#securityrequirements search results
POST Security requirements 🔓 #security #Securityrequirements #securityawareness #cybersecurity #cybersecurityawareness #cybersecuritynews #cyberattack #informationsecurity #infosec #informationsecurityawareness #datasecurity #dataservices #cloudsecurity #securityawareness

#TestableRequirements #SecurityRequirements #TestableSecurityRequirements #NEIS0736 #SoftwareSecurity

#SecurityRequirements for the #InternetofThings: A Systematic Approach @Macquarie_Uni 👉mdpi.com/1424-8220/20/2… #IoT #accesscontrol
Think about this; when was your #houseinsurance last reviewed? Do you know the #policy #securityrequirements? What are the #policylimits for your #valuables? As your home is the biggest single purchase you will ever make, it pays to check the #smallprint to protect it!

Have a look at our rule of the week 💻 R356. Verify sub-domain names. With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3hMRTDD #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🚪 R154. Eliminate backdoors With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3cgvc95 #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 📱 R328. Request MFA for critical systems With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3gsuWVF #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔒 R030. Avoid object reutilization With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3hqZyqW #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 📱 R362. Assign MFA mechanisms to a single account With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/33CGstL #securityrules #securityrequirements #wehackyoursoftware

Have a look at our rule of the week 📕 R088. Request client certificates 🔗 Visit the complete list and details here: bit.ly/3jVHMgA With Fluid Attacks, you can decide what you want us to test. #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔑 R128. Define unique data source With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/2EDVe9I #securityrules #securityrequirements #pentesting #wehackyoursoftware

Presenting a heuristic approach for #risktreatment based on a distinct terminology for #securityrequirements in: “Heuristic Risk Treatment for ISO/SAE 21434 Development Projects“ by C. Jakobs, M. Werner, K. Schmidt, G.Hansch. ACSIS Vol. 30 p. 653–662; tinyurl.com/2j63anxm

Have a look at our rule of the week 🔏 R039. Define unique data source With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3eqda5d #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔑 R361. Define unique data source With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/34c5obz #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔐 R045. Define unique data source With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3peakW7 #securityrules #securityrequirements #pentesting #wehackyoursoftware

It’s a wrap! The second GA was very intensive, with passionate discussions about #automatedmonitoring #securityrequirements #evidencemanagement #assessment. More info: 💻Medina-project.eu
To ensure third-party vendors and partners undergo #penetrationtesting, incorporate contractual clauses mandating regular testing, and set clear #securityrequirements as part of the onboarding process. Regularly assess their security practices and enforce #compliance.

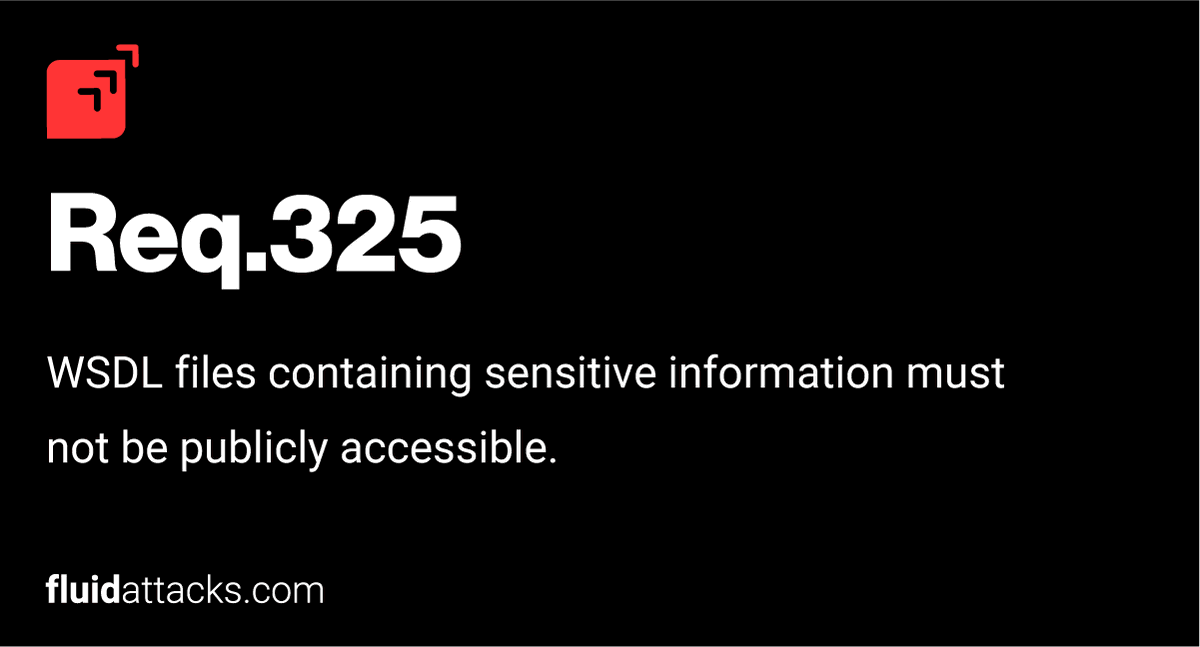
With Fluid Attacks, you can decide what you want us to test. Have a look at our rule of the week 📅 R325. Protect WSDL files. Visit the complete list and details here: bit.ly/3fsjZmo #securityrules #securityrequirements #pentesting #wehackyoursoftware
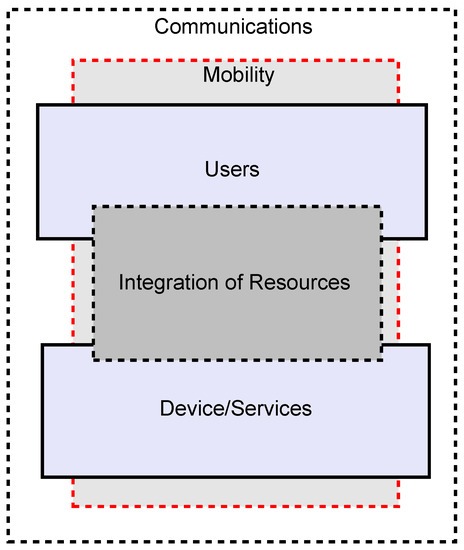
#SecurityRequirements are derived from multiple sources and make up for the security necessities of an #informationsystem, in order to ensure confidentiality, integrity & availability of the information that’s managed, transmitted/stored in the system. buff.ly/2J8FRY0

Have a look at our rule of the week 🔒 R326. Detect rooted devices With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3gZF9Jr #securityrules #securityrequirements #pentesting #wehackyoursoftware

Security requirements aren't optional add-ons—they're functional requirements. The OWASP ASVS provides levels 1-3 for assessing application security. How does your team capture and prioritize security requirements? #OWASPASVS #SecurityRequirements #SDLC
@PMOIndia @rajnathsingh @AmitShah @nsitharaman Thanks for #CCS decisions, pls also: Permanently #SecureBorders Gap up all #SecurityRequirements, internal & external, including #HR, #Logistics, & #Infra Have #UTs in #Northeast + other #StrategicPlaces. Double #SainikSchool + #NCC
With the competitive pressure to innovate, security is often forgotten. Yet we’re starting to see customers prepare for the oncoming wave of new #securityrequirements. Learn more about the Digital Trust Label: kdlski.co/3ZIglPr #IoTSecurity #InternetOfThings #Cybersecurity
FYI - 'For businesses involving sensitive US data, CISA has proposed new security requirements to limit access by adversary states. CISA document: cisa.gov/sites/default/…' - csoonline.com/article/358106… #cybersecurity #CISA #SecurityRequirements
csoonline.com
CISA proposes new security requirements for businesses exposed to cyber espionage
For businesses involving sensitive US data, CISA has defined new security requirements to limit access by adversary states.
organisation Regarding the product-related #securityrequirements of the first list of CRA Annex I, the standard #ETSI303645 has been indicated to us as one of the most relevant.
#Document and maintain #securityrequirements for applications and products. Include security requirements that are required by processes, controls, applicable laws, and regulations.
🛡 Formalizing #securityrequirements ⛓ Generating #tracemonitors 📍 Locating #rootcauses of vulnerabilities 🔐 Identifying #securityflaws in code and designs
Our team offers 4 main Microsoft Security Workshops that provide insight into the #security and protection services needed to best suit your organization's goals and #securityrequirements! Find out which workshop aligns with your needs, and sign up today: bit.ly/3v5CnP6
1️⃣ Rigorous Verification: Ensure a system aligns with specified #securityrequirements. 2️⃣ Programmatic Enforcement: Enforce defined requirements onto a targeted system. github.com/VeriDevOps/RQC…
github.com
GitHub - VeriDevOps/RQCODE: Java implementation of Requirement as Code concept. STIG requiremeents...
Java implementation of Requirement as Code concept. STIG requiremeents testing for Windows 10 platform - VeriDevOps/RQCODE
🚀 Part I is dedicated to #SecurityRequirementsEngineering, a critical aspect that underpins the development of secure and resilient systems. It involves identifying, analyzing, and specifying #securityrequirements to safeguard assets from potential #threats and #vulnerabilities.
Here’s a quick recap of the NIST SP 800-171 Update Project status report that I gave at the 13th Annual Peak Cyber Symposium in Colorado Springs, CO. linkedin.com/posts/ronrosse… #ProtectCUI #NIST800171 #SecurityRequirements #NIST800171A #SecurityAssessments #CMMC #Cybersecurity

Did you join our previous #NIS2 webinar? It received great feedback! ⭐️ The series continues Sept 28 with a deep dive into #securityrequirements under NIS2, including #PKI security controls, #codesigning, and their role in #compliance. 🔐 Register ➡ okt.to/bRmaZP
Did you join @Keyfactor's #NIS2 webinar? It received great feedback!⭐️ The series continues on 28th Sept with a deep dive into #securityrequirements under NIS2, including #PKI security controls, #codesigning, and their role in #compliance.🔐 Register: brighttalk.com/webcast/17778/…
To ensure third-party vendors and partners undergo #penetrationtesting, incorporate contractual clauses mandating regular testing, and set clear #securityrequirements as part of the onboarding process. Regularly assess their security practices and enforce #compliance.

#SecurityRequirements for the #InternetofThings: A Systematic Approach @Macquarie_Uni 👉mdpi.com/1424-8220/20/2… #IoT #accesscontrol

#TestableRequirements #SecurityRequirements #TestableSecurityRequirements #NEIS0736 #SoftwareSecurity

POST Security requirements 🔓 #security #Securityrequirements #securityawareness #cybersecurity #cybersecurityawareness #cybersecuritynews #cyberattack #informationsecurity #infosec #informationsecurityawareness #datasecurity #dataservices #cloudsecurity #securityawareness

Have a look at our rule of the week 🚪 R154. Eliminate backdoors With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3cgvc95 #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 💻 R356. Verify sub-domain names. With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3hMRTDD #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔒 R030. Avoid object reutilization With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3hqZyqW #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 📱 R328. Request MFA for critical systems With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3gsuWVF #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 📱 R362. Assign MFA mechanisms to a single account With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/33CGstL #securityrules #securityrequirements #wehackyoursoftware

Presenting a heuristic approach for #risktreatment based on a distinct terminology for #securityrequirements in: “Heuristic Risk Treatment for ISO/SAE 21434 Development Projects“ by C. Jakobs, M. Werner, K. Schmidt, G.Hansch. ACSIS Vol. 30 p. 653–662; tinyurl.com/2j63anxm

Have a look at our rule of the week 📕 R088. Request client certificates 🔗 Visit the complete list and details here: bit.ly/3jVHMgA With Fluid Attacks, you can decide what you want us to test. #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔑 R128. Define unique data source With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/2EDVe9I #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔏 R039. Define unique data source With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3eqda5d #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔑 R361. Define unique data source With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/34c5obz #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔐 R045. Define unique data source With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3peakW7 #securityrules #securityrequirements #pentesting #wehackyoursoftware

It’s a wrap! The second GA was very intensive, with passionate discussions about #automatedmonitoring #securityrequirements #evidencemanagement #assessment. More info: 💻Medina-project.eu

With Fluid Attacks, you can decide what you want us to test. Have a look at our rule of the week 📅 R325. Protect WSDL files. Visit the complete list and details here: bit.ly/3fsjZmo #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔒 R326. Detect rooted devices With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/3gZF9Jr #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 🔐 R026. Encrypt client-side session information With Fluid Attacks, you can decide what you want us to test. 🔗 Visit the complete list and details here: bit.ly/36z2kbf #securityrules #securityrequirements #wehackyoursoftware

Have a look at our rule of the week 📱 R228. Authenticate using standard protocols With Fluid Attacks, you can decide what you want us to test 🔗 Visit the complete list and details here: bit.ly/3itxVOM #securityrules #securityrequirements #pentesting #wehackyoursoftware

Have a look at our rule of the week 📅 R338. Implement perfect forward secrecy. Visit the complete list and details here 🔗 bit.ly/3ezx0cI With Fluid Attacks, you can decide what you want us to test. #securityrules #securityrequirements #pentesting #wehackyoursoftware

Something went wrong.
Something went wrong.
United States Trends
- 1. #GMMTV2026 527K posts
- 2. MILKLOVE BORN TO SHINE 75.9K posts
- 3. #WWERaw 76.9K posts
- 4. Panthers 37.7K posts
- 5. Finch 14.5K posts
- 6. Purdy 28.4K posts
- 7. AI Alert 8,037 posts
- 8. TOP CALL 9,230 posts
- 9. Moe Odum N/A
- 10. Bryce 21.2K posts
- 11. Timberwolves 3,892 posts
- 12. Keegan Murray 1,533 posts
- 13. Alan Dershowitz 2,711 posts
- 14. Barcelona 135K posts
- 15. Check Analyze 2,404 posts
- 16. Gonzaga 4,116 posts
- 17. Token Signal 8,572 posts
- 18. Dialyn 7,670 posts
- 19. #FTTB 5,951 posts
- 20. Enemy of the State 2,586 posts



















