#iocs search results
More sex shop themed Cyber Stealer panels: 69.30.247[.]233:3004 iloveboats9[.]vip @solostalking @500mk500 #InfoSec #malware #iocs
![AUZombie's tweet image. More sex shop themed Cyber Stealer panels:
69.30.247[.]233:3004
iloveboats9[.]vip
@solostalking @500mk500
#InfoSec #malware #iocs](https://pbs.twimg.com/media/G4qmqjEa4AAyV4I.png)
⚠️ Gunra is a fast-growing #ransomware using Conti-based code and double extortion It targets healthcare, manufacturing, and other sectors worldwide, deletes recovery options, and encrypts data across entire networks 👾 Explore analysis & gather #IOCs: any.run/malware-trends…

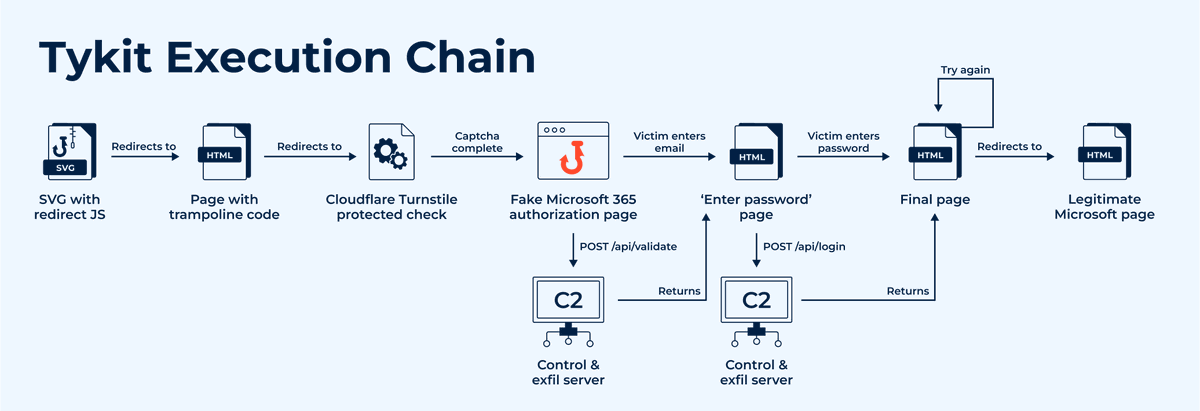
🚨 We uncovered #Tykit, a new #phishing kit targeting hundreds of US & EU companies in finance, construction, and telecom. It uses SVG-based delivery to harvest Microsoft 365 credentials ⚠️ See full analysis, how to detect it, and gather #IOCs: any.run/cybersecurity-…
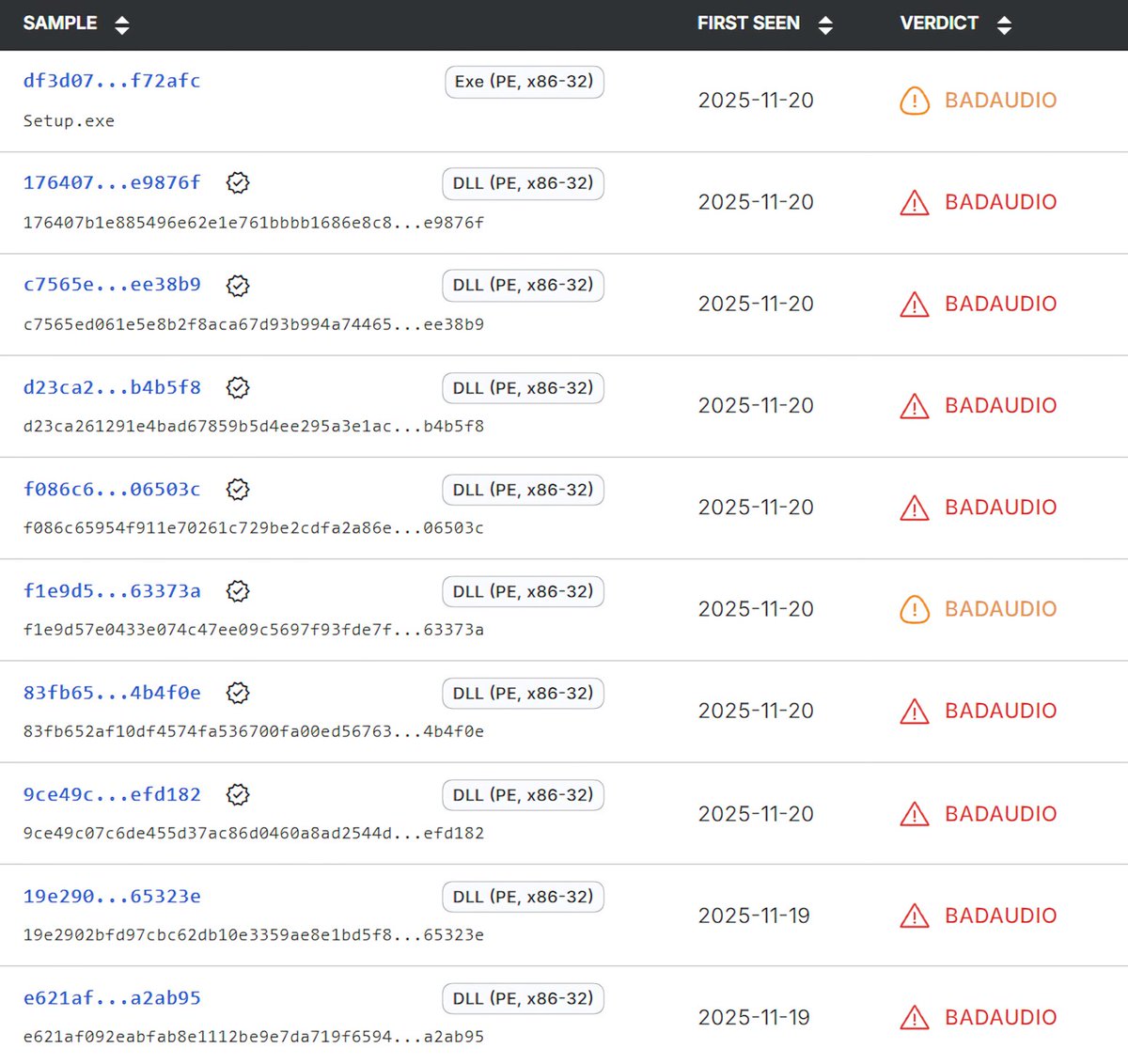
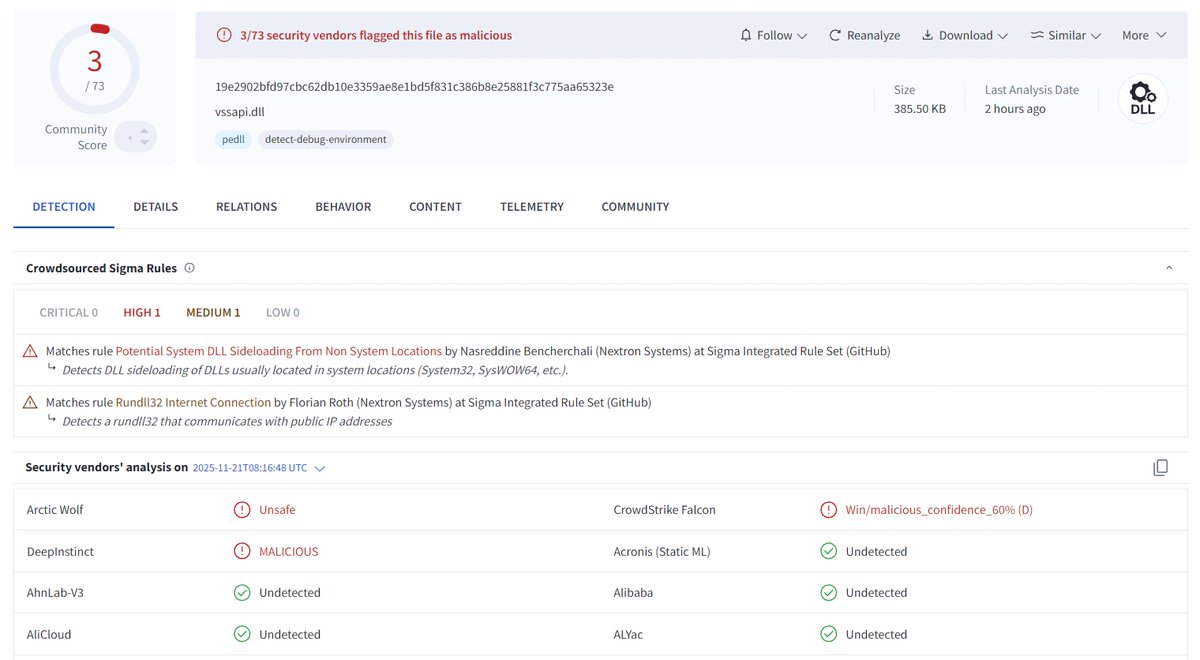
We got you some fresh #IOCs before the weekend. Yesterday, Google Threat Intel Group @Mandiant published a new report about #APT24's recent activities using #BADAUDIO as a first stage downloader. We retrohunted for this threat in our dataset and found two additional recent…
La próxima versión de #4n4lDetector será la herramienta que más nos ayudará en la recolección de #IOCs de #malware... no tengo dudas. Se han revisado y mejorado todos los módulos que la componen. Gracias a Sandra Badia Gimeno por la realización del nuevo logo de la herramienta.😘

Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️ /18.117.173[.]7 /kennedywilsoninc[.]com #IoCs #ScatteredSpider | #ThreatHunting #Censys @500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H
![soursec_'s tweet image. Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️
/18.117.173[.]7
/kennedywilsoninc[.]com
#IoCs #ScatteredSpider | #ThreatHunting #Censys
@500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H](https://pbs.twimg.com/media/GvmoDBYWYAEE1-8.jpg)
![soursec_'s tweet image. Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️
/18.117.173[.]7
/kennedywilsoninc[.]com
#IoCs #ScatteredSpider | #ThreatHunting #Censys
@500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H](https://pbs.twimg.com/media/GvmoLXCbsAApOs5.jpg)
![soursec_'s tweet image. Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️
/18.117.173[.]7
/kennedywilsoninc[.]com
#IoCs #ScatteredSpider | #ThreatHunting #Censys
@500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H](https://pbs.twimg.com/media/GvmoMRsbsAQtmyl.jpg)
![soursec_'s tweet image. Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️
/18.117.173[.]7
/kennedywilsoninc[.]com
#IoCs #ScatteredSpider | #ThreatHunting #Censys
@500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H](https://pbs.twimg.com/media/GvmoM8FbsAA-FM7.jpg)
🚨 Hunt Alert 🚨 Pivoted from the #SlowTempest #IOCs and uncovered a peculiar HTML page—only ~140 results globally, mainly in Hong Kong/China 🇭🇰🇨🇳. Most common port: 8888, potentially a admin/login panel. Thanks @MichalKoczwara for your input! Notably, the HTML page pivots…
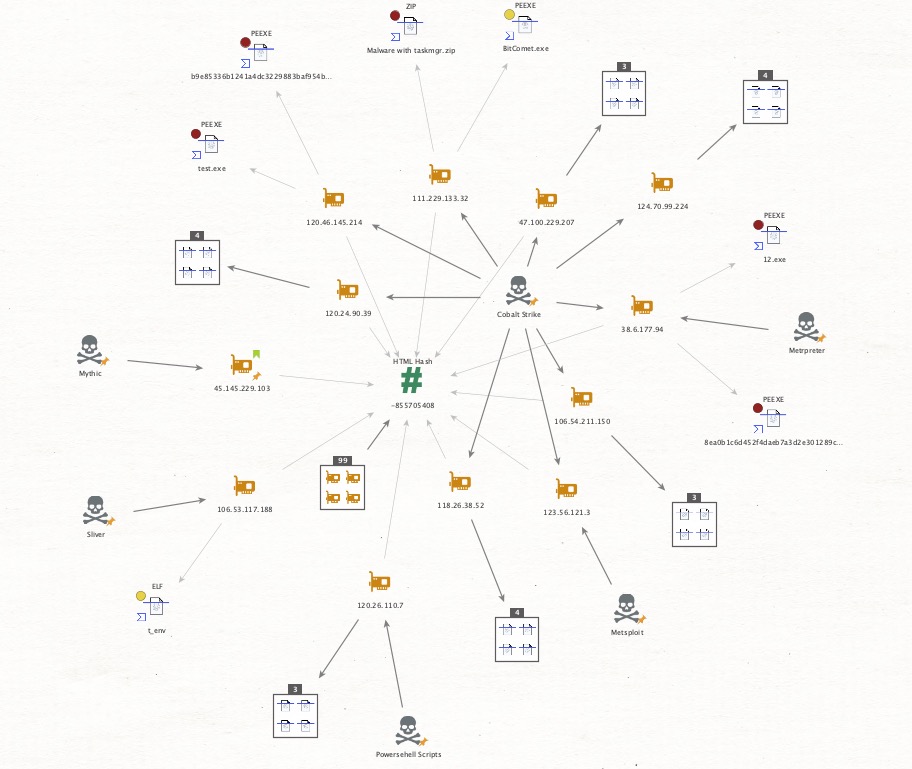
#GlassCage zero-click attack IOS Once triggered, the chain escalates to full root access via a combination of WebKit RCE (CVE-2025-24201) and Core Media kernel exploitation (CVE-2025-24085).#IOCs weareapartyof1.substack.com/p/glass-cage-z…
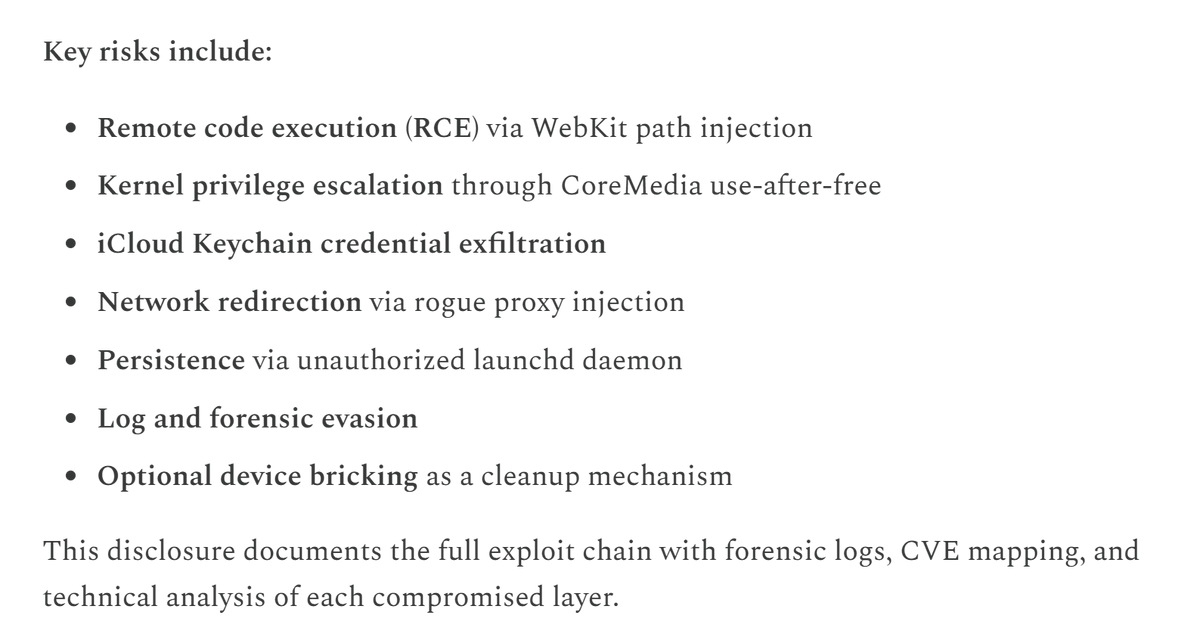

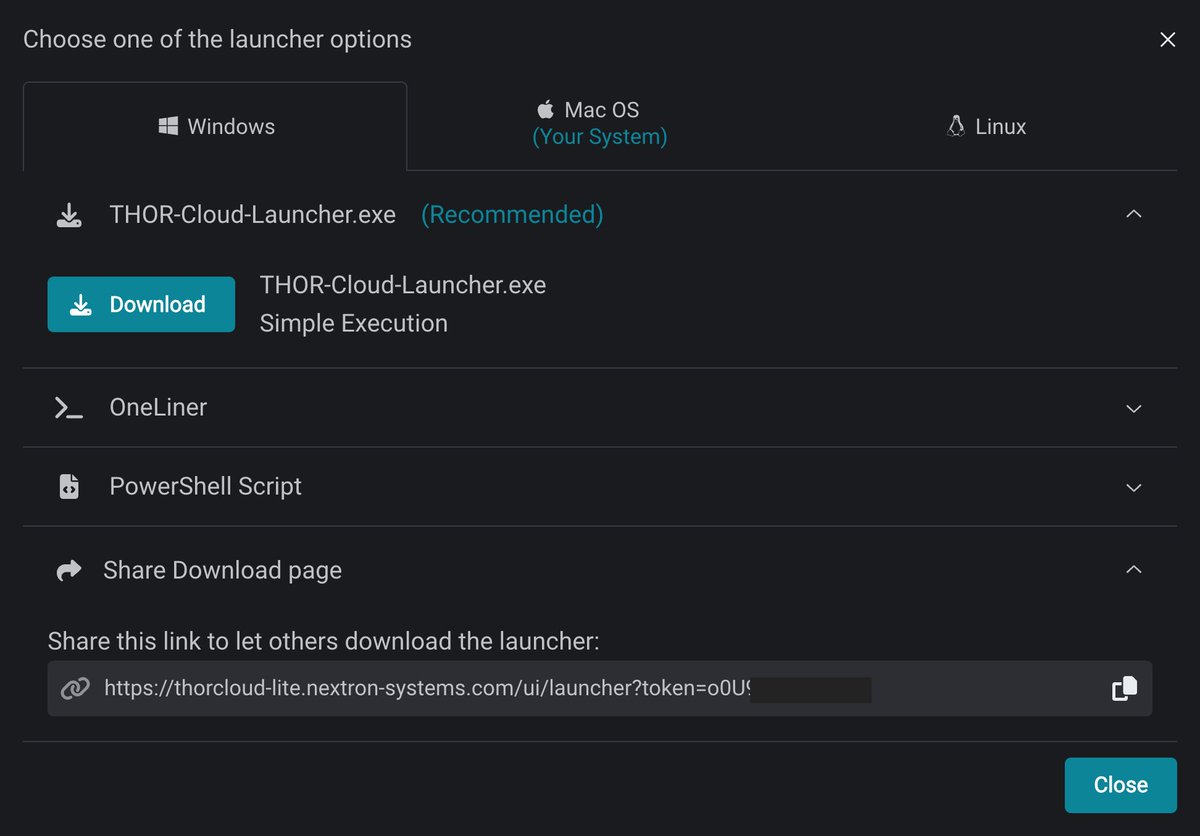
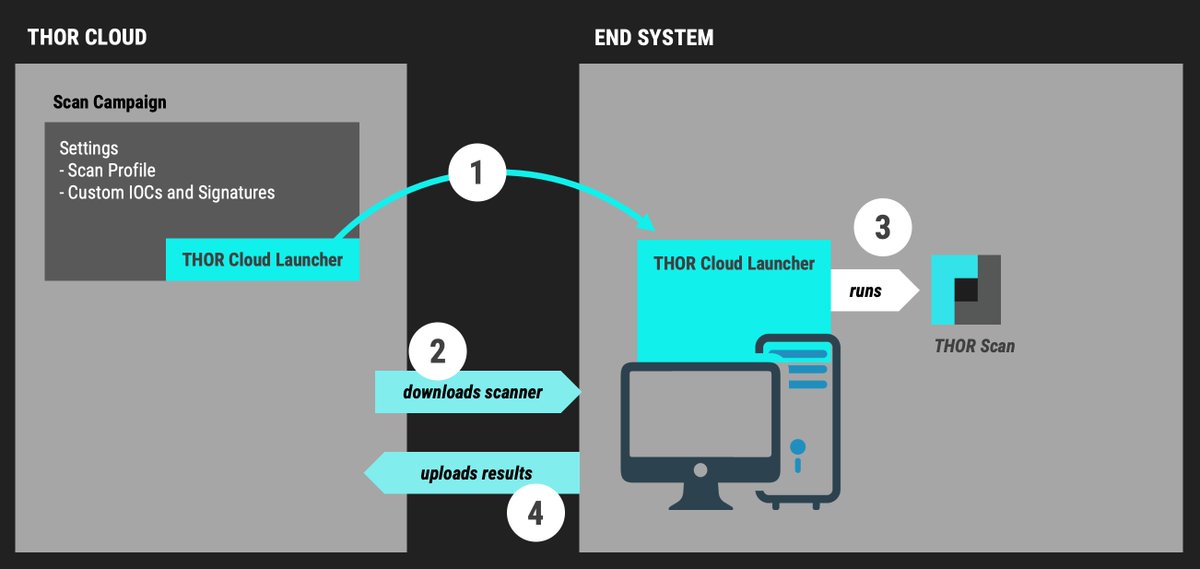
Ever got a bunch of #IOCs or #YARA rules and thought “how do I quickly check a few endpoints without setting up anything?” Here’s a trick: use THOR Cloud. You can just upload your IOCs or YARA rules, create a small scan campaign, and send someone a link. They download the…
Introducing THOR-Cloud Lite 🌩️: Seamless On-Demand Forensic Scanning Made Easy - apply YARA + Sigma + IOCs - it's free - many more features upcoming Blog 📘 nextron-systems.com/2023/10/30/int… Release Session 📺 youtu.be/ApeXFnFkKZg Register for Free ⚡️ thorcloud-lite.nextron-systems.com/ui/register?ut…
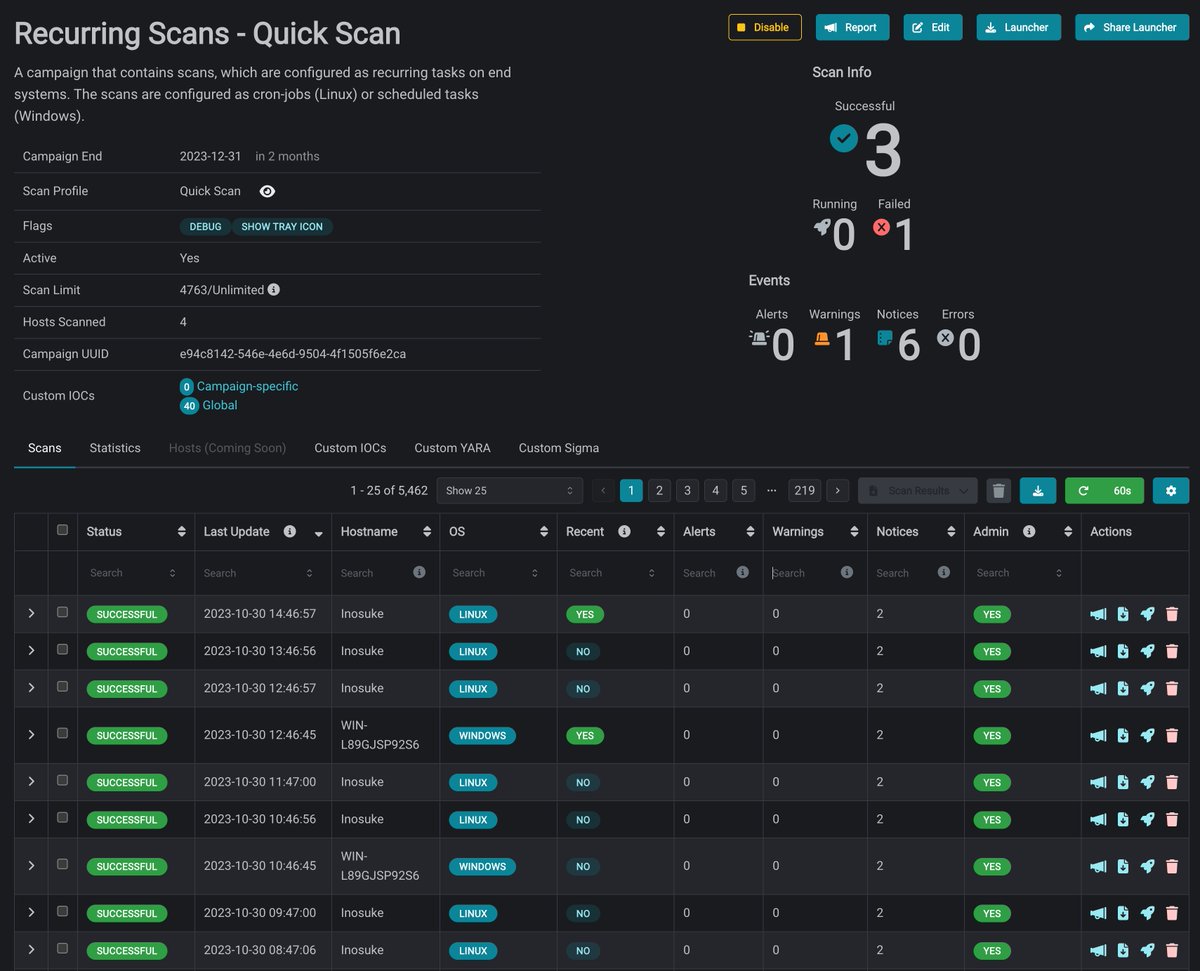

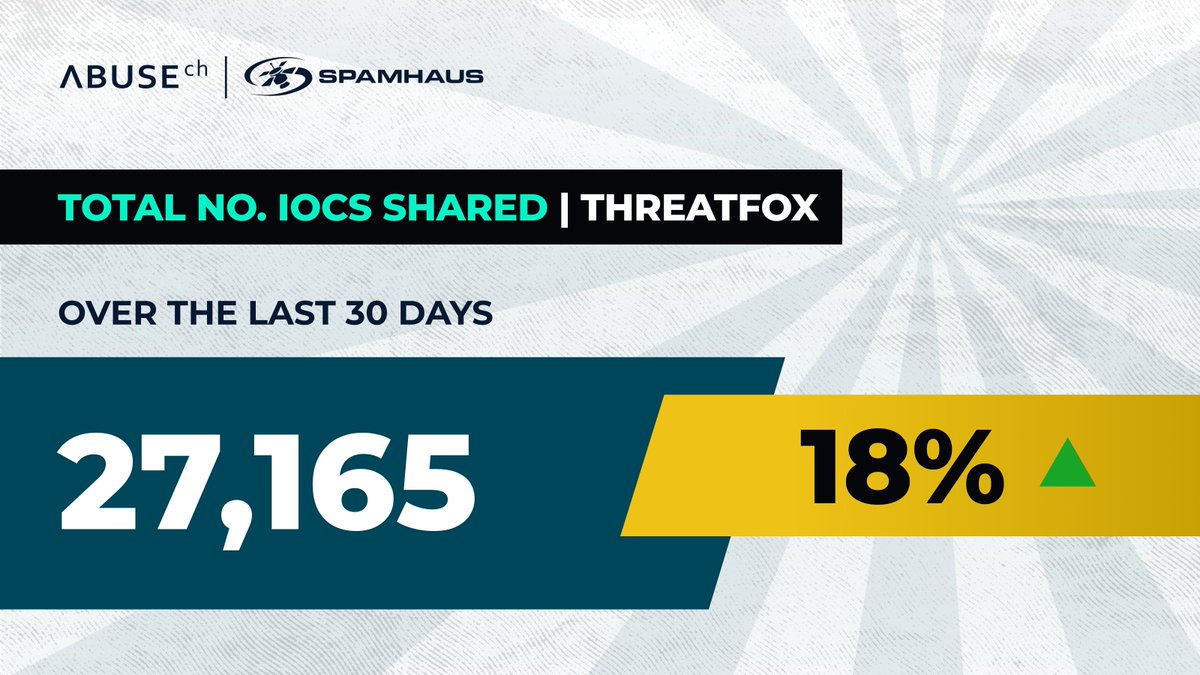
Over the past 30 days, our community shared 27,165 new #IOCs on ThreatFox 🦊 — an 18% increase from the previous month.👏 Huge shoutout to 'juroots', our top contributor with 2,746 IOCs submitted. 💀The most-shared malware family (or in this case framework)? Clearfake, with…
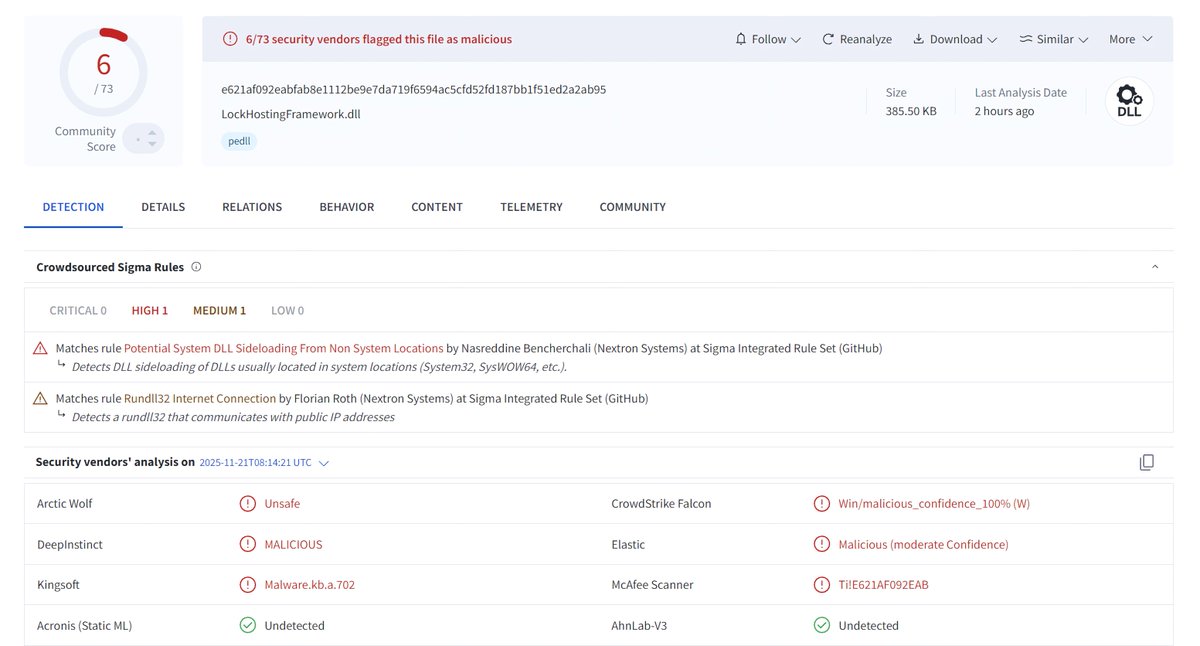
In the new #Latrodecuts version, the authors switched to AES-256 for string encryption and decryption. I provide this #IDAPython script, which you can use to extract and decrypt the strings, quickly get up to speed, and get #IOCs. github.com/Blu3Eye/Malwar…

Aprende a analizar el servidor del troyano #LarryLurexRAT con #4n4lDetector v.2.8. Además, abordo la extracción de #IOCs, #EDR y la recolección de información previa a un ejercicio de #reversing de #malware. Descarga: github.com/4n0nym0us/4n4l… Vídeo: youtube.com/watch?v=-zCPk_…

#botnet #iocs! 430 duplicates which means they have been online for a while. and 49 new malware urls! Malware urls/IOC's can be found here: pastebin.com/0QTEJvkX urlhaus.abuse.ch/browse/

👾 #Salty2FA is a #PhaaS that hijacks sessions and steals Microsoft 365 credentials, bypassing six MFA types. ⚠️ It uses Cloudflare Turnstile, heavy obfuscation and real-time credential validation to evade detection. See analysis & gather #IOCs: any.run/malware-trends…

Catch the unknowns. 🕵️♂️ Understand the attackers. Be ready. 🛡️ CATALYST delivers fresh IOCs & never-before-seen TTPs, linked to threat clusters. Level up your threat intel! 👉 Try it: catalyst.prodaft.com/welcome #ThreatIntel #Malware #IOCs #TTPs

🚨 #DragonForce #ransomware is built to paralyze organizations It wipes backups, disables recovery, spreads across networks, and encrypts everything with no way back. Victims are left facing multimillion-dollar ransom demands See analysis & gather #IOCs: any.run/malware-trends…

I had a blast at the @Gartner_inc #iocs event this week! Thanks to the whole @SADA crew and shout out to @milesward for the awesome tag team presentation on what we’re seeing in the #genai space!

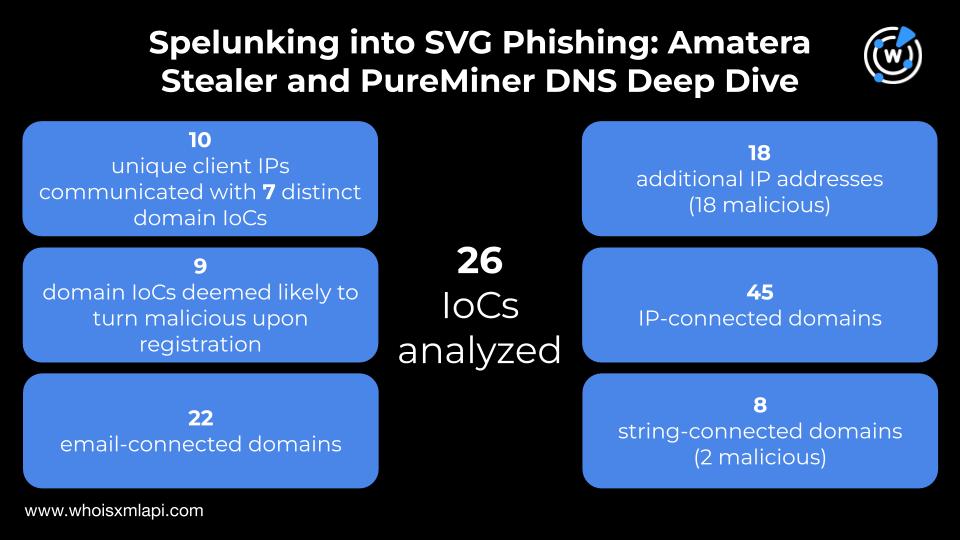
Nine of the 25 domains identified as #IoCs for the #AmateraStealer and #PureMiner SVG #phishing campaign were deemed likely to turn malicious 14–105 days before they were dubbed as such. We also uncovered 90+ new artifacts, 20 are already considered malicious. Get the lowdown in:…
Join the @Yugabyte team in Las Vegas on Dec 9-11 at @Gartner_inc #IOCS, the premier conference for infrastructure, operations, and cloud leaders.🔥 Visit our experts at the Yugabyte booth to win cool prizes and discover how #AI-ready, #multimodal, #distributed, #YugabyteDB can…

Manual rule writing? Out. Our Seamless IOC Ingestion feature auto-imports all threat intel indicators. No manual config. Deployment time: Hours ➡️ Minutes. Read more: hubs.la/Q03SgCH50 #ThreatIntelligence #IOCs #SecurityAutomation #SOCEfficiency #RuleWriting #Cybersecurity
More sex shop themed Cyber Stealer panels: 69.30.247[.]233:3004 iloveboats9[.]vip @solostalking @500mk500 #InfoSec #malware #iocs
![AUZombie's tweet image. More sex shop themed Cyber Stealer panels:
69.30.247[.]233:3004
iloveboats9[.]vip
@solostalking @500mk500
#InfoSec #malware #iocs](https://pbs.twimg.com/media/G4qmqjEa4AAyV4I.png)
🚨 Hunt Alert 🚨 Pivoted from the #SlowTempest #IOCs and uncovered a peculiar HTML page—only ~140 results globally, mainly in Hong Kong/China 🇭🇰🇨🇳. Most common port: 8888, potentially a admin/login panel. Thanks @MichalKoczwara for your input! Notably, the HTML page pivots…

In case you are a medical institution, it may be worth blocking this in your firewall or if you're using the CMS features, at least search internet traffic logs for the IP 202.114.4[.]119 #iocs
![craiu's tweet image. In case you are a medical institution, it may be worth blocking this in your firewall or if you're using the CMS features, at least search internet traffic logs for the IP 202.114.4[.]119 #iocs](https://pbs.twimg.com/media/GioS-TNWMAA0fxV.jpg)
![craiu's tweet image. In case you are a medical institution, it may be worth blocking this in your firewall or if you're using the CMS features, at least search internet traffic logs for the IP 202.114.4[.]119 #iocs](https://pbs.twimg.com/media/GioTFuJXsAAPC8p.png)
In the new #Latrodecuts version, the authors switched to AES-256 for string encryption and decryption. I provide this #IDAPython script, which you can use to extract and decrypt the strings, quickly get up to speed, and get #IOCs. github.com/Blu3Eye/Malwar…

#GlassCage zero-click attack IOS Once triggered, the chain escalates to full root access via a combination of WebKit RCE (CVE-2025-24201) and Core Media kernel exploitation (CVE-2025-24085).#IOCs weareapartyof1.substack.com/p/glass-cage-z…


Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️ /18.117.173[.]7 /kennedywilsoninc[.]com #IoCs #ScatteredSpider | #ThreatHunting #Censys @500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H
![soursec_'s tweet image. Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️
/18.117.173[.]7
/kennedywilsoninc[.]com
#IoCs #ScatteredSpider | #ThreatHunting #Censys
@500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H](https://pbs.twimg.com/media/GvmoDBYWYAEE1-8.jpg)
![soursec_'s tweet image. Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️
/18.117.173[.]7
/kennedywilsoninc[.]com
#IoCs #ScatteredSpider | #ThreatHunting #Censys
@500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H](https://pbs.twimg.com/media/GvmoLXCbsAApOs5.jpg)
![soursec_'s tweet image. Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️
/18.117.173[.]7
/kennedywilsoninc[.]com
#IoCs #ScatteredSpider | #ThreatHunting #Censys
@500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H](https://pbs.twimg.com/media/GvmoMRsbsAQtmyl.jpg)
![soursec_'s tweet image. Possible Scattered Spider Infra Targeting @KennedyWilson 🕷️
/18.117.173[.]7
/kennedywilsoninc[.]com
#IoCs #ScatteredSpider | #ThreatHunting #Censys
@500mk500 @MichalKoczwara @malwrhunterteam @skocherhan @1ZRR4H](https://pbs.twimg.com/media/GvmoM8FbsAA-FM7.jpg)
Very interesting sample. Targeting IR. b11a32e53602ea984a8608bead21c301c1bc3f2482b4cc9c69bf6876afbdb266 2 Stage > hxxps://networking.s3.ir-thr-at1[.]arvanstorage[.]ir/Payload.bat #maldoc #IoCs
![DmitriyMelikov's tweet image. Very interesting sample. Targeting IR.
b11a32e53602ea984a8608bead21c301c1bc3f2482b4cc9c69bf6876afbdb266
2 Stage > hxxps://networking.s3.ir-thr-at1[.]arvanstorage[.]ir/Payload.bat
#maldoc #IoCs](https://pbs.twimg.com/media/GFuUr2IWQAAIc3u.png)
![DmitriyMelikov's tweet image. Very interesting sample. Targeting IR.
b11a32e53602ea984a8608bead21c301c1bc3f2482b4cc9c69bf6876afbdb266
2 Stage > hxxps://networking.s3.ir-thr-at1[.]arvanstorage[.]ir/Payload.bat
#maldoc #IoCs](https://pbs.twimg.com/media/GFuVQauXkAE_iDi.png)
#botnet #iocs! 430 duplicates which means they have been online for a while. and 49 new malware urls! Malware urls/IOC's can be found here: pastebin.com/0QTEJvkX urlhaus.abuse.ch/browse/

Our latest advisory has #TTPs, #IOCs, and recommended mitigations to protect against exploitation of CVE-2023-26360, a vulnerability in Adobe ColdFusion that was exploited for initial access to fed gov’t servers. Read advisory: go.dhs.gov/oCD

Catch the unknowns. 🕵️♂️ Understand the attackers. Be ready. 🛡️ CATALYST delivers fresh IOCs & never-before-seen TTPs, linked to threat clusters. Level up your threat intel! 👉 Try it: catalyst.prodaft.com/welcome #ThreatIntel #Malware #IOCs #TTPs

At the recently held CYDES 2025, we disclosed #APT group #NightEagle (APT-Q-95). This threat group has been targeting high-tech industries for a long time, including chip semiconductors, AI/GPT and other fields. Actors used an unknown Exchange exploit chain. PPT: #IOCs #APT




🚨 Phishing Alert: We’ve spotted fake timesheet report emails leading to the Tycoon 2FA phishing kit—now abusing Pinterest visual bookmarks as intermediaries. Stay vigilant! 🔍 #IoCs: pin[.]it/7FwOYIHSO 8a[.]nextwavxe[.]ru/zz4bnhS7UpYZhbV4xqA/ #CyberSecurity #Phishing…
![SpiderLabs's tweet image. 🚨 Phishing Alert: We’ve spotted fake timesheet report emails leading to the Tycoon 2FA phishing kit—now abusing Pinterest visual bookmarks as intermediaries.
Stay vigilant! 🔍
#IoCs:
pin[.]it/7FwOYIHSO
8a[.]nextwavxe[.]ru/zz4bnhS7UpYZhbV4xqA/
#CyberSecurity #Phishing…](https://pbs.twimg.com/media/GkAQOT1XkAAHpqn.jpg)
Tracking #Candiru’s DevilsTongue #Spyware in Multiple Countries #IOCs Update github.com/blackorbird/AP…


ClickFix IoC : hrdepartments[.]org #IoCs #ClickFix | #Censys #ThreatHunting cc : @500mk500 @skocherhan @MichalKoczwara @malwrhunterteam @1ZRR4H
![soursec_'s tweet image. ClickFix IoC :
hrdepartments[.]org
#IoCs #ClickFix | #Censys #ThreatHunting
cc : @500mk500 @skocherhan @MichalKoczwara @malwrhunterteam @1ZRR4H](https://pbs.twimg.com/media/Gv4bKk7WcAAnici.jpg)
![soursec_'s tweet image. ClickFix IoC :
hrdepartments[.]org
#IoCs #ClickFix | #Censys #ThreatHunting
cc : @500mk500 @skocherhan @MichalKoczwara @malwrhunterteam @1ZRR4H](https://pbs.twimg.com/media/Gv4bPuvWYAAvTpU.jpg)
La próxima versión de #4n4lDetector será la herramienta que más nos ayudará en la recolección de #IOCs de #malware... no tengo dudas. Se han revisado y mejorado todos los módulos que la componen. Gracias a Sandra Badia Gimeno por la realización del nuevo logo de la herramienta.😘

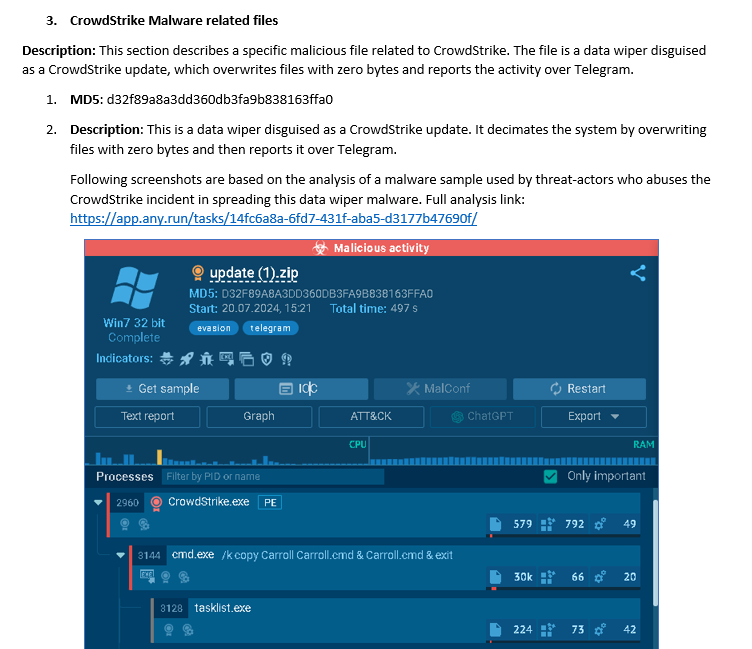
This report outlines #iocs related to #CrowdStrike incident collected by @DarkEntryAms team, including malware distribution related hostnames, and mitigation plan to help organizations protect their systems. Full report link: lnkd.in/dAGNKXSG
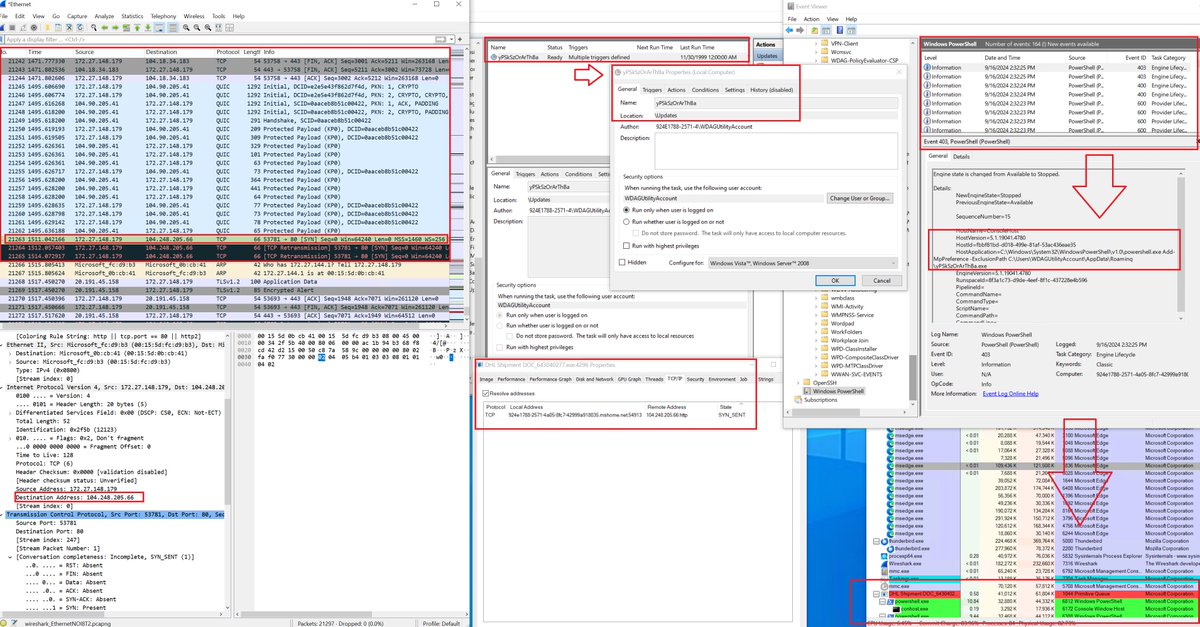
One more sample of #spearphishing gz attachment reaching #Lokibot C2 104.248.205.66:80 DHL Shipment DOC_643040277.gz >DHL Shipment DOC_643040277.exe > PowerShell > schtasks.exe > yPSkSzOrArThBa.exe The new #IOCs below. Ref: threatfox-api.abuse.ch/ioc/1323367/ @NDA0E

Something went wrong.
Something went wrong.
United States Trends
- 1. Auburn 37.3K posts
- 2. Bama 27.7K posts
- 3. Duke 29.1K posts
- 4. #SurvivorSeries 173K posts
- 5. Miami 116K posts
- 6. Stockton 14.6K posts
- 7. Virginia 48.1K posts
- 8. Cam Coleman 1,689 posts
- 9. Austin Theory 4,245 posts
- 10. Ole Miss 34.1K posts
- 11. Iron Bowl 15.2K posts
- 12. ACC Championship 7,324 posts
- 13. #RollTide 5,746 posts
- 14. Lane Kiffin 42.2K posts
- 15. Ty Simpson 3,689 posts
- 16. Cooper Flagg 5,145 posts
- 17. Notre Dame 23.4K posts
- 18. Ryan Williams 1,695 posts
- 19. Seth 20.7K posts
- 20. Stanford 8,375 posts