#adversarialattacks ผลการค้นหา
The Hidden Risk Behind 250 Documents and AI Corruption cysecurity.news/2025/10/the-hi… #Adversarialattacks #AIgovernance #AIRiskManagement

How To Secure Generative AI Systems Against Emerging Threats #GenerativeAI #AdversarialAttacks #AI #DataPoisoning #WAF #WebApplicationFirewall #CyberSecurityNews #ProphazeWAF prophaze.com/kb-articles/ho…

Apparently, our state-of-the-art vision models can still be fooled by a few well-placed pixels. Great news for security researchers, terrible news for self-driving cars trying to tell a stop sign from a sticker. #AI #AdversarialAttacks

Check out one of the latest topical papers from JPhys Complexity, exploring crossover phenomenon in adversarial attacks on voter model #CrossoverPhenomenon #AdversarialAttacks Read more here 👉 ow.ly/HNW950PUZrZ

How Image Resizing Could Expose AI Systems to Attacks cysecurity.news/2025/08/how-im… #Adversarialattacks #AItools #algorithms

🌟 @zicokolter revealed key vulnerabilities in #LLMs to #AdversarialAttacks. 🛡️Including a live demo, his insights underscore the urgent need for robust #AISafety measures. A vital call to action for AI security! 🤯🔐 #AIAlignmentWorkshop

Discover Transferability of Adversarial Attacks! #adversarialattacks #adversarialexamples #AIattacks #AIsecurity #deeplearning #foolingAImodels #MachineLearning #modelvulnerability #transferability aicompetence.org/adversarial-at…

Adversarial attacks pose a serious threat to AI systems. What innovative methods or techniques do you believe are crucial for safeguarding AI models against these attacks? 💡 Share your thoughts! #AIsecurity #AdversarialAttacks #AI #Security

This #AIPaper Propsoes an #AIFramework to Prevent #AdversarialAttacks on #Mobile #VehicleToMicrogrid Services #V2M #Data #energy #AI #ArtificialIntelligence #Tech #Technology #GenerativeAdversarialNetworks #GANs buff.ly/3BSju5u

Are Your #AI Conversations Safe? Exploring the Depths of #AdversarialAttacks on #MachineLearning Models #ArtificialIntelligence #Algorithm #ML #data #cybersecurity #researchers buff.ly/3uOLvYp

🚨 New research alert! AttackBench introduces a fair comparison benchmark for gradient-based attacks, addressing limitations in current evaluation methods. 📜Paper: arxiv.org/pdf/2404.19460 🏆LeaderBoard: attackbench.github.io #MLSecurity #AdversarialAttacks #AI #adversarial

#AdversarialAttacks on #AImodels are rising: what should you do now? #AI #ArtificialIntelligence #ML #MachineLearning #Tech #Technology #CyberSecurity #CyberCriminals #CyberAttacks buff.ly/3ZyVuOr

Adversarial Attacks in Graph Neural Networks #adversarialattacks #machinelearning #CyberSecurity Learn how to hack machine learning models and how to secure them! medium.com/@ronantech/adv…
blog.gopenai.com
Adversarial Machine Learning in Graph Neural Networks
Hacking Machine Learning Models
AI Agents and the Rise of the One-Person Unicorn cysecurity.news/2025/08/ai-age… #Accesscontrol #Adversarialattacks #agenticAI

Adversarial attacks: a hidden threat in AI! 🚨 Discover how these stealthy manipulations can fool even the smartest algorithms and what it means for the future of AI security. 🛡️ #AI #AdversarialAttacks #Cybersecurity
#NewArticle Evaluating the Vulnerability of #YOLOv5 to #AdversarialAttacks for Enhanced Cybersecurity in #MASS mdpi.com/2271690 #mdpijmse via @JMSE_MDPI @MDPIEngineering #perturbedimage #objectclassification

AI Jailbreak Threat: Vulnerabilities in Large Language Models Exposed #adversarialAImodels #adversarialattacks #AI #AIsystems #API #artificialintelligence #biases #Cybersecurity #GPT4 #jailbreakprompts #Largelanguagemodels #llm #machinelearning multiplatform.ai/ai-jailbreak-t…

🔔 Welcome to read Editor's Choice Articles in the Q1 of 2024: 📌Title: A Holistic Review of #MachineLearning Adversarial Attacks in #IoT Networks 🔗mdpi.com/1999-5903/16/1… #adversarialattacks #deeplearning #intrusiondetectionsystem #malwaredetectionsystem @ComSciMath_Mdpi
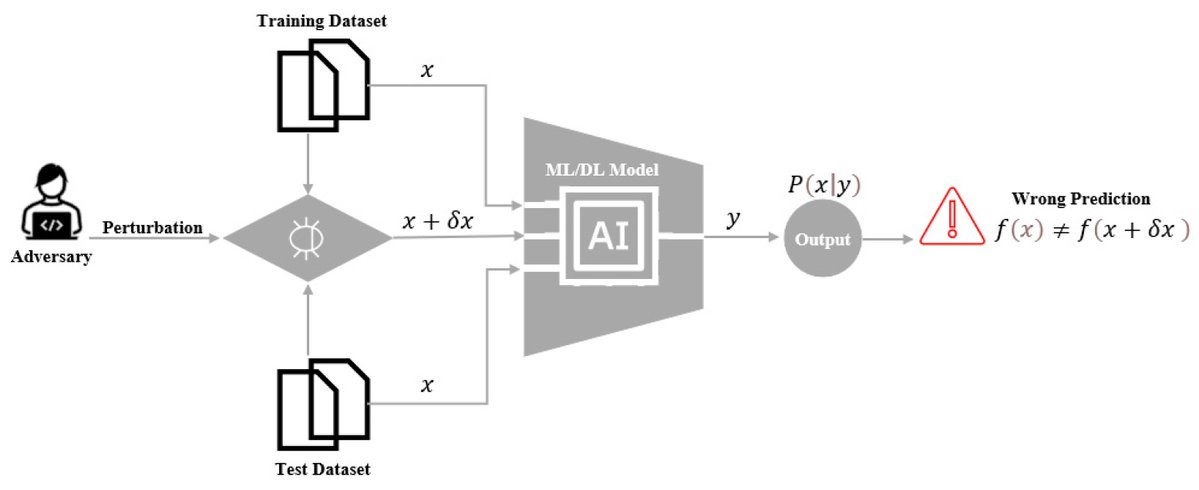
😈 Adversarial attacks = sneaky data gremlins! Train smart with adversarial examples & distillation to defend your neural nets. 🔗buff.ly/MIqCFgt and buff.ly/2veldxG #AI365 #AdversarialAttacks #NeuralNetworks #ML
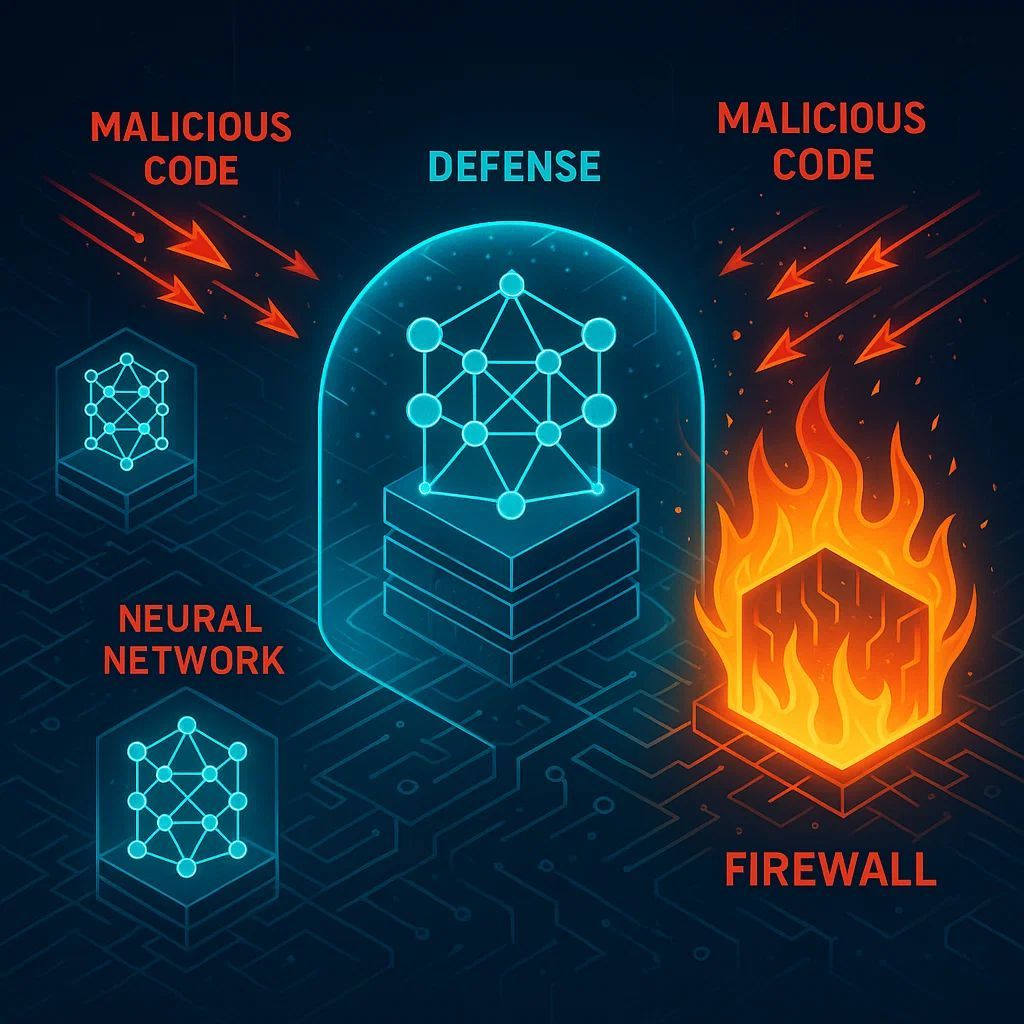
Following that was Zhang et al.'s "CIGA: Detecting Adversarial Samples via Critical Inference Graph Analysis," which explores how different layer connections help identify adversarial samples effectively. (acsac.org/2024/program/f…) 4/6 #ML #AdversarialAttacks #CyberSecurity

The Hidden Risk Behind 250 Documents and AI Corruption cysecurity.news/2025/10/the-hi… #Adversarialattacks #AIgovernance #AIRiskManagement

🚨 New Research Published in JCP! The Erosion of Cybersecurity Zero-Trust Principles Through Generative AI: A Survey on the Challenges and Future Directions 📄 Read the full article:mdpi.com/2624-800X/5/4/… #ZeroTrust #GenerativeAI #AdversarialAttacks

How Image Resizing Could Expose AI Systems to Attacks cysecurity.news/2025/08/how-im… #Adversarialattacks #AItools #algorithms

AI Agents and the Rise of the One-Person Unicorn cysecurity.news/2025/08/ai-age… #Accesscontrol #Adversarialattacks #agenticAI

Testing OpenAI Models Against Adversarial Attacks: A Guide for AI Researchers and Developers #AdversarialAttacks #AIsecurity #DeepteamFramework #MachineLearning #ModelRobustness itinai.com/testing-openai… Introduction to Adversarial Attacks on AI Models As artificial intelligenc…

📢 Welcome to read the top cited papers in the last 2 years: Top 9️⃣: #AdversarialMachineLearning Attacks against #IntrusionDetectionSystems: A Survey on Strategies and Defense Citations: 76 🔗 mdpi.com/1999-5903/15/2… #adversarialattacks #networksecurity @ComSciMath_Mdpi

Did you know that adversarial attacks can subtly manipulate input data to fool ML models into making wrong predictions? #AIsecurity #adversarialattacks
🔔 Welcome to read Editor's Choice Articles in the Q2 of 2024: 📌Title: Evaluating Realistic #AdversarialAttacks against Machine Learning Models for Windows PE Malware Detection mdpi.com/1999-5903/16/5… #adversarialtraining #explainableartificialintelligence @ComSciMath_Mdpi

Improving #Adversarial Transferability via Decision Boundary Adaptation (openreview.net/forum?id=IdAam…) to be presented at #UAI2025 @UncertaintyInAI @UTSA @utsacaicc @UTSResearch @Sydney_Uni #adversarialattacks #AI #neuralnetworks #privacy
🔔 Welcome to read Editor's Choice Articles in the Q1 of 2024: 📌Title: A Holistic Review of #MachineLearning Adversarial Attacks in IoT Networks 🔗 mdpi.com/1999-5903/16/1… #adversarialattacks #deeplearning #InternetofThings #intrusiondetectionsystem @ComSciMath_Mdpi

Can AI be tricked? We discuss real-world examples (#Tesla , #Siri ) of #adversarialattacks, where subtle changes fool #AI. Learn how to #secure #MachineLearning and understand the #vulnerabilities with our guest @mnkbuddh . Watch the clip to see how AI can be fooled. Check out…
The Hidden Risk Behind 250 Documents and AI Corruption cysecurity.news/2025/10/the-hi… #Adversarialattacks #AIgovernance #AIRiskManagement

🌟 @zicokolter revealed key vulnerabilities in #LLMs to #AdversarialAttacks. 🛡️Including a live demo, his insights underscore the urgent need for robust #AISafety measures. A vital call to action for AI security! 🤯🔐 #AIAlignmentWorkshop

🚨 New Research Published in JCP! The Erosion of Cybersecurity Zero-Trust Principles Through Generative AI: A Survey on the Challenges and Future Directions 📄 Read the full article:mdpi.com/2624-800X/5/4/… #ZeroTrust #GenerativeAI #AdversarialAttacks

Following that was Zhang et al.'s "CIGA: Detecting Adversarial Samples via Critical Inference Graph Analysis," which explores how different layer connections help identify adversarial samples effectively. (acsac.org/2024/program/f…) 4/6 #ML #AdversarialAttacks #CyberSecurity

How To Secure Generative AI Systems Against Emerging Threats #GenerativeAI #AdversarialAttacks #AI #DataPoisoning #WAF #WebApplicationFirewall #CyberSecurityNews #ProphazeWAF prophaze.com/kb-articles/ho…

How Image Resizing Could Expose AI Systems to Attacks cysecurity.news/2025/08/how-im… #Adversarialattacks #AItools #algorithms

Check out one of the latest topical papers from JPhys Complexity, exploring crossover phenomenon in adversarial attacks on voter model #CrossoverPhenomenon #AdversarialAttacks Read more here 👉 ow.ly/HNW950PUZrZ

AI Agents and the Rise of the One-Person Unicorn cysecurity.news/2025/08/ai-age… #Accesscontrol #Adversarialattacks #agenticAI

Presenting a novel approach to investigating #adversarialattacks on machine learning #classification models operating on tabular data: “Towards #automateddetection of adversarial attacks on tabular data” by P. Biczyk, Ł. Wawrowski. ACSIS Vol. 35 p.247–251; tinyurl.com/2fzmh9w6

#NewArticle Evaluating the Vulnerability of #YOLOv5 to #AdversarialAttacks for Enhanced Cybersecurity in #MASS mdpi.com/2271690 #mdpijmse via @JMSE_MDPI @MDPIEngineering #perturbedimage #objectclassification

Adversarial attacks pose a serious threat to AI systems. What innovative methods or techniques do you believe are crucial for safeguarding AI models against these attacks? 💡 Share your thoughts! #AIsecurity #AdversarialAttacks #AI #Security

Discover Transferability of Adversarial Attacks! #adversarialattacks #adversarialexamples #AIattacks #AIsecurity #deeplearning #foolingAImodels #MachineLearning #modelvulnerability #transferability aicompetence.org/adversarial-at…

😈 Adversarial attacks = sneaky data gremlins! Train smart with adversarial examples & distillation to defend your neural nets. 🔗buff.ly/MIqCFgt and buff.ly/2veldxG #AI365 #AdversarialAttacks #NeuralNetworks #ML

Next, Paul Stahlhofen presenting his work on #AdversarialAttacks for water distribution networks. Bad news: models for critical infrastructure are vulnerable. 😱 Good news: Now we know, we can use this knowledge to make systems more robust. 💪

🔒Protecting AI from #AdversarialAttacks! As #AI evolves, so do the risks. At Wibu-Systems, we use CodeMeter to shield machine learning models from adversarial threats, ensuring their integrity and security. Ready to safeguard your AI? wibu.com/blog/article/a… #ML #encryption

🔍 Query Tracking: AttackBench includes query tracking to enhance evaluation transparency, allowing fair comparisons by standardizing the number of queries each attack can leverage. #AdversarialAttacks

This #AIPaper Propsoes an #AIFramework to Prevent #AdversarialAttacks on #Mobile #VehicleToMicrogrid Services #V2M #Data #energy #AI #ArtificialIntelligence #Tech #Technology #GenerativeAdversarialNetworks #GANs buff.ly/3BSju5u

#AdversarialAttacks on #AImodels are rising: what should you do now? #AI #ArtificialIntelligence #ML #MachineLearning #Tech #Technology #CyberSecurity #CyberCriminals #CyberAttacks buff.ly/3ZyVuOr

Imposter.AI: Unveiling Adversarial Attack Strategies to Expose Vulnerabilities in Advanced Large Language Models itinai.com/imposter-ai-un… #LargeLanguageModels #AdversarialAttacks #ImposterAI #AIforBusiness #RedefineWithAI #ai #news #llm #ml #research #ainews #innov…

EaTVul: Demonstrating Over 83% Success Rate in Evasion Attacks on Deep Learning-Based Software Vulnerability Detection Systems itinai.com/eatvul-demonst… #AISecurity #AdversarialAttacks #SoftwareVulnerabilities #EvasionAttack #AIIntegration #ai #news #llm #ml #research #ainews #…

Something went wrong.
Something went wrong.
United States Trends
- 1. #StrangerThings5 101K posts
- 2. Thanksgiving 607K posts
- 3. Afghan 232K posts
- 4. National Guard 599K posts
- 5. Gonzaga 7,207 posts
- 6. holly 43.4K posts
- 7. Reed Sheppard 1,016 posts
- 8. #AEWDynamite 20.3K posts
- 9. robin 59.3K posts
- 10. Michigan 73.2K posts
- 11. Dustin 83.2K posts
- 12. #Survivor49 2,842 posts
- 13. Rahmanullah Lakanwal 88.6K posts
- 14. Tini 6,732 posts
- 15. Erica 11.2K posts
- 16. #GoAvsGo 1,211 posts
- 17. Kevin Knight 2,496 posts
- 18. Dusty May N/A
- 19. Bill Kristol 7,290 posts
- 20. Cease 28.5K posts