#memoryanalysis search results
MemProcFS-Analyzer v0.9 released with various enhancements. YARA support (incl. 284 rules for malware detection), improved ClamAV scan, Recent Folder Artifacts, Hunting Suspicious Image Mounts, Kroll RECmd Batch File v1.21, and much more. #MemProcFS #MemoryAnalysis #DFIR
🚨 NEWLY UPDATED 🚨 🧠 Struggling w/ #MemoryAnalysis? Our #MemoryForensics Cheat Sheet is here to help! It introduces an analysis framework & covers everything from memory acquisition to live memory analysis & tool usage. 👉 Get your copy: sans.org/u/1Dfb #DFIR

Announcing the release of @Volexity Volcano One: Get the performance, automation, analytics & modernization of Volcano Server PLUS the portability & offline capabilities of Volcano UI Pro. Contact us to learn more: volexity.com/company/contac… #memoryanalysis #memoryforensics #dfir

Virtual Secure Mode and memory acquisition: blog.rekall-forensic.com/2018/09/virtua… #dfir #memoryanalysis

The 13th annual @volatility #PluginContest is OPEN for submissions! This contest is designed to encourage research & development in the field of #memoryanalysis. Every year, contributions from all around the world continue to help build the next generation of #memoryforensics.

Analyzing Memory Dump with Volatility blog.pentesteracademy.com/analyzing-memo… #Pentesting #MemoryAnalysis #Volatility #CyberSecurity #Infosec

.@Volexity Volcano Server & Volcano One v23.07.13 adds 100 new YARA rules & IOCs to detect tampering with ETW, AMSI, Defender + event logging; brute force logins; redirected standard handles + lots of modern Windows rootkit methods. [1/3] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v23.07.13 adds 100 new YARA rules & IOCs to detect tampering with ETW, AMSI, Defender + event logging; brute force logins; redirected standard handles + lots of modern Windows rootkit methods. [1/3]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/F1A5kNHWABQkjQV.jpg)
.@Volexity Volcano Server & Volcano One v24.01.17 adds 150 new YARA rules, new IOCs for credential theft on Windows, and detection of new forms of code injection on Linux. [1/3] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v24.01.17 adds 150 new YARA rules, new IOCs for credential theft on Windows, and detection of new forms of code injection on Linux. [1/3]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/GEPEu1lWsAAfVE9.jpg)
Digital Forensics Tool: Volatility Memory Forensics Framework GitHub Link: github.com/blackhatethica… Support us on Patreon: patreon.com/blackhatethica… More Info: blackhatethicalhacking.com/tools/volatili… #volatility #memoryanalysis #digitalforensics #cybersecurity

We are excited to welcome 5 new @NDengineering @ND_CSE #Summer2021Interns to the @Volexity team! They'll be working at a rapidly growing Washington DC startup this summer to help build #nextgen #memoryanalysis software. #GoIrish #memoryforensics #DFIR

Forensicators, see how this cheatsheet authored by @sibertor can help! It provides a reference for #memoryanalysis operations in #Rekall, covering acquisition, live memory analysis, and parsing plugins. Download it here: digital-forensics.sans.org/u/xs2 #MemoryForensics #FOR526 #DFIR
We just released MemProcFS-Analyzer v1.2.0 with various enhancements. Check out the changelog for more information. Happy Memory Analysis! #MemProcFS #MemoryAnalysis #DFIR github.com/LETHAL-FORENSI…
🔍 Master #memoryforensics with ease! This new cheat sheet supports @SANSInstitute #FOR508, offering insights into #memoryanalysis tools & techniques. A must-have for forensicators in the field. #ThreatHunting #DigitalForensics #DFIR @chadtilbury 👉sans.org/u/1xIr

.@Volexity Volcano Server & Volcano One v24.04.16 adds 75 new YARA rules, as well as new IOCs for hidden home folders, ncat reverse shells, system time changes, and many more. [1/3] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v24.04.16 adds 75 new YARA rules, as well as new IOCs for hidden home folders, ncat reverse shells, system time changes, and many more. [1/3]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/GLezVejWwAAmBhd.jpg)
If you are new to the concept of #MalwareConfigurations and how to parse them at scale, our latest series covers key approaches. We explore their complex nature, value and how we approach the task of building out parsers. #malware #MemoryAnalysis bit.ly/3Vq7iOQ

.@Volexity Volcano Server & Volcano One v23.05.19 adds 125 new YARA rules, many new IOCs incl. process ghosting, integration of Windows registry + event logs into API + timeline results, & a refactored UI/UX alert pane. [1/3] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v23.05.19 adds 125 new YARA rules, many new IOCs incl. process ghosting, integration of Windows registry + event logs into API + timeline results, & a refactored UI/UX alert pane. [1/3]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/Fw5pFFIWwAA8ZE8.jpg)
Análisis cibernético forense en vivo con memoria volátil de computadora. gbhackers.com/live-forensics… #Hacking #Forensics #MemoryAnalysis #Volatile #Malware #Vulnerability #CyberCrime #CyberEspionage #CyberAttack #CyberSecurity

.@Volexity Volcano Server & Volcano One v23.11.22 adds direct cloud integrations + support for analyzing memory from Windows 23H2 & macOS Sonoma, and extends macOS persistence detection. [1/3] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v23.11.22 adds direct cloud integrations + support for analyzing memory from Windows 23H2 & macOS Sonoma, and extends macOS persistence detection. [1/3]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/GAMNIZdW8AAAv9F.jpg)
BETA 1 NOW OPEN | FOR532: Enterprise Memory Forensics In-Depth Understand structured/unstructured #memoryanalysis in #Windows & #Linux OS & how #Memoryforensics fits into modern #DFIR investigations! LIMITED SEATS 👉sans.org/u/1nSc @SANSEMEA @mathias_fuchs

The 13th annual @volatility #PluginContest is OPEN for submissions! This contest is designed to encourage research & development in the field of #memoryanalysis. Every year, contributions from all around the world continue to help build the next generation of #memoryforensics.

🚨 NEWLY UPDATED 🚨 🧠 Struggling w/ #MemoryAnalysis? Our #MemoryForensics Cheat Sheet is here to help! It introduces an analysis framework & covers everything from memory acquisition to live memory analysis & tool usage. 👉 Get your copy: sans.org/u/1Dfb #DFIR

Use Visual Studio Code extensions like "Memory Usage" or "Heap Prof" to analyze your app’s memory consumption. Regularly profile to catch leaks early and optimize performance. #VSCode #MemoryAnalysis #CodingTips @code
No Breach. Just Presence. | HD.39 youtu.be/ITdj-xmMJHk?si… via @YouTube No breach. No escalation. Just entropy archived in silence. The scheduler knows. The log persists.🎥 #PassiveMonitoring #DigitalForensics #MemoryAnalysis #ZeroFootprint #OperationalLogging #HD39
youtube.com
YouTube
No Breach. Just Presence. | HD.39
Use Visual Studio Code extensions like "Memory Usage" or "Heap Prof" to monitor and analyze your app's memory consumption in real-time. Identify leaks early and optimize performance efficiently! #VSCode #MemoryAnalysis #DevTips @code
DeepProbe automates memory forensics across Windows, Linux, and macOS, detecting hidden processes, persistence methods, and suspicious connections. Findings are mapped to MITRE ATT&CK for precise analysis. #MemoryAnalysis #ATTACKFramework #OpenSource ift.tt/bvQ7VyY
Tools like Volatility and Rekall make this possible. It’s forensic x-ray vision — and a must-know skill for modern SOC teams. #DigitalForensics #MemoryAnalysis #CyberSecurity #SOC #IncidentResponse #SOCAnalyst #DFIR
We just released MemProcFS-Analyzer v1.2.0 with various enhancements. Check out the changelog for more information. Happy Memory Analysis! #MemProcFS #MemoryAnalysis #DFIR github.com/LETHAL-FORENSI…
🚨 New Writeup Alert! 🚨 "Memory Analysis Introduction | TryHackMe Write-Up | FarrosFR" by Mochammad Farros Fatchur Roji is now live on IW! Check it out here: infosecwriteups.com/32e865e2a1c0 #farrosfr #tryhackme #memoryanalysis #infosec #security
Volatility 3 🔗 github.com/volatilityfoun… 👤 Volatility Foundation 📌 Reinvented: Modular, plugin-ready, Python 3-compatible forensic memory analysis tool—new codebase for 2025+ threats. #MemoryAnalysis #Vol3Power
PE-sieve – Detects fileless malware & in-memory payloads. From Hasherezade. 🌐 github.com/hasherezade/pe… #MemoryAnalysis #MalwareHunter
🎉 Proud to earn my Memory Analysis badge on Let'sDefend! 📈 Digging deeper into memory forensics to stay sharp on the #BlueTeam side. Onward to more skills and a safer digital world! 🌐 #Cybersecurity #MemoryAnalysis @LetsDefendIO app.letsdefend.io/my-rewards/det…
🔍 Memory Analysis in Action! 🔍 Let’s start investigating: Identify malicious processes and modules. Look for unusual network connections. Analyze suspicious memory artifacts. 💪 Every detail matters in securing our endpoints! #Hezbollah #Pakistan #MemoryAnalysis

🚀 Elevate your forensic investigations with our #MemoryForensics Cheat Sheet, supporting SANS #FOR508. Navigate #memoryanalysis like a pro with this indispensable guide. Perfect for all levels of expertise. #CyberSecurity #DigitalForensics @chadtilbury 👉sans.org/u/1xIr

9/10 Volatility Analyzes volatile memory dumps to identify forensic artifacts. Vital for uncovering what’s happening in memory during an incident! 📊 #Volatility #MemoryAnalysis
.@Volexity Volcano Server & Volcano One v24.09.12 adds 320 new YARA rules, IOCs for reverse shells on Linux, support for non-English unicode, and browser history from RAM [1/4] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v24.09.12 adds 320 new YARA rules, IOCs for reverse shells on Linux, support for non-English unicode, and browser history from RAM [1/4]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/GXx8g5qX0AAEPL9.jpg)
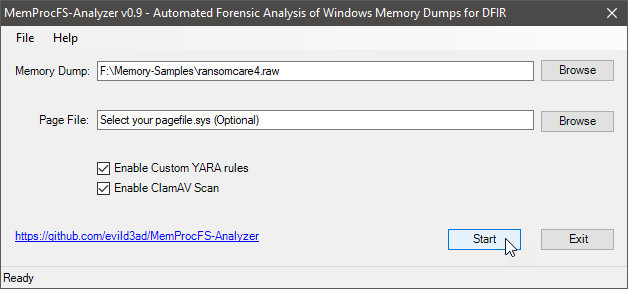
Just released MemProcFS-Analyzer v1.1.0 with various enhancements. Offline-Mode, Prefetch files, Microsoft Protection Logs, MemProcFS.log, 376 YARA rules, and much more. #MemProcFS #MemoryAnalysis #DFIR github.com/evild3ad/MemPr…
🚨 NEWLY UPDATED 🚨 🧠 Struggling w/ #MemoryAnalysis? Our #MemoryForensics Cheat Sheet is here to help! It introduces an analysis framework & covers everything from memory acquisition to live memory analysis & tool usage. 👉 Get your copy: sans.org/u/1Dfb #DFIR

The 13th annual @volatility #PluginContest is OPEN for submissions! This contest is designed to encourage research & development in the field of #memoryanalysis. Every year, contributions from all around the world continue to help build the next generation of #memoryforensics.

MemProcFS-Analyzer v0.9 released with various enhancements. YARA support (incl. 284 rules for malware detection), improved ClamAV scan, Recent Folder Artifacts, Hunting Suspicious Image Mounts, Kroll RECmd Batch File v1.21, and much more. #MemProcFS #MemoryAnalysis #DFIR

Virtual Secure Mode and memory acquisition: blog.rekall-forensic.com/2018/09/virtua… #dfir #memoryanalysis

Announcing the release of @Volexity Volcano One: Get the performance, automation, analytics & modernization of Volcano Server PLUS the portability & offline capabilities of Volcano UI Pro. Contact us to learn more: volexity.com/company/contac… #memoryanalysis #memoryforensics #dfir

Analyzing Memory Dump with Volatility blog.pentesteracademy.com/analyzing-memo… #Pentesting #MemoryAnalysis #Volatility #CyberSecurity #Infosec


Blackstorm Security training courses in Sao Paulo #malware #dfir #memoryanalysis #reverseengineering

Blackstorm Security training courses in Europe and Middle East: #malware #dfir #memoryanalysis #reverseengineering

Forensicators, see how this cheatsheet authored by @sibertor can help! It provides a reference for #memoryanalysis operations in #Rekall, covering acquisition, live memory analysis, and parsing plugins. Download it here: digital-forensics.sans.org/u/xs2 #MemoryForensics #FOR526 #DFIR

#Hacking #Forensics #MemoryAnalysis #Volatile #Malware #Vulnerability #CyberCrime #CyberEspionage #CyberAttack #CyberSecurity Live Cyber Forensics Analysis with Computer Volatile Memory. gbhackers.com/live-forensics…
🔍 Master #memoryforensics with ease! This new cheat sheet supports @SANSInstitute #FOR508, offering insights into #memoryanalysis tools & techniques. A must-have for forensicators in the field. #ThreatHunting #DigitalForensics #DFIR @chadtilbury 👉sans.org/u/1xIr

BETA 1 NOW OPEN | FOR532: Enterprise Memory Forensics In-Depth Understand structured/unstructured #memoryanalysis in #Windows & #Linux OS & how #Memoryforensics fits into modern #DFIR investigations! LIMITED SEATS 👉sans.org/u/1nSc @SANSEMEA @mathias_fuchs

BETA 1 NOW OPEN | FOR532: Enterprise Memory Forensics In-Depth Understand structured/unstructured #memoryanalysis in #Windows & #Linux OS & how #Memoryforensics fits into modern #DFIR investigations! LIMITED SEATS 👉sans.org/u/1nSc @SANSEMEA @mathias_fuchs

We are excited to welcome 5 new @NDengineering @ND_CSE #Summer2021Interns to the @Volexity team! They'll be working at a rapidly growing Washington DC startup this summer to help build #nextgen #memoryanalysis software. #GoIrish #memoryforensics #DFIR

.@Volexity Volcano Server & Volcano One v24.01.17 adds 150 new YARA rules, new IOCs for credential theft on Windows, and detection of new forms of code injection on Linux. [1/3] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v24.01.17 adds 150 new YARA rules, new IOCs for credential theft on Windows, and detection of new forms of code injection on Linux. [1/3]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/GEPEu1lWsAAfVE9.jpg)
.@Volexity Volcano Server & Volcano One v23.07.13 adds 100 new YARA rules & IOCs to detect tampering with ETW, AMSI, Defender + event logging; brute force logins; redirected standard handles + lots of modern Windows rootkit methods. [1/3] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v23.07.13 adds 100 new YARA rules & IOCs to detect tampering with ETW, AMSI, Defender + event logging; brute force logins; redirected standard handles + lots of modern Windows rootkit methods. [1/3]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/F1A5kNHWABQkjQV.jpg)
If you are new to the concept of #MalwareConfigurations and how to parse them at scale, our latest series covers key approaches. We explore their complex nature, value and how we approach the task of building out parsers. #malware #MemoryAnalysis bit.ly/3Vq7iOQ

To enhance examiner’s ability to conduct #MemoryAnalysis, we have added a new option for analyzing Microsoft crash dumps in #AXIOMCyber 7.0 with the integration of #Comae memory analysis technology. Learn all about it here: ow.ly/XcqC50NLhb6 #DFIR

.@Volexity Volcano Server & Volcano One v24.04.16 adds 75 new YARA rules, as well as new IOCs for hidden home folders, ncat reverse shells, system time changes, and many more. [1/3] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v24.04.16 adds 75 new YARA rules, as well as new IOCs for hidden home folders, ncat reverse shells, system time changes, and many more. [1/3]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/GLezVejWwAAmBhd.jpg)
.@Volexity Volcano Server & Volcano One v23.05.19 adds 125 new YARA rules, many new IOCs incl. process ghosting, integration of Windows registry + event logs into API + timeline results, & a refactored UI/UX alert pane. [1/3] #dfir #memoryforensics #memoryanalysis
![Volexity's tweet image. .@Volexity Volcano Server & Volcano One v23.05.19 adds 125 new YARA rules, many new IOCs incl. process ghosting, integration of Windows registry + event logs into API + timeline results, & a refactored UI/UX alert pane. [1/3]
#dfir #memoryforensics #memoryanalysis](https://pbs.twimg.com/media/Fw5pFFIWwAA8ZE8.jpg)
Something went wrong.
Something went wrong.
United States Trends
- 1. Wemby 34.5K posts
- 2. Steph 72.5K posts
- 3. Spurs 31.9K posts
- 4. Draymond 14.5K posts
- 5. Clemson 11.2K posts
- 6. Louisville 11K posts
- 7. Zack Ryder 16.1K posts
- 8. #SmackDown 51.9K posts
- 9. #DubNation 2,049 posts
- 10. Aaron Fox 2,299 posts
- 11. Harden 14.5K posts
- 12. Massie 56.3K posts
- 13. Marjorie Taylor Greene 46.8K posts
- 14. Brohm 1,668 posts
- 15. Dabo 1,995 posts
- 16. Bill Clinton 188K posts
- 17. Mitch Johnson N/A
- 18. UCLA 8,749 posts
- 19. Landry Shamet 5,997 posts
- 20. Matt Cardona 2,925 posts









![LETHAL_DFIR's tweet card. [1.2.0] - 2025-06-24 Added EZTools (.NET 9) DFIR RECmd Batch File v2.11 (2025-03-31) 423 YARA Custom Rules FS_Process_Console FS_SysInfo_Network: DNS Information Digital Signature Fixed Minor fi...](https://pbs.twimg.com/card_img/1988546326569611264/6zS03v38?format=jpg&name=orig)




















