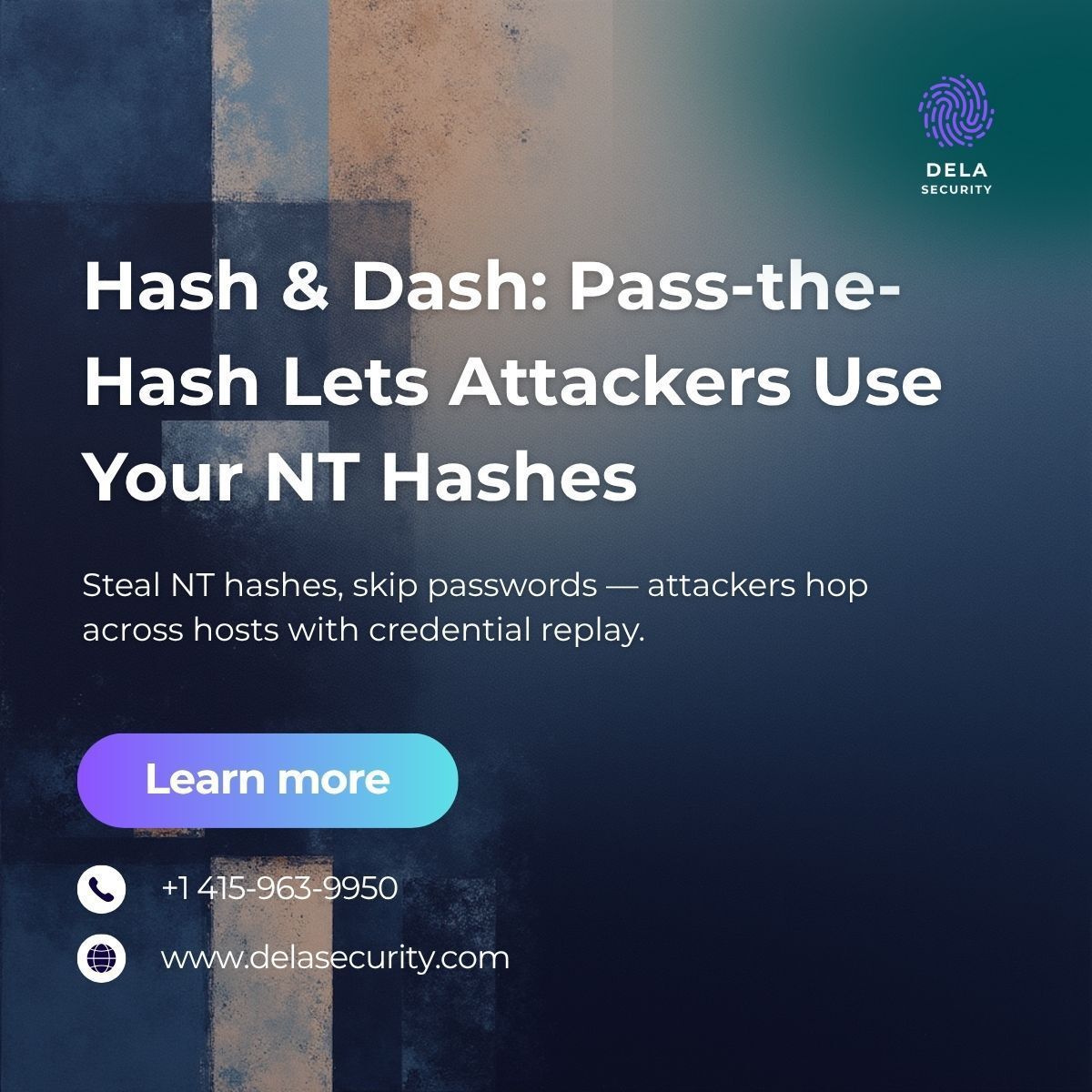
Pass-the-Hash reuses NT hashes to move laterally & escalate privileges. Protect LSA secrets, reduce NTLM, enforce MFA, & monitor unusual logins. Stop attackers from replaying credentials. Learn more: delasecurity.com #IdentitySecurity #DelaSecurity #ActiveDirectory
Passwords are no longer just a user issue. They are an enterprise risk. Join us on Dec 11th to learn how to shift from user effort to enterprise command. Register: hubs.la/Q03VS0hb0 #Passwords #PasswordManagement #IdentitySecurity #EnterpriseIT #BravuraSecurity

Opti, an Israeli AI-driven identity and access management startup, raises $20M seed funding to enhance risk assessment and secure access across finance, healthcare, retail, and tech sectors. #IdentitySecurity #AccessManagement #Israel ift.tt/pjNTWnr
Identity is now a frontline control. Align MFA, governance, and zero trust so daily operations resist account takeover and policy drift. #cybersecurity #infosec #IdentitySecurity #ZeroTrust #MFA
Fortinet reports a 42% year-on-year increase in stolen credentials across the dark web in 2025. 👉 Credentials remain the cheapest path into your castle. buff.ly/xwozOSd fortinet.com #IdentitySecurity #CredentialTheft #ZeroTrust
Opti, a NYC-based provider of an AI-native identity security platform, raised $20M in Seed funding. The company intends to use the funds to expand operations and its development efforts. #Opti #AI #IdentitySecurity #CyberSecurity #TechStartup #SeedFunding

Watch the #Video. #IdentitySecurity reimagined. @OleriaSecurity. Protect what matters with the first adaptive identity security product to give full clarity and control of your access. @Rseewald, founder & Managing Partner @EvolutionEquity explains. youtu.be/OxizeJJLxVU
Perimeters aren’t enough anymore. Learn why protecting user identity is now the real security boundary in modern cyber defense. redsecuretech.co.uk/blog/post/why-… #CyberSecurity #ZeroTrust #IdentitySecurity #DigitalSafety #AccessControl #InfoSec #CyberAwareness

CyberArk is proud to rank 5th on Great Place to Work’s 2025 Best Workplaces in Singapore list—for the third year in a row! Thank you to our amazing team for making this possible. Join us: spr.ly/60117WaXH #GPTWCertified #IdentitySecurity #Cybersecurity

Narayana Health Adopts Saviynt to Strengthen Identity Security #NarayanaHealth #Saviynt #IdentitySecurity #HealthcareCybersecurity #DigitalTransformation #DataProtection #CloudSecurity #IAM #CyberResilience #HealthTechInnovation faceoff.world/news/narayana-…

If you still trust the “voice” on the other end, your breach has already started. #CyberSecurity #DeepfakeThreats #IdentitySecurity #CISO #AIFraud #CyberResilience #BlackFence

#AI agents are the new privileged #MachineIdentities. Are you ready to secure them? Catch our re:Invent session: “AI Agents – The New Face of Privileged Machine Identities” Builder’s Showcase @ 4pm: spr.ly/60167UiJp #IdentitySecurity #AWSreInvent #Cybersecurity

GO VEZA!! Thank you @FastCompany 💪🙏🙌 “As apps, databases, and agents proliferate, companies are hard-pressed to know who has access to what, what they can do with that access, and whether they should even have it ...” #CyberSecurity #IdentitySecurity

AI agents don’t just complete tasks—they evolve. Kaitlin Harvey explains how chaos theory helps us understand unpredictable AI behavior and why identity security matters for safe innovation. Dive into the blog: spr.ly/60107qsQg #IdentitySecurity #AgenticAI #CyberSecurity

We’re excited to announce our partnership with @Carahsoft! Together, we’re making Beyond Identity’s secure-by-design identity and access management platform more accessible to government agencies. Read the details: hubs.la/Q03Mx9dn0 #ZeroTrust #IdentitySecurity…

BIG NEWS: SpecterOps raises $75M Series B to strengthen identity security! Led by @InsightPartners with @AnsaCapital, @M12vc, Ballistic Ventures, @DecibelVC, and @Cisco_Invests. ghst.ly/seriesb #IdentitySecurity #CyberSecurity (1/6)

We’re excited to welcome Ajit Hatti & Atharva Chincholkar @ PureID as they explore how digital passkeys can be hijacked, creating risks for identity theft and unauthorized access. #CyberSecurity #IdentitySecurity #Infosec #Passkeys #DigitalSecurity

Effective Group Policy = control, compliance & clarity. ✔️ Reduce misconfig risks ✔️ Meet regulatory needs ✔️ Simplify admin, boost security 🔒 Strong GPO = strong identity security. #GroupPolicy #IdentitySecurity #CyberSecurity #Netwrix

🔐 Help shape the future of identity security! Share your insights in the 2026 SANS ITDR Survey and make your voice heard in one of the most critical areas of cybersecurity. Take the survey 👉 sansurl.com/itdr-survey #IdentitySecurity #SANS #Cybersecurity @secgreene

Securing access to data everywhere and anywhere. GO VEZA! #cybersecurity #identitysecurity #ZeroTrust

GO VEZA!! @vezainc @Forbes forbes.com/councils/forbe… #IdentitySecurity #Cybersecurity #LeastPrivilege

We are integrating Rubrik Identity Resilience with @CrowdStrike Falcon® Next-Gen Identity Security, advancing #IdentitySecurity by enabling customers to surgically rollback malicious identity changes and restore identity providers to a safe state. Learn more:…




What an incredible week in Riyadh for #PartnerTrustSaudi! We’re inspired by our customers, partners & team as we help organizations across the Kingdom advance their privileged-centric #IdentitySecurity goals. Because partnership is the new perimeter #BeyondTrust #Cybersecurity




Cyber operations depend on robust identity governance that enforces least privilege and continuous verification. @SailPoint enables mission agility through strategic #identitysecurity frameworks. Read here to learn more: carah.io/SailPointCyber…

Cloud @IdentitySummit is back! Save the date and join this event with #IdentitySecurity, #MicrosoftEntra, and #CloudIdentity deep dive sessions in Dortmund, Germany. Call for Papers is open now: sessionize.com/cloud-identity… Stay tuned for more details: identitysummit.cloud

Just wrapped my slide-packed deep dive on taming rogue identities at @The_RMISC w/Gopi. 📸 Huge thanks to everyone who packed the room and kept the Q&A going! #IdentitySecurity #RMISC



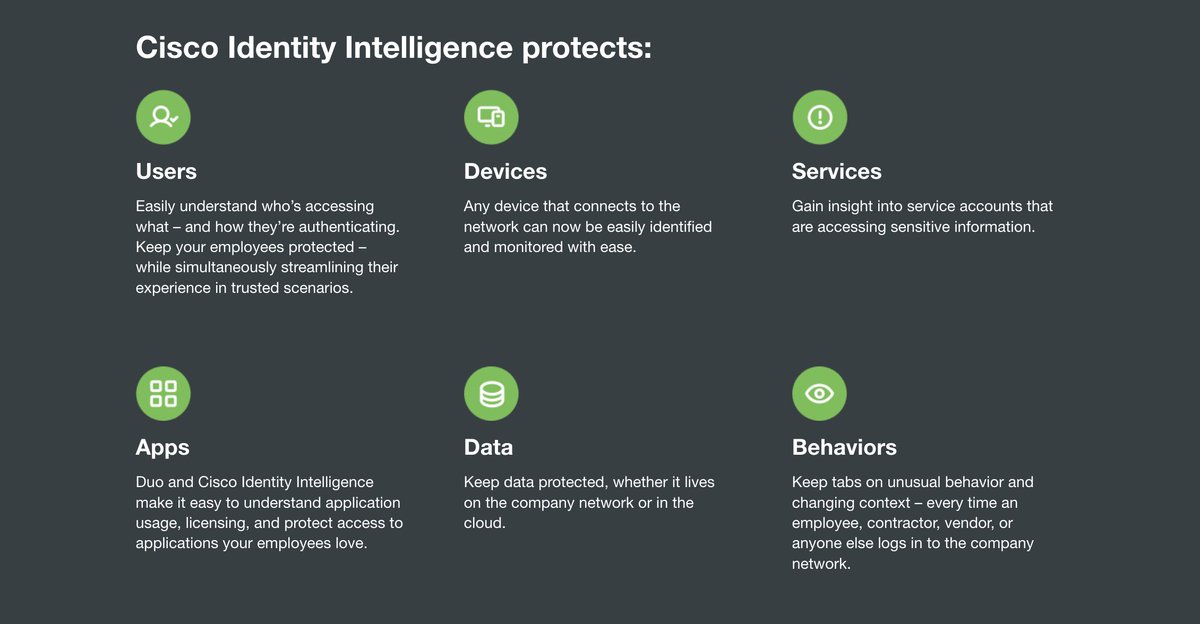
Identity is e v e r y t h i n g. It’s the key to your digital world 🔑 With @Cisco Identity Intelligence, we’ve got your team’s back, so nothing’s holding your organization back 🚀💪 #Identity #IdentitySecurity
Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Thanksgiving 314K posts
- 2. #StrangerThings5 342K posts
- 3. Afghan 394K posts
- 4. #DareYouToDeath 273K posts
- 5. Turkey Day 17.6K posts
- 6. DYTD TRAILER 198K posts
- 7. BYERS 79.2K posts
- 8. Good Thursday 23.4K posts
- 9. Feliz Día de Acción de Gracias N/A
- 10. robin 118K posts
- 11. Taliban 50.7K posts
- 12. #Thankful 4,306 posts
- 13. Vecna 80K posts
- 14. Rahmanullah Lakanwal 152K posts
- 15. Dustin 57.5K posts
- 16. AI Alert 9,617 posts
- 17. Tini 13.2K posts
- 18. #Grateful 2,420 posts
- 19. Nancy 74.6K posts
- 20. Holly 79.3K posts