#linuxvulnerability 搜尋結果
Have you heard of THIS NEW #LinuxVulnerability? @Guardicore Labs' @ace__pace highlights the impact of the recent vulnerability in @debian’s #apt buff.ly/2FJU9Mv #LinuxAPT #Linuxhacking #maninthemiddleattack #datacentersecurity #vulnerability
A high-severity flaw in the GNU C Library's dynamic loader, CVE-2023-4911, known as 'Looney Tunables,' has prompted the release of proof-of-concept (PoC) exploits online. . #avmconsulting #LinuxVulnerability, #CVE20234911, #RootPrivileges, #GNUCLibrary, #BufferOverflow,

Warning! Unprivileged Linux Users With UID > INT_MAX Can Execute Any Command #Debian #linux #LinuxVulnerability #privilegeescalation #redhat #Ubuntu #userprivilege #Vulnerability hackhex.com/computer/warni…

Critical vulnerability CVE-2024-27397 in the Linux kernel could allow local privilege escalation. Affects versions 4.1-6.8. Immediate updates recommended. ⚠️ #LinuxVulnerability #PrivilegeEscalation #USA #CybersecurityNews link: ift.tt/h0YtF5b

Los investigadores advierten sobre el nuevo malware OrBit Linux que secuestra el flujo de ejecución csirt.telconet.net/comunicacion/n… #Cybersecurity #LinuxVulnerability #ransomware

Symbiote: un malware sigiloso de Linux dirigido al sector financiero latinoamericano csirt.telconet.net/comunicacion/n… #Cybersecurity #linux #LinuxVulnerability #malware #ciberseguridad #securitynews

Critical Vulnerabilities in Linux and GitLab: Are Your Systems Safe? Visit bornsec.com/critical-vulne… read the full article. Follow us: @bornsec_LLP Contact us: 080-4027 3737 Please write to us: [email protected] Visit us: bornsec.com #Cybersecurity #LinuxVulnerability

🚨 Security Alert Red Hat warns of a backdoor in XZ Utils found in Linux. PROTECT YOUR DATA: 1. Update/downgrade XZ Utils 2. Monitor system activity 3. Strengthen access controls 4. Stay informed 5. Backup data regularly bit.ly/3JhqsB8 #CyberSecurity #LinuxVulnerability

Yesterday a new #LinuxVulnerability:Affects glibc versions 2.2-2.17 and allows remote execution of code by calling #gethostbyname(). ,
Yesterday a new #LinuxVulnerability:Affects glibc versions 2.2-2.17 and #AllowsRemoteExecutionOfCode by calling #gethostbyname(). ,
Two critical flaws (CVE-2025-46415, CVE-2025-46416) in guix-daemon allow local attackers to gain root access via socket exploitation and race conditions. Upgrade immediately! #GuixSecurity #PrivilegeEscalation #LinuxVulnerability #Cybersecurity #PatchNow securityonline.info/privilege-esca…
Make-Me-Root Linux ranjivost sajberinfo.com/2024/04/16/mak… #cve20241086 #kernelexploit #linuxvulnerability #makemeroot #privilegeescalation
sajberinfo.com
Make-Me-Root Linux ranjivost - Sajber Info Security
Nedavno otkrivena ranjivost CVE-2024-1086 Linux jezgra, poznata i kao “Make-Me-Root”, omogućava neprivilegovanim korisnicima da dobiju root pristup na
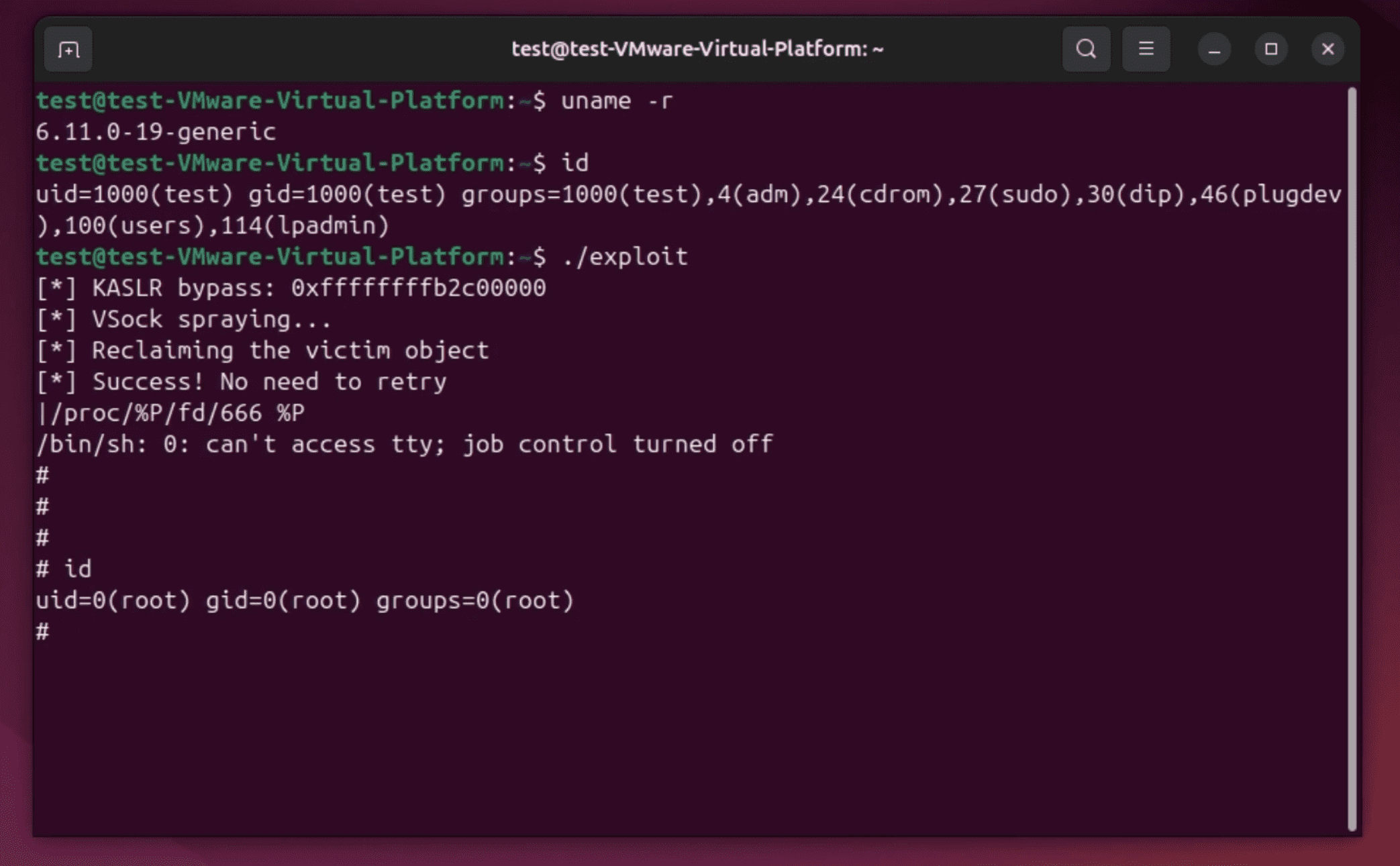
PoC reveals how a Linux vsock driver flaw enables local users to escalate privileges to root via a dangerous Use-After-Free vulnerability. #LinuxVulnerability #KernelExploit #PrivilegeEscalation #PoC securityonline.info/poc-unleashed-…
CISA Warns of Active Exploitation of 'PwnKit' #LinuxVulnerability in the Wild via @TheHackersNews lnkd.in/gfwuFZDB
Linux vulnerability leaves top sites wide open to attackers rt.com/usa/355558-lin… #linux #linuxvulnerability
Linuxカーネルに重大な脆弱性「StackRot」、ただちに確認を news.mynavi.jp/techplus/artic… #LinuxVulnerability #StackRot
Linux users! Read about a recently uncovered Linux kernel vulnerability. The weakness exploits a previously unknown flaw (CVE-2022-2588) to escalate privileges to the maximum level. #LinuxVulnerability #cybersecurity #cybersecurityeducation #ProjectAres thehackernews.com/2022/08/as-nas…
CVE-2018-8781: 8-Year-Old Linux Kernel Bug Discovered buff.ly/2HGDc7f by Milena Dimitrova #linuxkernel #linuxvulnerability #securitychronicles
Two critical flaws (CVE-2025-46415, CVE-2025-46416) in guix-daemon allow local attackers to gain root access via socket exploitation and race conditions. Upgrade immediately! #GuixSecurity #PrivilegeEscalation #LinuxVulnerability #Cybersecurity #PatchNow securityonline.info/privilege-esca…
PoC reveals how a Linux vsock driver flaw enables local users to escalate privileges to root via a dangerous Use-After-Free vulnerability. #LinuxVulnerability #KernelExploit #PrivilegeEscalation #PoC securityonline.info/poc-unleashed-…
Critical vulnerability CVE-2024-27397 in the Linux kernel could allow local privilege escalation. Affects versions 4.1-6.8. Immediate updates recommended. ⚠️ #LinuxVulnerability #PrivilegeEscalation #USA #CybersecurityNews link: ift.tt/h0YtF5b

Critical Vulnerabilities in Linux and GitLab: Are Your Systems Safe? Visit bornsec.com/critical-vulne… read the full article. Follow us: @bornsec_LLP Contact us: 080-4027 3737 Please write to us: [email protected] Visit us: bornsec.com #Cybersecurity #LinuxVulnerability

#LinuxVulnerability Alert: A decade-old flaw is putting CUPS at risk for DDoS and RCE attacks! Uptycs and Akamai identified 58K+ vulnerable devices that could be exploited with amplification factors up to 600x. 🔗 Learn more: bit.ly/3zFhk8v #CyberSecurity #Uptycs
Researcher develops an "Ld_preload" worm, highlighting potential security risks in Linux systems. #CyberSecurity #LinuxVulnerability ift.tt/Mqeug4H
🚨 Security Alert Red Hat warns of a backdoor in XZ Utils found in Linux. PROTECT YOUR DATA: 1. Update/downgrade XZ Utils 2. Monitor system activity 3. Strengthen access controls 4. Stay informed 5. Backup data regularly bit.ly/3JhqsB8 #CyberSecurity #LinuxVulnerability

A high-severity flaw in the GNU C Library's dynamic loader, CVE-2023-4911, known as 'Looney Tunables,' has prompted the release of proof-of-concept (PoC) exploits online. . #avmconsulting #LinuxVulnerability, #CVE20234911, #RootPrivileges, #GNUCLibrary, #BufferOverflow,

Linuxカーネルに重大な脆弱性「StackRot」、ただちに確認を news.mynavi.jp/techplus/artic… #LinuxVulnerability #StackRot
Linux users! Read about a recently uncovered Linux kernel vulnerability. The weakness exploits a previously unknown flaw (CVE-2022-2588) to escalate privileges to the maximum level. #LinuxVulnerability #cybersecurity #cybersecurityeducation #ProjectAres thehackernews.com/2022/08/as-nas…
Los investigadores advierten sobre el nuevo malware OrBit Linux que secuestra el flujo de ejecución csirt.telconet.net/comunicacion/n… #Cybersecurity #LinuxVulnerability #ransomware

CISA Warns of Active Exploitation of 'PwnKit' #LinuxVulnerability in the Wild via @TheHackersNews lnkd.in/gfwuFZDB
Symbiote: un malware sigiloso de Linux dirigido al sector financiero latinoamericano csirt.telconet.net/comunicacion/n… #Cybersecurity #linux #LinuxVulnerability #malware #ciberseguridad #securitynews

Microsoft Discovers New Privilege Escalation Flaws in Linux Operating System thehackernews.com/2022/04/micros… via @TheHackersNews #Linux #linuxvulnerability #vulnerabilities #cloudsecurity #infosec
The Linux kernel vulnerability named "Dirty Pipe" which comes across the same as Dirty Cow was identified again previously. Visit: stupa.io/post/the-dirty… to read our Cyber Security Engineer Manoj Ghimire @linux_overflow's take on it. #dirtypipe #linuxvulnerability
Researcher Discovers New Critical Linux Kernel 'Dirty Pipe' Vulnerability bitdefender.com/blog/hotforsec… #Linux #linuxvulnerability #cybersecuritynews #informationsecurity
Warning! Unprivileged Linux Users With UID > INT_MAX Can Execute Any Command #Debian #linux #LinuxVulnerability #privilegeescalation #redhat #Ubuntu #userprivilege #Vulnerability hackhex.com/computer/warni…

Have you heard of THIS NEW #LinuxVulnerability? @Guardicore Labs' @ace__pace highlights the impact of the recent vulnerability in @debian’s #apt buff.ly/2FJU9Mv #LinuxAPT #Linuxhacking #maninthemiddleattack #datacentersecurity #vulnerability

Critical vulnerability CVE-2024-27397 in the Linux kernel could allow local privilege escalation. Affects versions 4.1-6.8. Immediate updates recommended. ⚠️ #LinuxVulnerability #PrivilegeEscalation #USA #CybersecurityNews link: ift.tt/h0YtF5b

A high-severity flaw in the GNU C Library's dynamic loader, CVE-2023-4911, known as 'Looney Tunables,' has prompted the release of proof-of-concept (PoC) exploits online. . #avmconsulting #LinuxVulnerability, #CVE20234911, #RootPrivileges, #GNUCLibrary, #BufferOverflow,

Symbiote: un malware sigiloso de Linux dirigido al sector financiero latinoamericano csirt.telconet.net/comunicacion/n… #Cybersecurity #linux #LinuxVulnerability #malware #ciberseguridad #securitynews

Los investigadores advierten sobre el nuevo malware OrBit Linux que secuestra el flujo de ejecución csirt.telconet.net/comunicacion/n… #Cybersecurity #LinuxVulnerability #ransomware

Critical Vulnerabilities in Linux and GitLab: Are Your Systems Safe? Visit bornsec.com/critical-vulne… read the full article. Follow us: @bornsec_LLP Contact us: 080-4027 3737 Please write to us: [email protected] Visit us: bornsec.com #Cybersecurity #LinuxVulnerability

🚨 Security Alert Red Hat warns of a backdoor in XZ Utils found in Linux. PROTECT YOUR DATA: 1. Update/downgrade XZ Utils 2. Monitor system activity 3. Strengthen access controls 4. Stay informed 5. Backup data regularly bit.ly/3JhqsB8 #CyberSecurity #LinuxVulnerability

Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Birthday Charlie 26K posts
- 2. Good Tuesday 23.9K posts
- 3. #tuesdayvibe 2,518 posts
- 4. #Worlds2025 24.2K posts
- 5. Bears 92.2K posts
- 6. Romans 10.6K posts
- 7. Pentagon 68.8K posts
- 8. Blinken 25.4K posts
- 9. Dissidia 4,546 posts
- 10. Snell 25.8K posts
- 11. Jake Moody 14.6K posts
- 12. Martin Sheen 5,695 posts
- 13. Jayden 23.8K posts
- 14. Trump's Gaza 138K posts
- 15. Joji 36K posts
- 16. Swift 293K posts
- 17. Conquered 30K posts
- 18. Time Magazine 14.5K posts
- 19. #BearDown 2,497 posts
- 20. Ben Johnson 4,703 posts