#securitybestpractices search results
Do you know the benefits of least privilege and segregation of duties? #Infosec #AccessManagement #SecurityBestPractices

Why did the CodeIgniter developer cross the road? To escape SQL injections on the other side!" Source: devhubby.com/thread/how-to-… #CodeIgniter #DatabaseSecurity #SecurityBestPractices #SecureWebDev #php #sqlinjection

Stay ahead of security threats! Implement baseline measures, engage employees, and conduct regular risk analyses. Create a safer environment and reduce incidents. #SecurityBestPractices #ProactiveSecurity

Strengthen external security and protect your innovation ➡️ Insights from Catherine Newcomb, Chris Blask, Kurt H., and Mitch Ashley. Tune In ‼️ tinyurl.com/3bvf4wss #CyberResilience #SecurityBestPractices
Say goodbye to hardcoding sensitive information in your Node.js applications! 🔒 With a .env file, you can manage your environment variables effortlessly. Our new guide walks you through... #NodeJS #WebDev #SecurityBestPractices buff.ly/4fTGsaI


If a PHP secure cookie falls in the code forest, does it make a sound?" 🌲🔒🍪 Source: devhubby.com/thread/how-to-… #HTTP #Coding #SecurityBestPractices #InfoSec #scripting #cookiesofinstagram

After the July CrowdStrike outage, executives met at a Microsoft-hosted summit to unite over #SecurityBestPractices. Our CEO @chiesennegs offered insights based on our commitment to data protection. Read more from @KyleAlspach at @CRN: bit.ly/3XZtkLq

Leaving an admin session open for 8 hours is like handing your keys to a stranger at lunch and hoping they return them. Set strict session timeouts for privileged accounts. Inactivity should never equal access. #AccessControl #SessionManagement #SecurityBestPractices
Security threats emerge from anywhere 🛡️Get the infosheet to protect your program from every angle bit.ly/3BlByow #CyberSecurity #DataProtection #SecurityBestPractices #EmergingThreats #AccessControl #24x7Monitoring

Strengthening Cyber Defense: Key Tips to Safeguard Your Endpoints 🔐 #cybersecurity #endpointsecurity #securitybestpractices

🔒 Managing risk posture is key to predicting, preventing, and responding to cyber threats. From asset discovery to automated tools, robust strategies build resilience. Discover best practices here: bit.ly/3BeMiFn #CyberSecurity #RiskManagement #SecurityBestPractices

🛡️ Multi-factor authentication (MFA) isn’t just a best practice — it’s a requirement for many compliance standards. Ensure your systems meet today’s security expectations with this MFA implementation guide. 📖 openv.pn/42JBIB1 #Compliance #MFA #SecurityBestPractices…

The UK government has shared a “world-first” AI #Cybersecurity code of practice to help guide businesses in building #AI systems per #SecurityBestPractices. @PhilMuncaster discusses the code & how #ISO42001 can help organisations achieve compliance: isms.online/information-se…

IDempotent requests & session timeouts can prevent session fixation attacks. Use secure session IDs, rotate them regularly, and limit user data to only what's necessary for each request #SessionManagement #SecurityBestPractices
Beyond code, this checklist covers scanning container images and monitoring collaboration platforms to prevent credential exposure in your full workflow. #Docker #SecurityBestPractices #DevOpsTips Read more 👉 lttr.ai/AkDU7 #iFeelTech

Strengthen your organization’s online security by implementing two-factor authentication—a simple yet powerful way to protect sensitive data. #Authentication #CyberDefense #SecurityBestPractices blog.short.io/how-to-enforce…
Why did the CodeIgniter developer cross the road? To escape SQL injections on the other side!" Source: devhubby.com/thread/how-to-… #CodeIgniter #DatabaseSecurity #SecurityBestPractices #SecureWebDev #php #sqlinjection

الحل؟ 👇 استخدم users مخصصين بحدود واضحة. #SecurityBestPractices
STOP reusing passwords! It's the easiest way for a hacker to get into multiple accounts. 🙅 To follow the rules (12+ characters, mix of cases/symbols), you absolutely need a Password Manager. #SecurityBestPractices #DigitalSafety #DataProtection #PrinceMonga #RiyantraX

@citytechsoft provides full #cscart implementation, upgrades, and maintenance services. We optimise #StoreSpeed, apply #SecurityBestPractices, manage server-side and client-side performance, and ensure extension compatibility. citytechcorp.com/contact-us/ #cscartdevelopment

If your 'default' namespace is running prod workloads, you don’t need hackers. You already hacked yourself. #Kubernetes #SecurityBestPractices #DevOps
1. Identity & Access Management (IAM) Common IAM Misconfigurations Over-permissioned accounts and unused credentials are prime targets. Regularly audit and refine permissions! #CloudSecurity #SecurityBestPractices
- Mitigation: Applying patches or updates from the affected software vendor; employing input validation and bounds checking in cookie parsing logic. #SecurityBestPractices
Prompt patching and strict control of local access remain critical defenses. 🏰 #SecurityBestPractices #StaySafe
Access logs provide insight into who is accessing data and can help detect and respond to unauthorized access attempts in real-time. #DataMonitoring #AccessLogs #SecurityBestPractices

Proper error handling prevents attackers from gaining valuable insight into the inner workings of your application. #ErrorHandling #AppSecurity #SecurityBestPractices

Selling your home or lost a remote? 🗑️ Learn to erase garage door opener settings, clear remotes & keypads fast! Ensure security. 📞 Call us: (203) 489-2043 🧡 24H Garage Doors 24hourgaragedoorsct.com #SecurityBestPractices #ResetSettings #HomeSaleTips #DigitalCleanse

Congrats on a great new book, @ScottBVS — this is a must-read for the seniors in your life! #securitybestpractices #CyberSecurity #onlinesecurity

Do you know the benefits of least privilege and segregation of duties? #Infosec #AccessManagement #SecurityBestPractices

Security threats emerge from anywhere 🛡️Get the infosheet to protect your program from every angle bit.ly/3BlByow #CyberSecurity #DataProtection #SecurityBestPractices #EmergingThreats #AccessControl #24x7Monitoring

If a PHP secure cookie falls in the code forest, does it make a sound?" 🌲🔒🍪 Source: devhubby.com/thread/how-to-… #HTTP #Coding #SecurityBestPractices #InfoSec #scripting #cookiesofinstagram

#Mainframe #Security Best Practices - 5 Steps to Securing Big Iron sync.st/2AD4lUX @IBMZ @IBM_IMS #SecurityBestPractices #Cybersecurity
Learn how #application #development is like building a house #securitybestpractices hubs.ly/H04fY3M0

Why did the CodeIgniter developer cross the road? To escape SQL injections on the other side!" Source: devhubby.com/thread/how-to-… #CodeIgniter #DatabaseSecurity #SecurityBestPractices #SecureWebDev #php #sqlinjection

Stay ahead of security threats! Implement baseline measures, engage employees, and conduct regular risk analyses. Create a safer environment and reduce incidents. #SecurityBestPractices #ProactiveSecurity

Azure VM Security Best Practices @mastersecjedi @azure #azuresecurity #azurevmsecurity #securitybestpractices #malware #cloudsecurity virtualizationhowto.com/2019/11/azure-…

After the July CrowdStrike outage, executives met at a Microsoft-hosted summit to unite over #SecurityBestPractices. Our CEO @chiesennegs offered insights based on our commitment to data protection. Read more from @KyleAlspach at @CRN: bit.ly/3XZtkLq

CloudTALK Ep 3: Is your team determining how to get security right on AWS? James Bowyer of Trek10 shares 5 key tips to establish a solid security approach. #securitybestpractices #cloudnative trek10.io/2oDBZox

In a recent @DarkReading report on modern #SecOps best practices, discover how BPM's Fred Rica encourages enterprise Chief Information Security Officers (CISOs) to start their SOC strategy thinking. Read more: bit.ly/494xTGZ. #SOCStrategy #SecurityBestPractices #CISO

“@pacohope: Can you put more #crypto wrongness on a web page? I don’t even https://t.co/JwIsX7oIIn” < wow! #SecurityBestPractices
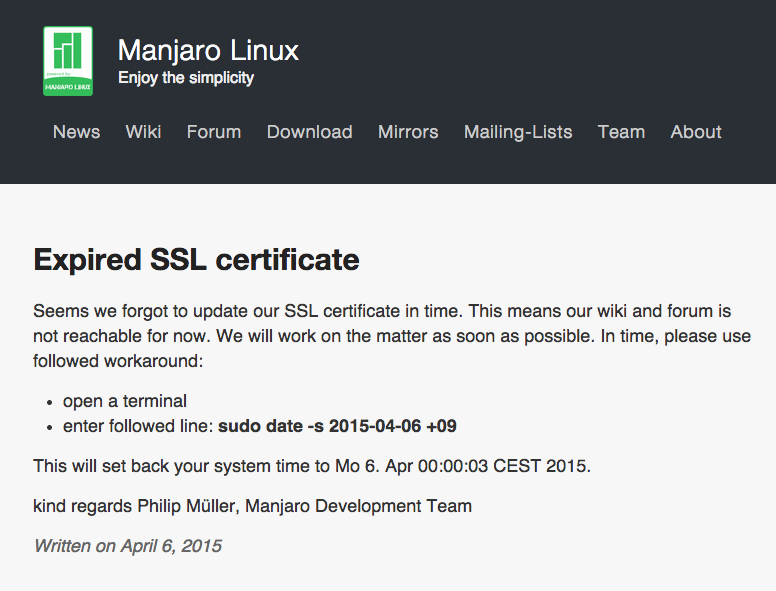
Learn how #application #development is like building a house from Onliner Steve Levinson #securitybestpractices hubs.ly/H05XZZY0

A question often on the minds of security experts: how do we create venue security in an unsecure world? @achitkara, along with input from global experts, shares best practices that help answer this complex question. okt.to/LdiVSq #SecurityBestPractices #FanSafety

Learn how #application #development is like building a house #securitybestpractices hubs.ly/H05rM-40

Say goodbye to hardcoding sensitive information in your Node.js applications! 🔒 With a .env file, you can manage your environment variables effortlessly. Our new guide walks you through... #NodeJS #WebDev #SecurityBestPractices buff.ly/4fTGsaI


API Security should be an integral part of your development process. Follow these best practices to ensure your API is secure from the start. aalpha.net/blog/api-secur… #apis #securitybestpractices #apidevelopment

Something went wrong.
Something went wrong.
United States Trends
- 1. Broncos 34K posts
- 2. Raiders 43.8K posts
- 3. Bo Nix 7,574 posts
- 4. #911onABC 22.5K posts
- 5. Geno 7,641 posts
- 6. AJ Cole N/A
- 7. GTA 6 83.5K posts
- 8. #WickedOneWonderfulNight 2,833 posts
- 9. Chip Kelly N/A
- 10. eddie 44K posts
- 11. #TNFonPrime 2,640 posts
- 12. #RaiderNation 2,692 posts
- 13. Crawshaw N/A
- 14. tim minear 2,665 posts
- 15. Cynthia 36.3K posts
- 16. Al Michaels N/A
- 17. #RHOC 1,978 posts
- 18. Ravi 15.4K posts
- 19. Jeanty 4,227 posts
- 20. Troy Franklin 1,586 posts








































