#netsec search results
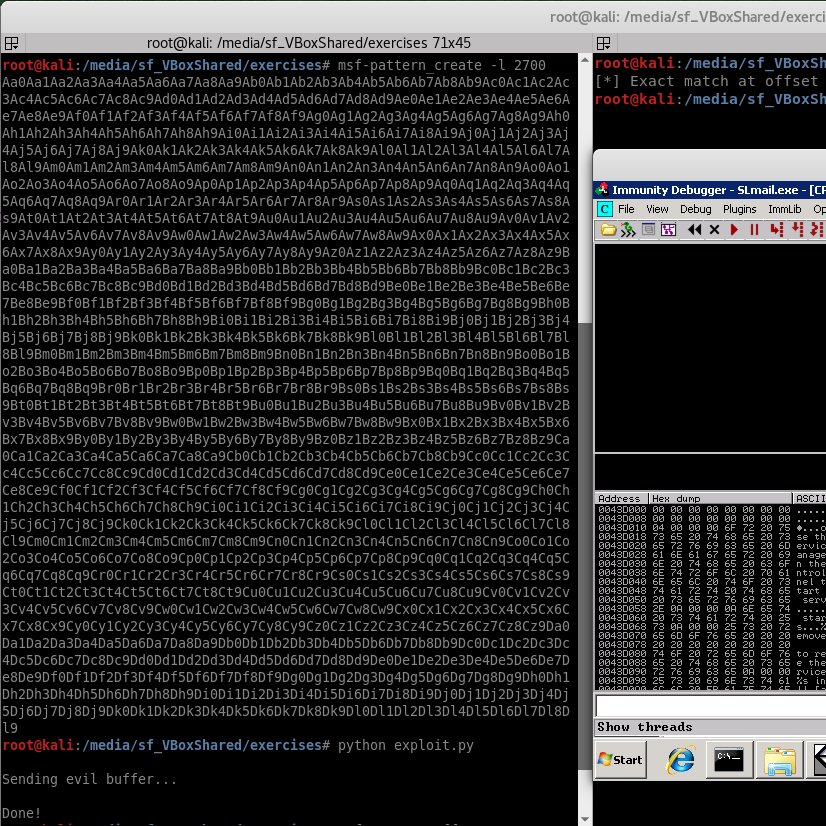
If you are thinking of a good port scanner that is simple and fast, you could check out https://github\.com/nullt3r/jfscan I have tested it and it's pretty accurate. Of course, nothing can replace OG Nmap entirely. #networksec #netsec #infosecurity

📢Call for #NDSSsyposium2025 co-located workshops is now open! ndss-symposium.org/ndss2025/submi… #netsec

Someone's quick and basic recon routine for finding Subdomains while doing Bug Bounty😁✌️ . . #hackers #netsec #bugbountytip #bugbountytips #bugbounty #infosec #redteam #pentesting #pentest #offsec #CTF #OWASP #hacking #cybersecurity #infosec #ethicalhacking #recon

This is what's coming, bof-launcher will become Open Adversary Simulation Kit. Ultimate flexibility and modularity, every piece of the system is a BOF which can be independently replaced. Cross-platform. With memory masking. #netsec #CyberSecurity #offensivesecurity #ziglang

#Telegram CEO caves to Israeli and U.S. pressure. Will now provide user IP addresses to governments upon request. #NetSec #CyberSec » @ZirafaMedia



#NetSec #Research "Generalized Encrypted Traffic Classification Using Inter-Flow Signals", ARES 2025. ]-> MAppGraph - Encrypted Network Traffic Classification using Deep Learning - github.com/soeai/mappgraph // In this paper, we present a novel encrypted traffic classification…
Week in review: WSUS vulnerability exploited to drop Skuld infostealer, PoC for BIND 9 DNS flaw published - helpnetsecurity.com/2025/11/02/wee… - #WeekInReview #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews

My latest work has been published: "CTU Hornet 65 Niner: A network dataset of geographically distributed low-interaction honeypots" The dataset has a unique value for studying the nature of Internet attacks over time. sciencedirect.com/science/articl… #honeypots #netsec #deception

#NetSec #Malware_analysis 1⃣ LinkPro: eBPF rootkit analysis synacktiv.com/en/publication… // LinkPro is a stealthy Linux rootkit utilizing eBPF and user-space techniques for covert process/file hiding, persistent C2, and targeted attacks on AWS for financial gain 2⃣ Defrosting…
Tufin is excited to be at #CPX2024! As a Check Point partner for over 30 years, we know how to automate and improve visibility across your Hybrid, #NetSec, and Cloud environments. Stop by Tufin booth #3 to meet with the team and enter for a chance to win an Avengers Tower Lego!

Join the growing number of #netsec & distributed system security workshops that have co-located with #NDSSsymposium. Submit a proposal by 1 August for next year's event ndss-symposium.org/ndss2025/submi…




Our Trusted Internet Connections (TIC) program released a final version of TIC 3.0 Cloud Use Case for federal agencies operating in a cloud environment. For more info on the new guide along with updates to other TIC resources, visit: go.dhs.gov/4xP #TIC #NetSec #InfoSec

Detect network threats sooner: deep learning for traffic anomaly detection - architectures; features; evaluation - full study: glcnd.io/deep-learning-… #NetSec #AI #Anomaly
Find #netsec inspiration and save money this New Year Register for #NDSSsymposium2025 by 17 January to save up to USD 200 🐤 Student rates are also available. ndss-symposium.org/ndss2025/atten…

Using @openziti or zrok and want to have your voice heard? NetFoundry is looking to hear from you to help drive the roadmap for open source and product features. Talk to @smilindave26, co-founder and CTO! openziti.discourse.group/t/seeking-open… #zerotrust #appsec #netsec #userinput
Tufinnovate 2024 is almost here! Hear from Tufin’s CEO, Ray Brancato, what to expect from our annual user conference. Save your spot now: okt.to/U04wqD #NetSec #Tufinnovate #CyberSecurity
Internet standards need to provide clearer and more rigorous guidelines to overcome #middlebox modifications, writes Ilies Benhabbour pulse.internetsociety.org/blog/http-conf… #IETF #netsec

#tools #NetSec #Offensive_security "Dissecting DCOM, Part 1". // This article aims at giving an introduction to the base principles of COM and DCOM protocols as well as a detailed network analysis of DCOM ]-> DCOM Lateral movement PoC - github.com/deepinstinct/D… ]-> Lateral…
#exploit #NetSec 1. GPOs manipulation and exploitation framework github.com/synacktiv/Grou… // GroupPolicyBackdoor - Python tool for stealthy manipulation of Active Directory GPOs to enable privilege escalation, featuring creation, modification, and removal functions, with safety…
🚨 CVE-2025-58083: General Industrial Controls Lynx... Authentication-free device reset in Lynx+ Gateway exposes industrial systems to complete remote takeover with zero barr... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-58083 - Security Alert
General Industrial Controls Lynx+ Gateway is missing critical authentication in the embedded web server which could allow an attacker to remotely re...
🚨 CVE-2021-4470: TG8 Firewall Unauthenticated RCE ... Trivial root RCE via direct syscmd parameter injection in runphpcmd.php - zero auth required, zero sanitation, maximum i... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2021-4470 - Security Alert
TG8 Firewall contains a pre-authentication remote code execution vulnerability in the runphpcmd.php endpoint. The syscmd POST parameter is passed dire...
🚨 CVE-2025-13188: D-Link DIR-816L authentication.c... Stack-based overflow in DIR-816L's authentication.cgi lets attackers bypass auth with a crafted Password parameter - pu... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-13188 - Security Alert
A vulnerability was detected in D-Link DIR-816L 2_06_b09_beta. Affected by this vulnerability is the function authenticationcgi_main of the file /auth...
🚨 CVE-2025-64446: Fortinet (CVSS: 9.1)... Path traversal in FortiWeb's HTTP handler grants admin command execution across multiple versions - prime target for pe... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-64446 - Security Alert
A relative path traversal vulnerability in Fortinet FortiWeb 8.0.0 through 8.0.1, FortiWeb 7.6.0 through 7.6.4, FortiWeb 7.4.0 through 7.4.9, FortiWeb...
🚨 CVE-2025-36251: AIX Command Execution (CVSS: 9.6... Nimsh SSL/TLS flaws in AIX/VIOS enable remote command execution with CVSS 9.6 - expanding on previous CVE-2024-56347 at... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-36251 - Security Alert
IBM AIX 7.2, and 7.3 and IBM VIOS 3.1, and 4.1 nimsh service SSL/TLS implementations could allow a remote attacker to execute arbitrary commands due t...
🚨 CVE-2025-36250: AIX C... NIM server RCE in AIX/VIOS scores perfect 10.0 CVSS - network-accessible, no auth, no user interaction, complete system compromise. #AIXVuln #RCE. zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-36250 - Security Alert
IBM AIX 7.2, and 7.3 and IBM VIOS 3.1, and 4.1 NIM server (formerly known as NIM master) service (nimesis) could allow a remote attacker to execute ar...
🚨 CVE-2025-36096: AIX Insufficiently Protected Cre... NIM private keys in AIX/VIOS exposed to MITM attacks - classic case of key material stored without proper crypto protec... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-36096 - Security Alert
IBM AIX 7.2, and 7.3 and IBM VIOS 3.1, and 4.1 stores NIM private keys used in NIM environments in an insecure way which is susceptible to unauthorize...
🚨 Zero-days in Cisco ISE + Citrix NetScaler are being exploited right now. This hits the identity plane — the core of enterprise access. Treat identity systems like high-risk assets.⚠️🔐🔥 #Cybersecurity #ZeroDay #NetSec #CiscoISE #Citrix #CyberAlert thecyberlens.com/p/enterprise-a…
🚨 CVE-2025-11367: N-central windows software probe... Deserialization RCE in N-central probe delivers full system compromise with zero authentication - perfect for supply ch... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-11367 - Security Alert
The N-central Software Probe < 2025.4 is vulnerable to Remote Code Execution via deserialization...
🚨 CVE-2025-64709: Typebot May Expose AWS EKS Crede... SSRF in Typebot's webhook block bypasses IMDSv2 to extract EKS node credentials - trivial path from chatbot admin to fu... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-64709 - Security Alert
Typebot is an open-source chatbot builder. In versions prior to 3.13.1, a Server-Side Request Forgery (SSRF) vulnerability in the Typebot webhook bloc...
🚨 CVE-2025-34067: Hikvision Integrated Security Ma... Hikvision's ISMP exposes unauthenticated RCE via Fastjson deserialization in /bic/ssoService/v1/applyCT - trivial LDAP ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-34067 - Security Alert
An unauthenticated remote command execution vulnerability exists in the applyCT component of the Hikvision Integrated Security Management Platform due...
🚨 CVE-2025-34068: Samsung WLAN AP WEA453e < 5.2.4.... Root RCE via unvalidated command1/command2 parameters in Samsung WEA453e "Tech Support" is trivial to exploit and activ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-34068 - Security Alert
An unauthenticated remote command execution vulnerability exists in Samsung WLAN AP WEA453e firmware prior to version 5.2.4.T1 via improper input vali...
⚡ CVE-2025-20355: Cisco Catalyst Center Software H... Open redirect in Catalyst Center's web interface lets attackers hijack HTTP requests without auth - classic vector for ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-20355 - Security Alert
A vulnerability in the web-based management interface of Cisco Catalyst Center Virtual Appliance could allow an unauthenticated, remote attacker to re...
🚨 CVE-2025-12762: Remote Code Execution vulnerabil... Critical command injection in pgAdmin 4's PLAIN-format restore exposes authenticated attackers to server-side RCE with ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-12762 - Security Alert
pgAdmin versions up to 9.9 are affected by a Remote Code Execution (RCE) vulnerability that occurs when running in server mode and performing restores...
🚀🔎🌐 Introducing the all-new Sn1per Enterprise endpoints explorer with HTTP status colors to quickly search, sort and filter all endpoints easily! 🎉👀👨💻 Check it out now at sn1persecurity.com/wordpress/sn1p… #infosec #bugbounty #netsec #offsec #pentest #pentesting #cybersecurity

🚨 CVE-2025-59367: ASUS (CVSS: 9.3)... Remote auth bypass in ASUS DSL routers (pre-1.1.2.3_1010) grants full system access with zero credentials – trivial to ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-59367 - Security Alert
An authentication bypass vulnerability has been identified in certain DSL series routers, may allow remote attackers to gain unauthorized access into ...
🚨 CVE-2021-4464: FIberHome AN5506-04-FA / HG6245D ... Cookie-based stack overflow in FiberHome routers is a textbook RCE vector—just send 512+ bytes and control EIP. No auth ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2021-4464 - Security Alert
FiberHome AN5506-04-FA firmware versions up to and including RP2631 and HG6245D prior to RP2602 contain a stack-based buffer overflow, as the HTTP ser...
⚡ CVE-2025-62453: GitHub Copilot and Visual Studio... Copilot's local security bypass lets attackers inject malicious code suggestions that circumvent VS Code's validation g... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-62453 - Security Alert
Improper validation of generative ai output in GitHub Copilot and Visual Studio Code allows an authorized attacker to bypass a security feature locall...
⚡ CVE-2025-62206: Microsoft Dynamics 365 (On-Premi... On-prem Dynamics 365 leaking sensitive data with no authentication required - just remote user interaction. Network att... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-62206 - Security Alert
Exposure of sensitive information to an unauthorized actor in Microsoft Dynamics 365 (on-premises) allows an unauthorized attacker to disclose informa...
🚨 CVE-2025-42887: Code Injection vulnerability in ... SAP Solution Manager remote function module injection grants full system control with minimal authentication - trivial ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-42887 - Security Alert
Due to missing input sanitation, SAP Solution Manager allows an authenticated attacker to insert malicious code when calling a remote-enabled function...
🩻The enigmatic figure of #USDoD (formerly #NetSec on #RaidForums) stands as a testament to the evolving landscape of #cybersecurity, representing the new age of #hackers. The #threatactor has returned, aiming to revitalize #BreachForums. Read more👇 socradar.io/unmasking-usdo…

Someone's quick and basic recon routine for finding Subdomains while doing Bug Bounty😁✌️ . . #hackers #netsec #bugbountytip #bugbountytips #bugbounty #infosec #redteam #pentesting #pentest #offsec #CTF #OWASP #hacking #cybersecurity #infosec #ethicalhacking #recon

#Telegram CEO caves to Israeli and U.S. pressure. Will now provide user IP addresses to governments upon request. #NetSec #CyberSec » @ZirafaMedia



Yup. Our students have been busy. #netsec

Spent most of today preparing the NOC talk for the last class of our Introduction to Security class tomorrow. This is the class were we show students all the behind the scene of the class: network, infrastructure, technologies used, and some highlights on our network monitoring.
unfurl is awesome 🚀 Pull bits out of URLs including domains, TLDs, paths, apexes and so much more! Definitely worth checking out. Another great tool from @tomnomnom 😎 #hackers #netsec #bugbountytip #bugbountytips #bugbounty #infosec #redteam #pentesting #pentest #offsec

If you are thinking of a good port scanner that is simple and fast, you could check out https://github\.com/nullt3r/jfscan I have tested it and it's pretty accurate. Of course, nothing can replace OG Nmap entirely. #networksec #netsec #infosecurity

My latest work has been published: "CTU Hornet 65 Niner: A network dataset of geographically distributed low-interaction honeypots" The dataset has a unique value for studying the nature of Internet attacks over time. sciencedirect.com/science/articl… #honeypots #netsec #deception

Getting RCE and arbitrary file disclosure with Ghostscript & PostScript + Bypasses (CVE-2023-36664 and CVE-2023-43115) blog.redteam-pentesting.de/2023/ghostscri… #bugbountytips #appsec #netsec #infosec #cybersecurity #vulnerability #bugbounty


Week in review: WSUS vulnerability exploited to drop Skuld infostealer, PoC for BIND 9 DNS flaw published - helpnetsecurity.com/2025/11/02/wee… - #WeekInReview #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews

Our Trusted Internet Connections (TIC) program released a final version of TIC 3.0 Cloud Use Case for federal agencies operating in a cloud environment. For more info on the new guide along with updates to other TIC resources, visit: go.dhs.gov/4xP #TIC #NetSec #InfoSec

OpenDoor – OWASP WEB Directory Scanner skynettools.com/opendoor-owasp… #infosec #netsec #pentest #cybersecurity #bugbounty

Smart File Hunter – Identify Files That Contain Sensitive Information Like Passwords & Private Keys skynettools.com/smart-file-hun… #infosec #netsec #pentest #cybersecurity #bugbounty

In WHAT alternate universe does it make sense to plug in your SIN# to a website? Sure as hell not in this one. What's scarier yet - this is a LEGIT email from a supplier I do business with. #netsec

📢Call for #NDSSsyposium2025 co-located workshops is now open! ndss-symposium.org/ndss2025/submi… #netsec

EasyPark has had a cyber attack resulting in a breach of non-sensitive customer data: Names, phone numbers, physical addresses, email addresses and some digits from credit/debit cards or IBAN. Read EasyPark's official statement here: easypark.com/en-de/comm #CyberSec #netsec

#NetSec has undergone several cycles of evolution (three eras to be precise). So, what’s next? Read more in the @Optiv blog. dy.si/Xx8tuJ

Nessuno è immune al furto dello smartphone, ma potete fare in modo che i ladri non si impossessino nemmeno di un byte dei vostri dati sensibili. >> kaspersky.it/blog/how-to-th…… #cybersec #infosec #netsec #mobile

AUTOMATE THE MOST POWERFUL SECURITY TOOLS Check our YouTube channel to see how Sn1per can help your security team! youtube.com/c/Sn1perSecuri… External Attack Surface Management | Offensive Security | Penetration Testing | OSINT | Bug Bounty #infosec #bugbounty #netsec #offsec
Week in review: 300k+ Plex Media Server instances still vulnerable to attack, exploited Git RCE flaw - helpnetsecurity.com/2025/08/31/wee… - #WeekInReview #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews

Something went wrong.
Something went wrong.
United States Trends
- 1. Massie 93.9K posts
- 2. #Varanasi 194K posts
- 3. #CollegeGameDay 2,026 posts
- 4. Lawson Luckie N/A
- 5. #MeAndTheeSeriesEP1 1.38M posts
- 6. Good Saturday 36K posts
- 7. Todd Snider N/A
- 8. #Caturday 4,928 posts
- 9. Willie Green 4,894 posts
- 10. #SaturdayVibes 5,339 posts
- 11. Brooklynn 3,948 posts
- 12. Virginia Tech 2,443 posts
- 13. Senior Day 2,824 posts
- 14. Draymond 31K posts
- 15. James Borrego 1,753 posts
- 16. Marjorie 116K posts
- 17. PONDPHUWIN AT MAT PREMIERE 881K posts
- 18. Mike Elko N/A
- 19. Lindsey Graham 21.4K posts
- 20. Raskin 19.6K posts