#securityvulnerabilities search results
#AI systems can be leveraged to insert hard-to-detect #SecurityVulnerabilities into computer chip designs, enabling even those with limited expertise to create sophisticated hardware attacks. @NYUTandon doi.org/g9576h techxplore.com/news/2025-10-a…
Jai shri Ram 🙏 got Bounty $$$ Thanks lord Krishna for this ! #BugBounty #SecurityVulnerabilities #InfoSec #CyberSecurity #EthicalHacking #BugHunting #WhiteHat #server #unblock #WebSecurity #HackerCommunity #CyberAware
#DigitalTransformation Brings #SecurityVulnerabilities, Canon Research Says - MSSP Alert bit.ly/2MxHik8

#Jenkins released a new version that fixes multiple #SecurityVulnerabilities. Update now bitn.am/2JCHo3T

Episode 3 of The @ActiveState Podcast is out! In this episode, Nicole Schwartz and Martin Drohmann dive into the challenges of managing #SecurityVulnerabilities while meeting development deadlines. Watch the full episode: bit.ly/3VVUHVD
The Indian Computer Emergency Response Team (CERT-In) issued a critical advisory on August 2, warning of severe #securityvulnerabilities in various #Apple products. Read more: bit.ly/3yyGmFy

HOW TO TRAIN YOUR #Ghidra 🐉 a complex collection of #sourcecode with many third-party dependencies that are known to contain #securityvulnerabilities.👉 kas.pr/4kvx #cybersecuritytraining #ittraining #infosec #reverseengineering
WordPress vulnerability in three popular file manager plugins installed in up to 1.3 million sites enables arbitrary file deletion. #wordpressplugins #SecurityVulnerabilities searchenginejournal.com/vulnerability-…
#SecurityVulnerabilities – a zero-day exploit had been discovered in #log4j, a popular #Java logging library. All the library’s versions between 2.0 and 2.14.1 included are affected. Find out more on #InfoQ: bit.ly/31Ldtpz @olimpiupop #SoftwareArchitecture #DevOps

🚨 Security Nightmare? AI-powered developer tools built on the #ModelContextProtocol (MCP) are introducing critical #SecurityVulnerabilities like: ➡️ Credential leaks ➡️ Unauthorized file access ➡️ Remote code execution 🔗 bit.ly/40XihDE #AIagents #Security

Understanding the human factor of #digitalsafety techradar.com/pro/understand… @TechRadarPro #securityvulnerabilities

#Log4shell was one of the most critical #SecurityVulnerabilities of the current history. Read the #InfoQ Q&A with Arshan Dabirsiaghi and learn how #ContrastSecurity took an alternative approach to fix the issues: bit.ly/34Xbr6Y @olimpiupop #Java #DependencyManagement

#SecurityVulnerabilities - A new vulnerability in the CRI-O container runtime used by many #Kubernetes installations allows a malicious user to gain root access to the host. The vulnerability was fixed by the CRI-O project: bit.ly/3uI3Bat @talonx #InfoQ #Containers

MS-LLTD, MDNS, and ICMPv6 represent three commonly employed #networkprotocols, carrying potential #securityvulnerabilities that might not have caught your attention. Check out our #PenteraLabs research to learn more about the business risk they pose: okt.to/nm4UED
Some risks -- like #SecurityVulnerabilities and system downtime -- are obvious, others not so much. Good #PatchManagement also requires weighing the possible risks of patching: bit.ly/4ajdA8M

Congrats to @Dooflin5 + Jesse Victors for having their research accepted to @thotcon 2023! Their selection demonstrates the high level of expertise our #SecurityEngineers have and places them among the best for identifying + solving even the most unique #securityvulnerabilities.

Severe weather events cause disruptions that could lead to #SecurityVulnerabilities. @barracuda's @GregArnette shares tips on protecting #data in the age of #ClimateChange, via @ITProToday @karendschwartz: ow.ly/8qtD30oLbYb #Cybersecurity #BCDR

Software companies typically provide #softwareupdates for 3 reasons: to add new features, fix known bugs, and #upgradesecurity. Always update to the latest version of your software to protect yourself from new or existing #securityvulnerabilities. 💻 #cybercrime #datasecurity

#SecurityVulnerabilities: #OpenSSL 3.0.4 introduced a bug that enabled a remote code execution vulnerability on machines computing 2048 bit RSA keys on X86_64 CPUs. A fix is now available in OpenSSL 3.0.5. Read more on #InfoQ: bit.ly/3PzXCNP #CloudSecurity #Encryption

#AI systems can be leveraged to insert hard-to-detect #SecurityVulnerabilities into computer chip designs, enabling even those with limited expertise to create sophisticated hardware attacks. @NYUTandon doi.org/g9576h techxplore.com/news/2025-10-a…
#SecurityVulnerabilities #Reputation #InvestorProtection #Compliance #Functionality #CodeQuality as your presale is life get an audit and protect your investors
#SecurityResearchers have found that in roughly 80% of cases, spikes in malicious activity are a precursor to the disclosure of new #SecurityVulnerabilities (CVEs) within six weeks. #Cybersecurity ow.ly/sXYM50WCVr1
WordPress vulnerability in three popular file manager plugins installed in up to 1.3 million sites enables arbitrary file deletion. #wordpressplugins #SecurityVulnerabilities searchenginejournal.com/vulnerability-…
🚨 Security Nightmare? AI-powered developer tools built on the #ModelContextProtocol (MCP) are introducing critical #SecurityVulnerabilities like: ➡️ Credential leaks ➡️ Unauthorized file access ➡️ Remote code execution 🔗 bit.ly/40XihDE #AIagents #Security

Insufficient logging and monitoring can slow down breach detection and worsen the impact of #SecurityVulnerabilities! ⚠️ Make sure you follow security logging standards, like #OWASP Logging Cheat Sheet guidelines, and enforce separate, restricted access controls. You can use…
Untrusted and risky automation solutions, like Telegram bots, expose users to hacks, phishing, and systemic risks. @MagicNewton offers a secure alternative. #SecurityVulnerabilities #RiskyAutomation
Untrusted and risky automation, often via Telegram bots, exposes users to hacks, phishing, and systemic risks. @MagicNewton #PrivateKeyRisk #SecurityVulnerabilities
Misconfigured AD CS certificate templates with ESC9 enable privilege escalation—attackers can impersonate Domain Admins by exploiting weak certificate mappings and security extensions. Stay vigilant! 🛡️ #ActiveDirectory #SecurityVulnerabilities ift.tt/PmOYbLV
🛡️ $302M crypto losses in May expose critical #SecurityVulnerabilities. @CertiK reveals code exploits driving massive industry risk. Will stricter #SmartContract audits restore investor confidence? Urgent protocol review needed.
Google Releases June Security Bulletin for Android Devices to Fix Vulnerabilities | Linn Freedman, Data Privacy + Cybersecurity Insider dataprivacyandsecurityinsider.com/2025/06/google… #Google #Android #securityvulnerabilities
dataprivacyandsecurityinsider.com
Google Releases June Security Bulletin for Android Devices to Fix Vulnerabilities
Google recently issued its June Android Security Bulletin that is designed to patch 34 vulnerabilities, all of which Google designates as high-severity
Malicious Unicode? 🛑 It can happen to the best of us. A recent post by @badger highlights how these characters can sneak past code reviews! daniel.haxx.se/blog/2025/05/1… Qodana’s NonAsciiCharacters inspection flags this to help you catch hidden #securityvulnerabilities
daniel.haxx.se
Detecting malicious Unicode
In a recent educational trick, curl contributor James Fuller submitted a pull-request to the project in which he suggested a larger cleanup of a set of scripts. In a later presentation, he could show...
Bug bounty hunters have earned $2M+ on FOGO, identifying 500+ critical vulnerabilities since 2023. #BugBountyPayouts #SecurityVulnerabilities
JUST IN: Critical security vulnerabilities found in the Model Context Protocol (MCP). Threats include Tool Poisoning, Rug-Pull Updates, Retrieval-Agent Deception, Server Spoofing, and Cross-Server Shadowing. User safety and data integrity at risk. #MCP #SecurityVulnerabilities
Get some intel into managing rising security vulnerabilities and combating the overwhelm that can come from all those CVEs. Download our practical guide for security leaders ➡️ directdefense.com/gain-clarity/?… #securityvulnerabilities #cybersecurity #cyberresilience #MITRE

Overwhelmed by long lists of CVEs? Vulnerability data can seem never ending, but our practical guide to managing rising vulnerabilities can help you build and maintain cyber resilience. ➡️ directdefense.com/gain-clarity/?… #securityvulnerabilities #cybersecurity #cyberresilience #MITRE

#Jenkins released a new version that fixes multiple #SecurityVulnerabilities. Update now bitn.am/2JCHo3T

Jai shri Ram 🙏 got Bounty $$$ Thanks lord Krishna for this ! #BugBounty #SecurityVulnerabilities #InfoSec #CyberSecurity #EthicalHacking #BugHunting #WhiteHat #server #unblock #WebSecurity #HackerCommunity #CyberAware

#DigitalTransformation Brings #SecurityVulnerabilities, Canon Research Says - MSSP Alert bit.ly/2MxHik8

#SmartHomes #SecurityNews #SecurityVulnerabilities #CyberAttack #CyberSecurityUpdates #CyberSecurityEvent #CyberSecurityReport #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace

Know how #MachineLearning is being used to handle #securityvulnerabilities by @farwa_sajjad96 via @datamadesimple bigdata-madesimple.com/machine-learni… #artificialintelligence #AI #ML #Cybersecurity #Security #technology #mistralsolutions

🌟 Meet Sahil Bugade, a passionate cybersecurity enthusiast from MIT ADT University! 🚀 Recently, he made history by entering NASA's Hall of Fame for uncovering a security vulnerability in their digital assets. 🛡️ #CybersecurityHero #NASA #SecurityVulnerabilities #MITADT

Severe weather events cause disruptions that could lead to #SecurityVulnerabilities. @barracuda's @GregArnette shares tips on protecting #data in the age of #ClimateChange, via @ITProToday @karendschwartz: ow.ly/8qtD30oLbYb #Cybersecurity #BCDR

33 vulnerabilities found in embedded open source networking stacks @Forescout #Amnesia33 #SecurityVulnerabilities #IoT #TCPIP #Authentication #EmbeddedSoftware tinyurl.com/y3pncwg9

Common Python Security Problems - websystemer.no/common-python-… #programming #python #securityvulnerabilities

Systemic Racism Is a Cybersecurity Threat on.cfr.org/3fzsdZw #CyberSecurity #SecurityVulnerabilities #AppsUnify

How to correct #SecurityVulnerabilities in #WebApplications? @RStyleLab shares some useful tips for businesses buff.ly/2HEELlc #WebDevelopment #WebApps #WebAppSecurity #CyberSecurity #CrossSiteScripting #SQLinjection #OpenSource via @clutch_co
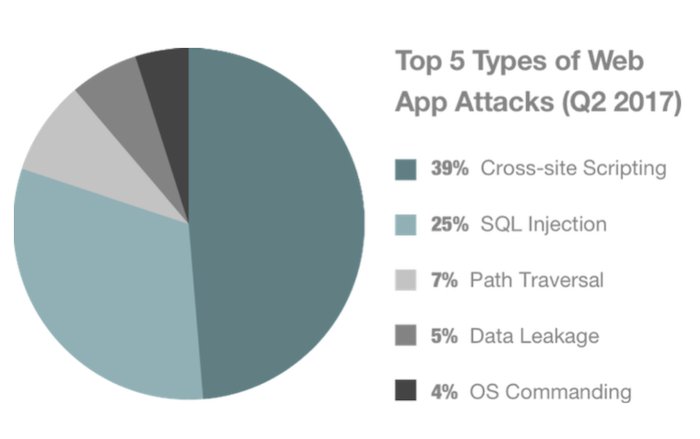
Is your company ready to face #cyberattacks? Komodo Consulting helps you identify #securityvulnerabilities in your application before hackers do. bit.ly/3tJCixt #datasecurity #cyberattacks #quotes

>>> #CodefreshLive STARTS NOW! Learn how to scan your #Docker images for #securityvulnerabilities using #Clair. LOG IN HERE: buff.ly/2FwWniZ

If you are using this plugin, we strongly recommend that you update to the latest version immediately to protect your site. Stay safe and secure online! #WordPress #OnlineCourses #SecurityVulnerabilities #ProtectYourSite

#SecurityVulnerabilities – a zero-day exploit had been discovered in #log4j, a popular #Java logging library. All the library’s versions between 2.0 and 2.14.1 included are affected. Find out more on #InfoQ: bit.ly/31Ldtpz @olimpiupop #SoftwareArchitecture #DevOps

Understanding the human factor of #digitalsafety techradar.com/pro/understand… @TechRadarPro #securityvulnerabilities

#Log4shell was one of the most critical #SecurityVulnerabilities of the current history. Read the #InfoQ Q&A with Arshan Dabirsiaghi and learn how #ContrastSecurity took an alternative approach to fix the issues: bit.ly/34Xbr6Y @olimpiupop #Java #DependencyManagement

Something went wrong.
Something went wrong.
United States Trends
- 1. Columbus 160K posts
- 2. President Trump 1.09M posts
- 3. Middle East 260K posts
- 4. Brian Callahan 9,726 posts
- 5. #IndigenousPeoplesDay 11.6K posts
- 6. Titans 40.1K posts
- 7. Thanksgiving 54.5K posts
- 8. Vrabel 7,019 posts
- 9. Cape Verde 12.6K posts
- 10. Macron 212K posts
- 11. Seth 49.1K posts
- 12. Marc 49.3K posts
- 13. Apple TV 5,560 posts
- 14. HAZBINTOOZ 5,290 posts
- 15. #WWERaw 55.4K posts
- 16. Shildt 2,859 posts
- 17. Sarah Strong 2,051 posts
- 18. Egypt 268K posts
- 19. Darius Smith 3,916 posts
- 20. #Isles 1,349 posts