#networksegmentation search results
Join Catherine and the crew at @ExertisBrdcast as they discuss how to secure your network and prevent cyberattacks in the latest episode of Techsplanation 2.0. Watch the full episode: bit.ly/3DOVTk7 #cyberattack #kvm #networksegmentation #airgapping #matroxvideo #ipkvm
Use isolated network segments for darknet activities. #NetworkSegmentation #DarknetOps #SecureArchitecture
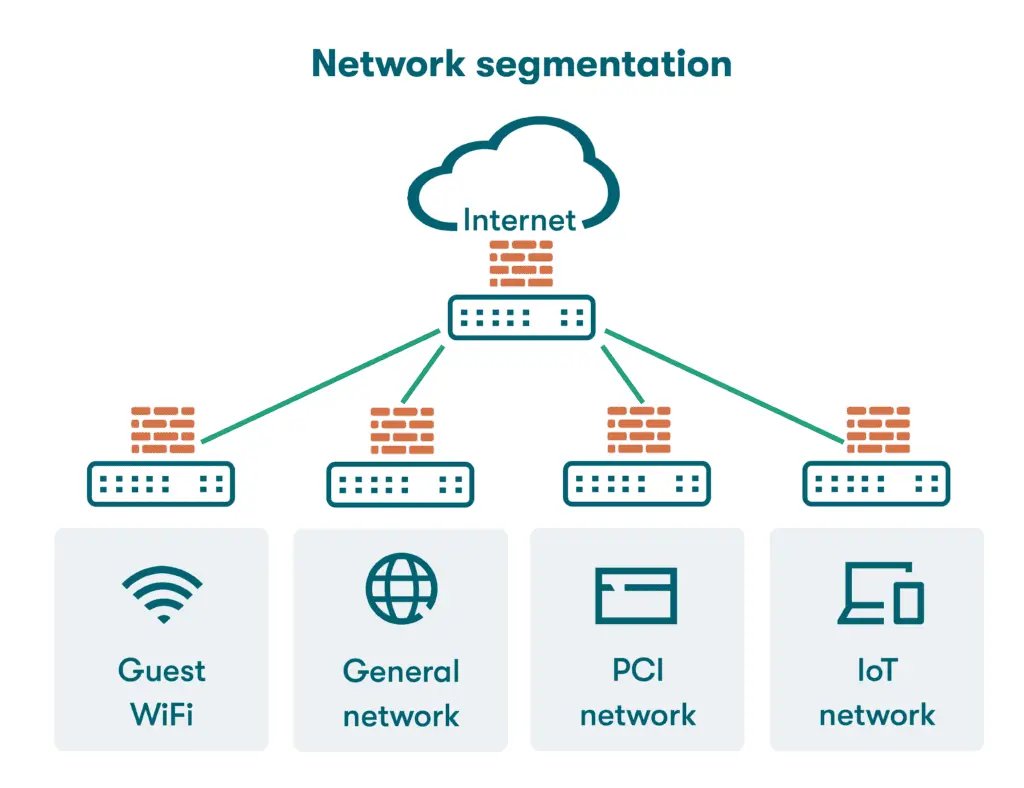
Segmentation limits damage—but only if traffic rules are enforced and monitored. Unchecked connections turn ‘protected zones’ into false security. #NetworkSegmentation #CyberResilience #DefenseInDepth #ArcherEnergySolutions

Claroty was named a Leader in IoT Security, receiving the highest possible scores in 10 criteria and the only Leader to earn the highest scores in #NetworkSegmentation & microsegmentation, deployment options, and partner ecosystem. 📌 hubs.li/Q03Kbjh40

⚡ Ask Archer: True resilience isn’t just isolation. Layered defenses, strong access controls, and continuous monitoring work together to protect critical systems from evolving threats. 📩 [email protected] #AskArcher #NetworkSegmentation #CriticalInfrastructure


Why network segmentation matters for bolstering cybersecurity: - 𝗟𝗶𝗺𝗶𝘁𝗶𝗻𝗴 𝗕𝗿𝗲𝗮𝗰𝗵 𝗜𝗺𝗽𝗮𝗰𝘁 🌐 - 𝗘𝗻𝗵𝗮𝗻𝗰𝗲𝗱 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗖𝗼𝗻𝘁𝗿𝗼𝗹𝘀 🛡️ - 𝗜𝗺𝗽𝗿𝗼𝘃𝗲𝗱 𝗜𝗻𝗰𝗶𝗱𝗲𝗻𝘁 𝗥𝗲𝘀𝗽𝗼𝗻𝘀𝗲 📜 #Cybersecurity #NetworkSegmentation #Defense

Protecting your OT network is crucial! Downtime, financial loss, and even human costs are on the line. Read the full blog: hubs.ly/Q02LbJKv0 #Cybersecurity #OTSecurity #NetworkSegmentation #RiskManagement #ZeroTrust #CriticalInfrastructure

#SonicWall Do you want to reduce attack surfaces and better secure your network? SonicWall’s 5-point #networksegmentation checklist can help. Enhance your defense strategy, control access to critical assets, and minimize damage if a breach occurs. Get it…

Maximize gateway security with network segmentation to protect sensitive data, deploy multiple distributed gateways to avoid single points of failure, and enhance performance across hybrid and remote environments. #NetworkSegmentation #HybridWork ift.tt/kqWGuQh
Navigating the Challenges of #NetworkSegmentation and Microsegmentation Without Disrupting Operations - buff.ly/3XOXbDS #IT #technology #cybersecurity #security #ITsecurity #infosec

#NetworkSegmentation is evolving with the expanding XIoT landscape. In this blog, read how to speed up segmentation without slowing down operations, and why a proactive strategy makes all the difference. hubs.li/Q03xBkmw0

Being proactive is key to a successful #cybersecurity strategy. Leverage SonicWall’s 5-point #networksegmentation checklist to reduce attack surfaces, enhance defenses, and secure your network. Learn more ➡️ bit.ly/3IeqtG9

🔒Enhance your network security with these 4 network segmentation types🌐 Physical, Logical, Wireless, and Device segmentation. Each provides layers of protection, safeguarding your digital assets. #CyberSecurity #NetworkSegmentation #ZeroTrust #InstaSafe

𝗔𝗜 𝗶𝘀 𝘁𝗿𝗮𝗻𝘀𝗳𝗼𝗿𝗺𝗶𝗻𝗴 𝗯𝘂𝘀𝗶𝗻𝗲𝘀𝘀𝗲𝘀. I𝘀 𝗶𝘁 𝗹𝗲𝗮𝘃𝗶𝗻𝗴 𝘆𝗼𝘂 𝗲𝘅𝗽𝗼𝘀𝗲𝗱 𝘁𝗼 𝗰𝘆𝗯𝗲𝗿 𝘁𝗵𝗿𝗲𝗮𝘁𝘀? 🤔cttsonline.com/2025/02/26/why… #CyberSecurity #AI #NetworkSegmentation #ITSecurity #TechTips #CTTSonline #GeorgetownTX #RoundRockTX #AustinTX

Don’t let your network be vulnerable to a single attack. By segmenting your network you can keep your sensitive data secure and minimize risk. Scroll through to see our top network segmentation tips. #NetworkSegmentation #CyberSecurityTips




What Is #NetworkSegmentation and Why It Matters #sme #businesstips - businesspartnermagazine.com/what-network-s…
Find guidelines to evaluate zero trust network segmentation solutions. bit.ly/42Tph3r #networksegmentation #zerotrust #informationsecurity

Research shows that large numbers of Operational and Clinical #IoT assets ship with known vulnerabilities, and in many cases are not (or cannot be) routinely patched. Find out how #NetworkSegmentation can help improve your Cyber Posture. #IoMT hubs.ly/Q01QtFpP0

Up-level your #cybersecurity with SonicWall’s 5-point #networksegmentation checklist. Enhance your defenses, control access to critical assets and better secure your network. Rethink your network segmentation strategy today. Learn more here: bit.ly/3IeqtG9

Discover hidden assets with Enclave's Asset Inventory features. Your network is visualized with Enclave. hubs.la/Q021TFfB0 #networksegmentation #infosec

12/14 Entreprises, segmentez vos réseaux ! Un intrus ne doit jamais passer du mail à la diffusion. Cloisonnez vos systèmes critiques. Sans murs, une brèche devient un effondrement. #TV5Monde #Cybersecurité #NetworkSegmentation

Cyber Definition: Network Segmentation #Cybersecurity #Definition #NetworkSegmentation #Breach #ArcherEnergySolutions

Cyber Fact 163 #Cybersecurity #Facts #NetworkSegmentation #CriticalInfrastructure #Breach #ArcherEnergySolutions

Flat networks are a hacker’s playground. Segmentation creates chokepoints that slow intruders and buy defenders time. #NetworkSegmentation #CyberDefense #OTSecurity #ArcherEnergySolutions

Data diodes enforce one-way traffic. Great for integrity, but don’t expect them to solve every security challenge. #DataDiodes #NetworkSegmentation #OTSecurity #ArcherEnergySolutions

Segmentation limits damage—but only if traffic rules are enforced and monitored. Unchecked connections turn ‘protected zones’ into false security. #NetworkSegmentation #CyberResilience #DefenseInDepth #ArcherEnergySolutions

Cyber Fact 164 #Cybersecurity #Facts #NetworkSegmentation #Attack #CriticalInfrastructure #ArcherEnergySolutions

⚡ Ask Archer: True resilience isn’t just isolation. Layered defenses, strong access controls, and continuous monitoring work together to protect critical systems from evolving threats. 📩 [email protected] #AskArcher #NetworkSegmentation #CriticalInfrastructure


Claroty was named a Leader in IoT Security, receiving the highest possible scores in 10 criteria and the only Leader to earn the highest scores in #NetworkSegmentation & microsegmentation, deployment options, and partner ecosystem. 📌 hubs.li/Q03Kbjh40

Use isolated network segments for darknet activities. #NetworkSegmentation #DarknetOps #SecureArchitecture

The Purdue Model isn’t just theory—it’s a map for survival. Without proper segmentation, a breach at the corporate level can cascade down to control systems. #PurdueModel #NetworkSegmentation #CyberResilience #ArcherEnergySolutions

Keep checking vulnerabilities of cyber infra to prevent cyberattacks! #cybersecurity #networksegmentation

Being proactive is key to a successful #cybersecurity strategy. Leverage SonicWall’s 5-point #networksegmentation checklist to reduce attack surfaces, enhance defenses, and secure your network. Learn more ➡️ bit.ly/3IeqtG9

Why network segmentation matters for bolstering cybersecurity: - 𝗟𝗶𝗺𝗶𝘁𝗶𝗻𝗴 𝗕𝗿𝗲𝗮𝗰𝗵 𝗜𝗺𝗽𝗮𝗰𝘁 🌐 - 𝗘𝗻𝗵𝗮𝗻𝗰𝗲𝗱 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗖𝗼𝗻𝘁𝗿𝗼𝗹𝘀 🛡️ - 𝗜𝗺𝗽𝗿𝗼𝘃𝗲𝗱 𝗜𝗻𝗰𝗶𝗱𝗲𝗻𝘁 𝗥𝗲𝘀𝗽𝗼𝗻𝘀𝗲 📜 #Cybersecurity #NetworkSegmentation #Defense

𝗔𝗜 𝗶𝘀 𝘁𝗿𝗮𝗻𝘀𝗳𝗼𝗿𝗺𝗶𝗻𝗴 𝗯𝘂𝘀𝗶𝗻𝗲𝘀𝘀𝗲𝘀. I𝘀 𝗶𝘁 𝗹𝗲𝗮𝘃𝗶𝗻𝗴 𝘆𝗼𝘂 𝗲𝘅𝗽𝗼𝘀𝗲𝗱 𝘁𝗼 𝗰𝘆𝗯𝗲𝗿 𝘁𝗵𝗿𝗲𝗮𝘁𝘀? 🤔cttsonline.com/2025/02/26/why… #CyberSecurity #AI #NetworkSegmentation #ITSecurity #TechTips #CTTSonline #GeorgetownTX #RoundRockTX #AustinTX

Via @ElisityInc: At RSAC 2025, @Claroty's Skip Sorrels explored the revolutionary transformation of #NetworkSegmentation in #healthcare environments, highlighting how modern solutions are finally solving decade-old challenges. 🎥 Watch here: hubs.li/Q03rpHks0

Navigating the Challenges of #NetworkSegmentation and Microsegmentation Without Disrupting Operations - buff.ly/3XOXbDS #IT #technology #cybersecurity #security #ITsecurity #infosec

⏰ LAST CALL to join TOMORROW's webinar with #cybersecurity leaders from @Claroty, @Cisco, and @ChildrensLA, who'll share the secrets to overcoming #NetworkSegmentation challenges. 📌 Sign up now: hubs.li/Q02Fvk1R0

Coming up Sep. 26: Join us for a live webinar and Q&A on #NetworkSegmentation in clinical environments. See how Medigate by @Claroty can reduce resources and boost segmentation initiatives across your full #cybersecurity journey. Register here: bit.ly/47ObWvQ

🔏 Journey into hospital #cybersecurity with this series on the #NetworkSegmentation of medical devices, feat. interviews with hospital systems expoert, who'll offer insights into their experiences, challenges, and triumphs. Sign up here: hubs.li/Q02BfxJ_0
Do you want to reduce attack surfaces and better secure your network? SonicWall’s 5-point #networksegmentation checklist can help. Enhance your defense strategy, control access to critical assets, and minimize damage if a breach occurs. Get it here: bit.ly/3IeqtG9

Something went wrong.
Something went wrong.
United States Trends
- 1. #DWTS 31.3K posts
- 2. Virginia 382K posts
- 3. New York 695K posts
- 4. Andy 57.9K posts
- 5. Jay Jones 66.7K posts
- 6. Alix 6,533 posts
- 7. #Election2025 11.1K posts
- 8. Whitney 9,706 posts
- 9. Louisville 111K posts
- 10. Elaine 56.2K posts
- 11. Zohran Mamdani 440K posts
- 12. #WWENXT 11.7K posts
- 13. Danielle 8,234 posts
- 14. Flav 6,254 posts
- 15. Abigail Spanberger 53.1K posts
- 16. Desmond Bane 1,222 posts
- 17. Mikie Sherrill 68.1K posts
- 18. Cuomo 343K posts
- 19. WOKE IS BACK 10.7K posts
- 20. Isaiah Evans N/A






















