#vulnerabilities 검색 결과
When #Vulnerabilities Pile Up - Finding the Real Value in #Security #Assessments Every year, a familiar pattern emerges. An organization invests in #penetration #testing. The report comes back. Dozens, sometimes hundreds, of findings. Fast forward 12 months... the same…

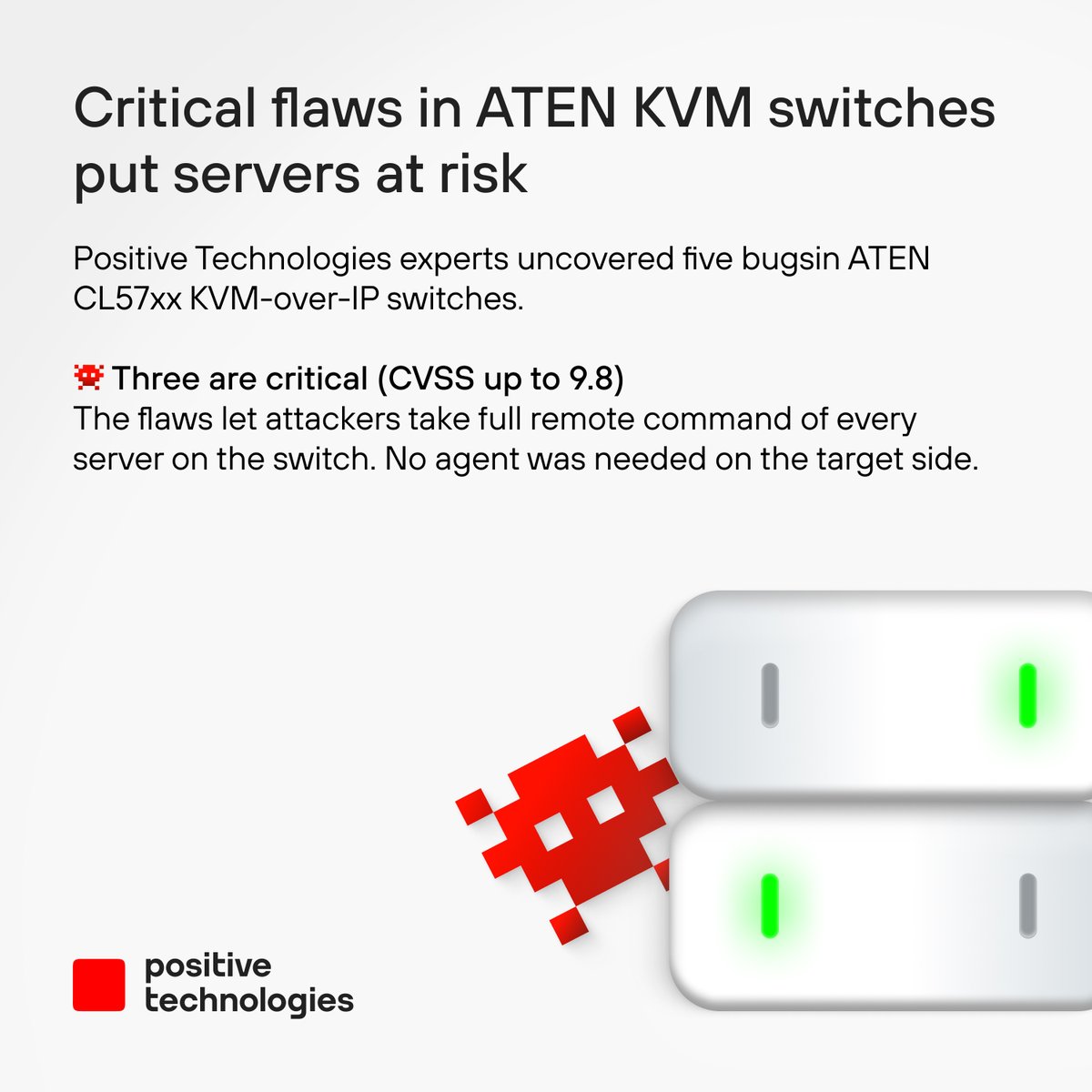
Critical flaws in ATEN KVM switches gave attackers full control remotely. Thanks to the team for the catch and @Sc4rlet9 especially! Patch now and stay protected. #Cybersecurity #Vulnerabilities #PositiveTechnologies



Rotem & Phillip from @CyberArk share several #vulnerabilities they discovered while tricking Microsft EPM #nullconBerlin2025 #nullcon



Critical #Android #vulnerabilities patched - update as soon as you can: malwarebytes.com/blog/news/2025…

🚨 Unit 515 uncovers new CVEs🚨 OPSWAT’s #Unit515 has identified multiple #vulnerabilities affecting Schneider Electric’s Modicon PLCs, including the M241 and other models commonly used in industrial environments. CVE-2025-2875 was disclosed in May, followed by six additional…
2025: A pivotal year for #SAPSecurity! We've analyzed critical #SAP #vulnerabilities from H1, uncovering dangers like #InsecureDeserialization & active exploitation. Get the updates below. 👀⬇️ Full analysis here 📖: bit.ly/4m7TyEx #Cybersecurity #ThreatIntelligence
CISA Adds Erlang SSH and Roundcube Flaws to Known Exploited Vulnerabilities Catalog dlvr.it/TLsYSL #Cybersecurity #Vulnerabilities #CISA #Erlang #SSH

Popular #AI Systems Still a Work-in-Progress for #Security - ift.tt/MRcrPH1 #vulnerabilities #cybersecurity #infosec #GenaI #LLMs

Vulnerability Management Challenges in #IoT & #OT Environments - buff.ly/Jy2Wm8I #vulnerabilities #security #OTsecurity #infosec #IIoT #edge #edgecomputing
A new, weaponized exploit for critical #SAP #vulnerabilities CVE-2025-31324 and CVE-2025-42999 is now public. If your systems are unpatched, they're at high risk. Act now: apply SAP security notes 3594142 and 3604119. Get the full story ➡️ bit.ly/45R1ogq #cybersecurity



🚨 @CISAgov adds 3 actively exploited flaws to its KEV Catalog: • CVE-2013-3893 – Internet Explorer • CVE-2007-0671 – Excel • CVE-2025-8088 – WinRAR Legacy ≠ Safe. Patch it or risk compromise. Are these still in your environment? #CISA #KEV #Vulnerabilities…

✅ #PrecisionMedicine is IMPORTANT in #Lupus, but PERSONALIZED medicine, - taking into account the personal socio-economic determinants & patient #vulnerabilities-, is even MORE IMPORTANT. Check our latest PAPER with @G_O_Daniel & Zoe from @LupusEurope at: sciencedirect.com/science/articl…

Cyber risk management is not an option; it's a necessity. Our service helps your SMB proactively address vulnerabilities and protect your assets. #Necessity #Vulnerabilities ? vciso.co
vciso.co
Expert Virtual CISO Services for Business Security Management | vCiso
vciso offers cost-effective virtual and fractional CISO services, ensuring your organization's information security through ISO 27001 and SOC 2 compliance, incident management, and strategic leader...
💰The @kamino & @immunefi bug bounty program offers up to $1.5 million for #critical #vulnerabilities in #SmartContracts, setting a Solana record💰 Read more👇 #Kamino #ImmuneFi #Solana #Web3Community #DeFi #BOUNTYHUNTERS #BountyProgram #CryptoNews #Bugs timescrypto.com/cryptonews/tec…
Currently verified, and at over 15,000 signatures. #genetic #vulnerabilities #boys #men #teens #kids #male #lungs #pulmonary #heart #law #legal #FinalysLaw #SaveBoys #SaveMen #medicine #health #vulnerable
I just signed the petition “Enact Finlay’s Law to Protect Ontario’s Children in Emergency Rooms” and you could help by adding your name too. Our goal is to reach 5,000 signatures and we need more support. You can read more and sign the petition here: change.org/p/enact-finlay…
Vulnerability Management Challenges in #IoT & #OT Environments - buff.ly/Jy2Wm8I #vulnerabilities #security #OTsecurity #infosec #IIoT #edge #edgecomputing
Just picked up my holiday photos! 50% landscapes, 50% Grype being @GrypeProject 👽📷 #vulnerabilities #security #family


‘Cyber threats can delay or derail M&A deals, risking value & reputation,’ says Nikhil Agarwal. Proactive cybersecurity #DueDiligence is critical to detect #vulnerabilities & ensure smooth integration. Read the whitepaper to know more: infy.com/42l4eIp #FortifyCyber…

This dangerous new botnet is shooting off attacks across the world faster than can be tracked - here's what we know about RondoDox #Botnet #Vulnerabilities #FirmwareUpdate #InternetConnectedDevices #LoginCredentials #Infrastructure #DDoS techradar.com/pro/security/t…
Recent #vulnerabilities due to design flaws and incorrect deployments have made APIs a target for attacks. McKinley Sconiers-Hasan, a solutions engineer in our #CERT division, discusses #CybersecurityAwarenessMonth - youtube.com/watch?v=IXuxD_…

youtube.com
YouTube
API Security: An Emerging Concern in Zero Trust Applications
Apple now offers $2 million for zero-click #RCE #vulnerabilities bleepingcomputer.com/news/security/…
Google says Cl0p hackers who exploited vulnerabilities in Oracle's E-Business Suite have stolen data from "dozens" of organizations since at least July 10 (Zack Whittaker/TechCrunch) buff.ly/NqgLh1j #hackers #Google #vulnerabilities
Pentesting 101 📚 Do you want to gain the fundamental skills to conduct a #penetrationtesting engagement but don't know where to start? This free Module is the answer for all the beginners out there! Explore practical techniques for finding #vulnerabilities and exploiting them…

Multiple #critical #vulnerabilities have been identified in #VMware products, with evidence of active exploitation by #ransomware groups. Organizations using these products should urgently apply the recommended patches to mitigate potential risks. 1. CISA Adds Four Known…


🚨 Critical AirBorne vulnerabilities expose Apple and third-party devices to Zero-Click attacks Researchers have identified a series of #vulnerabilities, collectively termed #AirBorne, affecting Apple's #AirPlay protocol. These flaws could allow attackers on the same Wi-Fi…

⚠️ CVE-2025-3746 🖥️ WordPress OTP-less one tap signin plugin 💬 vulnerable to privilege escalation via account takeover 🔗 cve.mitre.org/cgi-bin/cvenam… #ransomNews #vulnerabilities #security #CVE

Did you know that all Social Media sites come with psychosocial #vulnerabilities that antimalware can protect you from! Check out: Trick or Tweet? The Vulnerabilities Inherent to Twitter and All Social Networks - ow.ly/9A6W50WOoNW

Rotem & Phillip from @CyberArk share several #vulnerabilities they discovered while tricking Microsft EPM #nullconBerlin2025 #nullcon



🗨️ “As we move into 2025, security teams face a growing wave of AI-powered threats, social engineering attacks, identity exploitation, and supply chain #vulnerabilities”. In their session 'Future‑Proofing Against Cybercrime: The Six Trends Every Organisation Must Know',…

✅ Very happy to report that we have completed STEP 2 of #LUPUSALERT, asking a large international panel to triage & prioritize #lupus #vulnerabilities suggested during step 1, for inclusion in the final screening questionnaire 👍 Thanks to you all for your contributions 👏

Do you know the #vulnerabilities that are inherent in all #social media networks? Read this and you will - Trick or Tweet? The Vulnerabilities Inherent to Twitter and All Social Networks - ow.ly/jWST50VwXrp

Vulnerability Management Challenges in #IoT & #OT Environments - buff.ly/Jy2Wm8I #vulnerabilities #security #OTsecurity #infosec #IIoT #edge #edgecomputing

Critical flaws in ATEN KVM switches gave attackers full control remotely. Thanks to the team for the catch and @Sc4rlet9 especially! Patch now and stay protected. #Cybersecurity #Vulnerabilities #PositiveTechnologies




When #Vulnerabilities Pile Up - Finding the Real Value in #Security #Assessments Every year, a familiar pattern emerges. An organization invests in #penetration #testing. The report comes back. Dozens, sometimes hundreds, of findings. Fast forward 12 months... the same…

Popular #AI Systems Still a Work-in-Progress for #Security - ift.tt/MRcrPH1 #vulnerabilities #cybersecurity #infosec #GenaI #LLMs

Just picked up my holiday photos! 50% landscapes, 50% Grype being @GrypeProject 👽📷 #vulnerabilities #security #family


Do you know the #vulnerabilities that are inherent in all #social media networks? Read this and you will - Trick or Tweet? The Vulnerabilities Inherent to Twitter and All Social Networks - ow.ly/aanM50VZn3K

Something went wrong.
Something went wrong.
United States Trends
- 1. Baker 41.8K posts
- 2. 49ers 39.1K posts
- 3. Ty Dillon N/A
- 4. Packers 35.1K posts
- 5. Bucs 13.1K posts
- 6. Lions 44.5K posts
- 7. #TNABoundForGlory 12.9K posts
- 8. #BNBdip N/A
- 9. Fred Warner 14.8K posts
- 10. Flacco 13K posts
- 11. Cowboys 76.7K posts
- 12. Niners 6,174 posts
- 13. Byron 6,202 posts
- 14. George Springer 2,049 posts
- 15. #OnePride 2,134 posts
- 16. #FTTB 4,702 posts
- 17. #NASCAR 4,453 posts
- 18. Zac Taylor 3,467 posts
- 19. Cam Ward 3,237 posts
- 20. Egbuka 7,161 posts