#browsersecurity search results
Are your browser extensions putting your online security at risk? Discover the potential dangers and how to safeguard your digital life in our latest article. onwardcs.com/news/online-se… #Cybersecurity #OnlineSafety #BrowserSecurity
Your biggest SaaS risk might be sitting inside your browser. 🧩 Even one unvetted extension can steal data or bypass security. Here’s how to spot and remove them before they cause damage 👇 🔗 bit.ly/3JtJ0C9 #CyberSecurity #DataProtection #BrowserSecurity #SpinAI

Corrupting the data an AI system learns from so it behaves incorrectly or makes unsafe decisions. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX
Use a privacy-focused browser with anti-tracking. Standard browsers log and leak far too much data. #BrowserSecurity #AntiTracking #PrivacyTools
Join experts from Google and Promevo on November 19 at 1 PM EST for an exclusive InformationWeek webinar exploring how Chrome Enterprise Premium transforms your browser into a secure, zero-trust perimeter. hubs.ly/Q03PNXr20 #ChromeEnterprise #ZeroTrust #BrowserSecurity

AI browser agents are here and so are their cracks. When a browser‑agent can act on your behalf it also gains power over your data. Hidden commands in webpages can hijack them. Security must catch up before agents take over your workflow. #AI #CyberRisk #BrowserSecurity

As part of our research on the architectural vulnerabilites of AI browsers, we reached out to CISOs to get their perspective, Tom Le, CISO at Gap shares his. Read our full research: hubs.la/Q03NswMT0 #cybersecurity #browsersecurity #enterprisesecurity

🎓 Students love browser extensions. Hackers do too. Our VP of Engineering Sergiy Balynsky explains how unmonitored add-ons expose K-12 data to massive risk, and what to do about it. 📖 Read the blog: → bit.ly/4hTjWkO #CyberSecurity #K12Security #BrowserSecurity

Surprised? Some Chrome themes carry malware that tracks your activity and injects ads. Always check developer reviews. Even aesthetic add-ons can be risky. #BrowserSecurity #DOITCQuiz

🪝 BeEF — Browser Exploitation Framework BeEF (Browser Exploitation Framework) is a research tool that demonstrates browser-based attack vectors by hooking browsers and running controlled modules to assess client-side security. #BeEF #BrowserSecurity #AppSec #EthicalHacking




The collection of data you leave online through searches, clicks, and activity, which can reveal personal information. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Some extensions secretly track your activity or steal data. Regularly review and remove what you don’t use. #BrowserSecurity #DataProtection #DOITC

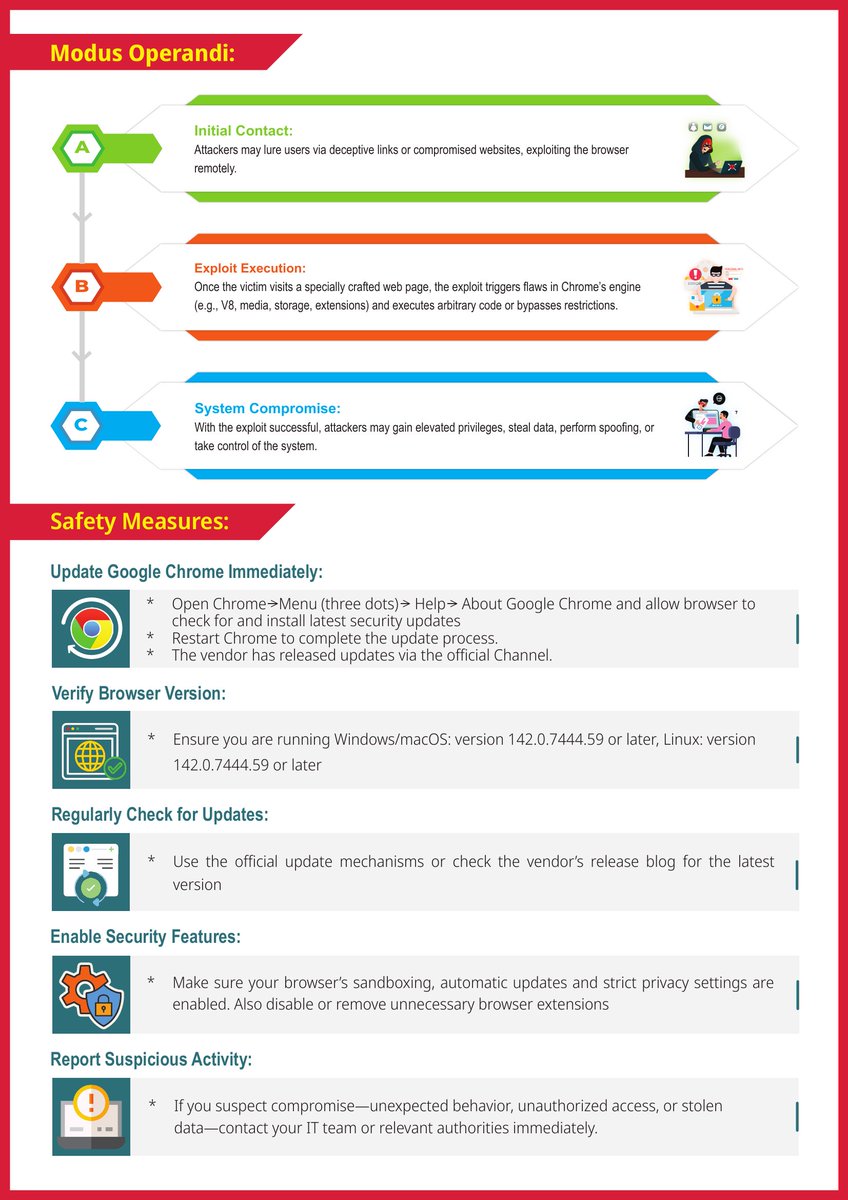
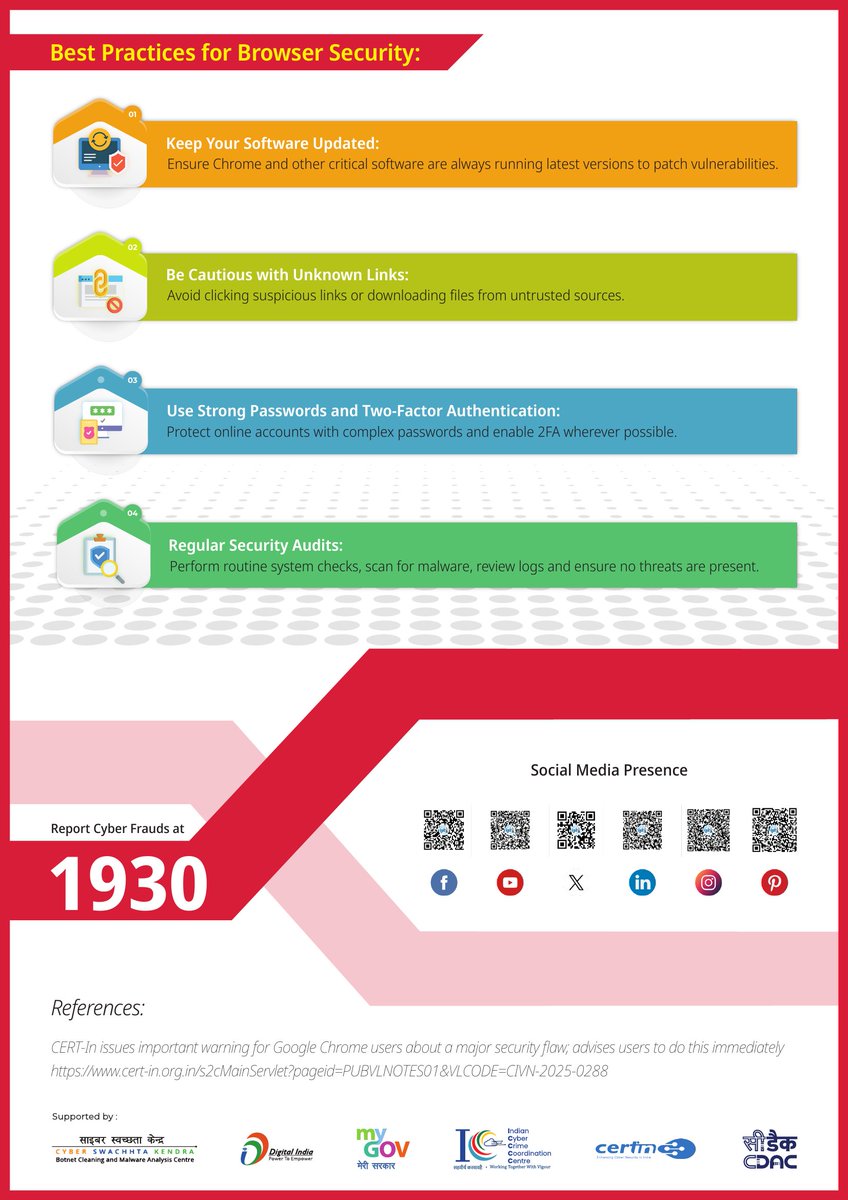
#CyberAlert ⚠️ Urgent Alert for Google Chrome Users! Major browsing vulnerabilities have been detected hackers could exploit them to steal your data update your browser immediately to stay safe online 💻 #CyberSafety #BrowserSecurity #GoogleChrome #DigitalSafety #CyberAwareness…

A set of tools and practices that protect your browser from malware, phishing, and data leaks. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

📸 End of the day, but already deep in the numbers: our Chief of Staff Mridula Kapur reviewing booth lead data after an amazing day at Black Hat — packed with conversations, sharp questions, and strong interest in our BDR solution. #cybersecurity #browsersecurity…

A security method where websites load in a remote, contained environment so harmful content never reaches your device. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Browser add-ons designed to steal data, track activity, or inject harmful code through websites. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Avoid autofill on sensitive forms. Autofill can be hijacked by hidden form fields. #FormHacking #AutofillExploits #BrowserSecurity

Jeff Moore, CISO, didn’t miss a beat in our rapid-fire Q&A with Aleksandra - and we have to say, he handled it like a pro 💪🏻 #cybersecurity #browsersecurity #enterprisesecurity #BlackHat
Are your browser extensions putting your online security at risk? Discover the potential dangers and how to safeguard your digital life in our latest article. onwardcs.com/news/online-se… #Cybersecurity #OnlineSafety #BrowserSecurity
These new AI browsers (Comet, ChatGPT Atlas) look 🔥 but... are they secure enough for sensitive info? Maybe incognito mode or just stick with Chrome is the safer play 👌 #AIBrowser #BrowserSecurity #Privacy #Tech

A critical memory flaw in Firefox’s WebAssembly GC (CVE-2025-13016) exposed 180M users to arbitrary code execution via malicious modules. Highlights need for AI-driven security and patch management. #WebAssemblyBug #BrowserSecurity #USA ift.tt/3MKY6zh
hendryadrian.com
Critical Firefox Bug Leaves 180M Users Exposed | eSecurity Planet
A memory flaw in Firefox's WebAssembly implementation remained hidden for six months, affecting over 180 million users and risking arbitrary code execution. This incident highlights the importance of...
Browser extensions can be misused as backdoors or privilege escalation tools. Learn why and how to stay safe. redsecuretech.co.uk/blog/post/brow… #CyberSecurity #BrowserSecurity #Extensions #Malware #InfoSec #ThreatIntel

Browsers are now the frontline of enterprise risk, says @LayerxSecurity's Or Eshed in this commentary. Shadow #AI, risky extensions, and hidden data flows demand a real strategy. #BrowserSecurity #cybersecurity #infosec #CISO #ITsecurity bit.ly/4pkxKqO
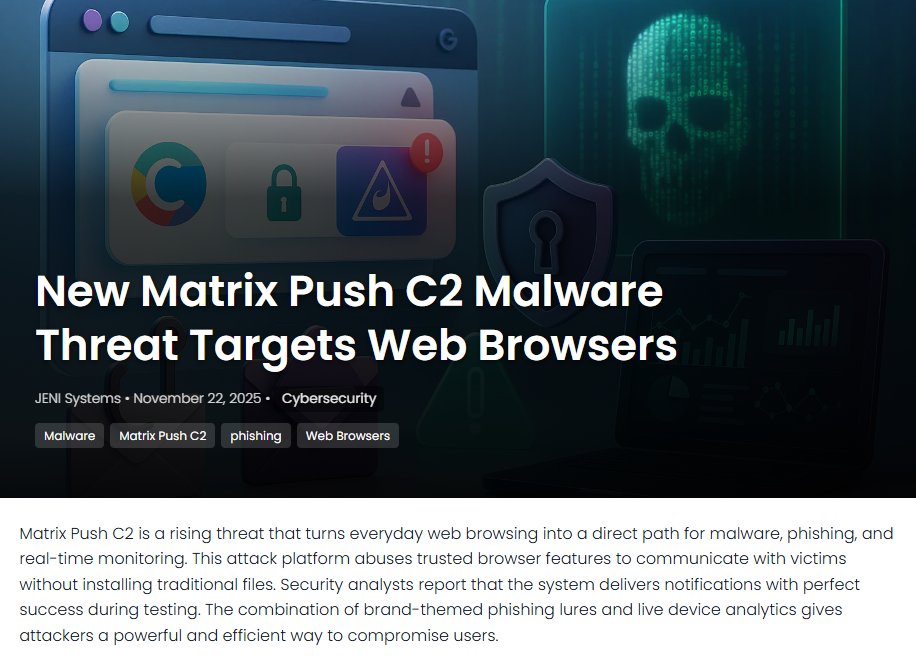
Matrix Push C2 hides command-and-control traffic inside browser notifications — turning everyday alerts into covert channels. Even pop-ups can lie. 🔔🕵️♂️ #C2Techniques #BrowserSecurity buff.ly/ZUqWpmZ
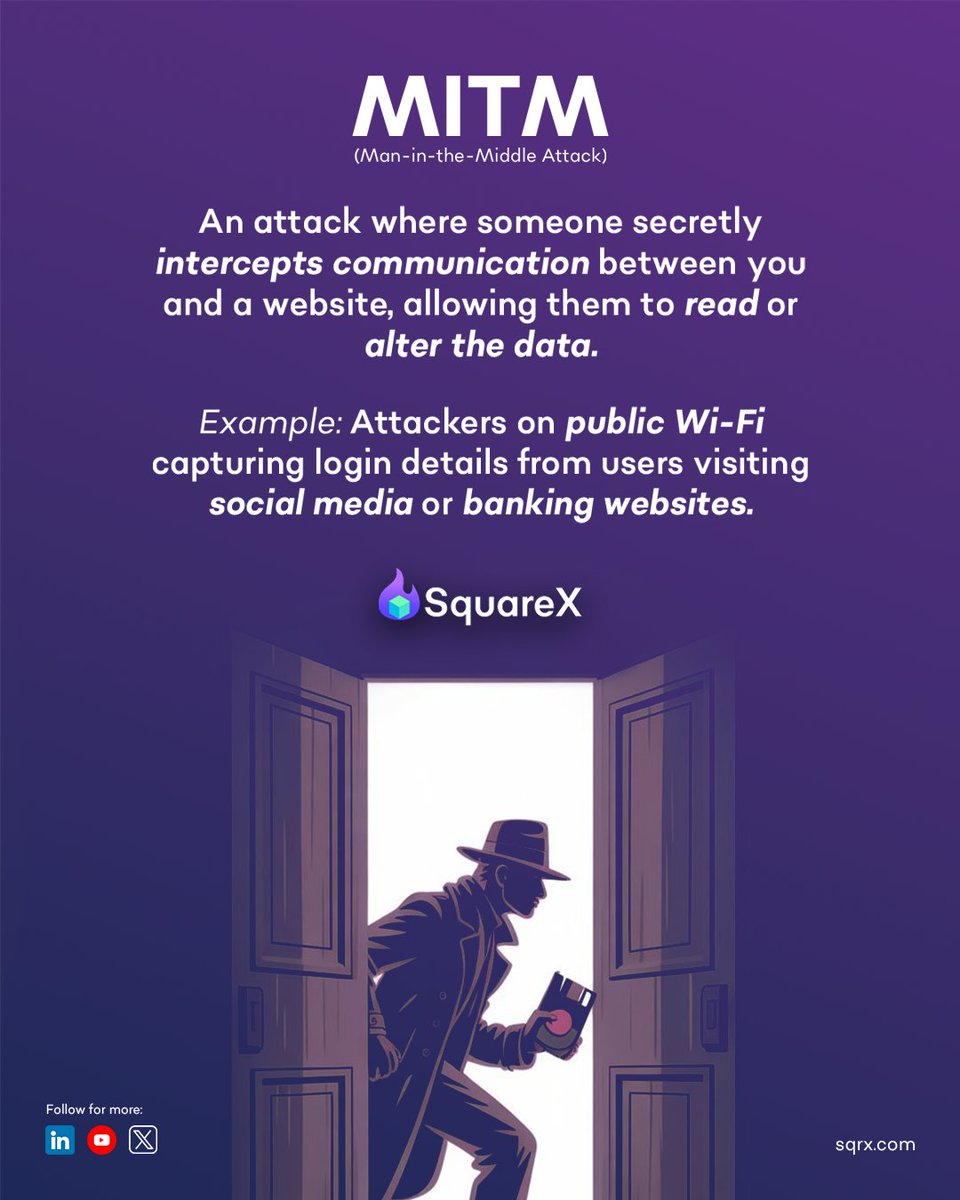
Man In The Middle - A hacker could use public WiFi to steal your credentials. Beware! #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX
Browsers are now the frontline of enterprise risk, says @LayerxSecurity's Or Eshed in this commentary. Shadow #AI, risky extensions, and hidden data flows demand a real strategy. #BrowserSecurity #cybersecurity #infosec #CISO #ITsecurity scworld.com/perspective/se…
Browsers are now the frontline of enterprise risk, says @LayerxSecurity's Or Eshed in this commentary. Shadow #AI, risky extensions, and hidden data flows demand a real strategy. #BrowserSecurity #cybersecurity #infosec #CISO #ITsecurity bit.ly/4pkxKqO
Matrix Push C2 hides inside trusted browser alerts and pushes fileless phishing and tracking that hits fast and feels unnerving. jenisystems.com/matrix-push-c2… #matrixpushc2 #browsersecurity #filelessmalware
Browser-based attacks are rising through malicious extensions that steal cookies, session tokens and passwords. Only install trusted add-ons, review permissions, and regularly audit what’s active in your browser. #CyberSecurity #BrowserSecurity #HackingTrends

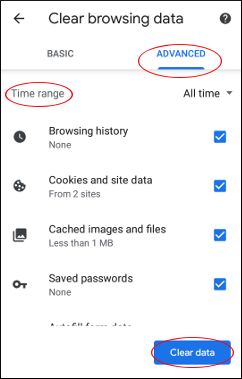
🧹 Clear your browsing data and cookies regularly. #BrowserSecurity #CyberHygiene #StaySafeOnline #cybersecurity
A security method where websites load in a remote, contained environment so harmful content never reaches your device. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Browsers are now the frontline of enterprise risk, says @LayerxSecurity's Or Eshed in this commentary. Shadow #AI, risky extensions, and hidden data flows demand a real strategy. #BrowserSecurity #cybersecurity #infosec #CISO #ITsecurity bit.ly/4pkxKqO
📌 Simple steps to lock down your browser at work 1. Track what’s actually being used 2. Control extensions & AI add-ons 3. Lock down logins & sessions Learn more from our Cybersecurity Awareness Training Community at: skool.com/techframework. #Cybersecurity #BrowserSecurity
Browser add-ons designed to steal data, track activity, or inject harmful code through websites. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Chrome exploit is live and on CISA’s radar. CVE-2025-13223 lets attackers run code via V8 engine flaws—translation: your browser could become their playground. SMBs, update Chrome now or risk getting burned. securityaffairs.com/184856/hacking… #CyberSecurity #BrowserSecurity
Your biggest SaaS risk might be sitting inside your browser. 🧩 Even one unvetted extension can steal data or bypass security. Here’s how to spot and remove them before they cause damage 👇 🔗 bit.ly/3JtJ0C9 #CyberSecurity #DataProtection #BrowserSecurity #SpinAI

Join experts from Google and Promevo on November 19 at 1 PM EST for an exclusive InformationWeek webinar exploring how Chrome Enterprise Premium transforms your browser into a secure, zero-trust perimeter. hubs.ly/Q03PNXr20 #ChromeEnterprise #ZeroTrust #BrowserSecurity

Your browser is your gateway to the online landscape, it must be protected ! Follow these tips to make your browsing experience safe and secure. #DoITC #BrowserSecurity #BeCyberAware #tipsandtricks

Some extensions secretly track your activity or steal data. Regularly review and remove what you don’t use. #BrowserSecurity #DataProtection #DOITC

Surprised? Some Chrome themes carry malware that tracks your activity and injects ads. Always check developer reviews. Even aesthetic add-ons can be risky. #BrowserSecurity #DOITCQuiz

Engaging conference session on browser security, featuring insightful insights and practical demonstrations. Grateful for the opportunity to learn from experts in the field. @imnarendrabhati @bsidesodisha #Cybersecurity #BrowserSecurity #InfoSec"

🎓 Students love browser extensions. Hackers do too. Our VP of Engineering Sergiy Balynsky explains how unmonitored add-ons expose K-12 data to massive risk, and what to do about it. 📖 Read the blog: → bit.ly/4hTjWkO #CyberSecurity #K12Security #BrowserSecurity

🎊 Delighted to announce @vivekramac; founder of @getsquarex as our Closing Note speaker for #NullconBerlin2024 🎊 Since secure web gateways are failing to detect a larger number of attacks, the question 'What comes next?' arises Link: nullcon.net/berlin-2024/sp… #browsersecurity

Corrupting the data an AI system learns from so it behaves incorrectly or makes unsafe decisions. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

AI browser agents are here and so are their cracks. When a browser‑agent can act on your behalf it also gains power over your data. Hidden commands in webpages can hijack them. Security must catch up before agents take over your workflow. #AI #CyberRisk #BrowserSecurity

As part of our research on the architectural vulnerabilites of AI browsers, we reached out to CISOs to get their perspective, Tom Le, CISO at Gap shares his. Read our full research: hubs.la/Q03NswMT0 #cybersecurity #browsersecurity #enterprisesecurity

Use a privacy-focused browser with anti-tracking. Standard browsers log and leak far too much data. #BrowserSecurity #AntiTracking #PrivacyTools

From speaking about Browsers till late night with @ericlaw @HomeSen @Qab and @posidron to getting to speak about the Webviews to hack the applications. Thanks to Dameon Welch for giving me this opportunity for All about CPX 2024, Bangkok, Thailand 🇹🇭 #CPX2024 #BrowserSecurity



The #MenloSecurity team is thrilled to be back at Infosecurity Europe this year, and we can't wait to connect with you. If you're looking to tackle today's most sophisticated cyber threats and explore the future of #browsersecurity, make Booth B75 your first stop! 📍 Visit us…

Thanks for the great roundtable discussion, Bryson Bort, Ken Kato, Ajit Hatti, and Sebastian Cesario! #cybersecurity #browsersecurity #RSAC25 #RSA @AdversaryVillag @abhijithbr

The collection of data you leave online through searches, clicks, and activity, which can reveal personal information. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

When Browsers Become the Attack Surface: Rethinking Security for Scattered Spider dlvr.it/TNNqsc #CyberSecurity #WebSecurity #BrowserSecurity #ScatteredSpider #DataProtection

Something went wrong.
Something went wrong.
United States Trends
- 1. Thanksgiving 359K posts
- 2. Trumplican 1,888 posts
- 3. Fani Willis 4,260 posts
- 4. Golesh 1,007 posts
- 5. Hong Kong 69.4K posts
- 6. #wednesdaymotivation 5,999 posts
- 7. #Wednesdayvibe 3,110 posts
- 8. Good Wednesday 34.2K posts
- 9. Mora 22.7K posts
- 10. Ruth 14K posts
- 11. Gretzky N/A
- 12. Karoline Leavitt 27.6K posts
- 13. #puebloenbatallayvictoria 2,914 posts
- 14. #StrangerThings5 19K posts
- 15. #BurnoutSyndromeSeriesEP1 251K posts
- 16. Colorado State 3,881 posts
- 17. Nuns 9,489 posts
- 18. Ribs 11.5K posts
- 19. Elijah Moore N/A
- 20. BYOB N/A


































