#cryptography نتائج البحث
🎤PQ-REACT conversations with our experts: Your decryption key to the future of #cryptography! In our first episode, we welcome our project's coordinator, Akis Kourtis, from the NCSR "DEMOKRITOS". Listen online: 🎧 podbean.com/ew/pb-i7rqd-19… ▶️ youtu.be/LcWRdPNg2_M?si… #PQREACT
For a #Blockchain to be truly post-quantum secure, it must be PQ-secure since genesis. Why? Because quantum computers can break the #cryptography of earlier, quantum-vulnerable blocks, potentially reverse-engineering them or forging them. This compromises the entire chain’s…
#Privacy as a Human Right: Why #Cryptography Is Essential for Freedom 🦾🌐⚔️ herbertrsim.com/privacy-human-… @XcomERC20 — ⚔.ws ☓.com

Why worst case hardness alone is not necessarily useful in #cryptography? 🤔 @talayhan_a explains the crucial difference between worst-case and average-case hardness, and why the latter is more valuable for building cryptographic primitives. Watch his full talk. 👇🏻
📚 Teoria dei codici, cos’è? Scopri la parola della settimana dal nostro vocabolario #TelsyABC. #Cybersecurity #Cryptography #CybersecurityAwareness
Delivered a talk on “Quantum Communication & Cryptographic Protocols” at IEEE CBIT Signal Processing Society. Great discussions on quantum communication, secure protocols & future of communication security. #QuantumComputing #Cryptography #IEEE #Quinfosys

New paper that can potentially impact ML-DSA (Dilithium) arxiv.org/abs/2510.07515 #QuantumCoin is safe, uses hybrid signature schemes, with SPHINCS+ (SLH-DSA) as a breakglass. Hybrid is the way to go, QuantumCoin the pioneer in blockchains for hybrid pqc. #cryptography $q
$XPR TIME 💪😎💪 “It's called "#Crypto" because the term is short for #Cryptography, the #Science of #Secure #Communication.” #BLOCKCHAIN like you MEAN IT with $XPR

🔒Are you curious about the future of cryptography and blockchain? XRPL Commons is proud to host the second edition of its 📚 Academic Insights series, bringing together leading cryptographers to explore the evolving relationship between #cryptography and #blockchain. 👉…

Where math meets magic. ✨ Complex computations become elegant, verifiable proofs. Fermah turns the heavy lifting of cryptography into a seamless dance of algorithms beautiful, efficient, and trustworthy. Proof generation reimagined. @fermah_xyz #Cryptography #ZKProofs #Fermah
2/ Blockchain security is built on two core cryptographic pillars: SHA-256 ensures data integrity and mining protection (as in Bitcoin), while ECDSA verifies wallet transactions across most networks. ⚡ #blockchain #cryptography

🚨This is for Nerds … 🤓 How Bitcoin Works Under the Hood ! 🤓 #Cryptography #MyFirstBitcoin series youtu.be/Lx9zgZCMqXE

Feeling like a CaveMan trying to learn how #Bitcoin Lightning ⚡️ Network Works .. ₿ ₿ ₿.. Alice 🙋🏽♀️ —> ₿ob 🤦🏾♂️ | —> Carol 🤦🏻♀️—> Dave 🤷🏻♂️ Glad it Works ! Yet to learn Hooow #MyFirstBitcoin Series youtu.be/yKdK-7AtAMQ
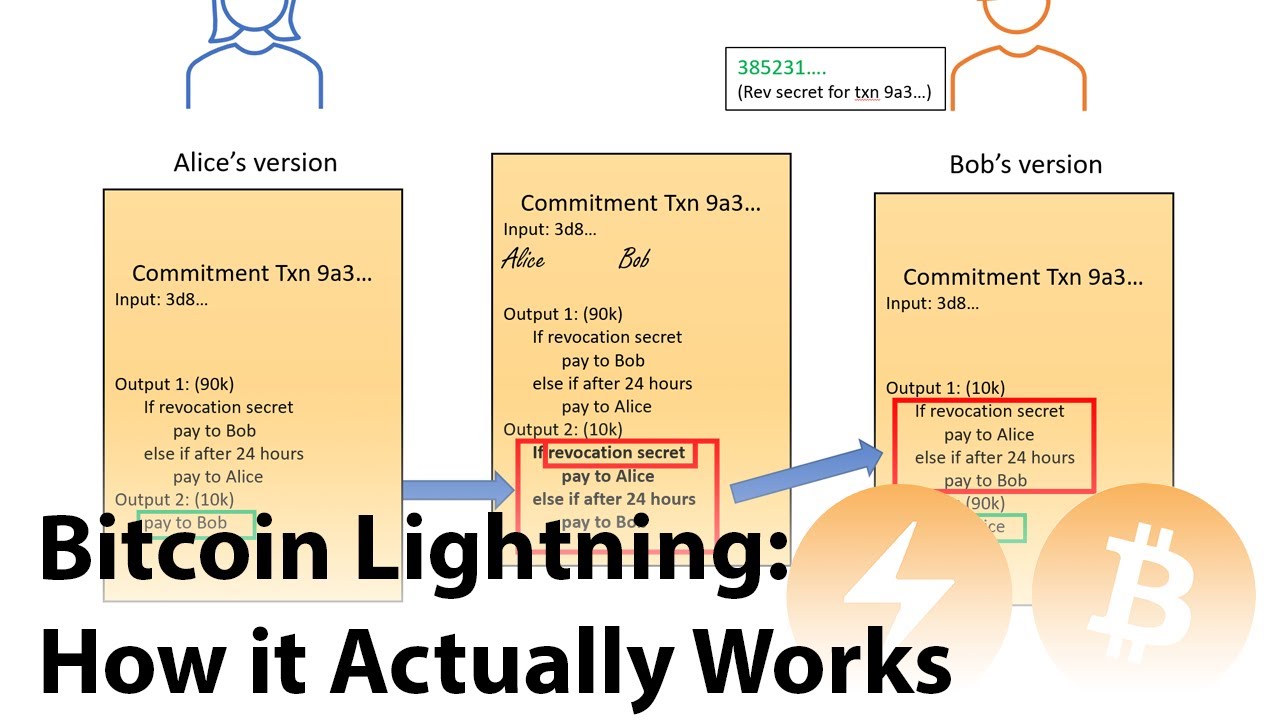
youtube.com
YouTube
Bitcoin Lightning Network Explained: How it Actually Works
Verisign’s Bill Carroll, Joseph Harvey, Matt Thomas, and Duane Wessels will all be presenting at #OARC45 this October. 🎤 Catch our sessions on post-quantum #cryptography #DNSSEC, Verisign’s Transitive Trust tool and #DNS resolution dependencies, and a break in the cold case of…

Enter @zama_fhe, pioneering Fully Homomorphic Encryption (FHE)! This groundbreaking tech allows computations on encrypted data, ensuring ultimate privacy and security. #FHE #Privacy #cryptography

Introducing @zama_fhean open source cryptography company building cutting-edge Fully Homomorphic Encryption (FHE) solutions for blockchain & AI. #Zama, #FHE, #Cryptography, #Privacy, #Blockchain

Ciao da Roma! 🇮🇹 The IXH 25 Hackathon has kicked off and the room is buzzing. Students from top Italian universities and across Europe are coming together to advance #cryptography and #Blockchain . Several of the XRPL Commons 🌊Aquarium residents are also attending and bringing…




إحتراف التشفير لازم يكون عن طريق كتابة كود تشفير لازم تتعلم برمجة تطبيقات التشفير .غير كده هيبقى نظري فقط #cryptography #Crypto #Cipher #CyberSecurity

The internet needs better ways to confirm what’s real. Not louder opinions — stronger proofs. This demo is one small example of where authenticity meets #cryptography, and where beauty meets verification. #ImageVerification #TrustAndSafety #Ecommerce #AI
Notable post-quantum #cryptography initiatives paving the way toward #QDay buff.ly/iYK0CW2 @CSOonline @JLeyden @MJHillEditor #tech #data #datasecurity #cybersecurity #cybercrime #encryption #PQC #leadership #CTO #CDO #CISO #CEO #business #quantumcomputing #research
How can we secure digital signatures in the quantum age? Learn about a new collaborative scheme in JEIS: journals.bilpubgroup.com/index.php/jeis… #JEIS #QuantumSecurity #Cryptography #Infosec

The link to the full blog post is: alecmuffett.com/article/126061 #cryptography #iacr
alecmuffett.com
“Key Management” is the cryptographic community’s version of “…it’s always DNS”
International Association for Cryptologic Research runs secure vote and then loses the keys so nobody knows what the result is. As one commenter put it: “So a single member can collude to res…
🎤PQ-REACT conversations with our experts: Your decryption key to the future of #cryptography! In our first episode, we welcome our project's coordinator, Akis Kourtis, from the NCSR "DEMOKRITOS". Listen online: 🎧 podbean.com/ew/pb-i7rqd-19… ▶️ youtu.be/LcWRdPNg2_M?si… #PQREACT

📚 Teoria dei codici, cos’è? Scopri la parola della settimana dal nostro vocabolario #TelsyABC. #Cybersecurity #Cryptography #CybersecurityAwareness
Hey @X algorithm, help me find my tribe. Web3 & Cryptography AI & Machine Learning Data Science Security & Privacy Mathematics, Proofs, Protocols Building cool things on-chain let’s connect. #buildinpublic #web3community #cryptography #AI #DataScience #TechTwitter
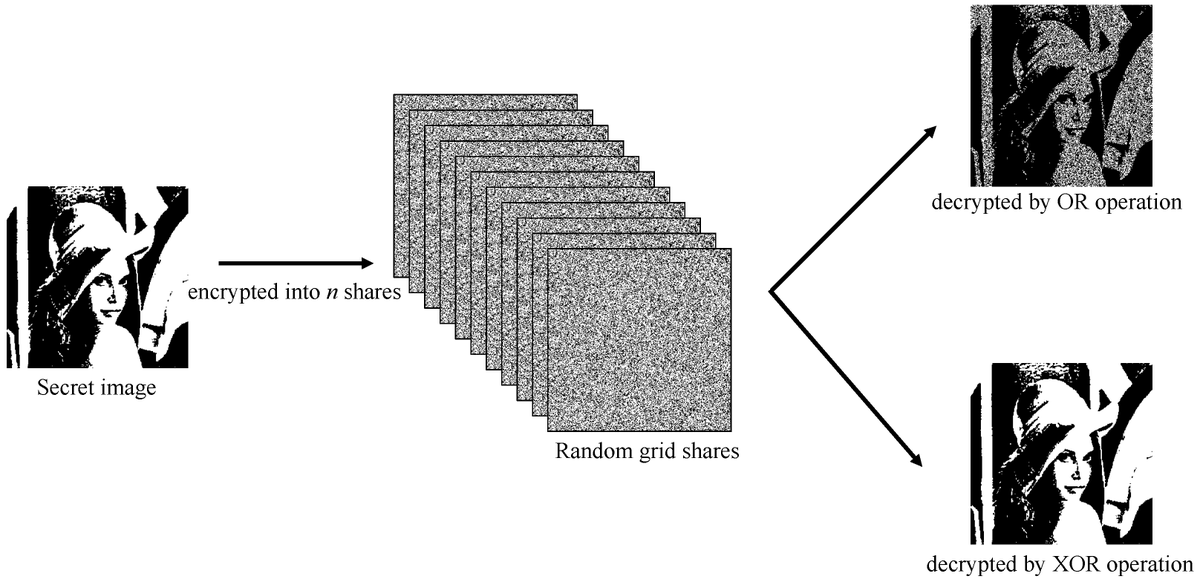
RG-Based Region Incrementing Visual #Cryptography with Abilities of OR and XOR #Decryption ✏️ Yu-Ru Lin and Justie Su-Tzu Juan 🔗 brnw.ch/21wXGMD Viewed: 1649; Cited: 3 #mdpisymmetry
📄 Plaintext — Data before encryption! Original readable information before cryptographic transformation. The starting point of the privacy journey. What you protect with crypto magic! 🔓✨ 🔗 chainterms.com/glossary/plain… #Plaintext #Cryptography #RawData #EncryptionBasics
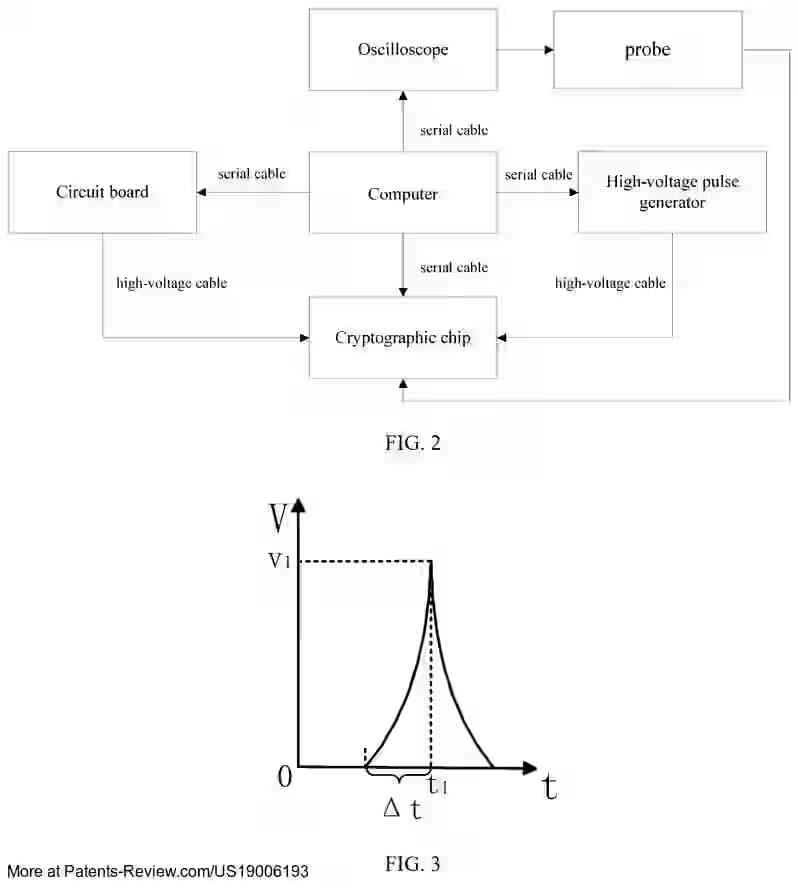
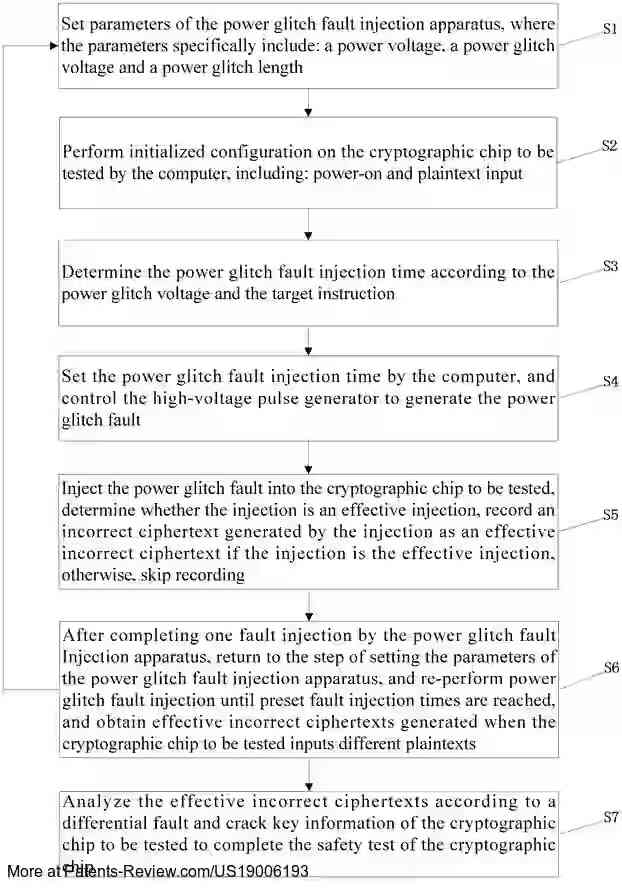
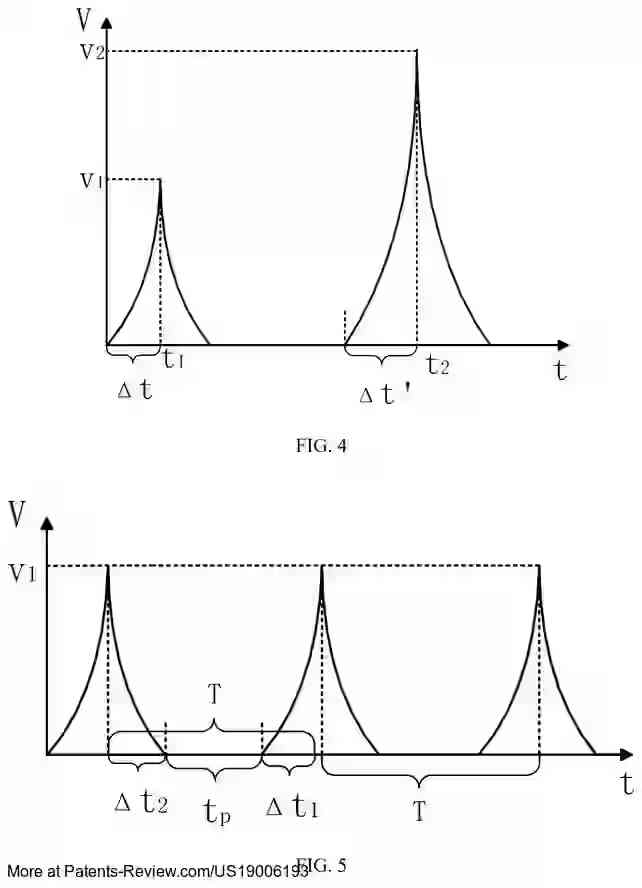
🔍 New patent grant: #US19006193B1 by #ChinaAutomotiveTech Discloses a method & apparatus for high-temporal-accuracy power glitch fault injection in cryptographic chips. By adjusting the rise time, it enhances control over injection timing, boosting success rates. #Cryptography…
Our Head of Research Thomas Prest will be speaking on - ""Post-Quantum Cryptography in Europe" on the 8th December at AusQRC. For more information, visit the website. hubs.li/Q03VbT6b0 #Cybersecurity #postquantum #cryptography

The internet needs better ways to confirm what’s real. Not louder opinions — stronger proofs. This demo is one small example of where authenticity meets #cryptography, and where beauty meets verification. #ImageVerification #TrustAndSafety #Ecommerce #AI
#Privacy as a Human Right: Why #Cryptography Is Essential for Freedom 🦾🌐⚔️ herbertrsim.com/privacy-human-… @XcomERC20 — ⚔.ws ☓.com

“Migrating #Telecom to #Quantum-Resistant #Cryptography on a Global Scale” - John Preuß Mattsson @john_preu25849 w/@ericsson Learn more: datatracker.ietf.org/meeting/123/ma… #IETF123 #IETF #PostQuantum #QKD #Cybersecurity #Ericsson #QRNG #TRNG #5G #6G #3GPP #OpenSSL
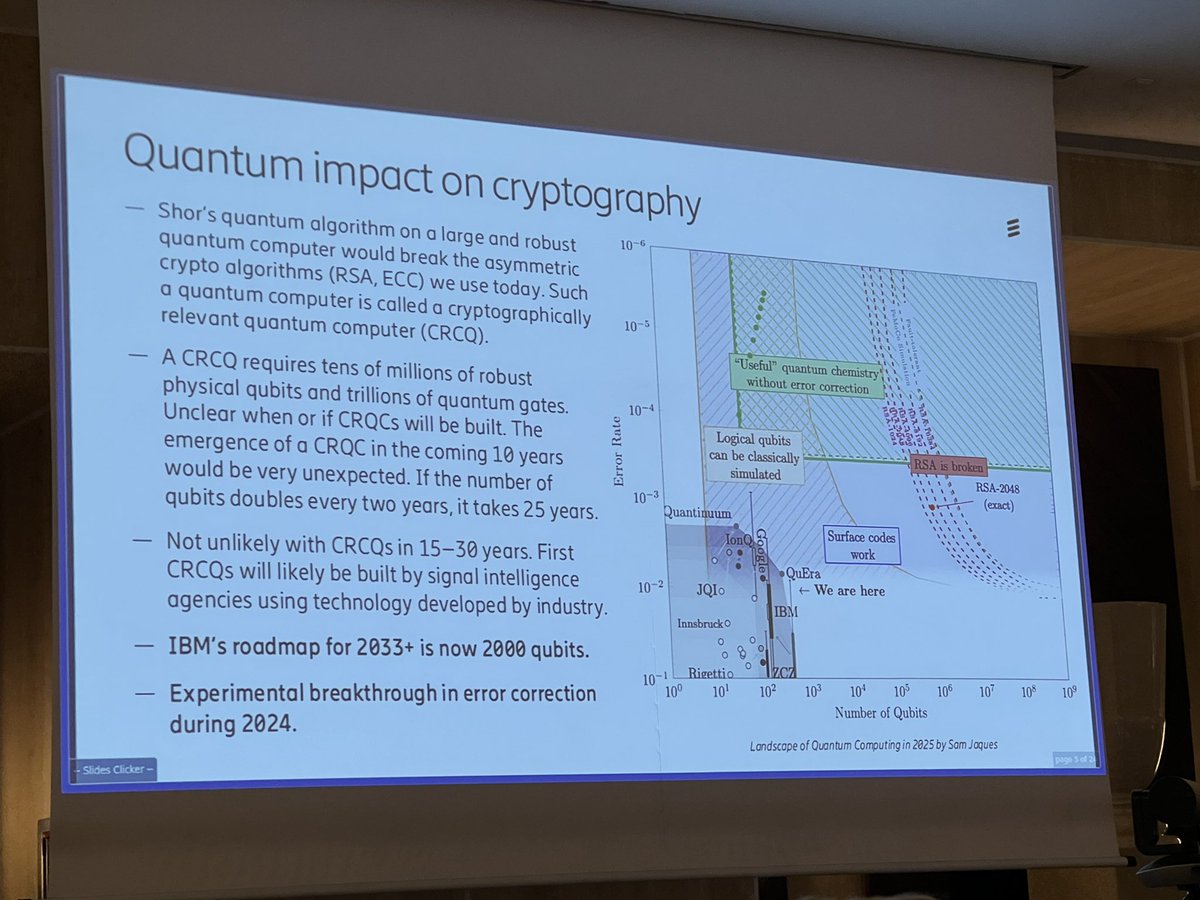


Quantum-Safe #Cryptography in Embedded Systems - buff.ly/DotL9J0 #quantumcomputing #encryption #OT #Security #cybersecurity #infosec #ICS #IoT #IIoT #OTsecurity

$XPR TIME 💪😎💪 “It's called "#Crypto" because the term is short for #Cryptography, the #Science of #Secure #Communication.” #BLOCKCHAIN like you MEAN IT with $XPR

إحتراف التشفير لازم يكون عن طريق كتابة كود تشفير لازم تتعلم برمجة تطبيقات التشفير .غير كده هيبقى نظري فقط #cryptography #Crypto #Cipher #CyberSecurity

🚨This is for Nerds … 🤓 How Bitcoin Works Under the Hood ! 🤓 #Cryptography #MyFirstBitcoin series youtu.be/Lx9zgZCMqXE

Feeling like a CaveMan trying to learn how #Bitcoin Lightning ⚡️ Network Works .. ₿ ₿ ₿.. Alice 🙋🏽♀️ —> ₿ob 🤦🏾♂️ | —> Carol 🤦🏻♀️—> Dave 🤷🏻♂️ Glad it Works ! Yet to learn Hooow #MyFirstBitcoin Series youtu.be/yKdK-7AtAMQ

youtube.com
YouTube
Bitcoin Lightning Network Explained: How it Actually Works
#Financial Firms Urged to Prepare for Quantum Computers - ift.tt/Dc8f3YF #quantumcomputing # encryption #cryptography #security #cybersecurity #infosec

Quantum Computing: The Next Big Threat to Bitcoin? Quantum breakthroughs could one day shatter the #cryptography protecting #Bitcoin and #cryptocurrencies. Shor’s Algorithm alone puts millions of #BTC at risk if exposed public keys can be cracked. In our new Financial Fox…

Join Verisign’s Joseph Harvey on Sept. 24 at the @NIST Sixth PQC Standardization Conference, where he’ll speak on the need for a post-quantum #cryptography strategy for #DNSSEC that utilizes two different types of algorithms. By combining a low-impact algorithm and a…

Enter @zama_fhe, pioneering Fully Homomorphic Encryption (FHE)! This groundbreaking tech allows computations on encrypted data, ensuring ultimate privacy and security. #FHE #Privacy #cryptography

TII’s CRC team helped uncover and fix a critical bug in NIST’s Deterministic ECDSA tests for the P-521 curve—boosting global cryptographic standards and digital security. Proud to support stronger cybersecurity. #TII #Cryptography #Cybersecurity #Innovation


Delivered a talk on “Quantum Communication & Cryptographic Protocols” at IEEE CBIT Signal Processing Society. Great discussions on quantum communication, secure protocols & future of communication security. #QuantumComputing #Cryptography #IEEE #Quinfosys

The quantum countdown has begun. Global deadlines are set for a cryptographic overhaul. The future of digital security is no longer theoretical—it's a real-world transition. It's time to get talking. 👇 hubs.li/Q03MvQKL0 #PQC #cryptography #PQC #postquantum

2/ Blockchain security is built on two core cryptographic pillars: SHA-256 ensures data integrity and mining protection (as in Bitcoin), while ECDSA verifies wallet transactions across most networks. ⚡ #blockchain #cryptography

The quantum apocalypse is a real risk to #Bitcoin and other blockchains. Migrate to post quantum #cryptography asap #pqc #y2q #qday

We are excited to announce the first speaker of Cryptist: @cryptoquick from @andurobtc and the author of BIP360! 🔎 He will explore #Bitcoin’s quantum vulnerabilities and present #BIP360, introducing post-quantum #cryptography for Taproot-compatible addresses.

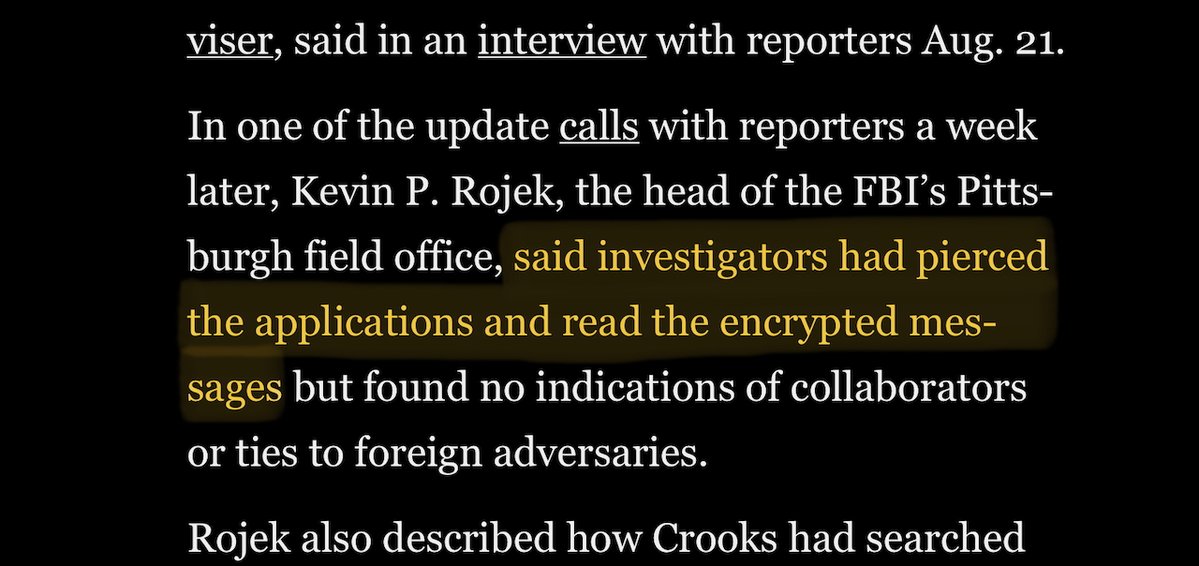
I feel like this tidbit from @CarolLeonnig's excellent reporting on #ButlerPA is being overlooked by the #cryptography community. washingtonpost.com/investigations… #encryption
The @CryptoVillage at @DEFCON 33 delivered great content on #cryptography & #privacy. 🕵🏻♀️ Congrats to @naomibrockwell @wbm312 @spaceraccoonsec @MateuszChrobok @yaelwrites @controlpaths @supersat @jshchnz & @taoeffect! All #DEFCON33 villages 👇🏽 infosecmap.com/event/def-con-… #InfoSec

Introducing @zama_fhean open source cryptography company building cutting-edge Fully Homomorphic Encryption (FHE) solutions for blockchain & AI. #Zama, #FHE, #Cryptography, #Privacy, #Blockchain

Something went wrong.
Something went wrong.
United States Trends
- 1. Ukraine 447K posts
- 2. #FanCashDropPromotion 3,236 posts
- 3. Le Cowboy N/A
- 4. #FursuitFriday 12.4K posts
- 5. Putin 147K posts
- 6. #pilotstwtselfieday N/A
- 7. #FridayVibes 6,462 posts
- 8. Dave Aranda N/A
- 9. #TrumpCrushesYourDreams 2,340 posts
- 10. Kenyon 1,663 posts
- 11. ON SALE NOW 12.9K posts
- 12. Sam LaPorta N/A
- 13. Good Friday 70.1K posts
- 14. SINGSA LATAI EP4 165K posts
- 15. October CPI 1,414 posts
- 16. Fang Fang 13.4K posts
- 17. Eric Swalwell 5,822 posts
- 18. John Wall N/A
- 19. UNLAWFUL 150K posts
- 20. Ja Rule 1,837 posts