#bindshell ผลการค้นหา
The Programmatic expression of my will 👇 That's how I evade anti-virus programs 💀 #100DaysOfCode #bindshell #Python #CodeNewbie #Hacking

Gtfo - Search For Unix Binaries That Can Be Exploited To Bypass System Security Restrictions j.mp/374l7st #BindShell #Blueteam
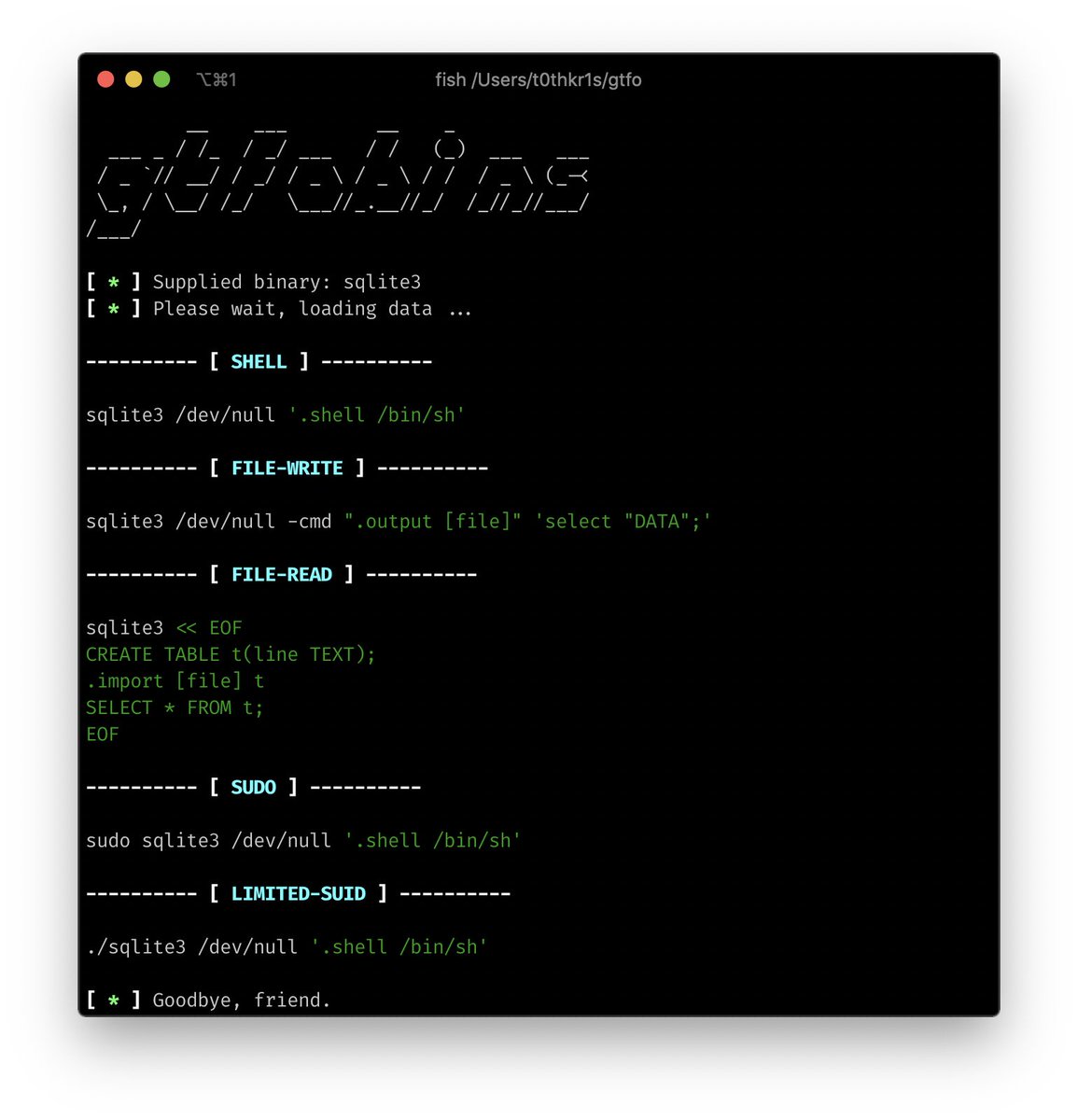
GodOfWar - Malicious Java WAR Builder With Built-In Payloads j.mp/2DfnYlb #BindShell #Godofwar #JAR #JSP #Linux #msfvenom
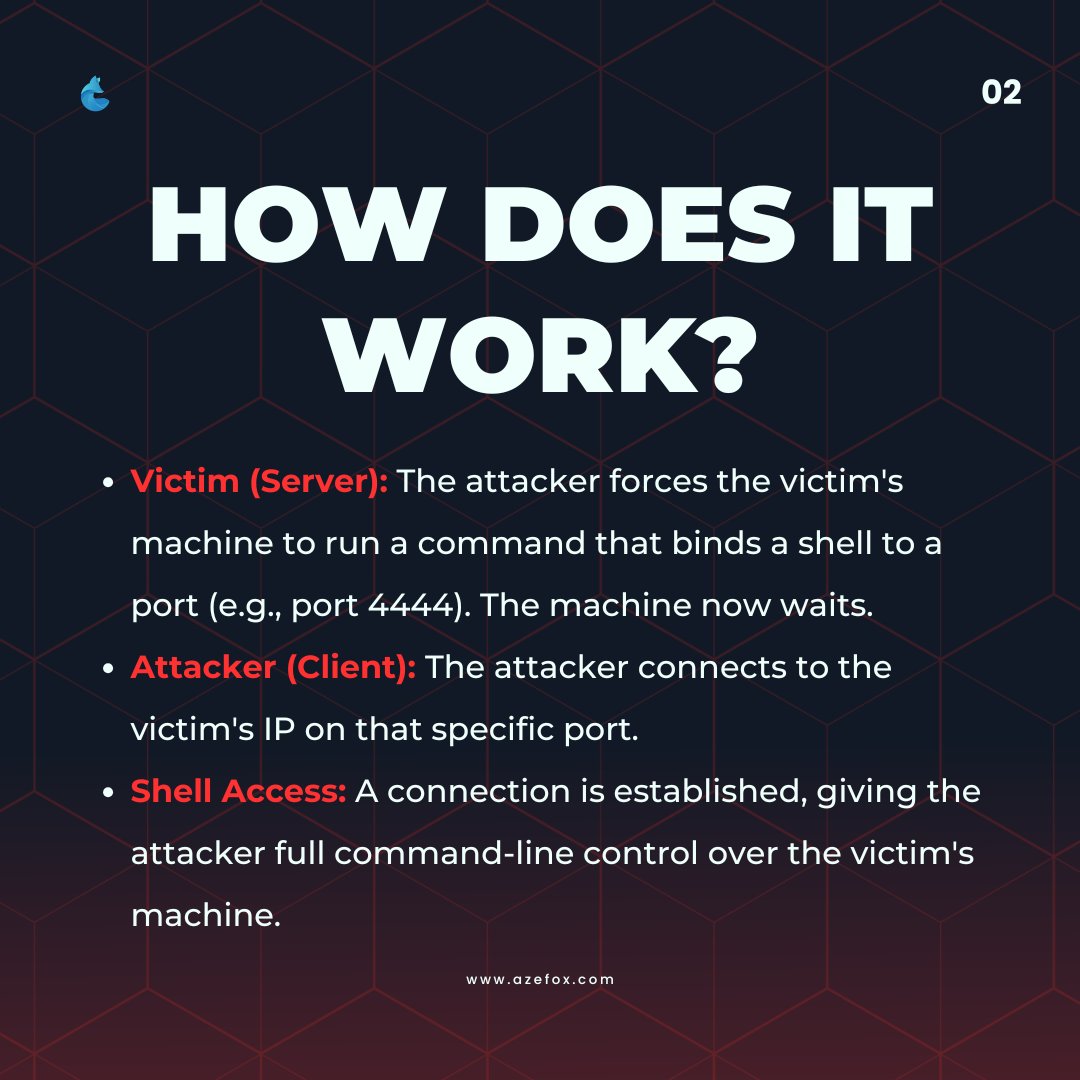
Bind Shell: a backdoor where the victim listens for connections. Direct but risky — firewalls & scans make it easier to detect than reverse shells. Follow Azefox Innovations to learn more on cybersecurity #CyberSecurity #EthicalHacking #BindShell #InfoSec #AzefoxInnovations



PostShell - Post Exploitation Bind/Backconnect Shell j.mp/2QgXVTQ #Antidebugging #BackConnect #Bindshell #Connections #Postshell

Faxhell - A Bind Shell Using The Fax Service And A DLL Hijack j.mp/3ffvVIj #BindShell #DLL #DllHijack #Faxhell #Leaks #Linux

GoSH - Golang Reverse/Bind Shell Generator bit.ly/38mlV1v #BindShell #golang #GoSH #ReverseShell #Shell

Shepard - In Progress Persistent Download/Upload/Execution Tool Using Windows BITS j.mp/34YDkIo #Bindshell #CommandLine #Python

Learn the main differences in between a bind shell and a reverse shell! zsecurity.org/hacking-101-bi… #cybersecurity #ethicalhacking #bindshell #reverseshell

GodOfWar - Malicious Java WAR Builder With Built-In Payloads j.mp/2DfnYlb #BindShell #Godofwar #JAR #JSP #Linux #msfvenom #spectresecurity

"RT Gtfo - Search For Unix Binaries That Can Be Exploited To Bypass System Security Restrictions j.mp/374l7st #BindShell #Blueteam https://t.co/xN3T8dYZfL"

earmas.ga - Gtfo - Search For Unix Binaries That Can Be Exploited To Bypass System Security Restrictions j.mp/374l7st #BindShell #Blueteam

Bir remote saldırı senaryosunda, saldırgan reverse veya bind shell tekniğini kullanarak kurbanın makinesinin kontrolünü ele geçirir. Bu bilgi postumuzda bir reverse ve bind shelli neyin oluşturduğunu açıklayacağız ve farklılıklarını vurgulayacağız. #bindshell #reverseshell



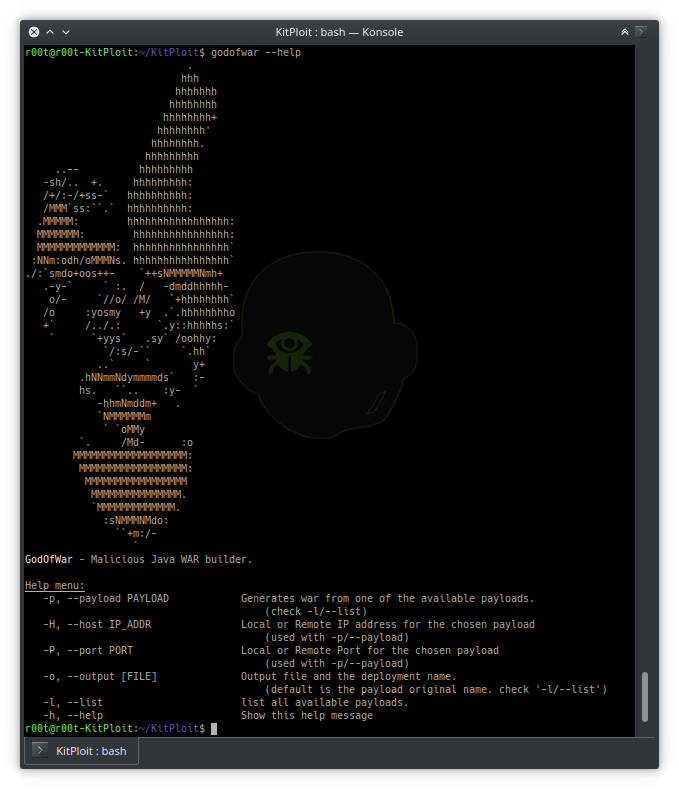
GoSH - Golang Reverse/Bind Shell Generator bit.ly/38mlV1v #BindShell #golang #GoSH #ReverseShell #Shell KitPloit

Learn #bindshell and #reverseshell in simplified way. Checkout more short videos at Instagram instagram.com/robensiv3?igsh… Watch detailed videos on youtube youtube.com/channel/UCsOqo…
Bind Shell: a backdoor where the victim listens for connections. Direct but risky — firewalls & scans make it easier to detect than reverse shells. Follow Azefox Innovations to learn more on cybersecurity #CyberSecurity #EthicalHacking #BindShell #InfoSec #AzefoxInnovations




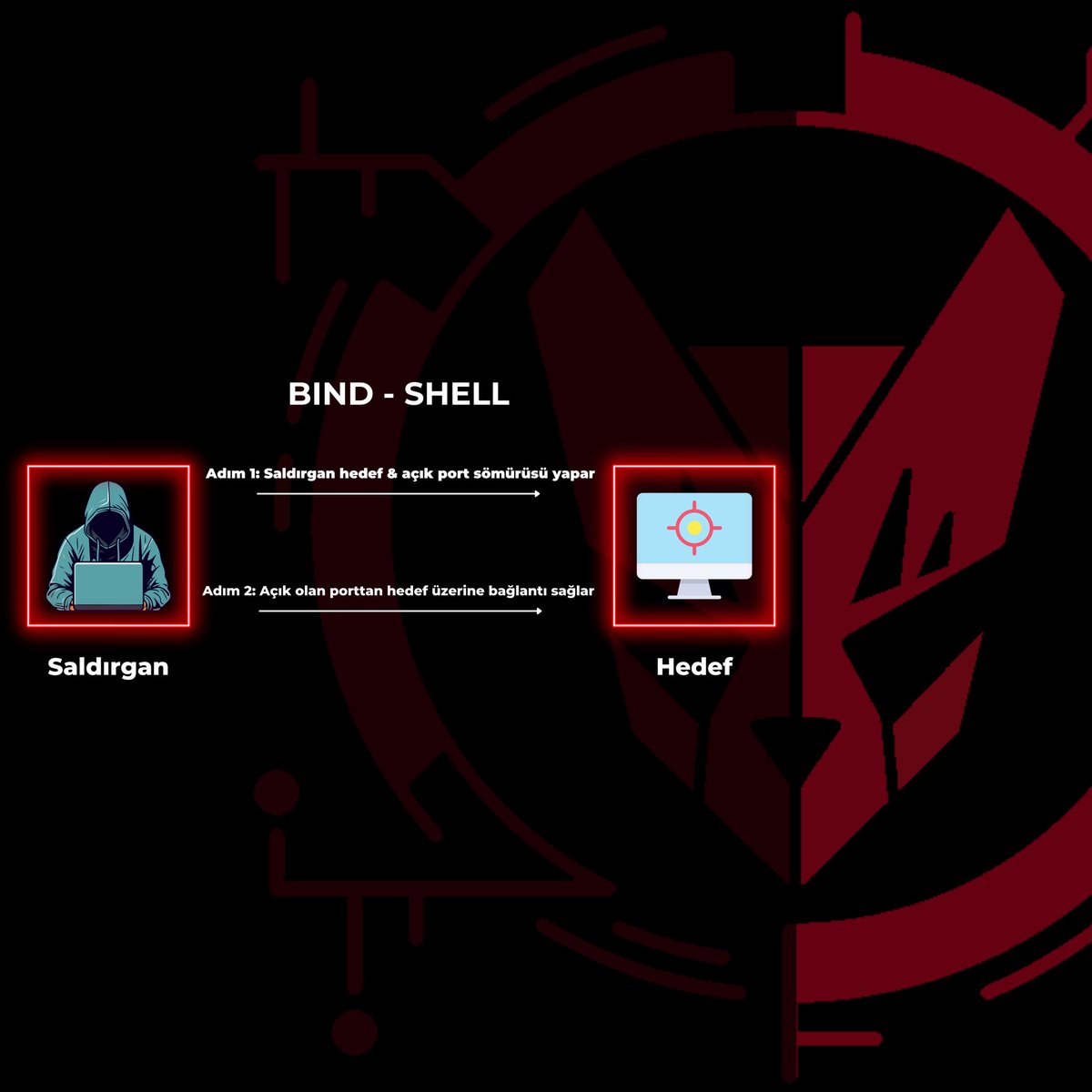
A #bindshell is a type of #shell that #listens on a specific #port for incoming connections. An established connection provides a #shellinterface to the remote machine, allowing the user to execute commands. Used for #remoteadministration and #troubleshooting.
Bir remote saldırı senaryosunda, saldırgan reverse veya bind shell tekniğini kullanarak kurbanın makinesinin kontrolünü ele geçirir. Bu bilgi postumuzda bir reverse ve bind shelli neyin oluşturduğunu açıklayacağız ve farklılıklarını vurgulayacağız. #bindshell #reverseshell




Diferencia entre Bind Shell y Reverse Shell | #BindShell #DiccionarioHacking #ReverseShell #Shell #Hacking esgeeks.com/diferencias-bi…
esgeeks.com
Diferencia entre Bind Shell y Reverse Shell » EsGeeks
Explorando las técnicas de acceso remoto en el mundo de la ciberseguridad: Descubre la diferencia entre Bind Shell y Reverse Shell.
Golang Bind and Reverse Shell #script #reverse_shell #bindshell #exploit #pentesting #hacking github.com/SaDs3c/goshell
🚨 Hablemos de hacking: #ReverseShell VS #bindshell🚨 Dos conceptos que a menudo se encuentran en el ámbito de la ciberseguridad son “Reverse Shell” y “Bind Shell“. Acá te presentamos más información sobre ambos! #redtiseg #Ciberseguridad redtiseg.com/2024/01/01/rev…
redtiseg.com
Reverse Shell vs. Bind Shell: Diferencias y Aplicaciones - REDTISEG
Dos conceptos que a menudo se encuentran en el ámbito de la ciberseguridad son “Reverse Shell” y “Bind Shell“.
Diferencia entre Bind Shell y Reverse Shell | #BindShell #DiccionarioHacking #ReverseShell #Shell #Hacking esgeeks.com/diferencias-bi…
esgeeks.com
Diferencia entre Bind Shell y Reverse Shell » EsGeeks
Explorando las técnicas de acceso remoto en el mundo de la ciberseguridad: Descubre la diferencia entre Bind Shell y Reverse Shell.
Diferencia entre Bind Shell y Reverse Shell | #BindShell #DiccionarioHacking #ReverseShell #Shell #Hacking esgeeks.com/diferencias-bi…
Just published our latest blog on Reverse Shell and Bind Shell: A Comprehensive Guide! Learn about these powerful techniques used by hackers and security professionals. Read it now on our website! krishanuchakraborty.com/blog/reverse-s… #reverseshell #bindshell #cybersecurity #hacking
OS on OS on OS @RealTryHackMe #reverseshell #bindshell #Netcat #webshells #WindowsShell #LinuxShell #tryhackme #pentesting

Learn #bindshell and #reverseshell in simplified way. Checkout more short videos at Instagram instagram.com/robensiv3?igsh… Watch detailed videos on youtube youtube.com/channel/UCsOqo…
It boggles my mind that Echo Mirage is still widely used as tool and it was written before I entered the hacking world. As far as I can tell it hasn't changed since then. #BindShell #IfYouKnowYouKnow #oldfartsclub
GoSH - Golang Reverse/Bind Shell Generator bit.ly/38mlV1v #BindShell #golang #GoSH #ReverseShell #Shell KitPloit

"RT GoSH - Golang Reverse/Bind Shell Generator bit.ly/38mlV1v #BindShell #golang #GoSH #ReverseShell #Shell https://t.co/Zm0KxqqCUU"

PostShell - Post Exploitation Bind/Backconnect Shell j.mp/2QgXVTQ #Antidebugging #BackConnect #Bindshell #Connections #Postshell

GodOfWar - Malicious Java WAR Builder With Built-In Payloads j.mp/2DfnYlb #BindShell #Godofwar #JAR #JSP #Linux #msfvenom

Gtfo - Search For Unix Binaries That Can Be Exploited To Bypass System Security Restrictions j.mp/374l7st #BindShell #Blueteam

Faxhell - A Bind Shell Using The Fax Service And A DLL Hijack j.mp/3ffvVIj #BindShell #DLL #DllHijack #Faxhell #Leaks #Linux

GoSH - Golang Reverse/Bind Shell Generator bit.ly/38mlV1v #BindShell #golang #GoSH #ReverseShell #Shell

Shepard - In Progress Persistent Download/Upload/Execution Tool Using Windows BITS j.mp/34YDkIo #Bindshell #CommandLine #Python

The Programmatic expression of my will 👇 That's how I evade anti-virus programs 💀 #100DaysOfCode #bindshell #Python #CodeNewbie #Hacking

Learn the main differences in between a bind shell and a reverse shell! zsecurity.org/hacking-101-bi… #cybersecurity #ethicalhacking #bindshell #reverseshell

A Bind Shell Using the Fax Service and a DLL Hijack github.com/ionescu007/fax… #Pentesting #BindShell #DLL #Hacking #Infosec


Bind Shell: a backdoor where the victim listens for connections. Direct but risky — firewalls & scans make it easier to detect than reverse shells. Follow Azefox Innovations to learn more on cybersecurity #CyberSecurity #EthicalHacking #BindShell #InfoSec #AzefoxInnovations




GodOfWar - Malicious Java WAR Builder With Built-In Payloads j.mp/2DfnYlb #BindShell #Godofwar #JAR #JSP #Linux #msfvenom #spectresecurity

Retro shellcoding for current threats: rebinding sockets in Windows shelliscoming.com/2019/11/retro-… #Windows #ShellCoding #BindShell #ExploitDev #Infosec



OS on OS on OS @RealTryHackMe #reverseshell #bindshell #Netcat #webshells #WindowsShell #LinuxShell #tryhackme #pentesting

Shepard - In Progress Persistent Download/Upload/Execution Tool Using Windows BITS dlvr.it/S26CCK #Bindshell #CommandLine #Python #Shepard

GoSH - Golang Reverse/Bind Shell Generator bit.ly/38mlV1v #BindShell #golang #GoSH #ReverseShell #Shell KitPloit

Bir remote saldırı senaryosunda, saldırgan reverse veya bind shell tekniğini kullanarak kurbanın makinesinin kontrolünü ele geçirir. Bu bilgi postumuzda bir reverse ve bind shelli neyin oluşturduğunu açıklayacağız ve farklılıklarını vurgulayacağız. #bindshell #reverseshell




"RT Gtfo - Search For Unix Binaries That Can Be Exploited To Bypass System Security Restrictions j.mp/374l7st #BindShell #Blueteam https://t.co/xN3T8dYZfL"

Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Halloween 855K posts
- 2. YouTube TV 50.2K posts
- 3. Dolphins 42K posts
- 4. #SinisterMinds 7,259 posts
- 5. Ryan Rollins 12.7K posts
- 6. Ravens 56.6K posts
- 7. #RUNSEOKJIN_epTOUR_ENCORE 112K posts
- 8. Mary Ann N/A
- 9. Lamar 53.5K posts
- 10. #T1WIN 8,337 posts
- 11. Mike McDaniel 5,282 posts
- 12. #Jin_TOUR_ENCORE 108K posts
- 13. YTTV N/A
- 14. Talbot 1,105 posts
- 15. Hulu 18.8K posts
- 16. Mindy 3,789 posts
- 17. frank iero 2,014 posts
- 18. #RHOC 3,590 posts
- 19. Corey Perry N/A
- 20. toby fox 8,106 posts

























