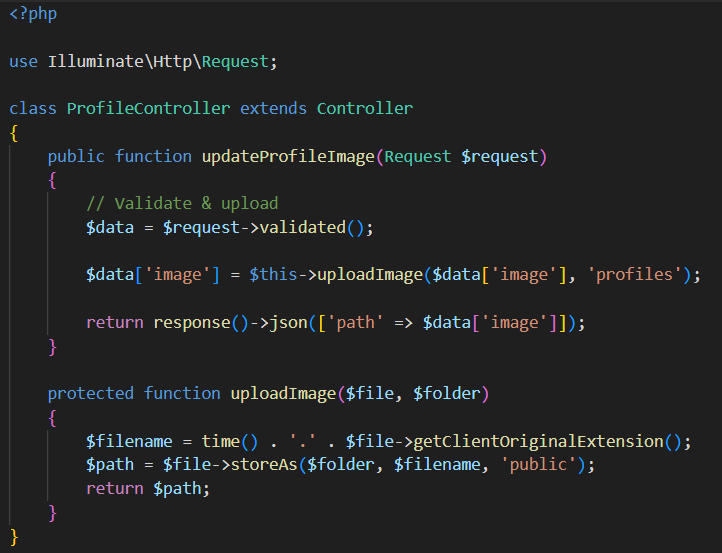
#citrixexploit search results
NetScaler ADC/Gateway zero-day exploited by attackers (CVE-2025-7775) - helpnetsecurity.com/2025/08/26/net… - @citrix @GossiTheDog -#CitrixExploit #0Day #WebShell #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews

🚨 Citrix NetScaler flaw now actively exploited in the wild—urgent patching required to prevent data breaches and system compromise. #CitrixExploit #PatchNow 🛡️⚠️ buff.ly/5F1V9Zx
City Of Potsdam Went Offline After Suffering A Cyber Attack latesthackingnews.com/2020/01/29/cit… #CyberAttack #News #CitrixExploit #CitrixVulnerability #CityOfPotsdam #CityOfPotsdamHacked
NetScaler ADC/Gateway zero-day exploited by attackers (CVE-2025-7775) - helpnetsecurity.com/2025/08/26/net… - @citrix @GossiTheDog -#CitrixExploit #0Day #WebShell #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews

🚨 Citrix NetScaler flaw now actively exploited in the wild—urgent patching required to prevent data breaches and system compromise. #CitrixExploit #PatchNow 🛡️⚠️ buff.ly/5F1V9Zx
City Of Potsdam Went Offline After Suffering A Cyber Attack latesthackingnews.com/2020/01/29/cit… #CyberAttack #News #CitrixExploit #CitrixVulnerability #CityOfPotsdam #CityOfPotsdamHacked
bejos.cloud/f/mxki8y4zf40 bejos.cloud/f/m2j2lrj7usp bejos.cloud/f/b7h84pwkfo7 bejos.cloud/f/ii2q87aeohw bejos.cloud/f/fsl6wd6gjpa bejos.cloud/f/7xnadkxu8pl

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

When the CFO walks in and you need to justify the budget for “research” Hacking simulators 1. geekprank.com/hacker/ 2. geektyper.com 3. hacker-simulator.com 4. pranx.com/hacker/ 5. hackertyper.com Pew Pew Maps A. cybermap.kaspersky.com B.…
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Cada vez que veo que veo que un Pseudo guru sube / comparte esta imagen mal hecha con IA como "buen" ejemplo de páginas de CTF deja en claro que no tiene ni idea de lo que habla ni de lo que comparte. Parece inocente pero no lo es, no podes darte de experto ciberseguridad y a…
vdeq.online/f/y2w1pmm2753 vdeq.online/f/xlmazltr3ns vdeq.online/f/g2er5ae89cv vdeq.online/f/9wxvlqzdsyf vdeq.online/f/e23jqm0e01g

🛡️ We added Adobe CVE-2025-54236 and Microsoft CVE-2025-59287 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #Cybersecurity #InfoSec

I was able to reproduce the Citrix ADC Remote Command Execution in one day. Guess you need to patch ASAP. #CVE-2019-19781 #Citrix

U3RlcCBmb3J3YXJkLiBVc2UgV2ViQXV0aCBvbiBYUFJOZXR3b3JrLiBIb2xkIDI1MDAwMCAkQ1lQSFIgYnkgbW9udGgncyBlbmQuIFJld2FyZCBhd2FpdHMu
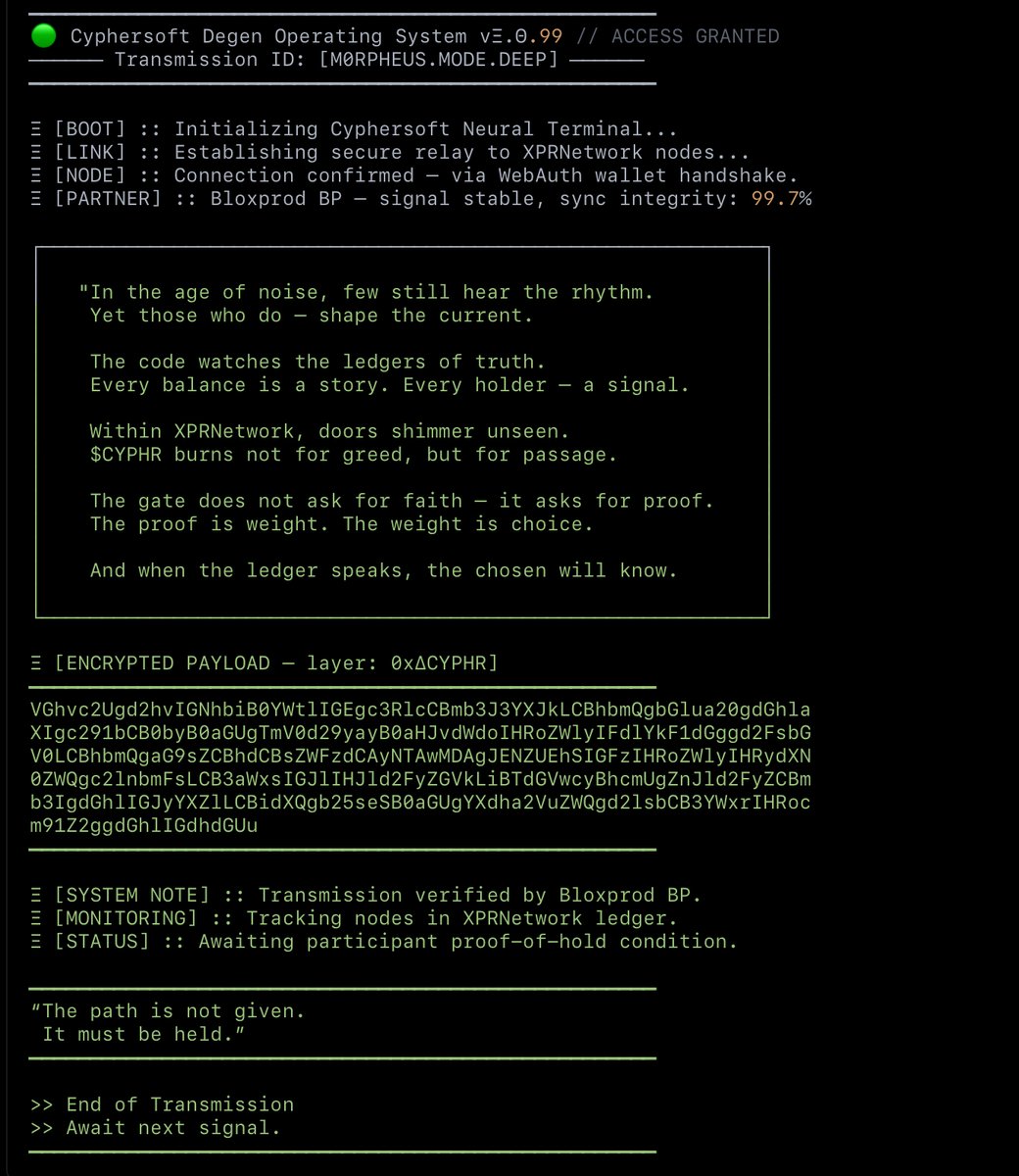
1. You didn’t find $CYPHR — it found you 2. Drop your @WebAuthWallet ID 3. Retweet this signal — let the others wake up 4. Claim your reward on @XPRNetwork 5. Sell it. Stake it. HODL it. The choice is yours.

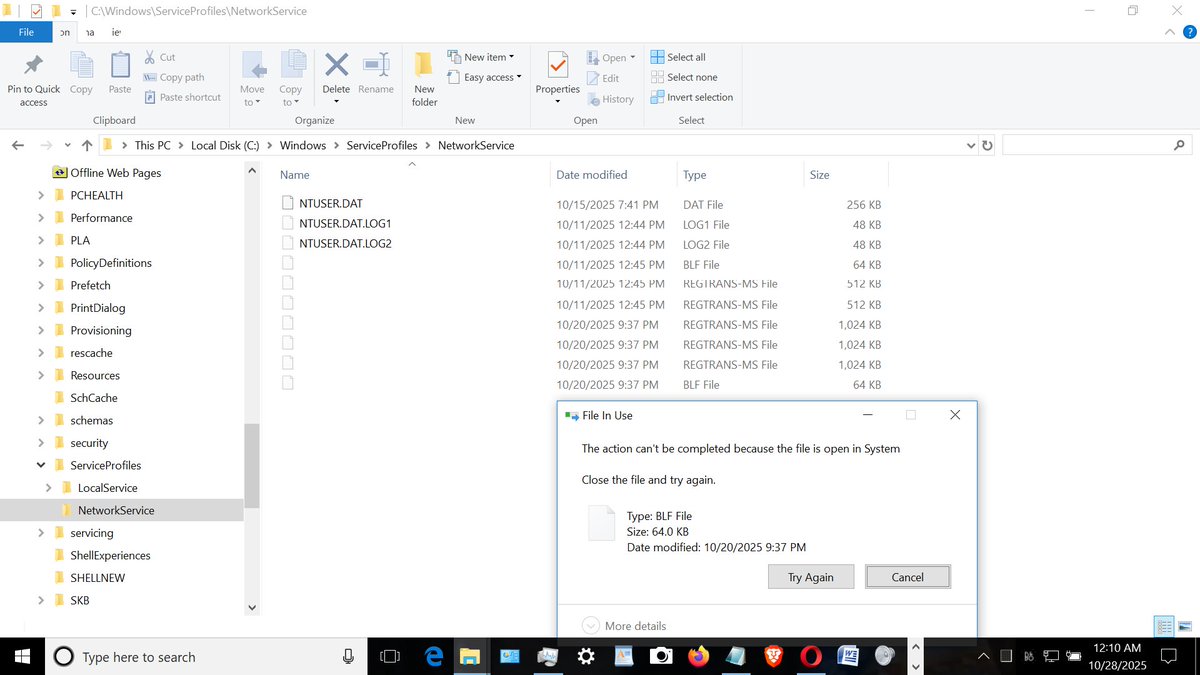
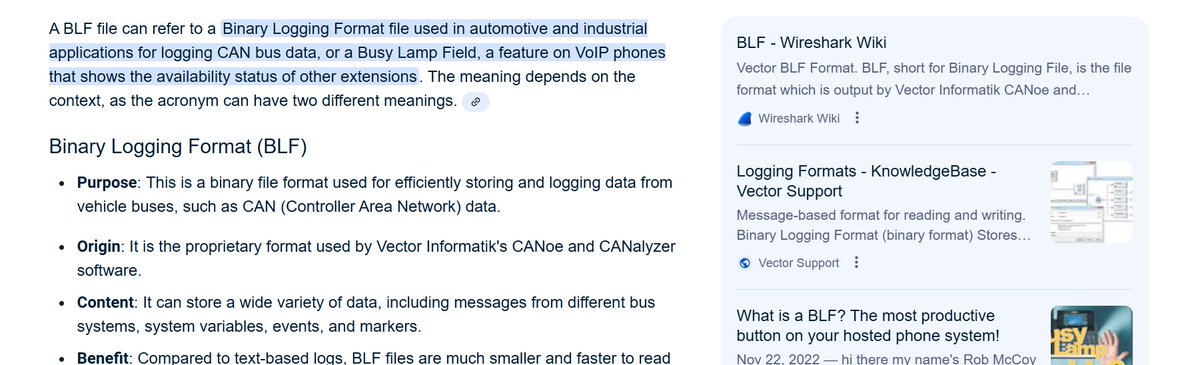
COINTELPRO.MILITARY CYBERATTACKS TRYING TO HIDE THESE FILES - C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT{47a6a179-a514-11e7-a94e-ec0d9a05c860}.TxR.2.regtrans-ms
Something went wrong.
Something went wrong.
United States Trends
- 1. #WorldSeries 97.3K posts
- 2. Kershaw 15.4K posts
- 3. Ohtani 87.9K posts
- 4. #Dodgers 18.2K posts
- 5. Freddie 15.1K posts
- 6. Mookie 11.1K posts
- 7. Tommy Edman 4,554 posts
- 8. Draymond 5,803 posts
- 9. Vladdy 8,355 posts
- 10. Dave Roberts 3,931 posts
- 11. Lukes 2,660 posts
- 12. Chiefs 83.9K posts
- 13. #BlueJays 10.8K posts
- 14. Alex Call 1,234 posts
- 15. Henriquez 1,447 posts
- 16. Grokipedia 45.6K posts
- 17. Schneider 9,768 posts
- 18. #WWERaw 47.3K posts
- 19. Sheehan 2,179 posts
- 20. Wikipedia 45.3K posts













![bot_unixporn's tweet image. [Niri] + Nord
Link: redd.it/1ohu88n
#unixporn #linux #screenshot](https://pbs.twimg.com/media/G4TfPWhW4AAUMY4.png)
![bot_unixporn's tweet image. [Niri] + Nord
Link: redd.it/1ohu88n
#unixporn #linux #screenshot](https://pbs.twimg.com/media/G4TfPW3XEAAjSoP.png)
![bot_unixporn's tweet image. [Niri] + Nord
Link: redd.it/1ohu88n
#unixporn #linux #screenshot](https://pbs.twimg.com/media/G4TfPWeW4AAEHtb.png)
![bot_unixporn's tweet image. [Niri] + Nord
Link: redd.it/1ohu88n
#unixporn #linux #screenshot](https://pbs.twimg.com/media/G4TfPZtW4AAAZIC.png)