#linuxmalware search results
#CoinMiners, #Cryptocurrency, #LinuxMalware, Fig:The script was copied from KORKERDS’ Python script for propagation A new Linux coin miner that is capable of deleting previously installed Linux malware, coin miners and services associated with that including the connection ports.

New year brings bad news for Linux as 2021 saw up to 10 times more malware samples #WindowsvsLinux #LinuxMalware neowin.net/news/new-year-…

New Linux Malware “EvilGnome” Spying on Linux Desktop Users and Steal Sensitive Files #cybersecurity #Linuxmalware Read More: gbhackers.com/new-linux-malw…

Learn to build a TLS-secured reverse shell in Python! Encrypt client-server comms with self-signed certs. Explore Linux malware dev here: mohitdabas.in/blog/linux-mal… #CyberSecurity #Python #LinuxMalware #InfoSec #Hacking #malware


FreakOut Malware that Exploits Critical Vulnerabilities in Linux Devices Read More: gbhackers.com/freakout-malwa… #linuxmalware #cybersecuritynews

#Cybersecurity TODAY - May 24th Morning Edition bit.ly/2FkRZn1 #LinuxMalware, #Windows10ZeroDays, #BTRTG

Every major Linux distro has been vulnerable for the last 12 years due to Polkit pkexec flaw #PwnKit #LinuxMalware #Linux neowin.net/news/every-maj…

Join us at the first session of the 2023 SANS Solution Forum, "#ThreatHunting in the Cloud," where we'll address the challenges and opportunities of #ThreatHunting in Linux-based cloud environments. 🎯 Register now to secure your spot: sans.org/webcasts/sans-… #LinuxMalware

Linux Malware Skidmap Uses kernel-mode Rootkits to Hide Cryptocurrency Mining Activities > Stealthy kernel-mode Rootkits > Creates Secret Master Password and Backdoor Access > Hides CPU usage and Network Traffic Read More: gbhackers.com/linux-malware-… #cybersecurity #LinuxMalware

#ArbitraryCodeExecution #Backdoor #LinuxMalware #Malware #CyberAttack #CyberSecurity Multi-Platform Malware “ACBackdoor” Attack Both Windows & Linux Users PC by Executing Arbitrary Code. intezer.com/blog-acbackdoo…

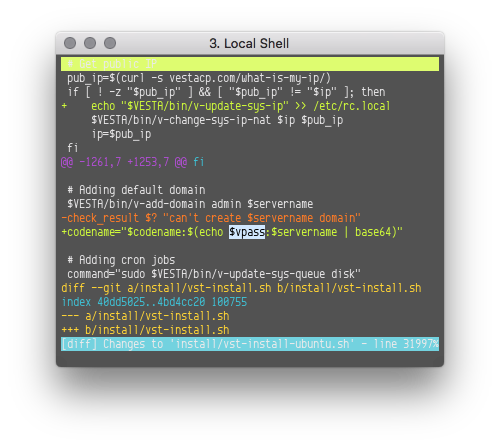
Are you a VestaCP control panel admin? Change your admin password NOW. Then, your server for the presence of Linux/ChachaDDoS. welivesecurity.com/2018/10/18/new… Nice analysis by @marc_etienne_ and @icecr4ck #supplychainattack #linuxmalware
Linux Malware uses Discord emojis for attacks.A new malware campaign uses Discord emojis to communicate with attackers. Patch your systems & report suspicious Discord activity. #cybersecurity #linuxmalware #Discord

FreakOut Malware that Exploits Critical Vulnerabilities in Linux Devices Read More: gbhackers.com/freakout-malwa… #linuxmalware #cybersecuritynews

☣️New Linux malware is controlled through emojis sent from Discord☣️ bleepingcomputer.com/news/security/… #LinuxMalware #DiscordSecurity #CyberThreats #MalwareResearch #CyberSecurity #LinuxSecurity

Three malicious Go modules—`prototransform`, `go-mcp`, and `tlsproxy`—found to obliterate Linux disks, emphasizing supply chain risks. Urgent attention needed to secure software integrity. 💻⚠️ #LinuxMalware #SupplyChainSecurity link: ift.tt/wxy4B5j

💻New Linux Malware Campaign Exploits Oracle Weblogic to Mine Cryptocurrency💻 thehackernews.com/2024/09/new-li… #LinuxMalware #OracleWeblogic #CryptocurrencyMining #CyberSecurity #MalwareAlert #CryptoMining #SecurityThreat #HackNews #WeblogicExploitation #MalwareCampaign

#BrutefourceAttack, #LinuxMalware, #WindowsMalware,#Hacking. Researchers discovered a new brute-force malware called StealthWorker that attack Windows & Linux platform via compromised E-commerce websites to steals personal information and payment data. fortinet.com/blog/threat-re…

A new supply-chain attack targets Linux servers with destructive malware hidden in malicious Go modules on GitHub. Highly obfuscated code can wipe critical data completely. Serious implications ahead! 💻⚠️ #LinuxMalware #GoModules link: ift.tt/1uKZiLH

🐧Linux malware “perfctl” behind years-long cryptomining campaign 🐧 bleepingcomputer.com/news/security/… #LinuxMalware #Cryptomining #CyberSecurity #Malware #ThreatIntel #InfoSec #Cryptocurrency #Hacking #DigitalSecurity

I reminded myself to post this set of screenshots as well. #Windowsmalware #Linuxmalware #Androidmalware #MacOSmalware #jbm111twitch


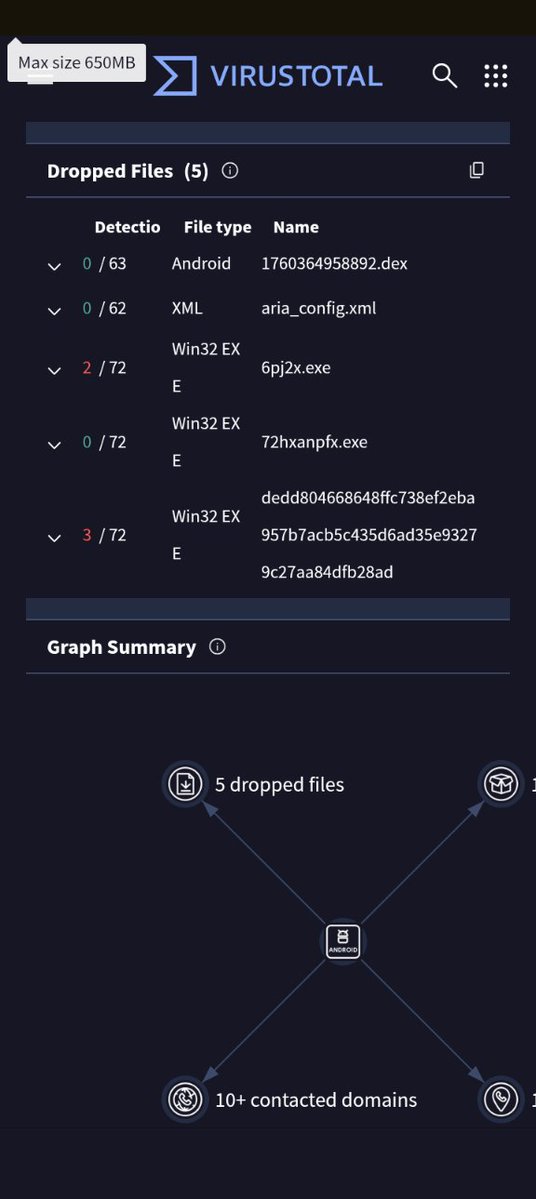
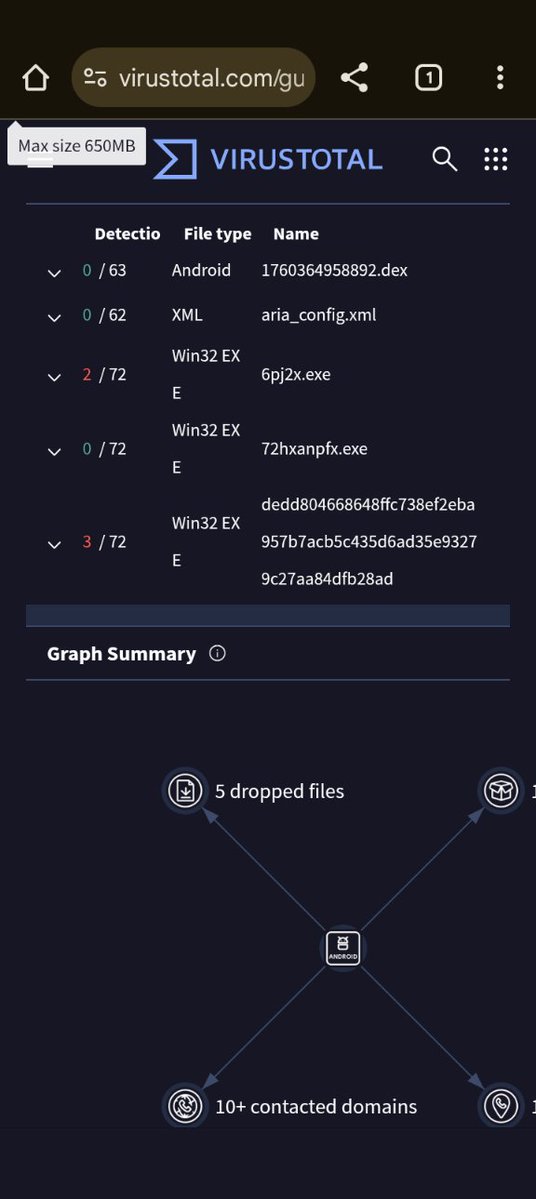
This last set of screenshots is a complete breakdown of what this fork of this piece of Linux malware is always programmed to do in its source code. #Windowsmalware #Linuxmalware #Androidmalware #MacOSmalware #jbm111twitch



This is the third set of screenshots that also shows that it is a fork of a piece of Linux malware that also got ported to MacOS as well. #Windowsmalware #Linuxmalware #MacOSmalware



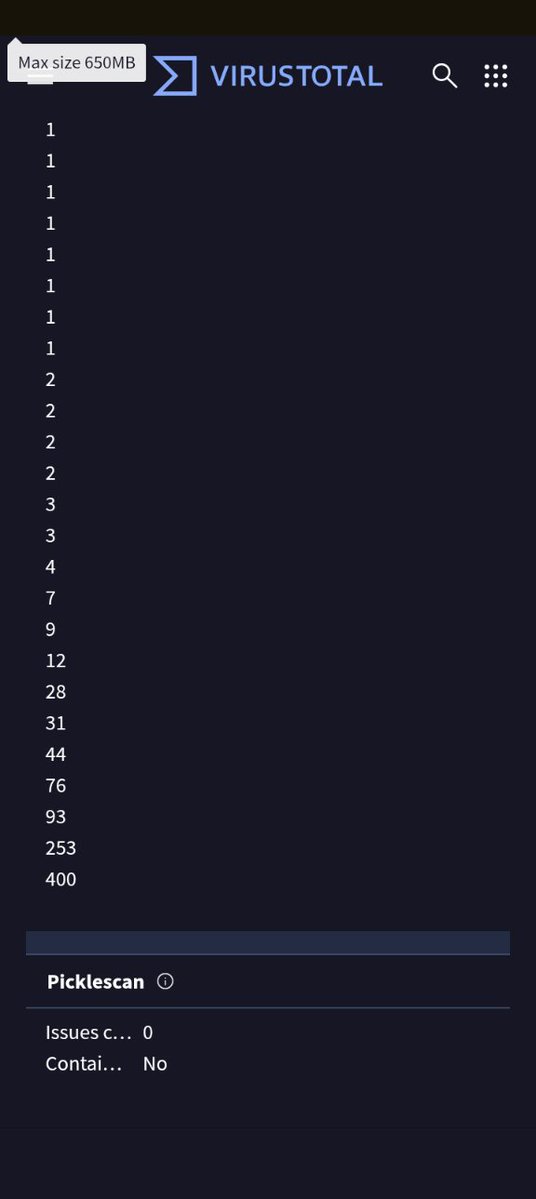
This is the second set of the screenshots from the fully broken down VirusTotal file scan. Note the company, and city in China that it is from. GameSir is the partnering company that keeps helping to keep the development of this emulator going. #Windowsmalware #Linuxmalware




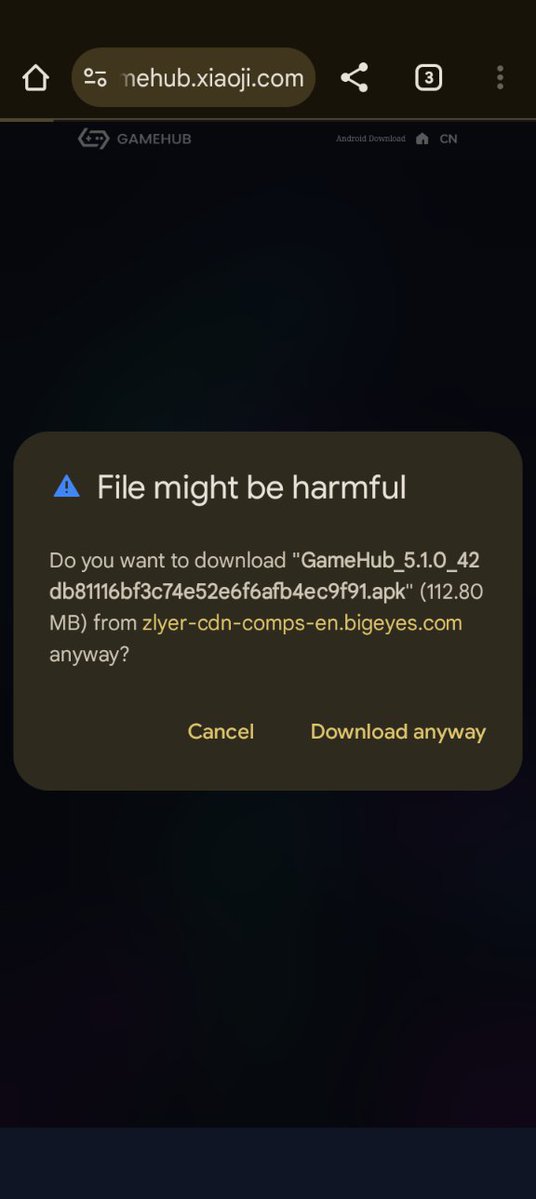
I downloaded the APK before uploading the APK file to VirusTotal' malware scanner. I have 4 more sets of screenshots to post on here . #Windowsmalware #Linuxmalware

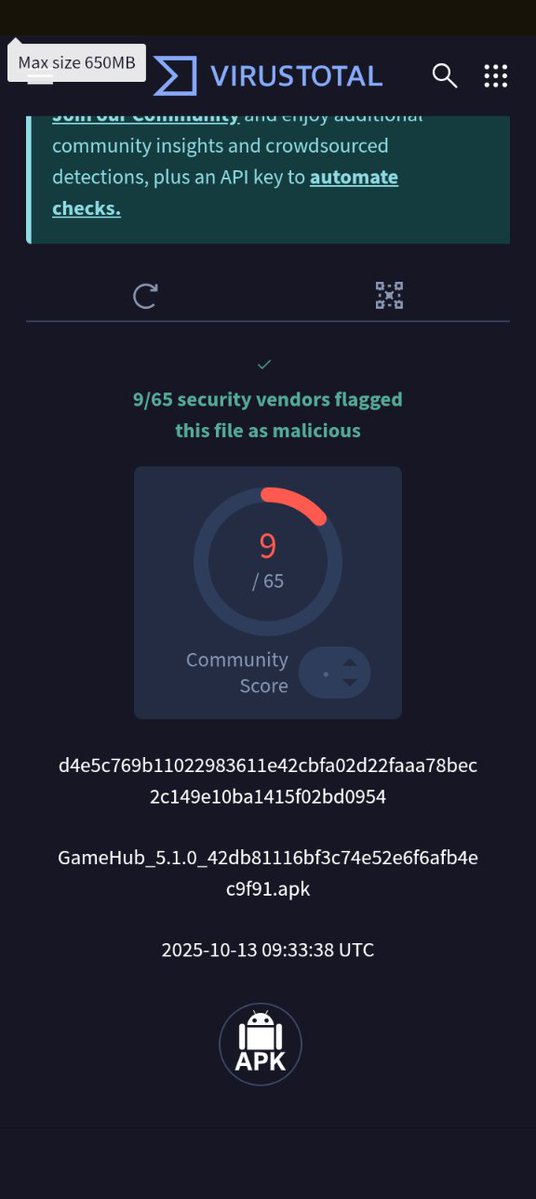


Does that malicious code in the title for that APK file look completely suspicious to you for the official GameHub emulator APK? It does to me. Note the download server URL as well. #Windowsmalware #Linuxmalware #jbm111twitch
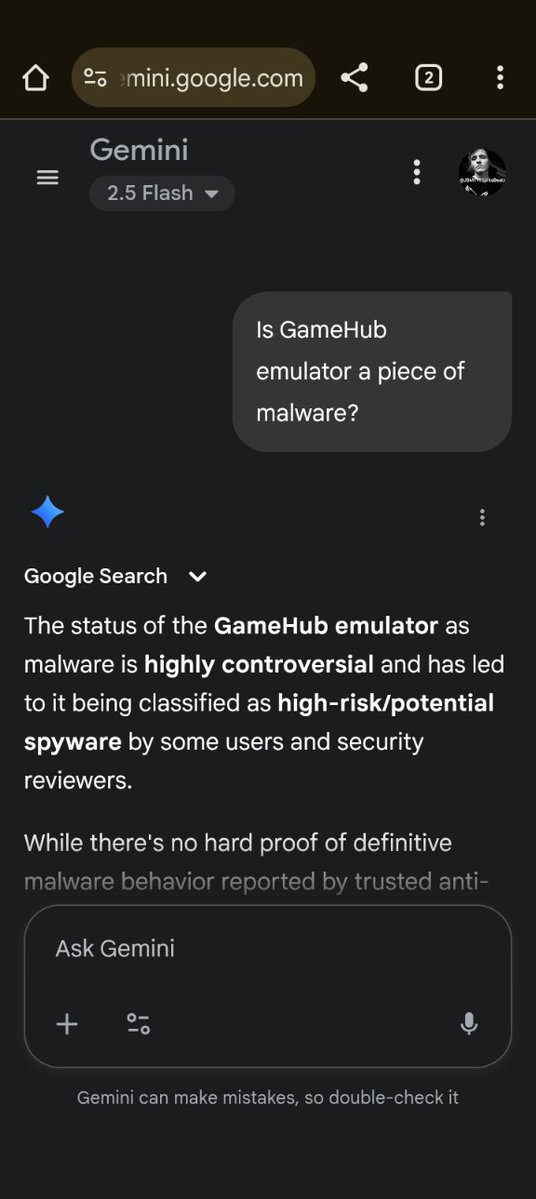
I asked a question to the website version of Google Gemini about GameHub emulator being a piece of malware. These are the first four screenshots i took from it. #GoogleGemini #Windowsmalware #Linuxmalware #jbm111twitch



XLab uncovers MystRodX, a new Linux backdoor hidden in dropper dst86.bin from 139.84.156.79. Features multi-layer XOR/AES encryption, passive DNS/ICMP triggers, and flexible C2 modes linked to active campaigns. #LinuxMalware #Encryption #Singapore ift.tt/NW3xtPL
hendryadrian.com
Mystrodx Covert Dual-Mode Backdoor EN
XLab discovered a novel Linux backdoor—MystRodX—delivered by a dropper dst86.bin from IP 139.84.156.79, featuring multi-layer XOR/AES encryption, passive activation via crafted DNS/ICMP triggers, and...
Linux Malware Delivered via Malicious RAR Filenames Evades Antivirus Detection reconbee.com/linux-malware-… #Linuxmalware #malwareattack #RAR #anitivirus #linux #cyberattack
reconbee.com
Linux Malware Delivered via Malicious RAR Filenames Evades Antivirus Detection
allowing a simple command like eval read more about Linux Malware Delivered via Malicious RAR Filenames Evades Antivirus Detection
A new Linux malware technique uses malicious RAR filenames with encoded Bash commands to bypass antivirus. VShell backdoor deployed via command injection and Base64 in phishing campaigns. #VShellAttack #CommandInjection #LinuxMalware ift.tt/t105fpx
RingReaper malware targets Linux servers, using io_uring to evade EDR solutions. ⚠️ Capabilities: 🔹 Process & network discovery 🔹 Privilege escalation 🔹 Self-destructs to hide traces Our proactive defenses catch what others miss. #RingReaper #LinuxMalware

Plague is a Linux backdoor disguised as a PAM library (libselinux.so.8) enabling persistent SSH access and authentication bypass with hidden passwords and layered obfuscation for stealth and persistence. #LinuxMalware #AuthBypass #Plague ift.tt/GVd8WgD
hendryadrian.com
Plague Linux PAM Backdoor
Researchers discovered Plague, a novel Linux backdoor that masquerades as a PAM library (e.g., libselinux.so.8) to provide persistent, stealthy SSH access and authentication bypass. The implant uses...
New #LinuxMalware Koske hides GPU/CPU cryptominers in AI‑generated panda JPEGs - fully in-memory, stealthy, persistent and likely LLM-assisted. Exploits open JupyterLab servers and unleash rootkits to mine 18+ cyrpto coins. eu1.hubs.ly/H0m2LHC0 #CyberSecurity #Cryptomining
New Koske Linux malware hides in cute panda images reconbee.com/new-koske-linu… #Koskelinuxmalware #linuxmalware #malwareattack #cutepanda #panda #cybersecurity #CybersecurityNews #cyberattack
reconbee.com
New Koske Linux malware hides in cute panda images
taking advantage of online-exposed JupyterLab instance misconfigurations read more about New Koske Linux malware hides in cute panda images
The Prometei botnet is back with a stealthy Linux variant, actively mining Monero and stealing credentials. It uses DGA, custom UPX packing, and sophisticated anti-analysis techniques #PrometeiBotnet #LinuxMalware #Cybersecurity #Cryptomining #Infostealer securityonline.info/prometei-botne…
securityonline.info
Prometei Botnet Evolves: Linux Variant Returns With Stealthier Payloads and Monero Mining Focus
The Prometei botnet is back with a stealthy Linux variant, actively mining Monero and stealing credentials. It uses DGA, custom UPX packing, and sophisticated anti-analysis techniques.
PumaBot, a new Go-based Linux malware, hijacks IoT devices by brute-forcing SSH credentials to spread malicious payloads. #CyberSecurity #IoTThreats #LinuxMalware

#LinuxMalware families evolving to target cloud resources. ELF-based threats, like #NoodleRAT and #Winnti, use dynamic linker hijacking to inject code, hook into services, and exploit vulnerabilities. #ThreatIntelligence #CyberSecurity #onpatrol4malware unit42.paloaltonetworks.com/elf-based-malw…
unit42.paloaltonetworks.com
The Evolution of Linux Binaries in Targeted Cloud Operations
Using data from machine learning tools, we predict a surge in cloud attacks leveraging reworked Linux Executable and Linkage Format (ELF) files. Using data from machine learning tools, we predict a...
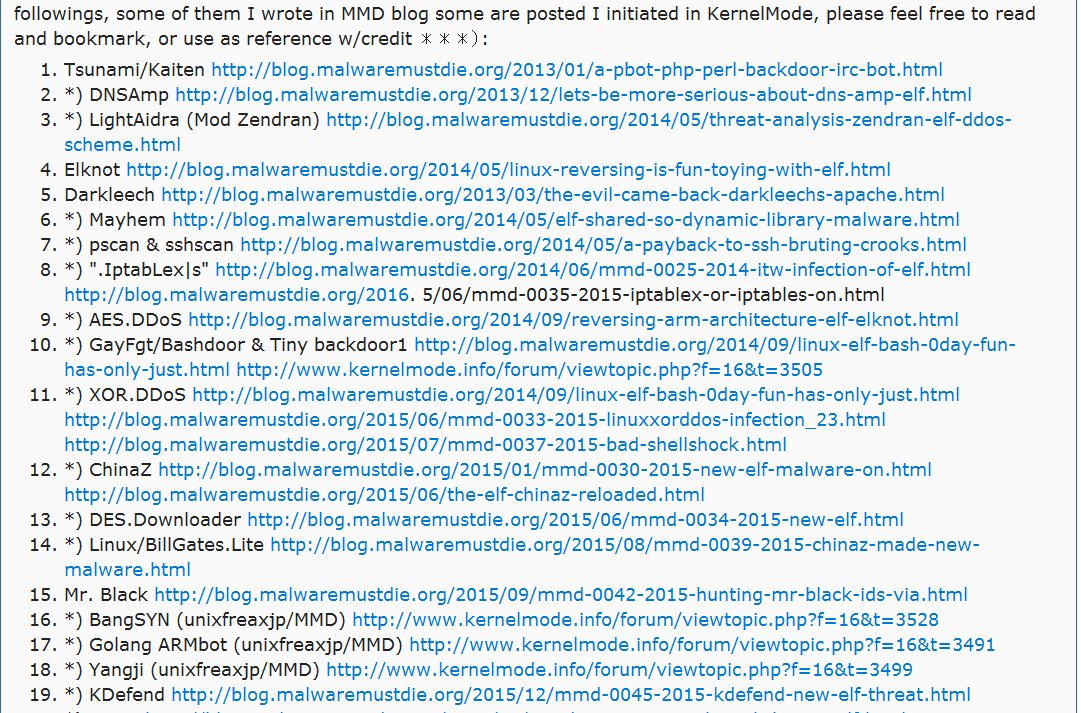
Here the "Full List of MMD #LinuxMalware Analysis Resource" cc: @binitamshah you didn't like? ;) reddit.com/r/LinuxMalware… #MalwareMustDie!
I asked a question to the website version of Google Gemini about GameHub emulator being a piece of malware. These are the first four screenshots i took from it. #GoogleGemini #Windowsmalware #Linuxmalware #jbm111twitch




Here we are on @reddit the "Full List of MMD #LinuxMalware Analysis Resource", #Amazing. Enjoy! :) reddit.com/r/LinuxMalware… #MalwareMustDie!
I downloaded the APK before uploading the APK file to VirusTotal' malware scanner. I have 4 more sets of screenshots to post on here . #Windowsmalware #Linuxmalware




#CoinMiners, #Cryptocurrency, #LinuxMalware, Fig:The script was copied from KORKERDS’ Python script for propagation A new Linux coin miner that is capable of deleting previously installed Linux malware, coin miners and services associated with that including the connection ports.

New Linux Malware “EvilGnome” Spying on Linux Desktop Users and Steal Sensitive Files #cybersecurity #Linuxmalware Read More: gbhackers.com/new-linux-malw…

FUD Linux malware Dropper, Alpha Programming language : Go github.com/nemzyxt/Alpha #cybersecurity #linuxmalware #malware #dropper

New year brings bad news for Linux as 2021 saw up to 10 times more malware samples #WindowsvsLinux #LinuxMalware neowin.net/news/new-year-…

FreakOut Malware that Exploits Critical Vulnerabilities in Linux Devices Read More: gbhackers.com/freakout-malwa… #linuxmalware #cybersecuritynews

☣️New Linux malware is controlled through emojis sent from Discord☣️ bleepingcomputer.com/news/security/… #LinuxMalware #DiscordSecurity #CyberThreats #MalwareResearch #CyberSecurity #LinuxSecurity

🐧Linux malware “perfctl” behind years-long cryptomining campaign 🐧 bleepingcomputer.com/news/security/… #LinuxMalware #Cryptomining #CyberSecurity #Malware #ThreatIntel #InfoSec #Cryptocurrency #Hacking #DigitalSecurity

💻New Linux Malware Campaign Exploits Oracle Weblogic to Mine Cryptocurrency💻 thehackernews.com/2024/09/new-li… #LinuxMalware #OracleWeblogic #CryptocurrencyMining #CyberSecurity #MalwareAlert #CryptoMining #SecurityThreat #HackNews #WeblogicExploitation #MalwareCampaign

I reminded myself to post this set of screenshots as well. #Windowsmalware #Linuxmalware #Androidmalware #MacOSmalware #jbm111twitch




#Cybersecurity TODAY - May 24th Morning Edition bit.ly/2FkRZn1 #LinuxMalware, #Windows10ZeroDays, #BTRTG

Researchers unearth highly evasive “parasitic” Linux malware - helpnetsecurity.com/2022/06/10/sym… - @joakimkennedy @IntezerLabs @BlackBerry #Symbiote #LinuxMalware #Linux #rootkit #LATAM #Financial

RingReaper malware targets Linux servers, using io_uring to evade EDR solutions. ⚠️ Capabilities: 🔹 Process & network discovery 🔹 Privilege escalation 🔹 Self-destructs to hide traces Our proactive defenses catch what others miss. #RingReaper #LinuxMalware

Join us at the first session of the 2023 SANS Solution Forum, "#ThreatHunting in the Cloud," where we'll address the challenges and opportunities of #ThreatHunting in Linux-based cloud environments. 🎯 Register now to secure your spot: sans.org/webcasts/sans-… #LinuxMalware

FreakOut Malware that Exploits Critical Vulnerabilities in Linux Devices Read More: gbhackers.com/freakout-malwa… #linuxmalware #cybersecuritynews

Linux Malware Skidmap Uses kernel-mode Rootkits to Hide Cryptocurrency Mining Activities > Stealthy kernel-mode Rootkits > Creates Secret Master Password and Backdoor Access > Hides CPU usage and Network Traffic Read More: gbhackers.com/linux-malware-… #cybersecurity #LinuxMalware

Something went wrong.
Something went wrong.
United States Trends
- 1. Louisville 48.2K posts
- 2. Jets 129K posts
- 3. MD-11 12.1K posts
- 4. Honolulu 4,150 posts
- 5. Courtois 67.3K posts
- 6. Sauce 87.3K posts
- 7. Madrid 426K posts
- 8. Liverpool 297K posts
- 9. Colts 62.4K posts
- 10. Cheney 273K posts
- 11. UPS Flight 2976 7,387 posts
- 12. Breece Hall 12.7K posts
- 13. Jared Isaacman 4,501 posts
- 14. #いい推しの日 825K posts
- 15. Beane 6,270 posts
- 16. Quinnen Williams 29.7K posts
- 17. McDonnell Douglas 4,699 posts
- 18. Conor Bradley 31.8K posts
- 19. Azzi 5,194 posts
- 20. Sarah Strong N/A