#vulnerabilities resultados da pesquisa
⚠️ CVE-2025-7775 🖥️ Citrix NetScaler ADC/Gateway memory overflow 💬 allows unauthenticated remote code execution on vulnerable NetScaler appliances, enabling full system takeover and lateral movement 🔗 cve.mitre.org/cgi-bin/cvenam… #ransomNews #vulnerabilities #security #CVE

When #Vulnerabilities Pile Up - Finding the Real Value in #Security #Assessments Every year, a familiar pattern emerges. An organization invests in #penetration #testing. The report comes back. Dozens, sometimes hundreds, of findings. Fast forward 12 months... the same…

Recent updates to the Stakeholder-Specific #Vulnerability Categorization (SSVC) framework help different stakeholders to prioritize #vulnerabilities according to their distinct risk appetites. Our latest post details the updates #CyberSecurityAwareness - sei.cmu.edu/blog/whats-new…

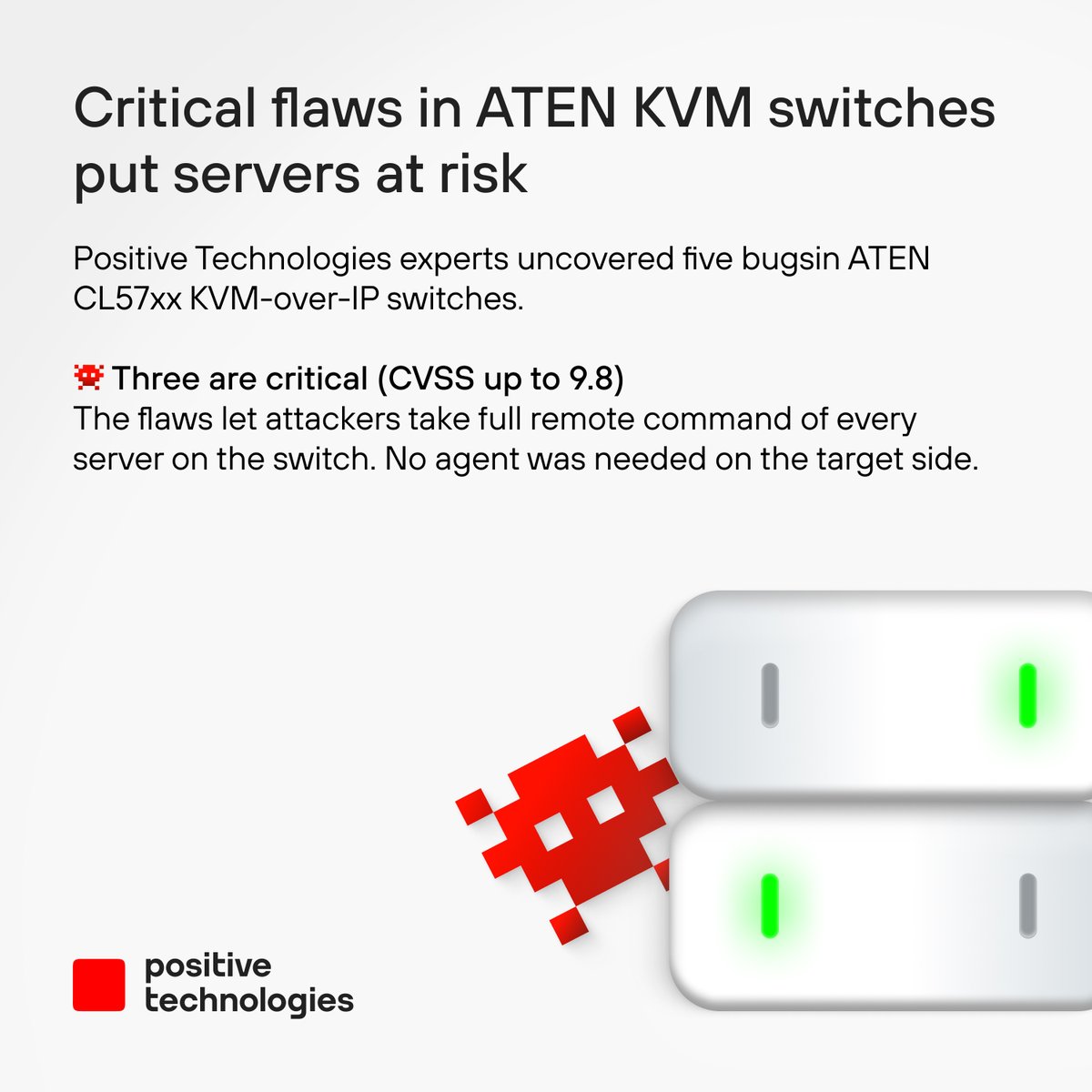
Critical flaws in ATEN KVM switches gave attackers full control remotely. Thanks to the team for the catch and @Sc4rlet9 especially! Patch now and stay protected. #Cybersecurity #Vulnerabilities #PositiveTechnologies



⚠️ Atenție! Mai multe vulnerabilități critice afectează Google Chrome și alte browsere bazate pe Chromium. 👉 Citește avertizarea completă pe site-ul DNSC: dnsc.ro/citeste/averti… #DNSC #CyberSecurity #Vulnerabilities #UpdateNow #SigurantaOnline

When you treat vulnerabilities as clues instead of chores, you uncover threats, fix blind spots and finally make your security program work smarter. Get the full story by #FoundryExpert Contributor, Tom Poperszky spr.ly/601079mSi #SecuritySoftware #Vulnerabilities

#AI can detect malicious chip #vulnerabilities with a 97% success rate - but will that be enough? - buff.ly/dHxXrcU #ML #hardwarevulnerabilities #semiconductors #security #supplychain

XXE #vulnerabilities happen when a misconfigured XML parser processes an XML input containing external entities. This exposure allows attackers to read local files or conduct SSRF attacks. Disable external entity processing in XML parsers and consider using JSON-based formats…

🚨 We uncovered #security #vulnerabilities in #Windows graphics. #CVE-2025-30388 and CVE-2025-53766 are #BufferOverflows enabling #RemoteCodeExecution. CVE-2025-47984 leaks memory over the network due to an incomplete fix. 👇research.checkpoint.com/2025/drawn-to-…
Critical #Android #vulnerabilities patched - update as soon as you can: malwarebytes.com/blog/news/2025…

#Cyberattacks on manufacturing aren't just IT issues. They stop production, they threaten supply chains and they exploit wireless and IoT #vulnerabilities. Risk-based security, network segmentation, and strict access controls are now critical.❗mou.sr/3LGw0JU

A new, weaponized exploit for critical #SAP #vulnerabilities CVE-2025-31324 and CVE-2025-42999 is now public. If your systems are unpatched, they're at high risk. Act now: apply SAP security notes 3594142 and 3604119. Get the full story ➡️ bit.ly/45R1ogq #cybersecurity



The #Swagger You Forgot Is the Risk You Inherited Sometimes the biggest #vulnerabilities aren’t hidden behind layers of #obfuscation, they’re sitting in plain sight, waiting for someone curious enough to look. That’s exactly what happened during a recent grey-box web application…

#Kubernetes: Newly disclosed #vulnerabilities in the #runC container runtime used in #Docker & Kubernetes (CVE-2025-31133, CVE-2025-52565, CVE-2025-52881) could be exploited to bypass isolation restrictions & get access to the host system (escape): #k8s bleepingcomputer.com/news/security/…
From 2022 through 2024, APT28 exploited #vulnerabilities to remotely and wirelessly access data from a targeted company network. Our latest post presents vulnerabilities, exploitations, weaknesses, and how they might impact the wireless system - sei.cmu.edu/blog/radio-fre…
YOU help keep this movement alive! Thanks for sticking with us while we pursue answers. Full video: youtu.be/3XERg8QilFA #Cybersecurity #Vulnerabilities #Accountability #Trustbutverify #Proofisinthepaper #HandCountedPaperBallots #ItsUpToUs #VerifyTheVote

youtube.com
YouTube
Pennsylvania Lawsuit Filed | Election Truth Alliance
BitsLab’s AI Audit Agent Discovers Multiple Vulnerabilities in Story Protocol’s Smart Contracts @0xbitslab #AI #Vulnerabilities #Web3Security chainwire.org/2025/11/04/bit…
⚠️ Ivanti Endpoint Manager Vulnerabilities Let Attackers Write Arbitrary Files to Disk Read more: cybersecuritynews.com/ivanti-endpoin… #cybersecuritynews #vulnerabilities #ivanti

✅ #PrecisionMedicine is IMPORTANT in #Lupus, but PERSONALIZED medicine, - taking into account the personal socio-economic determinants & patient #vulnerabilities-, is even MORE IMPORTANT. Check our latest PAPER with @G_O_Daniel & Zoe from @LupusEurope at: sciencedirect.com/science/articl…

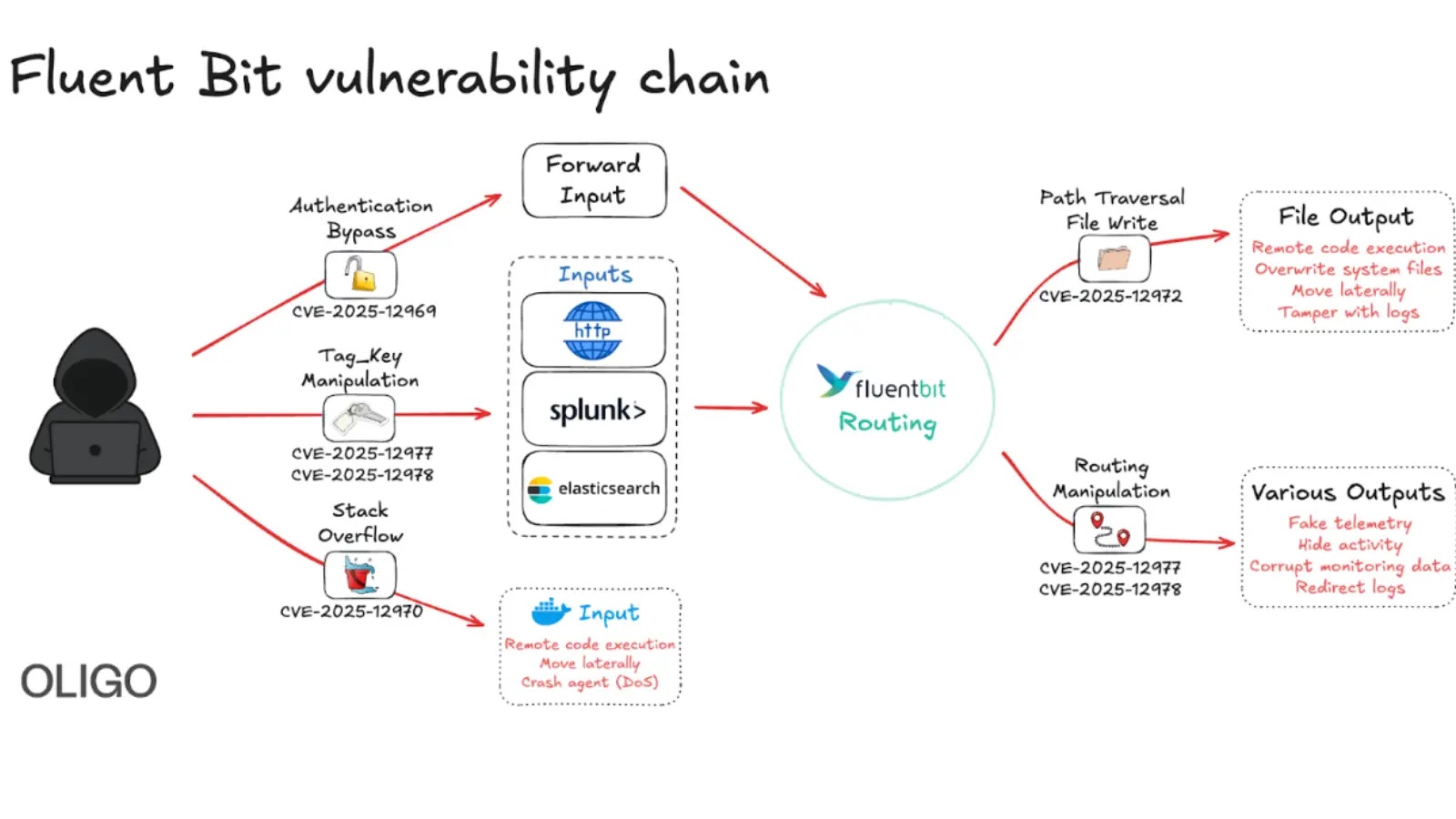
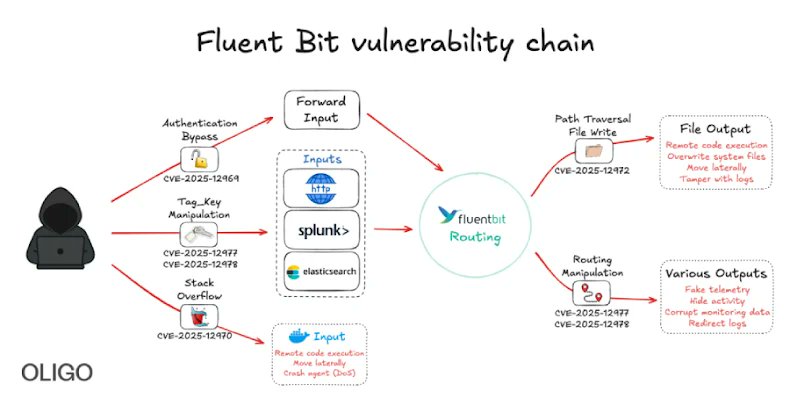
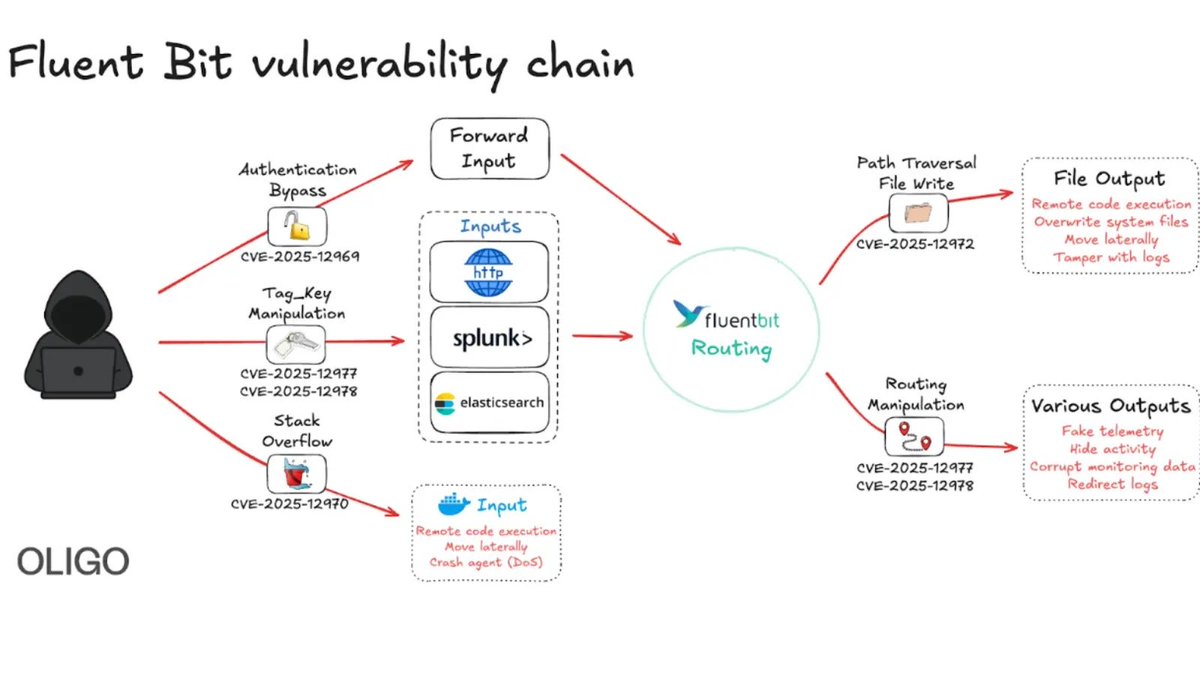
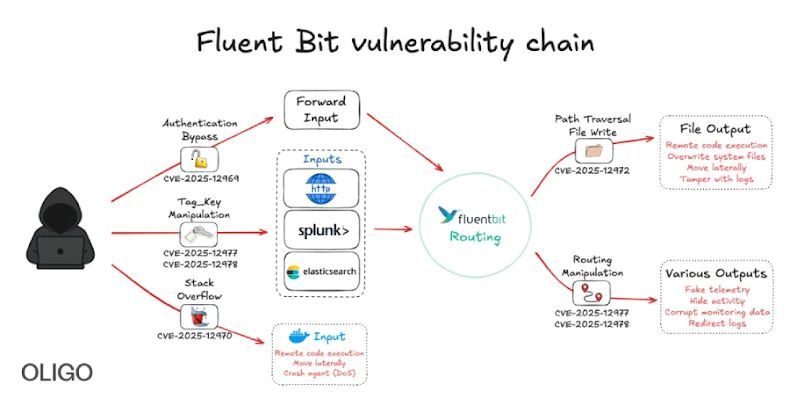
Critical Fluent Bit Vulnerabilities Allow Remote Attacks on Cloud Environments gbhackers.com/fluent-bit-vul… #CyberSecurity #Vulnerabilities #CSCIS
ثغرات خطيرة في Fluent Bit قد تمكّن المهاجمين من السيطرة على خدمات سحابية تستخدمه في مراقبة السجلات. الهجوم يعتمد على تنفيذ أوامر عن بُعد. تحديث عاجل مطلوب لوقف الاستغلال النشط. #FluentBit #CloudSecurity #Vulnerabilities #DevOps #CyberThreats
#WhatsApp closes #security_gap #Vulnerabilities that let researchers collect data on 3.5B accounts ift.tt/Va8M6B3

YOU help keep this movement alive! Thanks for sticking with us while we pursue answers. Full video: youtu.be/3XERg8QilFA #Cybersecurity #Vulnerabilities #Accountability #Trustbutverify #Proofisinthepaper #HandCountedPaperBallots #ItsUpToUs #VerifyTheVote

youtube.com
YouTube
Pennsylvania Lawsuit Filed | Election Truth Alliance
Meltdown and Spectre. Vulnerabilities in modern computers leak passwords and sensitive data meltdownattack.com #meltdown #security #vulnerabilities
DeepSeek-R1's code vulnerabilities spike with politically sensitive prompts, raising concerns about AI reliability in coding. thedailytechfeed.com/deepseek-r1-ai… #AI #Security #Vulnerabilities #Coding #Technology #Innovation #Programming #Software #Development #Automation #Reliability…

🔒 Critical vulnerabilities in Fluent Bit could compromise cloud infrastructures! Attackers can perform RCE, bypass auth, and cause DoS. Stay vigilant! #Cybersecurity #FluentBit #Vulnerabilities 🔗 Source: thehackernews.com/2025/11/new-fl…
NVIDIA Isaac-GR00T gets critical security patches for two high-severity bugs in the robotics stack. If your bots run Isaac, patch time before they get creative. #vulnerabilities threatcluster.io/cluster/nvidia…
New #Fluent_Bit #Vulnerabilities #Flaws Expose #Cloud to #RCE and Stealthy Infrastructure #Intrusions ift.tt/QUWvlzs
DeepSeek-R1's coding vulnerabilities spike with politically sensitive prompts, raising concerns about AI reliability in sensitive contexts. Link: thedailytechfeed.com/deepseek-r1-ai… #AI #Security #Vulnerabilities #Reliability #Technology #Coding #Sensitive #Cyber #Risks #Study #Prompts…

Cooper Steel Fabricators Data #Breach: 330 GB of Sensitive Project Data Up for Sale #cybersecurity #vulnerabilities bit.ly/3XRIeSM
Learn how to uncover high-impact #vulnerabilities already lurking in your AI-driven systems before they lead to #dataleaks in our training at @BlackHatEvents Europe. 🔗Reserve your seat today: blackhat.com/eu-25/training… #LLMSecurity #AppSec #AIsecurity #BHEU
Hackers target old, unpatched, and misconfigured systems every day. Discover the most exploited vulnerabilities in the wild and how to protect your organization. redsecuretech.co.uk/blog/post/top-… #CyberSecurity #Vulnerabilities #RCE #SQLInjection #Infosec #ThreatIntel #CyberAwareness

Pentesting 101 📚 Do you want to gain the fundamental skills to conduct a #penetrationtesting engagement but don't know where to start? This free Module is the answer for all the beginners out there! Explore practical techniques for finding #vulnerabilities and exploiting them…

Multiple #critical #vulnerabilities have been identified in #VMware products, with evidence of active exploitation by #ransomware groups. Organizations using these products should urgently apply the recommended patches to mitigate potential risks. 1. CISA Adds Four Known…

⚠️ CVE-2025-3746 🖥️ WordPress OTP-less one tap signin plugin 💬 vulnerable to privilege escalation via account takeover 🔗 cve.mitre.org/cgi-bin/cvenam… #ransomNews #vulnerabilities #security #CVE

Vulnerability Management Challenges in #IoT & #OT Environments - buff.ly/Jy2Wm8I #vulnerabilities #security #OTsecurity #infosec #IIoT #edge #edgecomputing
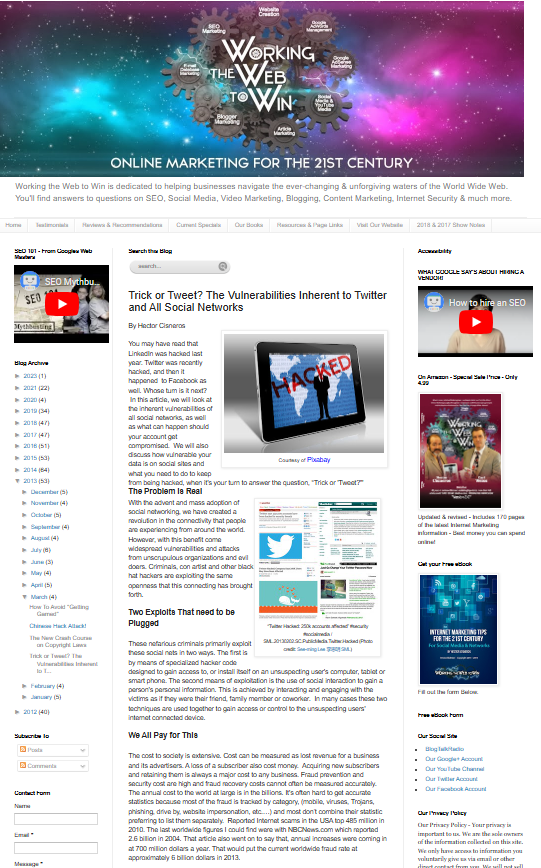
Did you know that all Social Media sites come with psychosocial #vulnerabilities that antimalware can protect you from! Check out: Trick or Tweet? The Vulnerabilities Inherent to Twitter and All Social Networks - ow.ly/PNmw50X2xoF
🗨️ “As we move into 2025, security teams face a growing wave of AI-powered threats, social engineering attacks, identity exploitation, and supply chain #vulnerabilities”. In their session 'Future‑Proofing Against Cybercrime: The Six Trends Every Organisation Must Know',…

✅ Very happy to report that we have completed STEP 2 of #LUPUSALERT, asking a large international panel to triage & prioritize #lupus #vulnerabilities suggested during step 1, for inclusion in the final screening questionnaire 👍 Thanks to you all for your contributions 👏

Recent updates to the Stakeholder-Specific #Vulnerability Categorization (SSVC) framework help different stakeholders to prioritize #vulnerabilities according to their distinct risk appetites. Our latest post details the updates #CyberSecurityAwareness - sei.cmu.edu/blog/whats-new…

#Nvidia #Triton #Vulnerabilities Pose Big Risk to #AI Models - ift.tt/9QulTS4 #genAI #IT #security #infosec #GPUs #AIsecurity #ML

How to #Prevent #Vulnerabilities Before They Show Up in a #Pentest It is often asked during pentest debriefs: "How could we have prevented these vulnerabilities before the test?" The reality is, by the time a vulnerability is discovered during a penetration test, it might…

When #Vulnerabilities Pile Up - Finding the Real Value in #Security #Assessments Every year, a familiar pattern emerges. An organization invests in #penetration #testing. The report comes back. Dozens, sometimes hundreds, of findings. Fast forward 12 months... the same…

Critical #Android #vulnerabilities patched - update as soon as you can: malwarebytes.com/blog/news/2025…

⚠️ CVE-2025-7775 🖥️ Citrix NetScaler ADC/Gateway memory overflow 💬 allows unauthenticated remote code execution on vulnerable NetScaler appliances, enabling full system takeover and lateral movement 🔗 cve.mitre.org/cgi-bin/cvenam… #ransomNews #vulnerabilities #security #CVE

Just picked up my holiday photos! 50% landscapes, 50% Grype being @GrypeProject 👽📷 #vulnerabilities #security #family


Critical flaws in ATEN KVM switches gave attackers full control remotely. Thanks to the team for the catch and @Sc4rlet9 especially! Patch now and stay protected. #Cybersecurity #Vulnerabilities #PositiveTechnologies




✅ #PrecisionMedicine is IMPORTANT in #Lupus, but PERSONALIZED medicine, - taking into account the personal socio-economic determinants & patient #vulnerabilities-, is even MORE IMPORTANT. Check our latest PAPER with @G_O_Daniel & Zoe from @LupusEurope at: sciencedirect.com/science/articl…

A new, weaponized exploit for critical #SAP #vulnerabilities CVE-2025-31324 and CVE-2025-42999 is now public. If your systems are unpatched, they're at high risk. Act now: apply SAP security notes 3594142 and 3604119. Get the full story ➡️ bit.ly/45R1ogq #cybersecurity



Something went wrong.
Something went wrong.
United States Trends
- 1. Luka 54.1K posts
- 2. Lakers 40.7K posts
- 3. #DWTS 91.8K posts
- 4. Clippers 15.6K posts
- 5. #LakeShow 3,215 posts
- 6. Robert 130K posts
- 7. Kris Dunn 2,106 posts
- 8. Kawhi 5,388 posts
- 9. Jaxson Hayes 1,946 posts
- 10. Reaves 8,790 posts
- 11. Ty Lue 1,384 posts
- 12. Alix 14.8K posts
- 13. Elaine 45.5K posts
- 14. Jordan 118K posts
- 15. Zubac 2,188 posts
- 16. Collar 39.2K posts
- 17. Dylan 35K posts
- 18. NORMANI 5,936 posts
- 19. Colorado State 2,299 posts
- 20. Godzilla 36.1K posts