#webshell wyniki wyszukiwania
Did you know that it is possible to elevate privileges with SeImpersonate in an ADCS environment? It is an alternative to *Potato that you can use in your Red Team operations. And you can do it all with Kraken! #redteam #webshell You can read about this technique explained in…

DarkCool All Tools For Hacking Activity! List:~ Exploiter, Checker, #Webshell Finder, Grabber, Searching, #Bruteforce, Random, And Others Tools github.com/DarkSkull777/D… #cybersecurity #pentesting #redteam

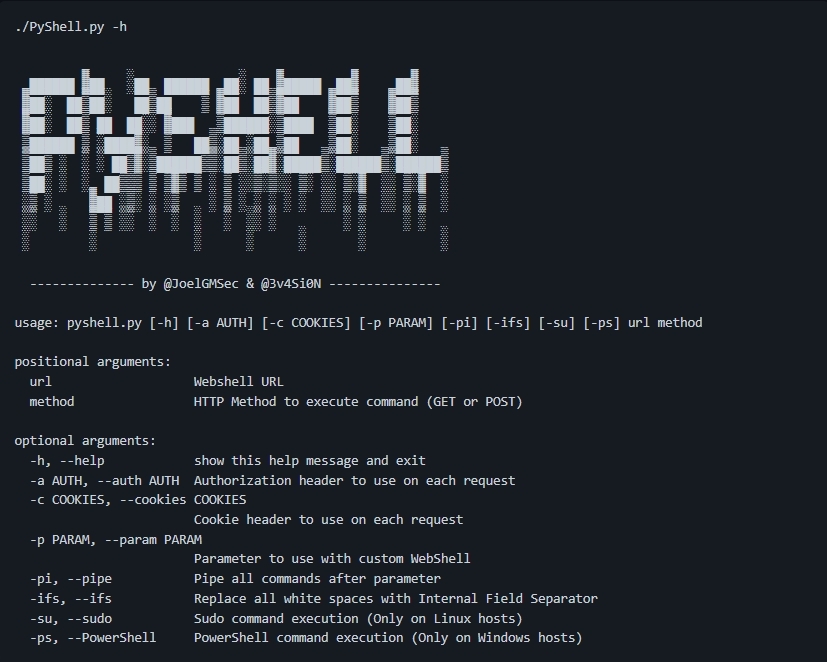
PyShell PyShell is Multiplatform #Python #WebShell. This tool helps you to obtain a shell-like interface on a web server to be remotely accessed. Unlike other webshells, the main goal of the tool is to use as little code as possible on the server side… t.me/hackgit/7870
Webshell on an IIS? SeImpersonate Privilege? But... you don't want to execute anything on disk to avoid detection. Using Kraken, you may elevate and preserve privileges by combining the execute_assembly module, impersonation, and tokens. It's that simple! #redteam #webshell
Did you know that you can Pass The Hash using SharpNamedPipePTH from @ShitSecure and get to impersonate the target through the leak of their access token? Yes, it is possible with Kraken! #redteam #webshell


The Kraken Wiki has been released! There are still many things to add, but you can create your own modules and make the project grow! #redteam #webshell ➡️ github.com/kraken-ng/Krak…

No, your eyes don't lie, Kraken now supports NET Framework 2.0! I'm sure it will be a great help in those outdated environments we audit. #redteam #webshell ➡️github.com/kraken-ng/Krak…

WebShell免杀真的不是很难,欢迎参阅我的开源项目:github.com/AabyssZG/WebSh… 以下是成功ByPass阿里的伏魔引擎的证明,也有许许多多的小伙伴在学习后收获颇多🥳 相信你能成为下一位成功的挑战者🫡 #bypass #aliyun #webshell #bypassAV #BlueTeam #redteam #Hacking



一场跨越十年的超时空思维碰撞:在腾讯安全应急响应中心找到了一个远古工具ScanWebshell 文章地址:blog.zgsec.cn/archives/535.h… 谁能想到,在十年后,在互联网的犄角旮旯里面,我还能重拾前人的经验、回忆和热枕,带着他们继续向前 #webshell #cybersecuritytips #Tencent #ByPass


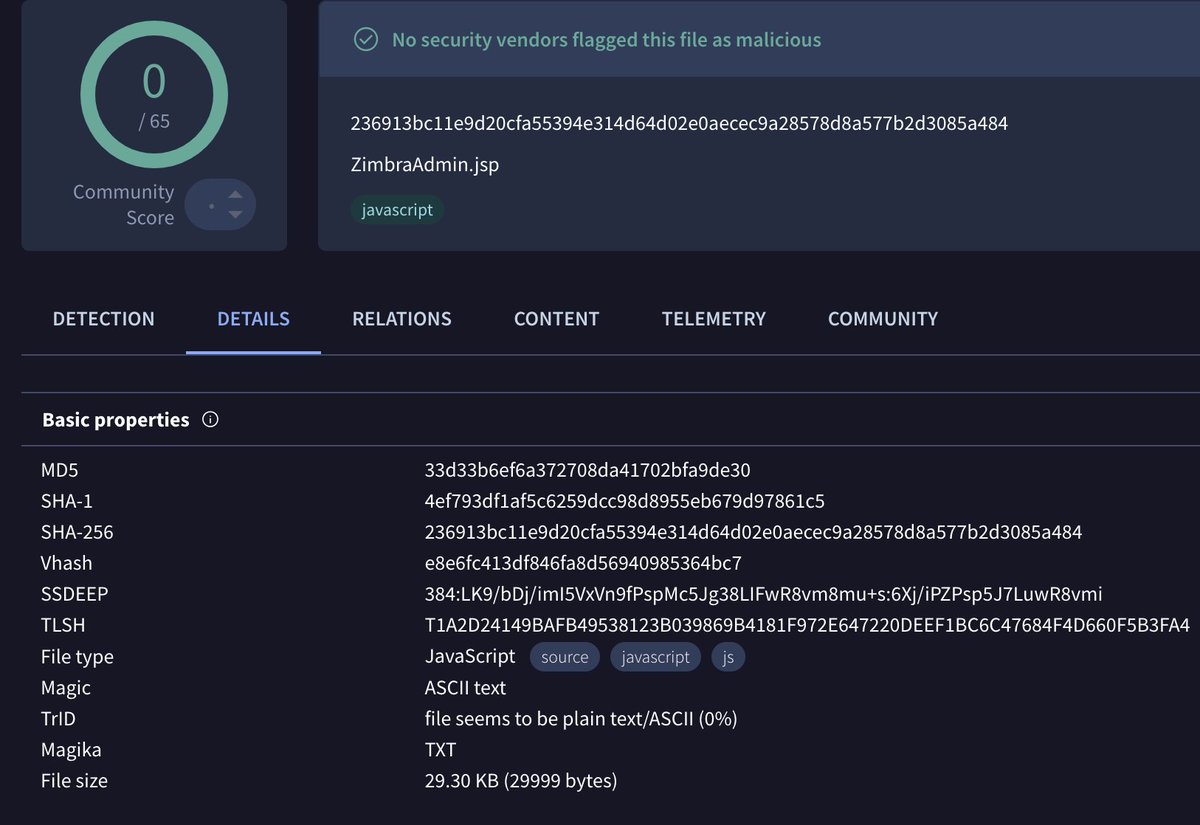
Interesting #Webshell masquerading a #Zimbra licit file found with 0 detection ratio. ☣️ZimbraAdmin.jsp➡️33d33b6ef6a372708da41702bfa9de30 2⃣Base64 replace characters 📸⤵️ 3⃣4⃣Webshell actions can be performed📸⤵️



Active exploitation of a command injection flaw in Array Networks AG Series gateways has been confirmed in Japan since August 2025. Unpatched devices risk web shell implants via DesktopDirect. #Japan #ArrayNetworks #WebShell ift.tt/8pxoeW4
#webshell #opendir #netsupport #rat at: https://appointedtimeagriculture\.com/wp-includes/blocks/post-content/ GatewayAddress=95.179.158.213:443 RADIUSSecret=dgAAAPpMkI7ke494fKEQRUoablcA

⚠️Atención: @uc_chile @IngenieriaUC A través de canales de Telegram, un actor de amenaza asegura poseer accesos tipo #webshell y está ofreciéndolos en venta desde el 01 de Mayo. El sitio presuntamente afectado es microct[.]ing[.]uc[.]cl.
![V3n0mStrike's tweet image. ⚠️Atención: @uc_chile @IngenieriaUC
A través de canales de Telegram, un actor de amenaza asegura poseer accesos tipo #webshell y está ofreciéndolos en venta desde el 01 de Mayo.
El sitio presuntamente afectado es microct[.]ing[.]uc[.]cl.](https://pbs.twimg.com/media/GNP_gucXcAAgO9o.png)
🚨Alerta México 🇲🇽 El sitio web dif[.]gomezpalacio[.]gob[.]mx, perteneciente al Ayuntamiento de Gómez Palacio Durango @AyuntamientoGP, presenta múltiples archivos #webshell activos. Estos archivos permiten a un atacante ejecutar comandos, manipular archivos, controlar la base de…
![V3n0mStrike's tweet image. 🚨Alerta México 🇲🇽
El sitio web dif[.]gomezpalacio[.]gob[.]mx, perteneciente al Ayuntamiento de Gómez Palacio Durango @AyuntamientoGP, presenta múltiples archivos #webshell activos.
Estos archivos permiten a un atacante ejecutar comandos, manipular archivos, controlar la base de…](https://pbs.twimg.com/media/GM3asOHW4AAS1pe.jpg)
👉🇲🇽#México: HerbDark supuestamente afirma haber desfigurado un subdominio del Ayuntamiento Gómez Palacio. @AyuntamientoGP 👉dif[.]gomezpalacio[.]gob[.]mx
![chum1ng0's tweet image. 👉🇲🇽#México: HerbDark supuestamente afirma haber desfigurado un subdominio del Ayuntamiento Gómez Palacio. @AyuntamientoGP
👉dif[.]gomezpalacio[.]gob[.]mx](https://pbs.twimg.com/media/GHiD7A7WkAA5rNc.jpg)
最近发现了这个老外写的免杀Webshell大马,可以过阿里云的查杀,就研究了一下,并将内容开源出来🧐 开源地址:github.com/AabyssZG/Gel4y… 里面讲解了这个WebShell大马的核心运作原理,觉得不错可以给我点个Star😆 #webshell #hacker #bypass #CyberSecurity


Gel4y Mini Shell Backdoor: webshell that can bypass some system security securityonline.info/mini-shell-bac…
🔓🛜 Hackers exploit ArrayOS AG VPN flaw to plant webshells Attackers are abusing a command injection bug to create rogue accounts and maintain access. #vpn #vulnerability #webshell #infosec

Active exploitation of a command injection flaw in Array Networks AG Series gateways has been confirmed in Japan since August 2025. Unpatched devices risk web shell implants via DesktopDirect. #Japan #ArrayNetworks #WebShell ift.tt/8pxoeW4
One Hat Cyber Team, an Indonesian #Hacktivist group, is using this PHP #webshell in the wild. File name: paku.php SHA1: F1C57D4DFA69EAB40227CC72EC043379AA19F9C3 SHA256: AFEBE260907B09BB39DD1764FF2C0BE5DCDF46A175011145DD6E9947A1C9BBE8 1/61 detection on VT -…

#BadCandy #Webshell #threatens #unpatched #Cisco #IOS_XE devices, warns #Australian #government ift.tt/q1hYAom

#BadCandy #Webshell threatens unpatched #Cisco IOS XE devices, warns Australian government securityaffairs.com/184095/hacking… #securityaffairs #hacking
Russian-linked hackers used stealthy living-off-the-land tactics and web shells like Localolive to target Ukrainian organizations, exploiting vulnerabilities while stealing sensitive data via PowerShell and scheduled tasks. #Ukraine #WebShell ift.tt/6t1zOHb
SessionReaper vulnerability (CVE-2025-54236) in Magento enables remote code execution via nested deserialization. Only 38% of stores patched after 6 weeks, exposing many to web shell attacks. #MagentoRisk #WebShell #USA ift.tt/sZ1783j
🚨 Chinese state hackers abused an ArcGIS geo-mapping tool for year-long, undetected persistence! They turned a component into a web shell. Stealthy! 🕵️♂️ bleepingcomputer.com/news/security/… #CyberSecurity #ChineseHackers #WebShell
🚨 Malware Alert! We've detected a new PHP backdoor / RCE dropper (webshell installer) on malwaredecoder.com Found suspicious files on your website? Scan them here immediately to protect your site! #MalwareAlert #PHPBackdoor #Webshell #RCE #WebsiteSecurity #WordPress

Huntress details log poisoning used to plant a China Chopper-style web shell on a web server, enabling actors to use AntSword and then deploy Nezha, an operations and monitoring tool, which was used to install Ghost RAT. huntress.com/blog/nezha-chi…

🚨 Webshell Sale | pms[.]portal[.]gov[.]bd #Bangladesh Alleged #Webshell access to government portal pms[.]portal[.]gov[.]bd — being sold for $300. Defanged: hxxps://pms[.]portal[.]gov[.]bd Do NOT access, buy, or use. #CyberSecurity
![cyberfeeddigest's tweet image. 🚨 Webshell Sale | pms[.]portal[.]gov[.]bd #Bangladesh
Alleged #Webshell access to government portal pms[.]portal[.]gov[.]bd — being sold for $300. Defanged: hxxps://pms[.]portal[.]gov[.]bd
Do NOT access, buy, or use. #CyberSecurity](https://pbs.twimg.com/media/G2hLB6EXEAACdqQ.jpg)
Cisco Talos researcher Joey Chen discloses details of UAT-8099, a Chinese-speaking cybercrime group mainly involved in search engine optimization (SEO) fraud and theft of high-value credentials, configuration files, and certificate data. blog.talosintelligence.com/uat-8099-chine…

🚨 Telegram channel peddling #Shell/#Webshell access allegedly targets #Austria 🇦🇹 For sale: 🔗 immo.now-ever[.]at 🔗 siebdruck-reinhard[.]at 🔗 ra-steflitsch[.]at Serious risk of exploitation & unauthorized access. #CyberSecurity #AustrianWebsites
![cyberfeeddigest's tweet image. 🚨 Telegram channel peddling #Shell/#Webshell access allegedly targets #Austria 🇦🇹
For sale:
🔗 immo.now-ever[.]at
🔗 siebdruck-reinhard[.]at
🔗 ra-steflitsch[.]at
Serious risk of exploitation & unauthorized access. #CyberSecurity #AustrianWebsites](https://pbs.twimg.com/media/G1c1fCUWkAAyKzI.jpg)
Selling accesses/webshells, interested parties contact me in dm (I only accept monero and pix) #webshell
💻 #Webshell Access for Sale – Mexico Educational Website 💻 A threat actor allegedly selling #Webshell access to an educational site of #Mexico. POC: hxxps://www.iee.edu.mx/wp-content/uploads/Unlimited[.]txt #Cybercrime #Infosec #Breach
![cyberfeeddigest's tweet image. 💻 #Webshell Access for Sale – Mexico Educational Website 💻
A threat actor allegedly selling #Webshell access to an educational site of #Mexico.
POC: hxxps://www.iee.edu.mx/wp-content/uploads/Unlimited[.]txt
#Cybercrime #Infosec #Breach](https://pbs.twimg.com/media/G0JQafsW0AAh06T.jpg)
🚨 #Webshell Access Exposed: #Australia Educational Website Targeted A threat actor allegedly gained #Webshell access to an #Australian educational website. POC has been shared. 🔗 hxxps://activity4you[.]au[.]edu/ #CyberSecurity #Australia #Infosec #CyberThreats
![cyberfeeddigest's tweet image. 🚨 #Webshell Access Exposed: #Australia Educational Website Targeted
A threat actor allegedly gained #Webshell access to an #Australian educational website. POC has been shared.
🔗 hxxps://activity4you[.]au[.]edu/
#CyberSecurity #Australia #Infosec #CyberThreats](https://pbs.twimg.com/media/G0EF_rmWkAAiDmU.jpg)
Something went wrong.
Something went wrong.
United States Trends
- 1. Tulane 13.9K posts
- 2. Gunther 24.3K posts
- 3. Cocona 93.8K posts
- 4. #SmackDown 36K posts
- 5. #AAA2025 44.5K posts
- 6. fnaf 2 64.7K posts
- 7. North Texas 7,520 posts
- 8. #MCWonyoungAAAte 10.9K posts
- 9. #GCWSay N/A
- 10. 5 YEARS WITH MC WONYOUNG 10.6K posts
- 11. Anthony Davis 2,307 posts
- 12. Boise State 3,820 posts
- 13. LA Knight 11.1K posts
- 14. Trouba 1,236 posts
- 15. #ROHFinalBattle 18.7K posts
- 16. UNLV 4,435 posts
- 17. Meek 8,845 posts
- 18. Flag Day 3,178 posts
- 19. Dizzy 6,583 posts
- 20. Athena 10.9K posts




![jstrosch's tweet image. #webshell
hxxp://54.224.107[.]126:8080/wp-content/uploads/2023/03/](https://pbs.twimg.com/media/FtXaJL3XoAEPNJh.jpg)



























