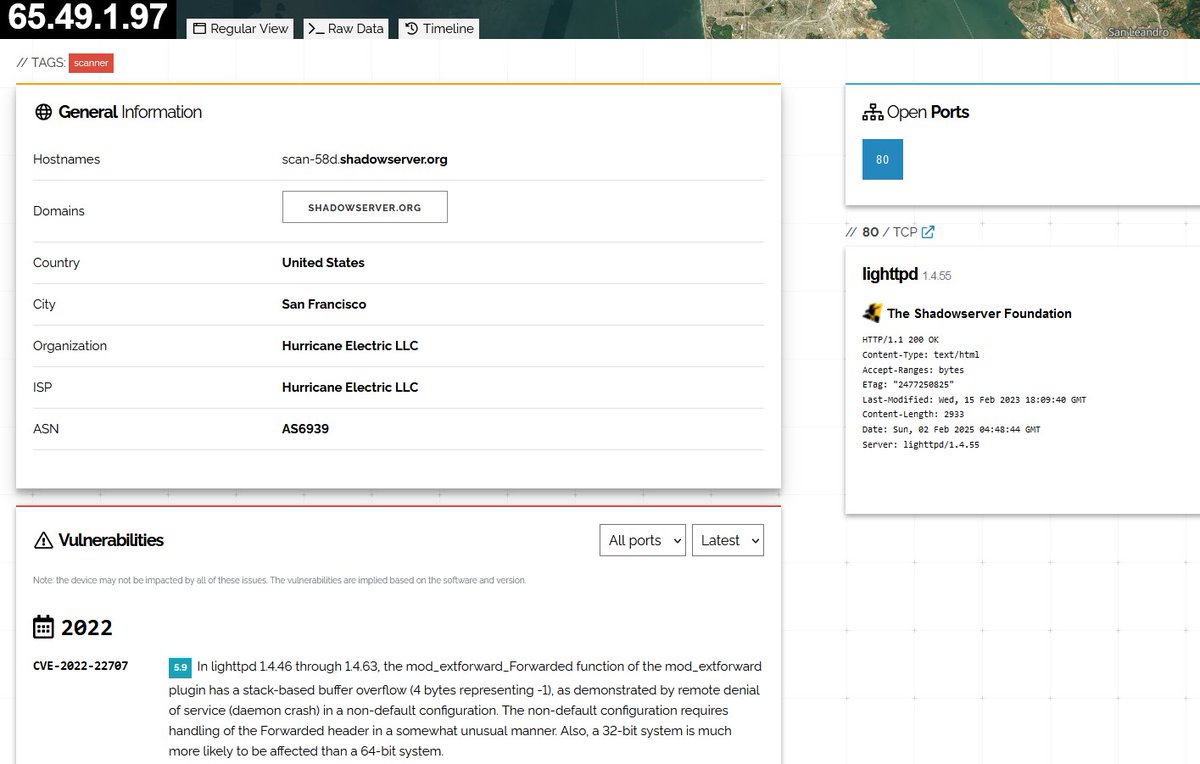
#botnet search results
⚠️ Nuevo #botnet en acción: AISURU está usando millones de dispositivos IoT como armas DDoS 💥 Tu cámara o router podrían estar atacando sin que lo sepas. 🔒 Cambia contraseñas, actualiza firmware. 💼 En @MMarcoSeguridad y @Ciberseguridad24h protegemos. 🌐 mmarcoseguridad.com
"Since October 8, 2025, GreyNoise has tracked a coordinated botnet operation involving over 100,000 unique IP addresses from more than 100 countries targeting Remote Desktop Protocol (RDP) services in the United States". #Cybersecurity #BotNet #RDP greynoise.io/blog/botnet-la…
Looks like this #Mirai threat actor is a BIG fan of our URLhaus platform 😜 👉 hXXp://45.141.215.196/FuckYou0urlhaus0abuse0ch/ We thought we'd send a little love back to the threat actor... their server’s been taken down, and their #botnet C2 domain is now sinkholed. 😘

💥 RondoDox botnet is firing an 'exploit shotgun' at Microsoft Edge vulnerabilities. Is your endpoint security ready? #Botnet #EdgeSecurity ⤵️
Nuevo botnet peligroso, RondoDox, ataca a nivel mundial a una velocidad incontrolable. ¡Descubre los detalles! #ciberseguridad #botnet exe.io/xrxcd

🔹 بوت نت RondoDox يستخدم أسلوب “طلقات الاستغلال العشوائية” شبكة RondoDox Botnet تعتمد على استراتيجية هجومية جديدة تُعرف بـ “Exploit Shotgun” لاستهداف أكبر عدد من الأنظمة في وقت واحد. #RondoDox #Botnet #Malware #CyberThreat

#RondoDox #botnet #targets #56 #n-#day #flaws #in #worldwide #attacks bleepingcomputer.com/news/security/…
RondoDox insegna che la tecnologia è sia affascinante che inquietante, mentre OpenAI e Microsoft affrontano le loro sfide. #OpenAI #botnet daily.movingwords.it

#ThreatProtection Uptick of activity attributed to the #RondoDox #botnet, read more about Symantec's protection: broadcom.com/support/securi… #malware
Looks like this #Mirai threat actor is a BIG fan of our URLhaus platform 😜 👉 hXXp://45.141.215.196/FuckYou0urlhaus0abuse0ch/ We thought we'd send a little love back to the threat actor... their server’s been taken down, and their #botnet C2 domain is now sinkholed. 😘…

#RondoDox #botnet fires 'exploit shotgun' at nearly every router and internet-connected home device #Malware #CyberSecurity theregister.com/2025/10/09/ron… via @theregister
RondoDox: a nova botnet ‘shotgun’ que ataca 56 vulnerabilidades em routers e câmaras #botnet #cve #digital #exploit #firmware #hacking #internet #iot #malware #marcas #qnap #segurança #servidores #tplink #vulnerabilidade #vulnerabilidades #web tugatech.com.pt/t72718-rondodo…
RondoDox botnet targets 56 n-day flaws in worldwide attacks reconbee.com/rondodox-botne… #RondoDoxbotnet #botnet #cyberattacks #CybersecurityNews
BOTNET RONDODOX VISA FALHAS DE 56 DIAS EM ATAQUES MUNDIAIS samirnews.com/2025/10/botnet… #SamirNews #botnet #rondodox #visa #falhas #de #56 #dias #em #ataques #mundiais
🪲 Security RondoDox botnet targets 56 n-day flaws across 30+ device types, including Pwn2Own-disclosed bugs. #Botnet #Vulnerabilities #CyberSecurity #IoT

Joker (IRATA/COPYBARA) #Android banking #botnet is still active. It has been observed that they are making changes to the botnet panel. Additionally, it appears that they are now targeting #Russia, a country they had not previously targeted. C2: hxxp://80[.]251.153.96/ md5:…
![0x6rss's tweet image. Joker (IRATA/COPYBARA) #Android banking #botnet is still active. It has been observed that they are making changes to the botnet panel. Additionally, it appears that they are now targeting #Russia, a country they had not previously targeted.
C2: hxxp://80[.]251.153.96/
md5:…](https://pbs.twimg.com/media/GVfy2eFW4AAO8tc.jpg)
![0x6rss's tweet image. Joker (IRATA/COPYBARA) #Android banking #botnet is still active. It has been observed that they are making changes to the botnet panel. Additionally, it appears that they are now targeting #Russia, a country they had not previously targeted.
C2: hxxp://80[.]251.153.96/
md5:…](https://pbs.twimg.com/media/GVfy4_0XAAAqLZ7.png)
![0x6rss's tweet image. Joker (IRATA/COPYBARA) #Android banking #botnet is still active. It has been observed that they are making changes to the botnet panel. Additionally, it appears that they are now targeting #Russia, a country they had not previously targeted.
C2: hxxp://80[.]251.153.96/
md5:…](https://pbs.twimg.com/media/GVfzC0WXAAA43ad.jpg)
![0x6rss's tweet image. Joker (IRATA/COPYBARA) #Android banking #botnet is still active. It has been observed that they are making changes to the botnet panel. Additionally, it appears that they are now targeting #Russia, a country they had not previously targeted.
C2: hxxp://80[.]251.153.96/
md5:…](https://pbs.twimg.com/media/GVfzmySWcAA_j1_.jpg)
94.156.71.]55 seems to be hosting files related to #mirai #botnet provider Limenet IP resolves to cyberbotne.stresse[.]live Using @ValidinLLC to pivot on base domain, I came across another IP 94.156.66[.]191 which previously had the website title StressLand :: Best IP Stresser
![raghav127001's tweet image. 94.156.71.]55 seems to be hosting files related to #mirai #botnet provider Limenet
IP resolves to cyberbotne.stresse[.]live
Using @ValidinLLC to pivot on base domain, I came across another IP
94.156.66[.]191 which previously had the website title StressLand :: Best IP Stresser](https://pbs.twimg.com/media/GTddfKVWYAAwdzj.png)
![raghav127001's tweet image. 94.156.71.]55 seems to be hosting files related to #mirai #botnet provider Limenet
IP resolves to cyberbotne.stresse[.]live
Using @ValidinLLC to pivot on base domain, I came across another IP
94.156.66[.]191 which previously had the website title StressLand :: Best IP Stresser](https://pbs.twimg.com/media/GTddg47XMAEmGYv.jpg)
![raghav127001's tweet image. 94.156.71.]55 seems to be hosting files related to #mirai #botnet provider Limenet
IP resolves to cyberbotne.stresse[.]live
Using @ValidinLLC to pivot on base domain, I came across another IP
94.156.66[.]191 which previously had the website title StressLand :: Best IP Stresser](https://pbs.twimg.com/media/GTdeCyuW4AAtiKl.jpg)
![raghav127001's tweet image. 94.156.71.]55 seems to be hosting files related to #mirai #botnet provider Limenet
IP resolves to cyberbotne.stresse[.]live
Using @ValidinLLC to pivot on base domain, I came across another IP
94.156.66[.]191 which previously had the website title StressLand :: Best IP Stresser](https://pbs.twimg.com/media/GTdeDyjW4AAmLUF.jpg)

#botnet #iocs! 430 duplicates which means they have been online for a while. and 49 new malware urls! Malware urls/IOC's can be found here: pastebin.com/0QTEJvkX urlhaus.abuse.ch/browse/

Amazing to finally meet in person @0dayCTF at @defcon !!! #botnet #spyware #ransomware #stealer #adware #defcon #defcon32 #cyber #womanincyber #womanincybersecurity #hacker #cybercriminal #хакер #skynet #blackhat #blackhathacker #vxug

IM android botnet #botnet is active. its based in China hash: 2e81663fda2f410c23b8642984d2076686129640b42fd3e866ad16e6cfd2c06a APK distribution address: hxxps://besa[.]top/test C2: hxxp://c999testdemo[.]pk6gb3[.]top:8092/pages/console/login.html icon_hash="-1153292831" urlscan:…
![0x6rss's tweet image. IM android botnet #botnet is active. its based in China
hash: 2e81663fda2f410c23b8642984d2076686129640b42fd3e866ad16e6cfd2c06a
APK distribution address: hxxps://besa[.]top/test
C2: hxxp://c999testdemo[.]pk6gb3[.]top:8092/pages/console/login.html
icon_hash="-1153292831"
urlscan:…](https://pbs.twimg.com/media/GfeZHg9XUAAlCpI.jpg)
![0x6rss's tweet image. IM android botnet #botnet is active. its based in China
hash: 2e81663fda2f410c23b8642984d2076686129640b42fd3e866ad16e6cfd2c06a
APK distribution address: hxxps://besa[.]top/test
C2: hxxp://c999testdemo[.]pk6gb3[.]top:8092/pages/console/login.html
icon_hash="-1153292831"
urlscan:…](https://pbs.twimg.com/media/GfeZJLOWcAA88IT.jpg)
![0x6rss's tweet image. IM android botnet #botnet is active. its based in China
hash: 2e81663fda2f410c23b8642984d2076686129640b42fd3e866ad16e6cfd2c06a
APK distribution address: hxxps://besa[.]top/test
C2: hxxp://c999testdemo[.]pk6gb3[.]top:8092/pages/console/login.html
icon_hash="-1153292831"
urlscan:…](https://pbs.twimg.com/media/GfeZK64XYAAR8c6.jpg)
![0x6rss's tweet image. IM android botnet #botnet is active. its based in China
hash: 2e81663fda2f410c23b8642984d2076686129640b42fd3e866ad16e6cfd2c06a
APK distribution address: hxxps://besa[.]top/test
C2: hxxp://c999testdemo[.]pk6gb3[.]top:8092/pages/console/login.html
icon_hash="-1153292831"
urlscan:…](https://pbs.twimg.com/media/Gfeg_3_W8AAzgcW.png)
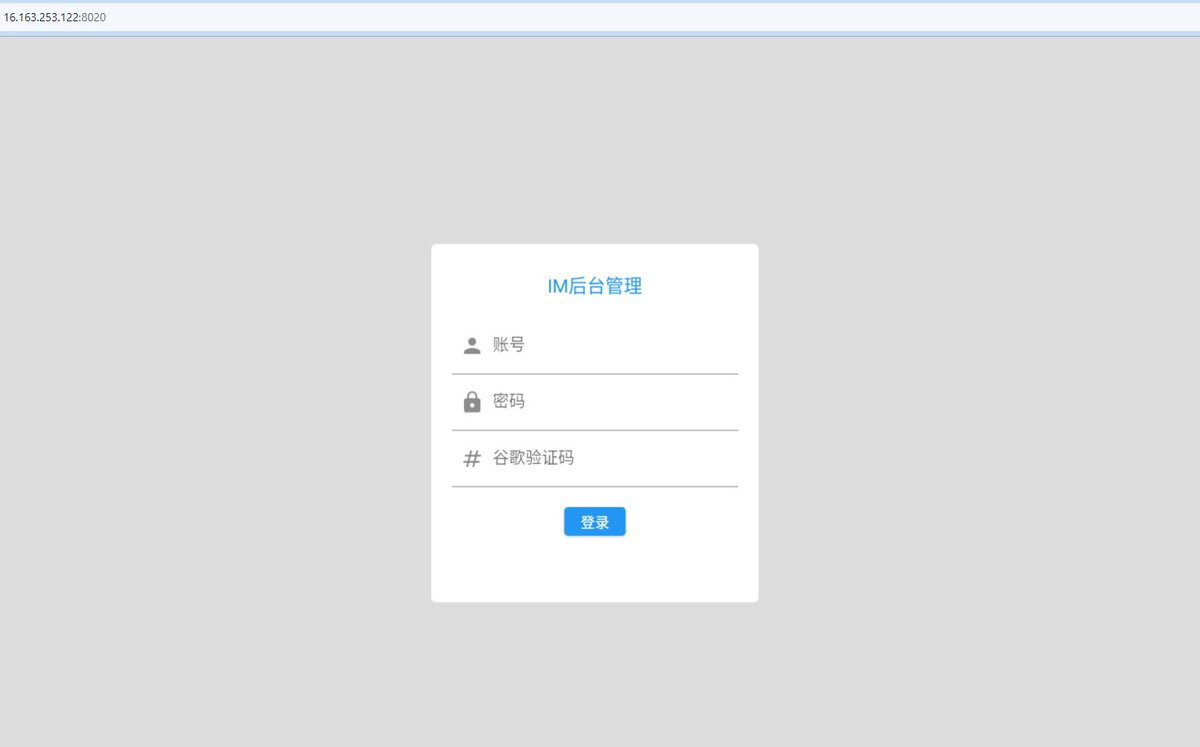
⚠️New #Android Banking Botnet Affecting many countries.. C2: hxxp://16.163.253[.122:8020 @LukasStefanko @malwrhunterteam
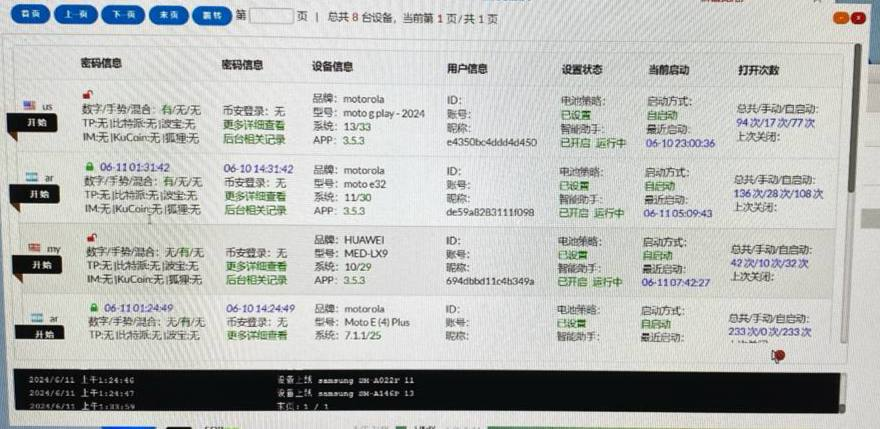

🚨#Opendir #botnet🚨 http://176.113.115.7/files/ ⚠️#Redline #Stealer ☣️C2C hosting with several pieces of malware per folder. 🔥#Bulletproof Hosting CATTECHNOLOGIES-AS, HK (AS57678)



🚨 Ermac Banking #Botnet v3.0 Leak 🚨 A site distributing #Hackingtools allegedly shared Ermac Banking Botnet V3.0 — an evolved #Android trojan derived from Cerberus & Hook. It targets 700+ banking, shopping & crypto apps worldwide. #Cybercrime #Malware

Found another interesting IP on #limenet http://91.92.242[.]121:1337 seems to be a #botnet dashboard showing the count of current infected hosts. Same on port 8080
![raghav127001's tweet image. Found another interesting IP on #limenet
http://91.92.242[.]121:1337 seems to be a #botnet dashboard showing the count of current infected hosts. Same on port 8080](https://pbs.twimg.com/media/GTeCfaAWYAAR34V.jpg)
![raghav127001's tweet image. Found another interesting IP on #limenet
http://91.92.242[.]121:1337 seems to be a #botnet dashboard showing the count of current infected hosts. Same on port 8080](https://pbs.twimg.com/media/GTeC8kiW0AAyFY5.jpg)
Ever heard of a #botnet? If not, it’s time to pay attention 👀 These massive networks of hacked devices are behind some of the biggest #cyberattacks ever! Let’s break down what botnets are, the most notorious botnets, the massive attacks they’ve executed, and how to keep your…

Good morning, @defcon and @vxunderground #botnet #spyware #ransomware #stealer #adware #defcon #defcon32 #cyber #womanincyber #womanincybersecurity #hacker #cybercriminal #хакер #skynet #blackhat #blackhathacker #vxug


Something went wrong.
Something went wrong.
United States Trends
- 1. Jets 60.1K posts
- 2. Justin Fields 3,727 posts
- 3. Aaron Glenn N/A
- 4. Peart 1,365 posts
- 5. #BroncosCountry 2,109 posts
- 6. Tyrod N/A
- 7. Sherwood 1,191 posts
- 8. Good Sunday 64.9K posts
- 9. #JetUp 1,201 posts
- 10. #AskFFT N/A
- 11. #sundayvibes 6,360 posts
- 12. #DENvsNYJ 1,382 posts
- 13. Bam Knight N/A
- 14. Brownlee 1,002 posts
- 15. Nate Adkins N/A
- 16. Garrett Wilson N/A
- 17. Rich Eisen N/A
- 18. Troy Franklin N/A
- 19. George Stephanopoulos 2,294 posts
- 20. Lutz 1,413 posts