#securitybestpractices search results
Why did the CodeIgniter developer cross the road? To escape SQL injections on the other side!" Source: devhubby.com/thread/how-to-… #CodeIgniter #DatabaseSecurity #SecurityBestPractices #SecureWebDev #php #sqlinjection

Stay ahead of security threats! Implement baseline measures, engage employees, and conduct regular risk analyses. Create a safer environment and reduce incidents. #SecurityBestPractices #ProactiveSecurity

Do you know the benefits of least privilege and segregation of duties? #Infosec #AccessManagement #SecurityBestPractices

Strengthen external security and protect your innovation ➡️ Insights from Catherine Newcomb, Chris Blask, Kurt H., and Mitch Ashley. Tune In ‼️ tinyurl.com/3bvf4wss #CyberResilience #SecurityBestPractices
Leaving an admin session open for 8 hours is like handing your keys to a stranger at lunch and hoping they return them. Set strict session timeouts for privileged accounts. Inactivity should never equal access. #AccessControl #SessionManagement #SecurityBestPractices
Say goodbye to hardcoding sensitive information in your Node.js applications! 🔒 With a .env file, you can manage your environment variables effortlessly. Our new guide walks you through... #NodeJS #WebDev #SecurityBestPractices buff.ly/4fTGsaI


If a PHP secure cookie falls in the code forest, does it make a sound?" 🌲🔒🍪 Source: devhubby.com/thread/how-to-… #HTTP #Coding #SecurityBestPractices #InfoSec #scripting #cookiesofinstagram

Strengthening Cyber Defense: Key Tips to Safeguard Your Endpoints 🔐 #cybersecurity #endpointsecurity #securitybestpractices

Security threats emerge from anywhere 🛡️Get the infosheet to protect your program from every angle bit.ly/3BlByow #CyberSecurity #DataProtection #SecurityBestPractices #EmergingThreats #AccessControl #24x7Monitoring

After the July CrowdStrike outage, executives met at a Microsoft-hosted summit to unite over #SecurityBestPractices. Our CEO @chiesennegs offered insights based on our commitment to data protection. Read more from @KyleAlspach at @CRN: bit.ly/3XZtkLq

🔒 Managing risk posture is key to predicting, preventing, and responding to cyber threats. From asset discovery to automated tools, robust strategies build resilience. Discover best practices here: bit.ly/3BeMiFn #CyberSecurity #RiskManagement #SecurityBestPractices

In a recent @DarkReading report on modern #SecOps best practices, discover how BPM's Fred Rica encourages enterprise Chief Information Security Officers (CISOs) to start their SOC strategy thinking. Read more: bit.ly/494xTGZ. #SOCStrategy #SecurityBestPractices #CISO

Learn about the Dos and Don'ts of basic cybersecurity to keep yourself and your organization safe. zurl.co/nvel #cybersecurityawarenessmonth2023 #securitybestpractices #cybersecurity

Using Citrix's NetScaler Console tools to upgrade and apply configuration fixes systematically is advised. #NetScalerConsole #SecurityBestPractices
Discover the benefits of Resource Hardening & Operations in your DevOps based cloud deployments. Increase impact, achieve security excellence. #DevOps #Cloud #SecurityBestPractices valewood.org/topics/devops/…
Limit cookie IDs to session duration to minimize tracking and reduce your app's digital footprint. Use secure cookies with short expiration times for better user privacy. #DigitalPrivacy #SecurityBestPractices
#Day40 #WomeninSTEM #SecurityBestPractices #IncidentResponse #AccessControl #NetworkSecurity #DataProtection #BackupTesting #InfoSec #CyberSecurity #SecurityAwareness #100DaysChallenge #PatchManagement
🔒Question for today: Does your organization have a documented security policy? If not, that's step one to getting better security practices. @ireteeh @nyerenwam @itsacybersumtin #Day39 #WomeninSTEM #SecurityBestPractices #NIST #RiskAssessment #SecurityPolicy #100DaysChallenge
IDempotent requests & session timeouts can prevent session fixation attacks. Use secure session IDs, rotate them regularly, and limit user data to only what's necessary for each request #SessionManagement #SecurityBestPractices
Beyond code, this checklist covers scanning container images and monitoring collaboration platforms to prevent credential exposure in your full workflow. #Docker #SecurityBestPractices #DevOpsTips Read more 👉 lttr.ai/AkDU7 #iFeelTech

Strengthen your organization’s online security by implementing two-factor authentication—a simple yet powerful way to protect sensitive data. #Authentication #CyberDefense #SecurityBestPractices blog.short.io/how-to-enforce…
blog.short.io
How to Enforce 2FA for Team Members
Cybersecurity is a critical concern for organizations, especially with the increasing reliance on online platforms for collaboration and communication. One effective measure to enhance cybersecurity...
Why did the CodeIgniter developer cross the road? To escape SQL injections on the other side!" Source: devhubby.com/thread/how-to-… #CodeIgniter #DatabaseSecurity #SecurityBestPractices #SecureWebDev #php #sqlinjection

الحل؟ 👇 استخدم users مخصصين بحدود واضحة. #SecurityBestPractices
STOP reusing passwords! It's the easiest way for a hacker to get into multiple accounts. 🙅 To follow the rules (12+ characters, mix of cases/symbols), you absolutely need a Password Manager. #SecurityBestPractices #DigitalSafety #DataProtection #PrinceMonga #RiyantraX

Congrats on a great new book, @ScottBVS — this is a must-read for the seniors in your life! #securitybestpractices #CyberSecurity #onlinesecurity

Why did the CodeIgniter developer cross the road? To escape SQL injections on the other side!" Source: devhubby.com/thread/how-to-… #CodeIgniter #DatabaseSecurity #SecurityBestPractices #SecureWebDev #php #sqlinjection

Security threats emerge from anywhere 🛡️Get the infosheet to protect your program from every angle bit.ly/3BlByow #CyberSecurity #DataProtection #SecurityBestPractices #EmergingThreats #AccessControl #24x7Monitoring

If a PHP secure cookie falls in the code forest, does it make a sound?" 🌲🔒🍪 Source: devhubby.com/thread/how-to-… #HTTP #Coding #SecurityBestPractices #InfoSec #scripting #cookiesofinstagram

Do you know the benefits of least privilege and segregation of duties? #Infosec #AccessManagement #SecurityBestPractices

Stay ahead of security threats! Implement baseline measures, engage employees, and conduct regular risk analyses. Create a safer environment and reduce incidents. #SecurityBestPractices #ProactiveSecurity

Azure VM Security Best Practices @mastersecjedi @azure #azuresecurity #azurevmsecurity #securitybestpractices #malware #cloudsecurity virtualizationhowto.com/2019/11/azure-…

Learn how #application #development is like building a house #securitybestpractices hubs.ly/H04fY3M0

#Mainframe #Security Best Practices - 5 Steps to Securing Big Iron sync.st/2AD4lUX @IBMZ @IBM_IMS #SecurityBestPractices #Cybersecurity
After the July CrowdStrike outage, executives met at a Microsoft-hosted summit to unite over #SecurityBestPractices. Our CEO @chiesennegs offered insights based on our commitment to data protection. Read more from @KyleAlspach at @CRN: bit.ly/3XZtkLq

In a recent @DarkReading report on modern #SecOps best practices, discover how BPM's Fred Rica encourages enterprise Chief Information Security Officers (CISOs) to start their SOC strategy thinking. Read more: bit.ly/494xTGZ. #SOCStrategy #SecurityBestPractices #CISO

A question often on the minds of security experts: how do we create venue security in an unsecure world? @achitkara, along with input from global experts, shares best practices that help answer this complex question. okt.to/LdiVSq #SecurityBestPractices #FanSafety

“@pacohope: Can you put more #crypto wrongness on a web page? I don’t even https://t.co/JwIsX7oIIn” < wow! #SecurityBestPractices
CloudTALK Ep 3: Is your team determining how to get security right on AWS? James Bowyer of Trek10 shares 5 key tips to establish a solid security approach. #securitybestpractices #cloudnative trek10.io/2oDBZox

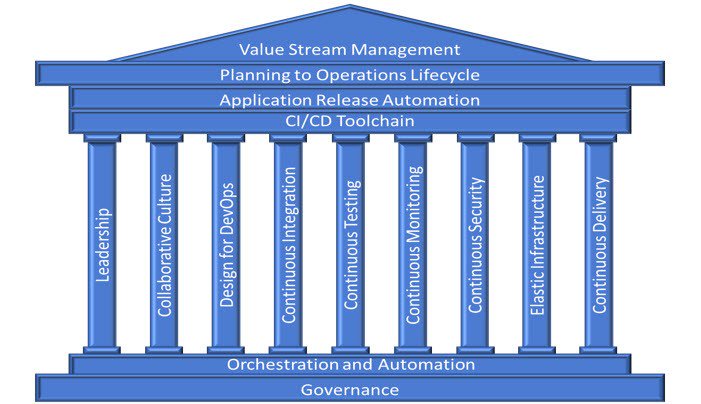
'9 Pillars of Continuous Security Best Practices' from Trace3's Marc Hornbeek & Imran Chaudhari #blog #securitybestpractices hubs.ly/H0gcfzZ0
Now that we’re set up to work remotely, check a few #securitybestpractices. Ensure your OS, office suite & security software are updated. If applicable, connect via your corp VPN. Change password of your ISP-provided Internet router (hint:Google), & use a home security router.

Say goodbye to hardcoding sensitive information in your Node.js applications! 🔒 With a .env file, you can manage your environment variables effortlessly. Our new guide walks you through... #NodeJS #WebDev #SecurityBestPractices buff.ly/4fTGsaI


Learn how #application #development is like building a house from Onliner Steve Levinson #securitybestpractices hubs.ly/H05XZZY0

Something went wrong.
Something went wrong.
United States Trends
- 1. GeForce Season 4,030 posts
- 2. Comey 186K posts
- 3. Everton 145K posts
- 4. St. John 8,564 posts
- 5. Mark Kelly 123K posts
- 6. Amorim 61.6K posts
- 7. Manchester United 84.1K posts
- 8. #sjubb N/A
- 9. Iowa State 3,501 posts
- 10. UCMJ 18.2K posts
- 11. Seton Hall 2,361 posts
- 12. Opus 4.5 9,201 posts
- 13. #LightningStrikes N/A
- 14. Pickford 11.3K posts
- 15. 49ers 19.5K posts
- 16. Genesis Mission 2,166 posts
- 17. Benedict Arnold 3,907 posts
- 18. Dealing 30.5K posts
- 19. Hegseth 48.4K posts
- 20. Lipsey N/A






































