#exploitdev نتائج البحث
This should be the final set of labs published publicly. That's all folks for now... #RE #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com



Bypassing PIE with partial overwrite? 🔥 Instead of guessing full addresses, just overwrite specific bytes to align with predictable offsets. Precision > brute force. A reminder that security evolves, and so must we. 🛡️ #CyberSecurity #ExploitDev #ReverseEngineering


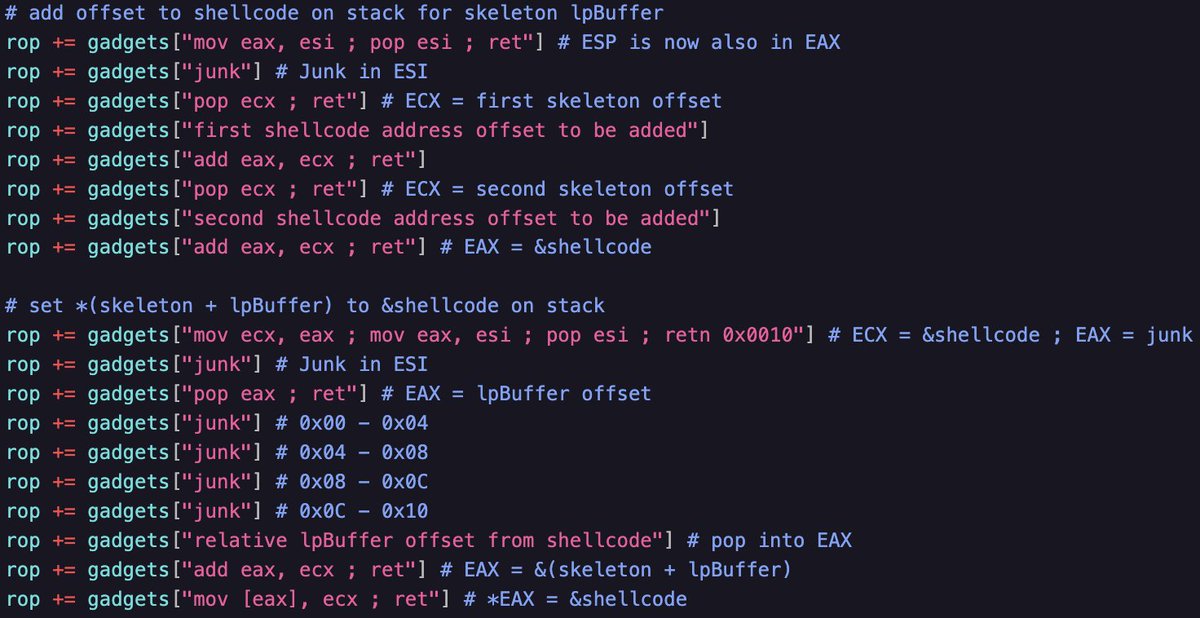
Hand-crafted ROP chain 🛠️! Had limited gadgets, so I used an IAT entry for HeapAlloc and calculated the VirtualAllocStub RVA offset. Got creative without ASLR and possibly should've used a read primitive. Details in the gist! #ROP #ExploitDev #osed gist.githubusercontent.com/snowcra5h/a7c1…

I’m happy to announce that I passed OSED from @offsectraining 😍😍 I just got the email and man IT FELT SO GOOD #CyberSecurity #exploitdev

Happy New Year 2025! #infosec #CyberSec #ExploitDev #Hacker #Bug #bugbountyhunter #vulnerabilityResearcher #ReverseEngineering #Binex

If you're exploiting a driver offering R/W access to physical memory on Win11 24H2, you can leverage this simple trick to circumvent kernel address leak restrictions and retrieve the kernel base address :p xacone.github.io/kaslr_leak_24h… #exploitdev #driverexploitation
🚨 Released a full SEH exploit chain for DeepFreeze 8! With custom shellcode and ROP chain. Software was fully reversed, and an SEH vuln discovered studying for the #OSED 💪Blog write-up coming soon.🔍github.com/snowcra5h/Faro… #CyberSecurity #ExploitDev
𝑪𝒊𝒂𝒐 𝑰𝒕𝒂𝒍𝒚, 𝑪𝒊𝒂𝒐 𝑹𝒐𝒎𝒂! 𝑹𝒆𝒂𝒅𝒚 𝒇𝒐𝒓 𝑪𝒐𝒓𝒆𝒍𝒂𝒏? Sign up for our Expert-level stack class: bit.ly/corelan-traini… #corelan #stack #exploitdev #windows11
🇦🇺 Corelan hits Melbourne for the FIRST time! 💥 Stack Exploit Dev: Feb 3–6, 2026 🧨 Heap Masterclass: Feb 9–12, 2026 🎯 w/ @TantoSecurity 🧠 Real skills. No fluff. 💣 Come prepared. 🕐 Early bird ends Sept 2025 👉 bit.ly/corelan-traini… #Corelan #ExploitDev
Pwning LLaMA.cpp RPC Server #LLAMACpp #RPCServer #ExploitDev #CTF pwner.gg/2024/10/03/lla…
New article alert : ek0msUSB medium.com/@ekoms1/ek0msu… #hacker #greyhat #exploitdev #commandandcontrol #payloads




Interested in Software Exploitation? This course is for you and will take you from knowing nothing, to understanding how exploits work and how to write them... I hope it will be useful to someone out there! #Offsec #Cybersecurity #ExploitDev #Debugging youtube.com/watch?v=5GGyFb…

🔔 Reminder: Zürich, Corelan Stack is coming Oct 7–10, 2025 ✅ No nonsense, No BS ✅ Just real-world exploit dev skills 🎟️ eventcreate.com/e/sigs-corelan… 💛 RT appreciated! #corelan #win11 #exploitdev
🇧🇪 Belgian Roots. Global Impact. 🌍 Corelan delivers world-class exploit dev training for Windows: 🔹 Stack Smashing 🔹 Heap Masterclass Built in Europe. Respected worldwide. Sign up 👉 bit.ly/corelan-traini… #CyberSecurity #ExploitDev #MadeInBelgium
⚠️ Afraid of public classes? 🔒 Corelan Academy = private, intense, small-group exploit dev training 2–8 ppl • one-on-one access • flexible timing • competitive pricing • Stack & Heap DM or reply interested #corelan #exploitdev #training #heap #stack #corelanacademy
Ma solution pour les exercices heap du #CTF Protostar github.com/devl00p/blog/b… #exploitdev #reverseengineering #vulndev
ONE more chance this year to take our popular Bootcamp. High-quality materials, real class, real instructor (AND the perfect prep for our heap exploitation class). Seats are selling fast! What are you waiting for? deep-conference.com/predeep-bootca… #corelan#windows11 #exploitdev

💥 Push, Pop, Boom. Corelan Stack isn’t just another course — it’ll make things click. Expert-level stack exploitation. Zero fluff, real deal. “The course filled in gaps I didn’t even know I had.” — Fabio, Brazil 👉 bit.ly/corelan-traini… #corelan #stack #exploitdev
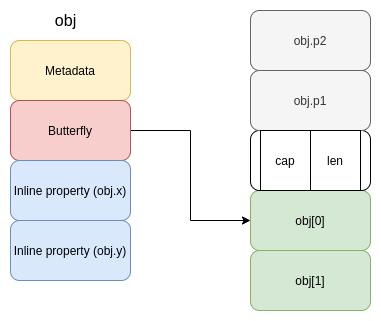
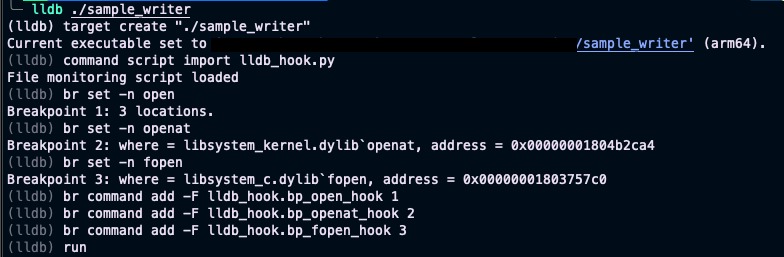
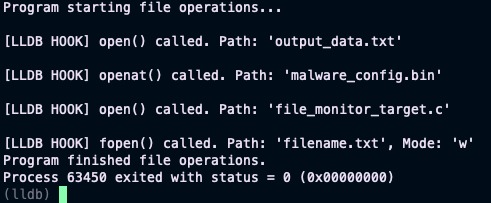
Tip #2: Level up your security analysis! 🚀 Use #lldb & Python 🐍 to dynamically monitor every file a program opens (open/openat/fopen). Crucial for #MalwareAnalysis & #ExploitDev to uncover file system interactions. See what that binary really touches! 💻📂 #CyberSecurity

⚠️ Afraid of public classes? 🔒 Corelan Academy = private, intense, small-group exploit dev training 2–8 ppl • one-on-one access • flexible timing • competitive pricing • Stack & Heap DM or reply interested #corelan #exploitdev #training #heap #stack #corelanacademy
⚠️ Afraid of public classes? 🔒 Corelan Academy = private, intense, small-group exploit dev training 2–8 ppl • one-on-one access • flexible timing • competitive pricing • Stack & Heap DM or reply interested #corelan #exploitdev #training #heap #stack #corelanacademy
New article alert : ek0msUSB medium.com/@ekoms1/ek0msu… #hacker #greyhat #exploitdev #commandandcontrol #payloads




New whitepaper: Polymorphic shellcode bypasses on modern architectures—evasion techniques, detection gaps, and practical defenses. Read: github.com/MottaSec/White… #SecurityResearch #ExploitDev #BlueTeam
CVE-2025-52915 assigned - my first vulnerability!🥳 A classic BYOVD case: kernel driver with unrestricted process termination. Vendor coordination turned out more challenging than the exploit itself. Technical write-up: blacksnufkin.github.io/posts/BYOVD-CV… #ExploitDev #CVE #BYOVD #RedTeam
Privilege escalation isn't always about the shell. Kernel memory leaks can offer direct paths to root access. Details: versprite.com/blog/the-shell… #PrivilegeEscalation #LinuxSecurity #ExploitDev
NEW: Digital Demonology Grimoire - A dark exploration into buffer overflow exploitation & shellcode analysis Perfect reading for👹 github.com/h3xorc1sm/digi… #DEFCON #ExploitDev #Shellcode #BufferOverflow #InfoSec #HackTheGibson
"Those who gaze into the assembler, take care that the assembler does not gaze also into them." The silicon souls whisper their secrets... github.com/h3xorc1sm/digi… #DEFCON #ExploitDev #DigitalDemonology
We dissect a DFG compiler bug we discovered in Safari/WebKit. This post covers root cause, impact, and technical analysis: blog.exodusintel.com/2025/08/04/oop… #WebKit #VulnerabilityResearch #ExploitDev #Safari #CyberSecurity #ExodusIntel
🔔 Reminder: Zürich, Corelan Stack is coming Oct 7–10, 2025 ✅ No nonsense, No BS ✅ Just real-world exploit dev skills 🎟️ eventcreate.com/e/sigs-corelan… 💛 RT appreciated! #corelan #win11 #exploitdev
Bypassing PIE with partial overwrite? 🔥 Instead of guessing full addresses, just overwrite specific bytes to align with predictable offsets. Precision > brute force. A reminder that security evolves, and so must we. 🛡️ #CyberSecurity #ExploitDev #ReverseEngineering


Hand-crafted ROP chain 🛠️! Had limited gadgets, so I used an IAT entry for HeapAlloc and calculated the VirtualAllocStub RVA offset. Got creative without ASLR and possibly should've used a read primitive. Details in the gist! #ROP #ExploitDev #osed gist.githubusercontent.com/snowcra5h/a7c1…

Happy New Year 2025! #infosec #CyberSec #ExploitDev #Hacker #Bug #bugbountyhunter #vulnerabilityResearcher #ReverseEngineering #Binex

I’m happy to announce that I passed OSED from @offsectraining 😍😍 I just got the email and man IT FELT SO GOOD #CyberSecurity #exploitdev

This should be the final set of labs published publicly. That's all folks for now... #RE #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com



It's truly beautiful.🥹Avoiding bad characters, compensating for limited gadgets. It's like crafting a piece of art🎨. Challenges like this make the #OSED so rewarding!💪Got any tricks up your sleeve? Share them with me. Friday is exam day. #ExploitDev #ArtInCode #infosecurity
I really enjoy teaching private classes! Even if you're just a small group (min. 4), willing to travel to Belgium, we can make it happen! I still have some timeslots in November & December. DM if interested @corelanconsult #windows #exploitdev #corelan #nevergiveup

Education is power! corelan-training.com/index.php/trai… #nevergiveup #exploitdev #windows11 #stack #heap @corelanc0d3r

New article alert : ek0msUSB medium.com/@ekoms1/ek0msu… #hacker #greyhat #exploitdev #commandandcontrol #payloads




The whole course, labs, videos, etc can be found below. #Cybersecurity #Offsec #ExploitDev #Debugging #Reversing exploitation.ashemery.com

Interested in Software Exploitation? This course is for you and will take you from knowing nothing, to understanding how exploits work and how to write them... I hope it will be useful to someone out there! #Offsec #Cybersecurity #ExploitDev #Debugging youtube.com/watch?v=5GGyFb…

Mastering buffer overflows in Vulnserver is essential for exploit development. WinDBG aids in debugging vulnerabilities by controlling EIP and generating shellcode. A must-learn for secure environments! 🔍⚙️ #ExploitDev #BufferOverflow link: ift.tt/fFk6AGK

Built my own 64-bit ELF packer — something I always wanted to try. XOR encrypts the .text section with a dynamic key and injects a custom stub in new PT_LOAD segment github.com/0x3xploit/entr… #Linux #ELF #Exploitdev #ReverseEngineering #RedTeam #BinaryAnalysis #infosec



All the Assembly and #RE labs have now been shared. I just need to find the reference to the Crackme(s) I used and then it should be 100% complete. #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com

ONE more chance this year to take our popular Bootcamp. High-quality materials, real class, real instructor (AND the perfect prep for our heap exploitation class). Seats are selling fast! What are you waiting for? deep-conference.com/predeep-bootca… #corelan#windows11 #exploitdev

🧠 Heap exploits today = brains > brute force. Leaks, UAFs, type confusion—APT-level tactics. Is your defense still stuck in 2015? 👇 What’s your go-to heap hardening move? #CyberSecurity #ExploitDev 👉️ sec.co/blog/modern-he…

I was driving back home and never thought this last #offsec #ExploitDev #SoftwareExploitation share for 2022 will go this viral. THANKS to all those who Retweeted/Liked/Commented/etc... Wishing you all a great 2023 ...

Uploaded all my Offensive Security & Reverse Engineering (OSRE) course labs (docx) to my repo found below. Most of them have very detailed instructions and should be great to get you started in Software Exploitation. 1/n #Offsec #SoftwareExploitation #RE exploitation.ashemery.com

YES! 🔥 The legendary Corelan (@corelanc0d3r) exploit development training is happening in ROME! 🇮🇹 Absolutely stoked about this opportunity right here in Italy. Time to level up those #ExploitDev skills! 💪 #Corelan #CyberSecurity #InfoSec #Reversing #Rome #Hacking #Cyber

Think kernel bugs are too deep to reach? Think again. 🔥 At #NullconBerlin2025, dive headfirst into a hands-on Linux kernel exploitation with security researcher Andrey Konovalov — no prior kernel knowledge required. Know More: nullcon.net/berlin-2025/tr… #LinuxKernel #ExploitDev

Something went wrong.
Something went wrong.
United States Trends
- 1. FIFA 356K posts
- 2. The WET 117K posts
- 3. FINALLY DID IT 438K posts
- 4. Paraguay 28.1K posts
- 5. Brazil 79.7K posts
- 6. Argentina 230K posts
- 7. Frank Gehry 4,229 posts
- 8. Croatia 25.1K posts
- 9. Portugal 104K posts
- 10. Hep B 15.6K posts
- 11. Matt Campbell 11.1K posts
- 12. Morocco 68K posts
- 13. Warner Bros 245K posts
- 14. Iowa State 9,431 posts
- 15. #Mundial2026 40.9K posts
- 16. Group L 17.8K posts
- 17. #USMNT 1,432 posts
- 18. Ghana 84.4K posts
- 19. Infantino 74.8K posts
- 20. Senegal 52.4K posts