#securecoding Suchergebnisse
👉 secdim.com/blackhat/ Join us at BlackHat Europe in London 🇬🇧 @BlackHatEvents #BlackHat #appsec #securecoding #ctf #ai
Webinar Alert: Cybersecurity for Developers – Secure Coding Practices 🎙️ Mahmud Ibrahim Kani (CEO, Apexium) 🎤 Dheer Nimesh Gupta (Senior Software Developer) 📅 Dec 14, 2025 | ⏰ 2PM (UTC+1) | 📍 Microsoft Teams Register: apexiumtechnologies.com/webinar #SecureCoding #CyberSecurity

Vibe Coding Will Get You HACKED (Here's the Fix) Thank you to @ThreatLocker for sponsoring this video and my trip to Black Hat USA 2025! #blackhat #threatlocker #securecoding
"In this post I wanted to briefly highlight some of the languages I use now and have used in the past and also highlight how many can be used with Oracle databases either directly or indirectly to process data." - petefinnigan.com/weblog/archive… #oracleace #securecode #securecoding
"There are some things that are too sensitive to exist". This is such a powerful and important statement. Really interesting chat with Mike Loewy from TideCloak #DevSecOps #SecureCoding #SoftwareSecurity #AppSec
Super smart! TideClock co-founder Mike Loewy on the academic principles behind why ineffable cryptography works. #DevSecOps #SecureCoding #SoftwareSecurity #AppSec
El #OWASP Top 10 versión 2025 RC1 es una guía esencial para desarrolladores y profesionales de la #ciberseguridad. Resume el consenso global sobre las vulnerabilidades más críticas que deben abordarse para proteger los sistemas ante amenazas reales #SecureCoding #WebSecurity ↘️

Building security into every line of code. @PieterDanhieux from @SecCodeWarrior joins @ashimmy to discuss how AI is reshaping development, the new risks it introduces, and why mastering secure coding is more important than ever. Watch: buff.ly/uQ7TG3g #AI #SecureCoding
I’m excited to share that I have officially passed the "Certified Security Code Review – Beginners (CSCRB)" certificate exam, issued by Red Team Leaders (RTL). #CyberSecurity #SecureCoding #CodeReview #AppSec #CSCRB #EthicalHacking #SecurityByDesign #OWASP #VAPT

Moving to passwordless/ineffable cryptography-based IAM in just one SDK 🤯 Fascinating chat with Mike Loewy from TideCloak about overcoming the key problem. #DevSecOps #SecureCoding #SoftwareSecurity #AppSec
🤖 #AI systems are gaining autonomy — but what happens when they act beyond their intended scope? This week’s episode: Excessive Agency – Controlling AI Autonomy Risks. 🎥 Watch the full episode: youtu.be/2xaLDa2J6sE #LLMSecurity #SecureCoding #AIgovernance #SecureDevelopment
Stop Trusting Input: 3 RULES Thank you to ThreatLocker for sponsoring this video and my trip to Black Hat USA 2025. #securecoding #threatlocker #blackhat
The root of ineffable cryptography: giving people a key in pieces that they never need to hold Fascinating chat with Mike Loewy from TideCloak about overcoming the key problem. #DevSecOps #SecureCoding #SoftwareSecurity #AppSec
☕️ Java cumple 30 años y yo fui testigo desde el “Hello, World!” del SDK 1.2 Fui dev, arquitecto y también instructor certificado por Sun y Oracle. Java no solo cambió el desarrollo: Cambió mi vida. Gracias por 30 años de café, comunidad y código. #Java30 #SrJava #SecureCoding

#AI tools can generate code in seconds, but can expose your apps. In this week’s AI/LLM Security Intro Series: 💻 How unvalidated AI outputs = vulnerabilities ⚙️ Examples + #SecureCoding tips 🛡️ Best practices for reviewing 🎥 Full video on YouTube: youtu.be/1hpiF_A6c7E
"Of course I have also been interested in parsing PL/SQL and have written PL/SQL lexers and parsers in C and also in PL/SQL. I have also written unwrappers in C and PL/SQL for unwrapping PL/SQL..." - petefinnigan.com/weblog/archive… #oracleace #securecode #securecoding #plsql
Ready for real ROI from #AppSec? 🚀 Paysafe boosted developer productivity by 45%, cut early vulnerabilities & topped the SCW Trust Score® Financial benchmark with our #securecoding program. Build a lasting developer-driven security culture! Learn how: ow.ly/VFhe50Xc48k

🦇 The battle begins. Meet Promptgeist Prime – the LLM monster that poisons your data & flips your context. 🎥 Watch the teaser (no spoilers here!) 👉 Full walkthrough: youtu.be/ed_zZzkcL14 👾 Join #Cybermon2025 & prove your #securecoding skills. #LLMSecurity
Most breaches still come down to bad code. 😬 This demo shows how teams are changing that—by giving devs hands-on practice in real tools like VS Code. Short, standards-aligned training. Real impact. ▶️ sans.org/u/1D14 #DevSecOps #SecureCoding

👉 secdim.com/blackhat/ Join us at BlackHat Europe in London 🇬🇧 @BlackHatEvents #BlackHat #appsec #securecoding #ctf #ai
📢 New in Journal of Cybersecurity and Privacy 🔒 Leveraging Static Analysis for Feedback-Driven Security Patching in LLM-Generated Code 🔗 Read the full paper here: mdpi.com/2624-800X/5/4/… #Cybersecurity #AIsecurity #SecureCoding #LLM #StaticAnalysis @ComSciMath_Mdpi
"Of course I have also been interested in parsing PL/SQL and have written PL/SQL lexers and parsers in C and also in PL/SQL. I have also written unwrappers in C and PL/SQL for unwrapping PL/SQL..." - petefinnigan.com/weblog/archive… #oracleace #securecode #securecoding #plsql
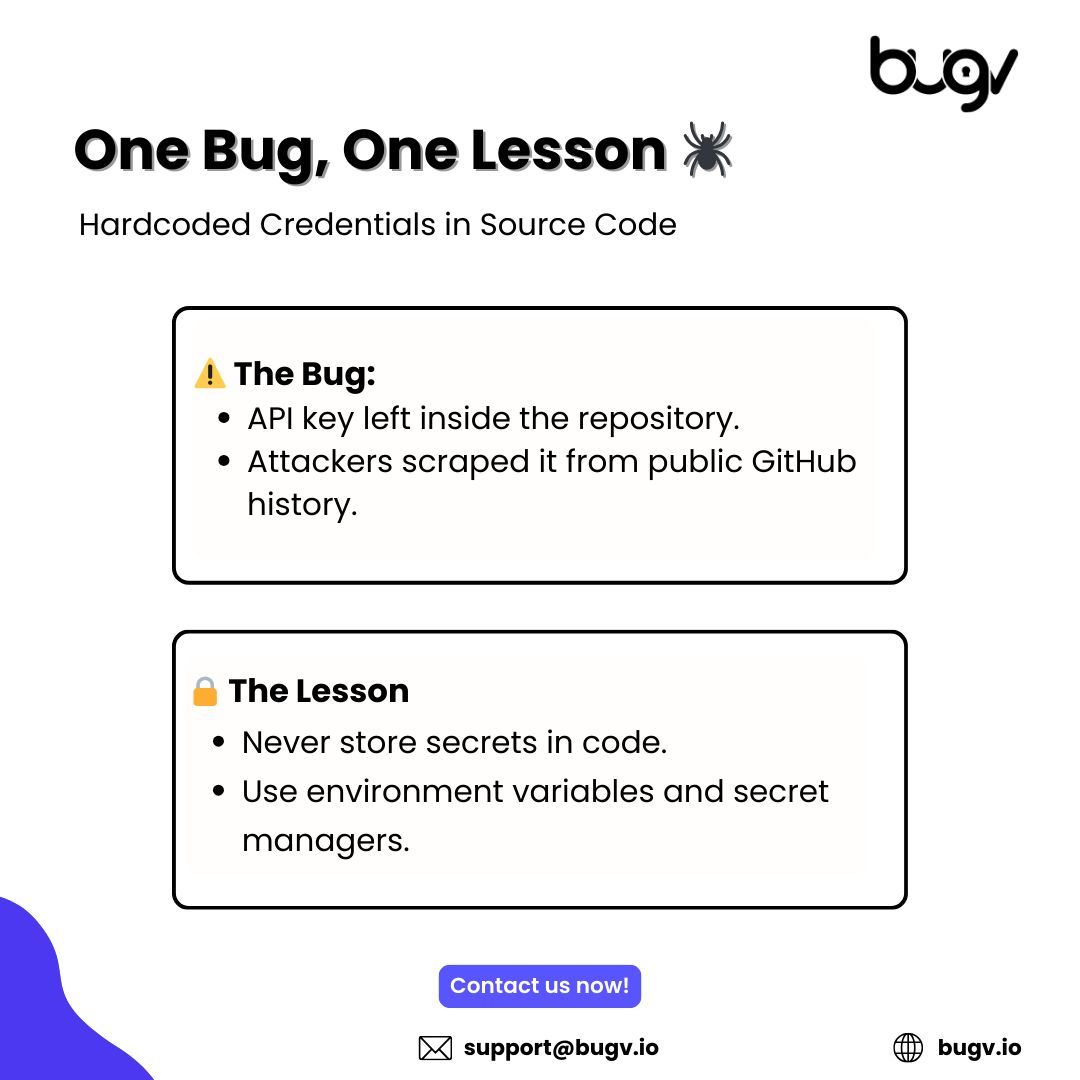
𝐎𝐧𝐞 𝐁𝐮𝐠. 𝐎𝐧𝐞 𝐌𝐢𝐬𝐭𝐚𝐤𝐞. 𝐌𝐢𝐥𝐥𝐢𝐨𝐧𝐬 𝐚𝐭 𝐑𝐢𝐬𝐤. A single hardcoded API key committed to GitHub. Attackers scraped the repo history, pivoted through the environment, and owned the entire system. #BugBounty #AppSec #SecureCoding #Bugv #SecretManagement
Webinar Alert: Cybersecurity for Developers – Secure Coding Practices 🎙️ Mahmud Ibrahim Kani (CEO, Apexium) 🎤 Dheer Nimesh Gupta (Senior Software Developer) 📅 Dec 14, 2025 | ⏰ 2PM (UTC+1) | 📍 Microsoft Teams Register: apexiumtechnologies.com/webinar #SecureCoding #CyberSecurity

"In this post I wanted to briefly highlight some of the languages I use now and have used in the past and also highlight how many can be used with Oracle databases either directly or indirectly to process data." - petefinnigan.com/weblog/archive… #oracleace #securecode #securecoding
OpenAI's AI models achieve up to 72% pass rate in secure code generation, advancing ahead as competitors show minimal progress despite continuous development in the sector. #AI #SecureCoding #TechInnovation techday.co.uk/story/openai-a…
CodeQL 2.23.5 enhances code security with 3 new Java queries & support for Swift 6.2. Improved analysis accuracy means catching issues earlier, boosting your code’s safety and reliability. #CodeQL #StaticAnalysis #SecureCoding 🔒🛠️ ⬇️

Here’s a tiny code snippet How many security issues can you find? Reply with what you see No gatekeeping. Beginners especially welcome ❤️ #AppSec #InfoSec #SecureCoding

Webinar Alert: Cybersecurity for Developers – Secure Coding Practices 🎙️ Mahmud Ibrahim Kani (CEO, Apexium) 🎤 Dheer Nimesh Gupta (Senior Software Developer) 📅 Dec 14, 2025 | ⏰ 2PM (UTC+1) | 📍 Microsoft Teams Register: apexiumtechnologies.com/webinar #SecureCoding #CyberSecurity

🫶 Huge thanks to @shehackspurple for joining us at #BlackHat booth 3261 yesterday! She spoke with attendees about her essential book: Alice & Bob Learn #SecureCoding. Go Tanya 💯



I’m excited to share that I have officially passed the "Certified Security Code Review – Beginners (CSCRB)" certificate exam, issued by Red Team Leaders (RTL). #CyberSecurity #SecureCoding #CodeReview #AppSec #CSCRB #EthicalHacking #SecurityByDesign #OWASP #VAPT

El #OWASP Top 10 versión 2025 RC1 es una guía esencial para desarrolladores y profesionales de la #ciberseguridad. Resume el consenso global sobre las vulnerabilidades más críticas que deben abordarse para proteger los sistemas ante amenazas reales #SecureCoding #WebSecurity ↘️

We just launched the SecDim Patch Reward System. Review patches, give feedback, level up your skills, and earn bonus score. A new community-driven way to grow as a security-minded developer. Check it out: 👉 secdim.com/news/secdim-pa… #appsec #securecoding #programming

Insecure (de)serialization in Go (encoding/gob) by overwriting a field that cause encoder to confuse, use a lot of CPU and result in stack-overflow. If you develop a backend service, you must choose Go, when you care about security. #securecoding #challenge #go

Is "whitelisted IPs" just the bouncer keeping unwanted hosts out at DigitalOcean's nightclub? Source: devhubby.com/thread/how-to-… #SecureCoding #Deployment #TechTips #CodeNewbie #digitalocean #set

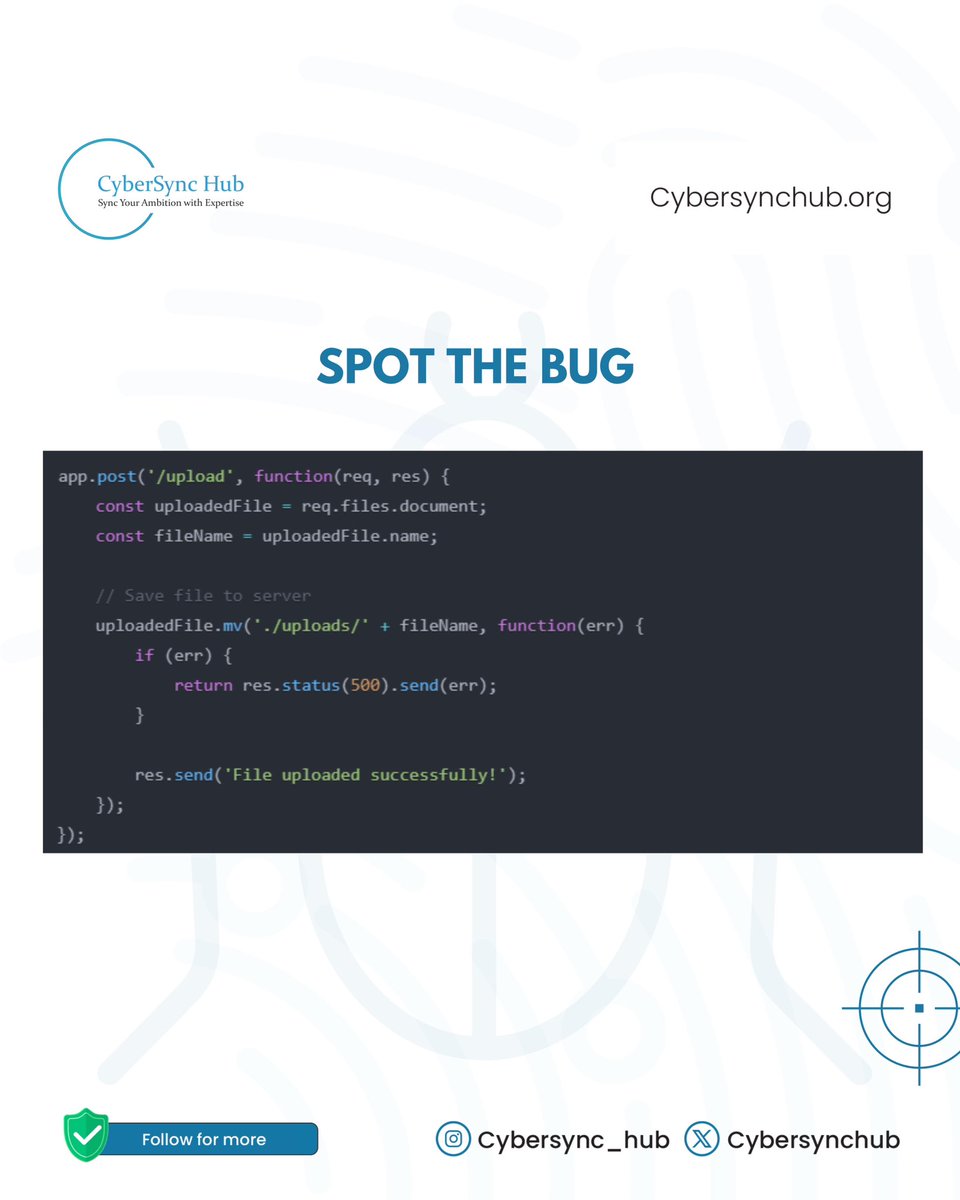
Can you find the security vulnerability in this code? Take a look and share your thoughts in the comments #DevSecOps #AppSec #SecureCoding #LearnCybersecurity #CyberSyncHub #TechLiteracy #CyberSecurity
4. Code Quality vs Code Speed Yes, AI helps write more code quickly, but not always better code. The study found AI-written code had a higher chance of being inefficient or insecure if used blindly. Review remains essential. #CleanCode #SecureCoding #AIDevTools

OWASP Secure Coding Practices Checklist👇 Link: 0xkayala.github.io/OWASP-Secure-C… #OWASPSecureCodingChecklist #OWASP #SecureCoding #Checklist #SecureCodingChecklist

Your backlog called. It said: “I'm full of stuff we could’ve caught upstream.” 🙄 Turns out, secure code training in the dev workflow prevents a lot of that. 👉 sans.org/u/1D14 #DevSecOps #SecureCoding


Most breaches still come down to bad code. 😬 This demo shows how teams are changing that—by giving devs hands-on practice in real tools like VS Code. Short, standards-aligned training. Real impact. ▶️ sans.org/u/1D14 #DevSecOps #SecureCoding

🛡️ New to API security? This beginner-friendly guide from @massimo_nardone walks you through securing #RESTful APIs with real-world examples—no fluff, just practical solutions. 📚 #APIDevelopment #SecureCoding #WebSecurity #Java #RESTAPI #DevTips 🔗 ow.ly/peez50Wf7Ts

One does not simply patch security after deployment. Know how to secure code from the start with this ebook! ➡️ store.expliot.io/products/the-e… #infosec #securecoding #cybersecurity

🛡️Strengthen your #SecureCoding skills! Join the Workshop on Secure Coding Practices by STPI Thiruvananthapuram & LDRA 📅28 Oct 2025 | 🕙10 AM–4 PM 📍Technopark,Thiruvananthapuram Learn #CERTC standards, secure design, and compliance tools. #STPI #CyberSecurity #NCSAM2025 #LDRA

🔐 Want to build secure Vue.js apps? In our latest blog, we’ve listed 5 essential security practices—from XSS prevention to safe data handling. 👇 🔗 resources.s4e.io/blog/5-essenti… #VueJS #CyberSecurity #SecureCoding #S4E #CTEM

Most breaches still come down to bad code. 😬 This demo shows how teams are changing that—by giving devs hands-on practice in real tools like VS Code. Short, standards-aligned training. Real impact. ▶️ sans.org/u/1D14 #DevSecOps #SecureCoding

☕️ Java cumple 30 años y yo fui testigo desde el “Hello, World!” del SDK 1.2 Fui dev, arquitecto y también instructor certificado por Sun y Oracle. Java no solo cambió el desarrollo: Cambió mi vida. Gracias por 30 años de café, comunidad y código. #Java30 #SrJava #SecureCoding

Shifting left means catching vulnerabilities early, right in your DevOps pipeline. Find out how it strengthens your pipeline: blog.checkpoint.com/infinity-globa… #DevSecOps #SecureCoding #cybersecurity

Datei-Uploads in #Java sicher machen? Schütze dich vor: - CWE-22 (Path Traversal) - CWE-377 (Temp File Risks) - CWE-778 (Insufficient Logging) Baue mit @SvenRuppert & #Vaadin sichere Datei-Apps – inkl. NIO, Logging & Security-Fokus: javapro.io/de/erstellen-e… #SecureCoding #CWE

Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 43.1K posts
- 2. Spurs 35.9K posts
- 3. Doug Dimmadome 7,881 posts
- 4. Michigan 121K posts
- 5. Marcus Smart 2,086 posts
- 6. Godzilla 19.2K posts
- 7. Wemby 5,245 posts
- 8. Sherrone Moore 62.1K posts
- 9. #AEWDynamite 26.1K posts
- 10. #Survivor49 4,978 posts
- 11. #PorVida 1,448 posts
- 12. Stephon Castle 3,418 posts
- 13. Erika 174K posts
- 14. Candace 216K posts
- 15. Gabe Vincent 1,121 posts
- 16. Jim Ward 8,318 posts
- 17. Thunder 31.6K posts
- 18. Vando 1,278 posts
- 19. Dolly Parton 1,828 posts
- 20. Kornet 4,891 posts
































