#browsersecurity kết quả tìm kiếm
Your biggest SaaS risk might be sitting inside your browser. 🧩 Even one unvetted extension can steal data or bypass security. Here’s how to spot and remove them before they cause damage 👇 🔗 bit.ly/3JtJ0C9 #CyberSecurity #DataProtection #BrowserSecurity #SpinAI

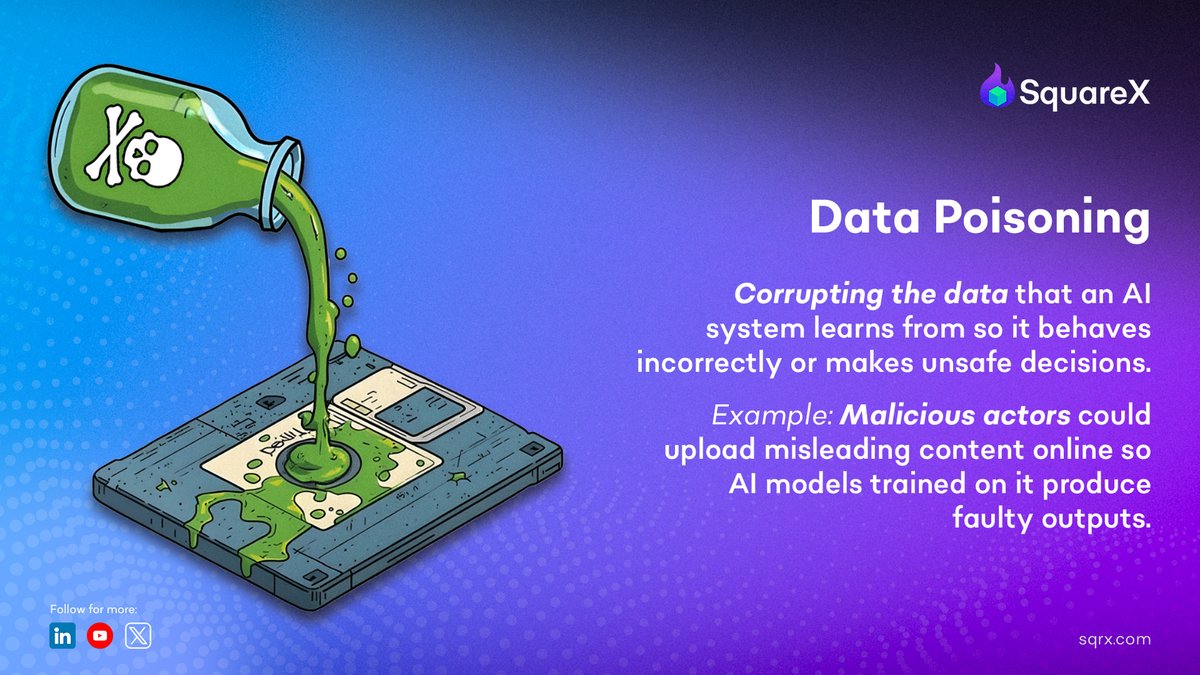
Corrupting the data an AI system learns from so it behaves incorrectly or makes unsafe decisions. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX
Browser add-ons designed to steal data, track activity, or inject harmful code through websites. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

The collection of data you leave online through searches, clicks, and activity, which can reveal personal information. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Shadow AI in browsers creates hidden risks with unmanaged GenAI tools gaining elevated permissions to exfiltrate data. Key defenses include session monitoring, AI-use policies, and identity controls. #EnterpriseAI #BrowserSecurity #US ift.tt/xJzIGeY
A tracking method that identifies you using unique browser and device traits, even without cookies. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

A set of tools and practices that protect your browser from malware, phishing, and data leaks. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Kampanye ShadyPanda mengungkap celah besar di sistem review ekstensi Chrome & Edge. Ekstensi yang awalnya aman bisa berubah jadi spyware lewat update kecil yang tak diawasi. Baca selengkapnya: androidponsel.com/kenapa-ekstens… #CyberSecurity #BrowserSecurity #Chrome #Edge

Attackers manipulate an AI system by feeding it crafted prompts that override its original instructions. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

A security method where websites load in a remote, contained environment so harmful content never reaches your device. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Join experts from Google and Promevo on November 19 at 1 PM EST for an exclusive InformationWeek webinar exploring how Chrome Enterprise Premium transforms your browser into a secure, zero-trust perimeter. hubs.ly/Q03PNXr20 #ChromeEnterprise #ZeroTrust #BrowserSecurity

🎓 Students love browser extensions. Hackers do too. Our VP of Engineering Sergiy Balynsky explains how unmonitored add-ons expose K-12 data to massive risk, and what to do about it. 📖 Read the blog: → bit.ly/4hTjWkO #CyberSecurity #K12Security #BrowserSecurity

In 2024, scammers used deepfaked video calls of executives to trick companies like Arup into transferring millions in fake transactions. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

AI browser agents are here and so are their cracks. When a browser‑agent can act on your behalf it also gains power over your data. Hidden commands in webpages can hijack them. Security must catch up before agents take over your workflow. #AI #CyberRisk #BrowserSecurity

As part of our AI Sidebar Spoofing research, we gathered insights from leading security experts. Tin Zaw, Former Project Leader and Co-Author of OWASP Automated Threats Project and Handbook, weighs in. #cybersecurity #browsersecurity #enterprisesecurity

Use a privacy-focused browser with anti-tracking. Standard browsers log and leak far too much data. #BrowserSecurity #AntiTracking #PrivacyTools
🪝 BeEF — Browser Exploitation Framework BeEF (Browser Exploitation Framework) is a research tool that demonstrates browser-based attack vectors by hooking browsers and running controlled modules to assess client-side security. #BeEF #BrowserSecurity #AppSec #EthicalHacking




Millions use Grammarly daily, but is it secure for your sensitive data? Learn more in this detailed risk analysis blog: #BrowserSecurity #BrowserExtensions #DataPrivacy #Grammarly #ITSecurity #Compliance

As part of our research on the architectural vulnerabilites of AI browsers, we reached out to CISOs to get their perspective, Tom Le, CISO at Gap shares his. Read our full research: hubs.la/Q03NswMT0 #cybersecurity #browsersecurity #enterprisesecurity

Shadow AI in browsers creates hidden risks with unmanaged GenAI tools gaining elevated permissions to exfiltrate data. Key defenses include session monitoring, AI-use policies, and identity controls. #EnterpriseAI #BrowserSecurity #US ift.tt/xJzIGeY
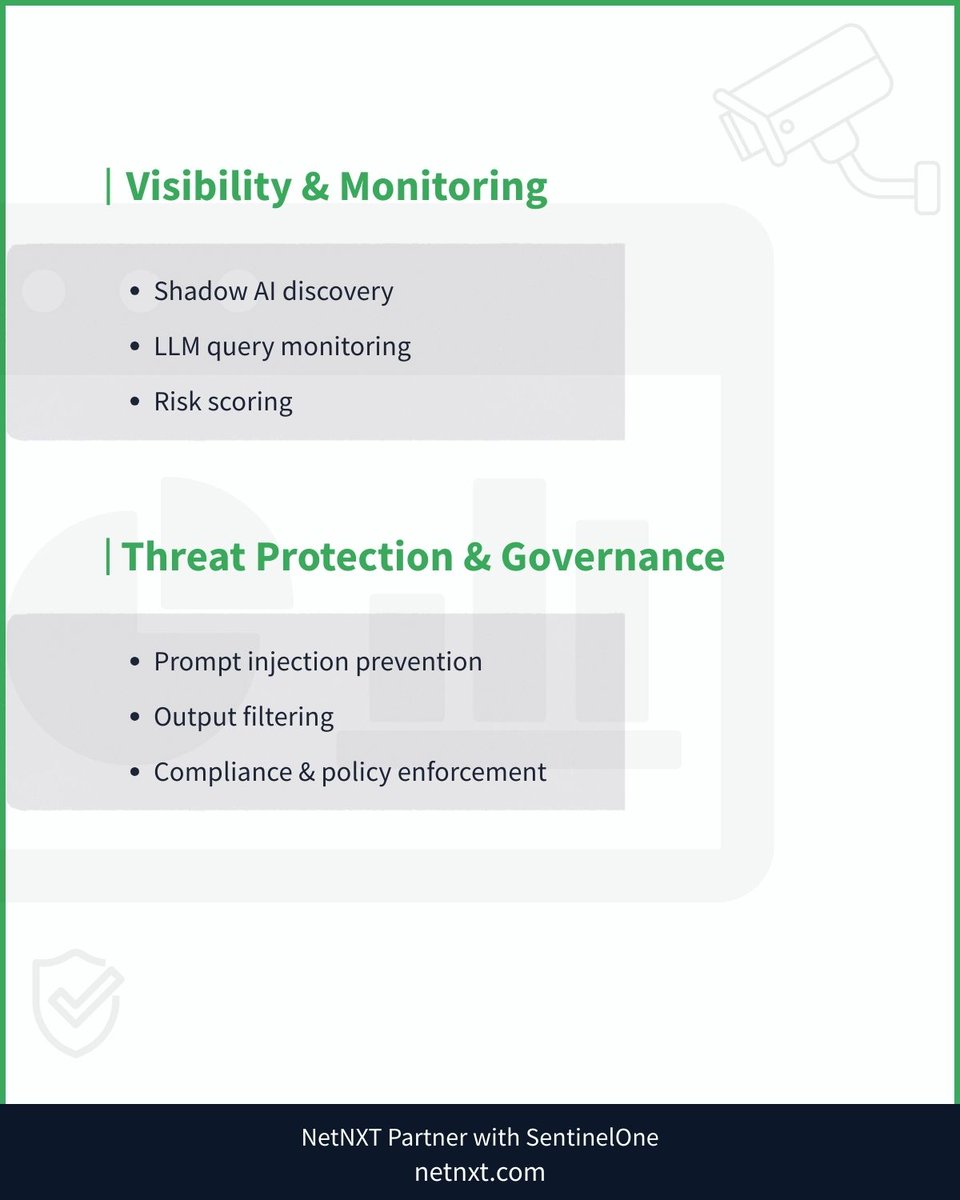
Your browser is now one of the biggest entry points for attackers. Hidden scripts, token leaks, risky extensions, weak sandboxing all expand your attack surface. Need an enterprise-ready hardening checklist. Connect Today- netnxt.com/contact?utm_so… #browsersecurity #cybersecurity

Chrome, Edge Extensions Caught Tracking Users تحقيقات تكشف إضافات في Chrome وEdge كانت تتعقب المستخدمين وتضيف أبواباً خلفية، ما يثير مخاوف حول خصوصية التصفح. #BrowserSecurity #Privacy #Chrome #Edge #CyberAlert

To check if your Chrome or Edge browser has any of the malicious extensions, go to the extensions page and look for any suspicious or unfamiliar ones. Google has removed the extensions, but Microsoft's response has been slower. #BrowserSecurity #MaliciousExtensions #CyberSecurity
Browser extensions can be hijacked for supply-chain attacks. Learn how attackers exploit updates and how to secure your systems. redsecuretech.co.uk/blog/post/supp… #CyberSecurity #SupplyChainAttack #BrowserSecurity #InfoSec #ExtensionMalware #ThreatDetection
Five Chrome extensions dormant 7 years turned spyware on ~4 M devices—sleeper add‑ons can flip silently. Enforce extension whitelists and watch outbound traffic. malwarebytes.com/blog/news/2025… #infosec #BrowserSecurity #SupplyChain
Browser Hygiene 101: Do not mix business with pleasure. 🛑 Create a dedicated Chrome/Brave profile specifically for "Finance." No fun extensions, no random browsing. Limit the blast radius. #OpSec #BrowserSecurity #Web3
Kampanye ShadyPanda mengungkap celah besar di sistem review ekstensi Chrome & Edge. Ekstensi yang awalnya aman bisa berubah jadi spyware lewat update kecil yang tak diawasi. Baca selengkapnya: androidponsel.com/kenapa-ekstens… #CyberSecurity #BrowserSecurity #Chrome #Edge

🌐🧩 ShadyPanda extensions infect 4.3m browsers The “shadypanda” campaign used Chrome & Edge extensions that morphed into malware, reaching over 4.3m installs. Time to review your extensions. #browsersecurity #malware #chrome #edge

🔐 Security Guide | Preventing Asset Theft from Malicious Browser Extensions Browser extensions are crucial gateways to Web3, but can also become backdoors for asset loss. #BrowserSecurity #WalletExtensions #TransactionSecurity
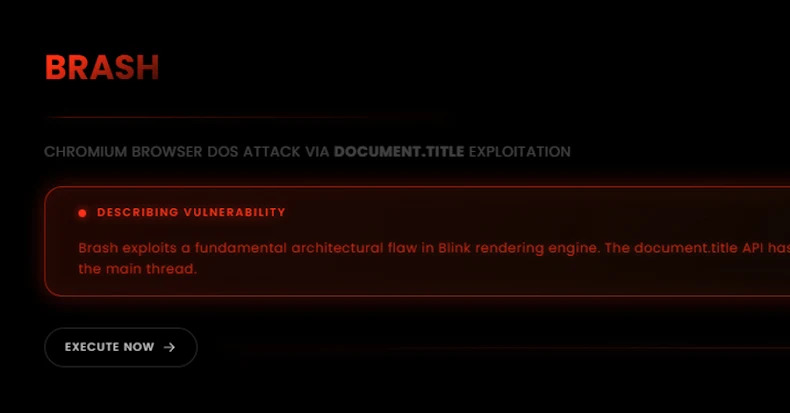
New "Brash" Exploit Crashes Chromium Browsers Instantly with a Single Malicious URL dlvr.it/TPX7tK #CyberSecurity #Chromium #BrowserSecurity #Vulnerability #Malware
Has anyone used any of these AI browsers on a permanent basis? Curious about real-world experiences with ChatGPT Atlas or Comet #AIBrowser #BrowserSecurity #chatgpt #comet

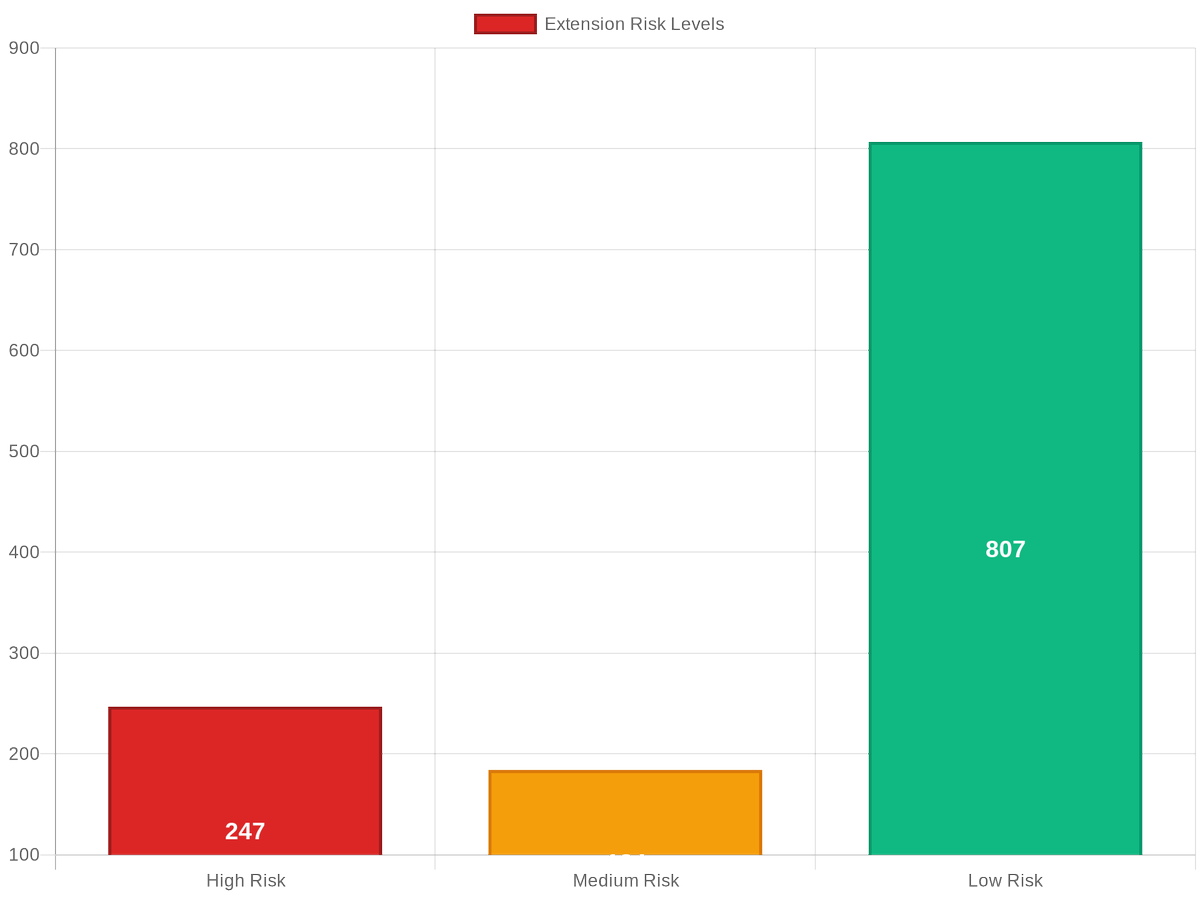
🚨 BREAKING: 62% of Chrome extensions request permissions they never use! Our analysis of 1238 extensions found: • 247 can access all your data • 248 modify security headers • 124 are abandoned See which... #BrowserSecurity #ExtensionRisk #CyberSecurity
The browser is the foundation of modern work, but it’s also a security blind spot. Attacks exploit legitimate features. We must place the browser at the center of security architecture to simplify defense. #Cybersecurity #BrowserSecurity
Understanding WebRTC Leaks: Hidden Privacy Vulnerability Explained bit.ly/42F7s9Y #WebRTCLeak #BrowserSecurity #PrivacyVulnerability #VPNLeaks #OnlineSecurity #TechEducation #SecurityFlaws #PrivacyProtection

Are your browser extensions putting your online security at risk? Discover the potential dangers and how to safeguard your digital life in our latest article. onwardcs.com/news/online-se… #Cybersecurity #OnlineSafety #BrowserSecurity
A critical memory flaw in Firefox’s WebAssembly GC (CVE-2025-13016) exposed 180M users to arbitrary code execution via malicious modules. Highlights need for AI-driven security and patch management. #WebAssemblyBug #BrowserSecurity #USA ift.tt/3MKY6zh
Browser extensions can be misused as backdoors or privilege escalation tools. Learn why and how to stay safe. redsecuretech.co.uk/blog/post/brow… #CyberSecurity #BrowserSecurity #Extensions #Malware #InfoSec #ThreatIntel

Browsers are now the frontline of enterprise risk, says @LayerxSecurity's Or Eshed in this commentary. Shadow #AI, risky extensions, and hidden data flows demand a real strategy. #BrowserSecurity #cybersecurity #infosec #CISO #ITsecurity bit.ly/4pkxKqO
Your biggest SaaS risk might be sitting inside your browser. 🧩 Even one unvetted extension can steal data or bypass security. Here’s how to spot and remove them before they cause damage 👇 🔗 bit.ly/3JtJ0C9 #CyberSecurity #DataProtection #BrowserSecurity #SpinAI

Corrupting the data an AI system learns from so it behaves incorrectly or makes unsafe decisions. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Kampanye ShadyPanda mengungkap celah besar di sistem review ekstensi Chrome & Edge. Ekstensi yang awalnya aman bisa berubah jadi spyware lewat update kecil yang tak diawasi. Baca selengkapnya: androidponsel.com/kenapa-ekstens… #CyberSecurity #BrowserSecurity #Chrome #Edge

Browser add-ons designed to steal data, track activity, or inject harmful code through websites. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Join experts from Google and Promevo on November 19 at 1 PM EST for an exclusive InformationWeek webinar exploring how Chrome Enterprise Premium transforms your browser into a secure, zero-trust perimeter. hubs.ly/Q03PNXr20 #ChromeEnterprise #ZeroTrust #BrowserSecurity

A tracking method that identifies you using unique browser and device traits, even without cookies. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

The collection of data you leave online through searches, clicks, and activity, which can reveal personal information. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

A set of tools and practices that protect your browser from malware, phishing, and data leaks. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Attackers manipulate an AI system by feeding it crafted prompts that override its original instructions. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

🎓 Students love browser extensions. Hackers do too. Our VP of Engineering Sergiy Balynsky explains how unmonitored add-ons expose K-12 data to massive risk, and what to do about it. 📖 Read the blog: → bit.ly/4hTjWkO #CyberSecurity #K12Security #BrowserSecurity

Surprised? Some Chrome themes carry malware that tracks your activity and injects ads. Always check developer reviews. Even aesthetic add-ons can be risky. #BrowserSecurity #DOITCQuiz

Some extensions secretly track your activity or steal data. Regularly review and remove what you don’t use. #BrowserSecurity #DataProtection #DOITC

Engaging conference session on browser security, featuring insightful insights and practical demonstrations. Grateful for the opportunity to learn from experts in the field. @imnarendrabhati @bsidesodisha #Cybersecurity #BrowserSecurity #InfoSec"

A security method where websites load in a remote, contained environment so harmful content never reaches your device. #cybersecurity #browsersecurity #onlinesafety #ai #infosec #SquareX

Your browser is your gateway to the online landscape, it must be protected ! Follow these tips to make your browsing experience safe and secure. #DoITC #BrowserSecurity #BeCyberAware #tipsandtricks

As part of our research on the architectural vulnerabilites of AI browsers, we reached out to CISOs to get their perspective, Tom Le, CISO at Gap shares his. Read our full research: hubs.la/Q03NswMT0 #cybersecurity #browsersecurity #enterprisesecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Thursday 21.7K posts
- 2. rUSD N/A
- 3. #DMDCHARITY2025 1.12M posts
- 4. Halle Berry 3,382 posts
- 5. Earl Campbell 2,127 posts
- 6. Diddy 74.7K posts
- 7. #TheChallenge41 2,239 posts
- 8. #LifeAITestnet 6,758 posts
- 9. #TusksUp N/A
- 10. Market Focus 4,787 posts
- 11. Free Tina 14.8K posts
- 12. Steve Cropper 7,242 posts
- 13. #Survivor49 2,951 posts
- 14. Milo 12.7K posts
- 15. seokjin 163K posts
- 16. Jamal Murray 7,900 posts
- 17. Mike Lindell 24K posts
- 18. Metroid Prime 4 13.9K posts
- 19. Ryan Nembhard 3,928 posts
- 20. fnaf 2 16.7K posts





































