#phishingdetection search results
Another case of callback phishing sent from a trusted platform, detected by our core tech—NACE. #EmailSecurity #PhishingDetection

🚫 Don’t let phishing emails slip through! Meet Catch Phish - Your ultimate in-email analysis and training tool! 🌟 Enhance your security today! Reach out for a demo or visit our website to get started.🛡️ 📩[email protected] #CatchPhish #PhishingDetection #StayAlert

We are excited to share that Sumatak Technologies has chosen to partner with Forge. #cybersecurity #phishingDetection #systemsecurity #startup @adgpi @IAF_MCC @indiannavy @HQ_IDS_India @SumatakTech

Could Chrome put an end to annoying notification prompts on websites? Looks like it #GoogleChrome #NotificationPrompts #PhishingDetection theverge.com/2022/6/9/23161…

TitanHQ’s cybersecurity platform delivers advanced email protection, real-time phishing detection, and seamless integration across your security stack. 🔗Learn more: ow.ly/LccR50VqmuI #Cybersecurity #EmailProtection #PhishingDetection
For anyone dealing with managing domain name abuse, especially at scale. One of my favorite customizable features of the @iQGlobalAS Abuse Manager #dnsabuse #phishingdetection #malwaredetection #cybersecurity #domains #ICANN
Investigating a suspicious domain, url, IP, or hash? Use Threat Intelligence API to uncover its threat type, first seen, and last seen. Try it free → threat-intelligence.whoisxmlapi.com/api Fast, actionable IOC context. #ThreatIntel #IOCEnrichment #PhishingDetection #MalwareAnalysis #Infosec
iQ nominated for Scamfighter Organization of the Year blog.iq.global/2021/01/12/iq-… #domainnames #dnsabuse #phishingdetection #ICANN #domains #domainindustry #malwaredetection

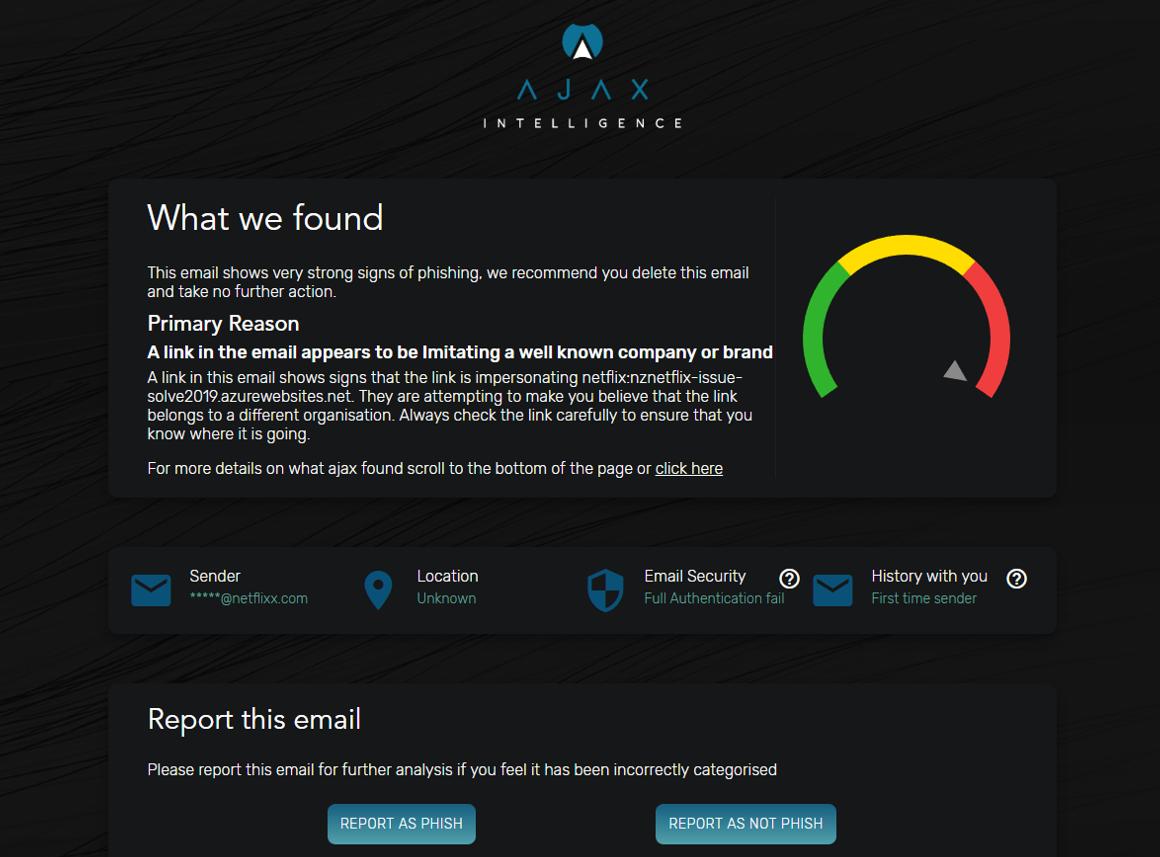
Our Ajax Phishing Detection solution is proving very popular with SMB clients. The explanation page provides clear reasons why a warning banner was applied to the email and guides the user to do the right thing. adepteq.com/ajax #PhishingDetection #CyberSecurity
🔍 Spot phishing emails by checking sender details, unexpected attachments, and urgent language. When in doubt, don't click! Need help? Contact us: tinyurl.com/uvkzcjd8 #PhishingDetection #EmailSafety #CyberAware

S = Sender L = Links A = Attachments M = Message text By giving people the term “SLAM” to remember, it’s quicker for them to do a check on any suspicious or unexpected email without missing something important. mydware.com/about-us/conta… #MYDWARE #phishingdetection #SLAM
To keep employees well prepared, they need training and refreshers on security awareness. Read more 👉 lttr.ai/ABdY4 #PhishingDetection #PasswordSecurity #TrainingFrequency #TeamSharp #CybersecurityAwareness #BusinessPasswordManager #CostlyCompliancePenalty

A new paper was published by Deepak Puthal et al. from Australia. A Novel Logo Identification Technique for Logo-Based Phishing Detection in #CyberPhysicalSystems #phishing #phishingdetection logo-based detection mdpi.com/1999-5903/14/8…

This is one where everyone is cognizant of the need to protect sensitive data as well as avoid phishing scams, and keep passwords secured. Read more 👉 lttr.ai/8kO3 #PhishingDetection #PasswordSecurity #TrainingFrequency #TeamSharp #CybersecurityAwareness

Review security needs for employee devices that access business data and apps, such as securing the phone with a passcode and keeping it properly updated. Read more 👉 lttr.ai/9jwT #PhishingDetection #PasswordSecurity #TrainingFrequency #TeamSharp

The gold standard for security awareness training is to develop a cybersecure culture. Read the full article: How Often Should You Train Employees on Cybersecurity Awareness? ▸ lttr.ai/86bT #PhishingDetection #PasswordSecurity #TrainingFrequency #TeamSharp

Automation and Integration are important keywords when managing abuse, and our new Ruleset for iQ Abuse Manager does both! iq.global/blog/introduci… #dnsabuse #phishingdetection #malwaredetection

📢 #HighlyViewedPapers 📚 Detecting Phishing Domains Using Machine Learning 🔗 mdpi.com/2076-3417/13/8… 👨🔬 by Ms. Shouq Alnemari et al. #phishingdetection #machinelearning #phishingdomains

📣 Call for Reading-Mach. Learn. Knowl. Extr., Volume 6, Issue 1 (March 2024): mdpi.com/2504-4990/6/1 Recommended Paper: "Prompt Engineering or Fine-Tuning? A Case Study on #PhishingDetection with #LargeLanguageModels" 🔗 mdpi.com/2504-4990/6/1/…

Microsoft Threat Intelligence blocked a phishing campaign using an AI-obfuscated SVG attachment with encoded business terms to hide a JavaScript payload redirecting to phishing sites. Detected via advanced AI signals. #PhishingDetection #SVGThreat ift.tt/Lt7phJx
Spotting phishing just got an upgrade—Comet sees what others miss. Next-gen email defense, zero stress. #CyberSecurity #PhishingDetection
AntiPhishStack: LSTM-Based Stacked Generalization Model for Optimized Phishing URL Detection ✏️ Saba Aslam et al. 🔗 brnw.ch/21wUlJO Viewed: 3361; Cited: 17 #mdpisymmetry #phishingdetection #LSTMnetworks #maliciousURL

SOCs use this to trace phishing origins and block rogue mail servers. #EmailSecurity #HeaderAnalysis #PhishingDetection #SOCForensics #scorpion_drogon
AI-Powered Phishing Detection – Does It Actually Work? cybersecuritynews.com/ai-powered-phi… #cybersecurity #phishingdetection #phishingattacks #phishing #threats #targeting #work
TitanHQ’s cybersecurity platform delivers advanced email protection, real-time phishing detection, and seamless integration across your security stack. 🔗Learn more: ow.ly/LccR50VqmuI #Cybersecurity #EmailProtection #PhishingDetection
TitanHQ’s cybersecurity platform delivers advanced email protection, real-time phishing detection, and seamless integration across your security stack. 🔗Learn more: ow.ly/LccR50VqmuI #Cybersecurity #EmailProtection #PhishingDetection
Investigating a suspicious domain, url, IP, or hash? Use Threat Intelligence API to uncover its threat type, first seen, and last seen. Try it free → threat-intelligence.whoisxmlapi.com/api Fast, actionable IOC context. #ThreatIntel #IOCEnrichment #PhishingDetection #MalwareAnalysis #Infosec
TitanHQ’s cybersecurity platform delivers advanced email protection, real-time phishing detection, and seamless integration across your security stack. 🔗Learn more: ow.ly/LccR50VqmuI #Cybersecurity #EmailProtection #PhishingDetection
⚠️ For educational use only. Always operate within legal and authorized boundaries. #PhishingDetection #EmailSecurity #CyberSecurityTraining #SOC #EmailForensics #SecurityTools
Natural Language Processing is transforming how we detect phishing by analyzing linguistic patterns, semantic context, and deception markers in real time. Read on via RSA Conference: rsaconference.com/library/blog/t… #Cybersecurity #NLP #PhishingDetection #AIinSecurity #CyberConsciousAI
Enhance your cybersecurity by adopting advanced phishing detection strategies. Learn how interactive sandboxes and AI tools can protect against evolving threats. #CyberSecurity #PhishingDetection #AI #InfoSec thedailytechfeed.com/enhancing-phis…
thedailytechfeed.com
Enhancing Phishing Detection: A Comprehensive Guide to Identifying and Mitigating Threats
Enhancing Phishing Detection: A Comprehensive Guide to Identifying and Mitigating Threats The Daily Tech Feed -
*Overall Insights* Imbalanced data hurt precision across models. SMOTE & class weighting helped. Random Forest performed best overall. Next steps: Multiclass Classification! #ML #PhishingDetection
TitanHQ’s cybersecurity platform delivers advanced email protection, real-time phishing detection, and seamless integration across your security stack. 🔗Learn more: ow.ly/LccR50VqmuI #Cybersecurity #EmailProtection #PhishingDetection
AI-powered security systems can detect and prevent phishing attacks by analyzing emails and identifying suspicious activity. AI-driven phishing detection is a critical component of modern security. #AIandSecurity #PhishingDetection
To the cybersecurity pros out there, what other methods or tools do you use for analyzing phishing emails? I’d love to learn more and add them to my growing toolkit. 8/8 #SOCAnalyst #PhishingDetection #BlueTeam #EmailSecurity
Fighting cyber threats with AI-powered defense! 🚨 From phishing detection to dark web surveillance, hawkshield.ai delivers real-time protection & unmatched insight 🛡️ Stay ahead with intelligent threat detection. #PhishingDetection #CyberThreats #AIDefense #Hawkshield

We are excited to share that Sumatak Technologies has chosen to partner with Forge. #cybersecurity #phishingDetection #systemsecurity #startup @adgpi @IAF_MCC @indiannavy @HQ_IDS_India @SumatakTech

Recognizing a scam before even opening it—when your security instincts are on point! 🧐 #phishingdetection #infosec

Another case of callback phishing sent from a trusted platform, detected by our core tech—NACE. #EmailSecurity #PhishingDetection

📢 #HighlyViewedPapers 📚 Detecting Phishing Domains Using Machine Learning 🔗 mdpi.com/2076-3417/13/8… 👨🔬 by Ms. Shouq Alnemari et al. #phishingdetection #machinelearning #phishingdomains

A new paper was published by Deepak Puthal et al. from Australia. A Novel Logo Identification Technique for Logo-Based Phishing Detection in #CyberPhysicalSystems #phishing #phishingdetection logo-based detection mdpi.com/1999-5903/14/8…

🚫 Don’t let phishing emails slip through! Meet Catch Phish - Your ultimate in-email analysis and training tool! 🌟 Enhance your security today! Reach out for a demo or visit our website to get started.🛡️ 📩[email protected] #CatchPhish #PhishingDetection #StayAlert

🔥 Read our Paper 📚 Enhanced Feature Selection Using Genetic Algorithm for Machine-Learning-Based Phishing URL Detection 🔗 mdpi.com/2076-3417/14/1… 👨🔬 by Emre Kocyigit et al. #featureselection #geneticalgorithm #phishingdetection @uni_lu

@segasec_com adds early-warning service for #phishingdetection. The new feature can detect scam takeover efforts before they occur. https:// zcu.io/0jG1

📣 Call for Reading-Mach. Learn. Knowl. Extr., Volume 6, Issue 1 (March 2024): mdpi.com/2504-4990/6/1 Recommended Paper: "Prompt Engineering or Fine-Tuning? A Case Study on #PhishingDetection with #LargeLanguageModels" 🔗 mdpi.com/2504-4990/6/1/…

iQ nominated for Scamfighter Organization of the Year blog.iq.global/2021/01/12/iq-… #domainnames #dnsabuse #phishingdetection #ICANN #domains #domainindustry #malwaredetection

#highlycitedpaper Title: A #DeepLearning-Based #PhishingDetection System Using #CNN, LSTM, and LSTM-CNN Authors: Zainab Alshingiti, Rabeah Alaqel, et al. Views 16258, Citations 63 Find more at: mdpi.com/2079-9292/12/1… #mdpielectronics #openaccess #electronics

AntiPhishStack: LSTM-Based Stacked Generalization Model for Optimized Phishing URL Detection ✏️ Saba Aslam et al. 🔗 brnw.ch/21wUlJO Viewed: 3361; Cited: 17 #mdpisymmetry #phishingdetection #LSTMnetworks #maliciousURL

To keep employees well prepared, they need training and refreshers on security awareness. Read more 👉 lttr.ai/ABdY4 #PhishingDetection #PasswordSecurity #TrainingFrequency #TeamSharp #CybersecurityAwareness #BusinessPasswordManager #CostlyCompliancePenalty

Could Chrome put an end to annoying notification prompts on websites? Looks like it #GoogleChrome #NotificationPrompts #PhishingDetection theverge.com/2022/6/9/23161…

This is one where everyone is cognizant of the need to protect sensitive data as well as avoid phishing scams, and keep passwords secured. Read more 👉 lttr.ai/8kO3 #PhishingDetection #PasswordSecurity #TrainingFrequency #TeamSharp #CybersecurityAwareness

Review security needs for employee devices that access business data and apps, such as securing the phone with a passcode and keeping it properly updated. Read more 👉 lttr.ai/9jwT #PhishingDetection #PasswordSecurity #TrainingFrequency #TeamSharp

The gold standard for security awareness training is to develop a cybersecure culture. Read the full article: How Often Should You Train Employees on Cybersecurity Awareness? ▸ lttr.ai/86bT #PhishingDetection #PasswordSecurity #TrainingFrequency #TeamSharp

Our Ajax Phishing Detection solution is proving very popular with SMB clients. The explanation page provides clear reasons why a warning banner was applied to the email and guides the user to do the right thing. adepteq.com/ajax #PhishingDetection #CyberSecurity

Automation and Integration are important keywords when managing abuse, and our new Ruleset for iQ Abuse Manager does both! iq.global/blog/introduci… #dnsabuse #phishingdetection #malwaredetection

No more falling for phishing scams! #AI can now detect phishing attempts before they even reach you. 🛡️ #PhishingDetection #AIinAction #CyberAwareness

Something went wrong.
Something went wrong.
United States Trends
- 1. #River 5,746 posts
- 2. Jokic 27.6K posts
- 3. Lakers 52.9K posts
- 4. Namjoon 59.1K posts
- 5. #AEWDynamite 51.4K posts
- 6. #ReasonableDoubtHulu N/A
- 7. Rejoice in the Lord 1,127 posts
- 8. Clippers 15.1K posts
- 9. Shai 16.7K posts
- 10. Simon Nemec 2,354 posts
- 11. Thunder 40.7K posts
- 12. #NIKKE3rdAnnivBattleReport 10.4K posts
- 13. #dispatch 84.1K posts
- 14. Mikey 72.9K posts
- 15. Ty Lue 1,256 posts
- 16. Rory 8,364 posts
- 17. Visi 7,649 posts
- 18. Steph 31.5K posts
- 19. Valve 61.7K posts
- 20. Joker 27.3K posts
































