#networksegmentation search results
Claroty was named a Leader in IoT Security, receiving the highest possible scores in 10 criteria and the only Leader to earn the highest scores in #NetworkSegmentation & microsegmentation, deployment options, and partner ecosystem. 📌 hubs.li/Q03Kbjh40

Use isolated network segments for darknet activities. #NetworkSegmentation #DarknetOps #SecureArchitecture
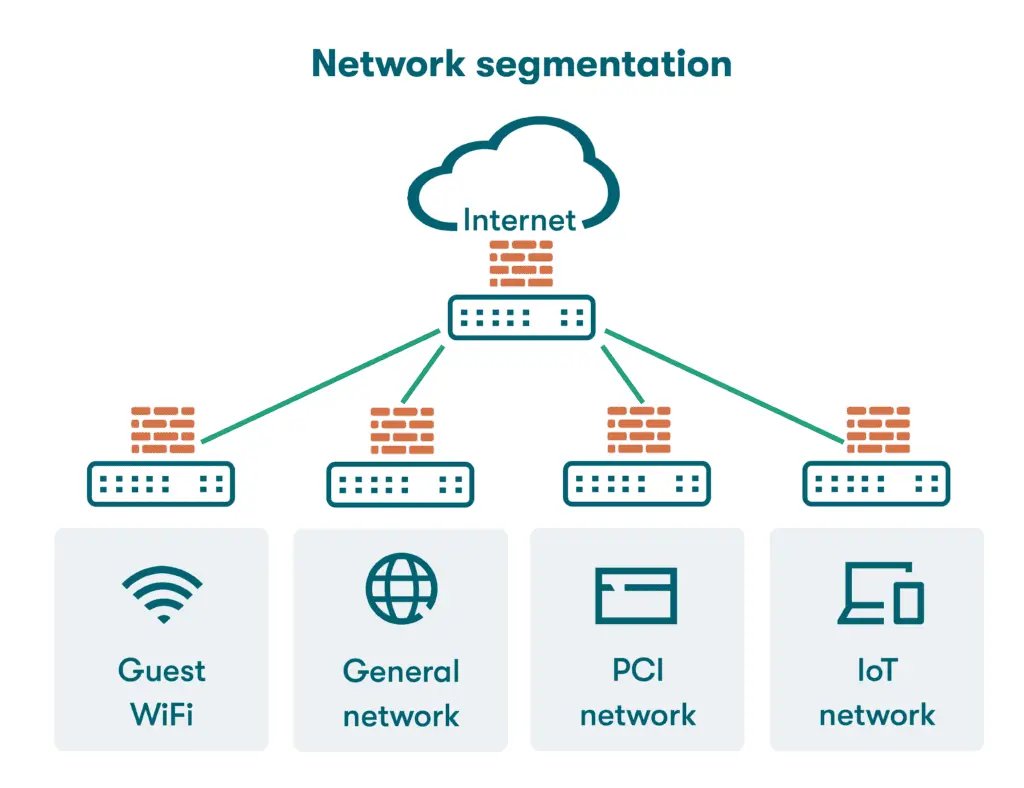
Segmentation limits damage—but only if traffic rules are enforced and monitored. Unchecked connections turn ‘protected zones’ into false security. #NetworkSegmentation #CyberResilience #DefenseInDepth #ArcherEnergySolutions

⚡ Ask Archer: True resilience isn’t just isolation. Layered defenses, strong access controls, and continuous monitoring work together to protect critical systems from evolving threats. 📩 [email protected] #AskArcher #NetworkSegmentation #CriticalInfrastructure


Being proactive is key to a successful #cybersecurity strategy. Leverage SonicWall’s 5-point #networksegmentation checklist to reduce attack surfaces, enhance defenses, and secure your network. Learn more ➡️ bit.ly/3IeqtG9

Navigating the Challenges of #NetworkSegmentation and Microsegmentation Without Disrupting Operations - buff.ly/3XOXbDS #IT #technology #cybersecurity #security #ITsecurity #infosec

Why network segmentation matters for bolstering cybersecurity: - 𝗟𝗶𝗺𝗶𝘁𝗶𝗻𝗴 𝗕𝗿𝗲𝗮𝗰𝗵 𝗜𝗺𝗽𝗮𝗰𝘁 🌐 - 𝗘𝗻𝗵𝗮𝗻𝗰𝗲𝗱 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗖𝗼𝗻𝘁𝗿𝗼𝗹𝘀 🛡️ - 𝗜𝗺𝗽𝗿𝗼𝘃𝗲𝗱 𝗜𝗻𝗰𝗶𝗱𝗲𝗻𝘁 𝗥𝗲𝘀𝗽𝗼𝗻𝘀𝗲 📜 #Cybersecurity #NetworkSegmentation #Defense

Do you want to reduce attack surfaces and better secure your network? SonicWall’s 5-point #networksegmentation checklist can help. Enhance your defense strategy, control access to critical assets, and minimize damage if a breach occurs. Get it here: bit.ly/3IeqtG9

#SonicWall Do you want to reduce attack surfaces and better secure your network? SonicWall’s 5-point #networksegmentation checklist can help. Enhance your defense strategy, control access to critical assets, and minimize damage if a breach occurs. Get it…

Join Catherine and the crew at @ExertisBrdcast as they discuss how to secure your network and prevent cyberattacks in the latest episode of Techsplanation 2.0. Watch the full episode: bit.ly/3DOVTk7 #cyberattack #kvm #networksegmentation #airgapping #matroxvideo #ipkvm
Up-level your #cybersecurity with SonicWall’s 5-point #networksegmentation checklist. Enhance your defenses, control access to critical assets and better secure your network. Rethink your network segmentation strategy today. Learn more here: bit.ly/3IeqtG9

Are these 5 crucial steps part of your #networksegmentation strategy? Empower your #cybersecurity approach with SonicWall’s #networksegmentation checklist. Designed to enhance your defenses, so you can effectively secure and control critical assets. bit.ly/3IeqtG9

Protecting your OT network is crucial! Downtime, financial loss, and even human costs are on the line. Read the full blog: hubs.ly/Q02LbJKv0 #Cybersecurity #OTSecurity #NetworkSegmentation #RiskManagement #ZeroTrust #CriticalInfrastructure

Rethink how to secure and control access to critical assets with #SonicWall. Our 5-point #networksegmentation checklist helps to enhance your defenses, reduce #cyberattack surfaces and secure your network. Up-level your network segmentation strategy today. bit.ly/3IeqtG9

#NetworkSegmentation is evolving with the expanding XIoT landscape. In this blog, read how to speed up segmentation without slowing down operations, and why a proactive strategy makes all the difference. hubs.li/Q03xBkmw0

🔒Enhance your network security with these 4 network segmentation types🌐 Physical, Logical, Wireless, and Device segmentation. Each provides layers of protection, safeguarding your digital assets. #CyberSecurity #NetworkSegmentation #ZeroTrust #InstaSafe

Be proactive, not reactive. SonicWall’s 5-point #networksegmentation checklist helps you to enhance your defenses, reduce attack surfaces, and better secure your network. Ready to rethink your network segmentation strategy? Learn more here: bit.ly/3IeqtG9

Research shows that large numbers of Operational and Clinical #IoT assets ship with known vulnerabilities, and in many cases are not (or cannot be) routinely patched. Find out how #NetworkSegmentation can help improve your Cyber Posture. #IoMT hubs.ly/Q01QtFpP0

Don’t let your network be vulnerable to a single attack. By segmenting your network you can keep your sensitive data secure and minimize risk. Scroll through to see our top network segmentation tips. #NetworkSegmentation #CyberSecurityTips




A network that is secure by design, with effective access control, segmentation and contextual awareness helps you to identify risks, prevent threats and limit the blast radius of a successful attack. Find out more - hubs.ly/Q01QtQzv0 #NetworkSegmentation #NetworkSecurity

Maximize gateway security with network segmentation to protect sensitive data, deploy multiple distributed gateways to avoid single points of failure, and enhance performance across hybrid and remote environments. #NetworkSegmentation #HybridWork ift.tt/kqWGuQh
Segmentation limits damage—but only if traffic rules are enforced and monitored. Unchecked connections turn ‘protected zones’ into false security. #NetworkSegmentation #CyberResilience #DefenseInDepth #ArcherEnergySolutions

⚡ Ask Archer: True resilience isn’t just isolation. Layered defenses, strong access controls, and continuous monitoring work together to protect critical systems from evolving threats. 📩 [email protected] #AskArcher #NetworkSegmentation #CriticalInfrastructure


What is zero trust network segmentation? It reduces the attack surface by isolating potential threats. Every access request is verified, ensuring better control. #ZeroTrust #NetworkSegmentation
Data diodes enforce one-way traffic. Great for integrity, but don’t expect them to solve every security challenge. #DataDiodes #NetworkSegmentation #OTSecurity #ArcherEnergySolutions

IoT devices often lack proper security. Segment networks to reduce risk #IoTSecurity #NetworkSegmentation #CyberRisk #TechTrends
Cyber Fact 164 #Cybersecurity #Facts #NetworkSegmentation #Attack #CriticalInfrastructure #ArcherEnergySolutions

Flat networks are a hacker’s playground. Segmentation creates chokepoints that slow intruders and buy defenders time. #NetworkSegmentation #CyberDefense #OTSecurity #ArcherEnergySolutions

One weak link can put your entire hospital network at risk. Network segmentation protects sensitive systems, boosts HIPAA compliance, and keeps operations running smoothly. #NetworkSegmentation #HealthcareSecurity #DataProtection #ITForScrubs #Healthcare itforscrubs.com/blog/segmentin…
Cyber Definition: Network Segmentation #Cybersecurity #Definition #NetworkSegmentation #Breach #ArcherEnergySolutions

Cyber Fact 163 #Cybersecurity #Facts #NetworkSegmentation #CriticalInfrastructure #Breach #ArcherEnergySolutions

The Purdue Model has guided network segmentation for decades—but is it enough for today’s IT/OT environments? Stacy Bressler breaks it down in our new On Target with Archer episode. Watch here: youtu.be/zwfS1AbVDKI #PurdueModel #NetworkSegmentation #CriticalInfrastructure #OT
youtube.com
YouTube
The Purdue Model Explained: Does It Still Protect Critical Infrastr...
The Purdue Model isn’t just theory—it’s a map for survival. Without proper segmentation, a breach at the corporate level can cascade down to control systems. #PurdueModel #NetworkSegmentation #CyberResilience #ArcherEnergySolutions

Today's pentest crystal ball. Implement network segmentation across all systems. Visit ayb.ad. #NetworkSegmentation #CyberDefence #SecureNetworks #CyberBestPractices

IT upgrades every few years. OT keeps hardware for decades. One is elastic and adaptable, the other static and purpose-built. This shapes how each must be secured. Read why it matters: hubs.ly/Q03CsyJf0 #OTsecurity #NetworkSegmentation #CriticalInfrastructure
Municipal IoT deployments—from smart meters to traffic sensors—use network segmentation and certificate-based authentication to prevent lateral attacks .#IoTSecurity #NetworkSegmentation
What Is Network Segmentation in Cyber Security and Why It Matters Learn how network segmentation boosts cyber security by reducing risks and limiting threats. skillogic.com/blog/what-is-n… #CyberSecurityCourse #NetworkSegmentation #SkillogicCyberSecurity #SkillogicInstitute
Cyber Definition: Network Segmentation #Cybersecurity #Definition #NetworkSegmentation #Breach #ArcherEnergySolutions

Cyber Fact 163 #Cybersecurity #Facts #NetworkSegmentation #CriticalInfrastructure #Breach #ArcherEnergySolutions

Flat networks are a hacker’s playground. Segmentation creates chokepoints that slow intruders and buy defenders time. #NetworkSegmentation #CyberDefense #OTSecurity #ArcherEnergySolutions

Segmentation limits damage—but only if traffic rules are enforced and monitored. Unchecked connections turn ‘protected zones’ into false security. #NetworkSegmentation #CyberResilience #DefenseInDepth #ArcherEnergySolutions

Cyber Fact 164 #Cybersecurity #Facts #NetworkSegmentation #Attack #CriticalInfrastructure #ArcherEnergySolutions

Data diodes enforce one-way traffic. Great for integrity, but don’t expect them to solve every security challenge. #DataDiodes #NetworkSegmentation #OTSecurity #ArcherEnergySolutions

⚡ Ask Archer: True resilience isn’t just isolation. Layered defenses, strong access controls, and continuous monitoring work together to protect critical systems from evolving threats. 📩 [email protected] #AskArcher #NetworkSegmentation #CriticalInfrastructure


Use isolated network segments for darknet activities. #NetworkSegmentation #DarknetOps #SecureArchitecture

Claroty was named a Leader in IoT Security, receiving the highest possible scores in 10 criteria and the only Leader to earn the highest scores in #NetworkSegmentation & microsegmentation, deployment options, and partner ecosystem. 📌 hubs.li/Q03Kbjh40

Being proactive is key to a successful #cybersecurity strategy. Leverage SonicWall’s 5-point #networksegmentation checklist to reduce attack surfaces, enhance defenses, and secure your network. Learn more ➡️ bit.ly/3IeqtG9

𝗔𝗜 𝗶𝘀 𝘁𝗿𝗮𝗻𝘀𝗳𝗼𝗿𝗺𝗶𝗻𝗴 𝗯𝘂𝘀𝗶𝗻𝗲𝘀𝘀𝗲𝘀. I𝘀 𝗶𝘁 𝗹𝗲𝗮𝘃𝗶𝗻𝗴 𝘆𝗼𝘂 𝗲𝘅𝗽𝗼𝘀𝗲𝗱 𝘁𝗼 𝗰𝘆𝗯𝗲𝗿 𝘁𝗵𝗿𝗲𝗮𝘁𝘀? 🤔cttsonline.com/2025/02/26/why… #CyberSecurity #AI #NetworkSegmentation #ITSecurity #TechTips #CTTSonline #GeorgetownTX #RoundRockTX #AustinTX

Do you want to reduce attack surfaces and better secure your network? SonicWall’s 5-point #networksegmentation checklist can help. Enhance your defense strategy, control access to critical assets, and minimize damage if a breach occurs. Get it here: bit.ly/3IeqtG9

Rethink how to secure and control access to critical assets with #SonicWall. Our 5-point #networksegmentation checklist helps to enhance your defenses, reduce #cyberattack surfaces and secure your network. Up-level your network segmentation strategy today. bit.ly/3IeqtG9

The Purdue Model isn’t just theory—it’s a map for survival. Without proper segmentation, a breach at the corporate level can cascade down to control systems. #PurdueModel #NetworkSegmentation #CyberResilience #ArcherEnergySolutions

Are these 5 crucial steps part of your #networksegmentation strategy? Empower your #cybersecurity approach with SonicWall’s #networksegmentation checklist. Designed to enhance your defenses, so you can effectively secure and control critical assets. bit.ly/3IeqtG9

🔏 Journey into hospital #cybersecurity with this series on the #NetworkSegmentation of medical devices, feat. interviews with hospital systems expoert, who'll offer insights into their experiences, challenges, and triumphs. Sign up here: hubs.li/Q02BfxJ_0
Via @ElisityInc: At RSAC 2025, @Claroty's Skip Sorrels explored the revolutionary transformation of #NetworkSegmentation in #healthcare environments, highlighting how modern solutions are finally solving decade-old challenges. 🎥 Watch here: hubs.li/Q03rpHks0

Up-level your #cybersecurity with SonicWall’s 5-point #networksegmentation checklist. Enhance your defenses, control access to critical assets and better secure your network. Rethink your network segmentation strategy today. Learn more here: bit.ly/3IeqtG9

Why network segmentation matters for bolstering cybersecurity: - 𝗟𝗶𝗺𝗶𝘁𝗶𝗻𝗴 𝗕𝗿𝗲𝗮𝗰𝗵 𝗜𝗺𝗽𝗮𝗰𝘁 🌐 - 𝗘𝗻𝗵𝗮𝗻𝗰𝗲𝗱 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗖𝗼𝗻𝘁𝗿𝗼𝗹𝘀 🛡️ - 𝗜𝗺𝗽𝗿𝗼𝘃𝗲𝗱 𝗜𝗻𝗰𝗶𝗱𝗲𝗻𝘁 𝗥𝗲𝘀𝗽𝗼𝗻𝘀𝗲 📜 #Cybersecurity #NetworkSegmentation #Defense

Navigating the Challenges of #NetworkSegmentation and Microsegmentation Without Disrupting Operations - buff.ly/3XOXbDS #IT #technology #cybersecurity #security #ITsecurity #infosec

Something went wrong.
Something went wrong.
United States Trends
- 1. #VERZUZ 35.4K posts
- 2. Birdman 8,565 posts
- 3. No Limit 25.5K posts
- 4. Mia X 588K posts
- 5. Wayne 35.1K posts
- 6. #HalloweenHavoc 39.4K posts
- 7. Tamar 7,497 posts
- 8. Turk 587K posts
- 9. Master P 4,720 posts
- 10. Snoop 8,752 posts
- 11. Jonas Brothers 3,453 posts
- 12. Juvie 3,139 posts
- 13. Silkk 1,594 posts
- 14. Tim Banks N/A
- 15. Mississippi State 6,588 posts
- 16. Semaj 1,811 posts
- 17. Bama 15.2K posts
- 18. Will Smith 8,659 posts
- 19. Choppa Style 1,568 posts
- 20. Kelly Price 1,059 posts

























