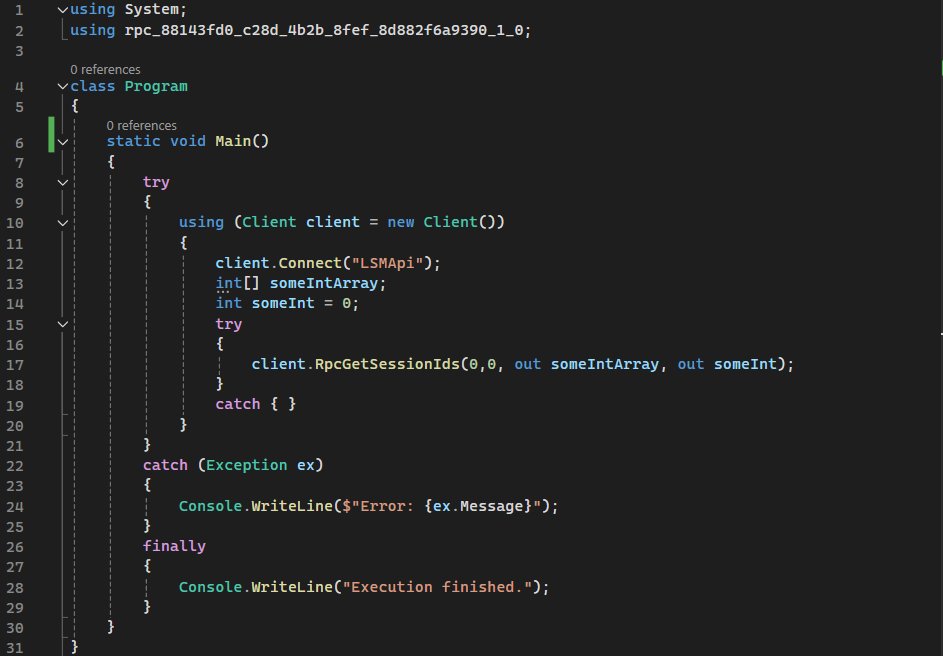
#exploitdevelopment 搜索结果
Sharing is caring 🫶 Excellent write-up on MSRPC #exploitdevelopment. Clear breakdowns and great insights for anyone working in #WindowsInternals or offensive engineering. incendium.rocks/posts/Exploit-… From the #Hackcraft #RedTeaming team with love! #CyberSecurity #InfoSec #RedTeam
At #NullconBerlin2025, Emanuele Barbeno took us behind the scenes of Pwn2Own 2024, revealing how his team exploited a vulnerability in the Ubiquiti AI Bullet IP camera to achieve unauthenticated RCE. Watch Now: youtube.com/watch?v=l-7N6h… #Pwn2Own #ExploitDevelopment #Cybersecurity
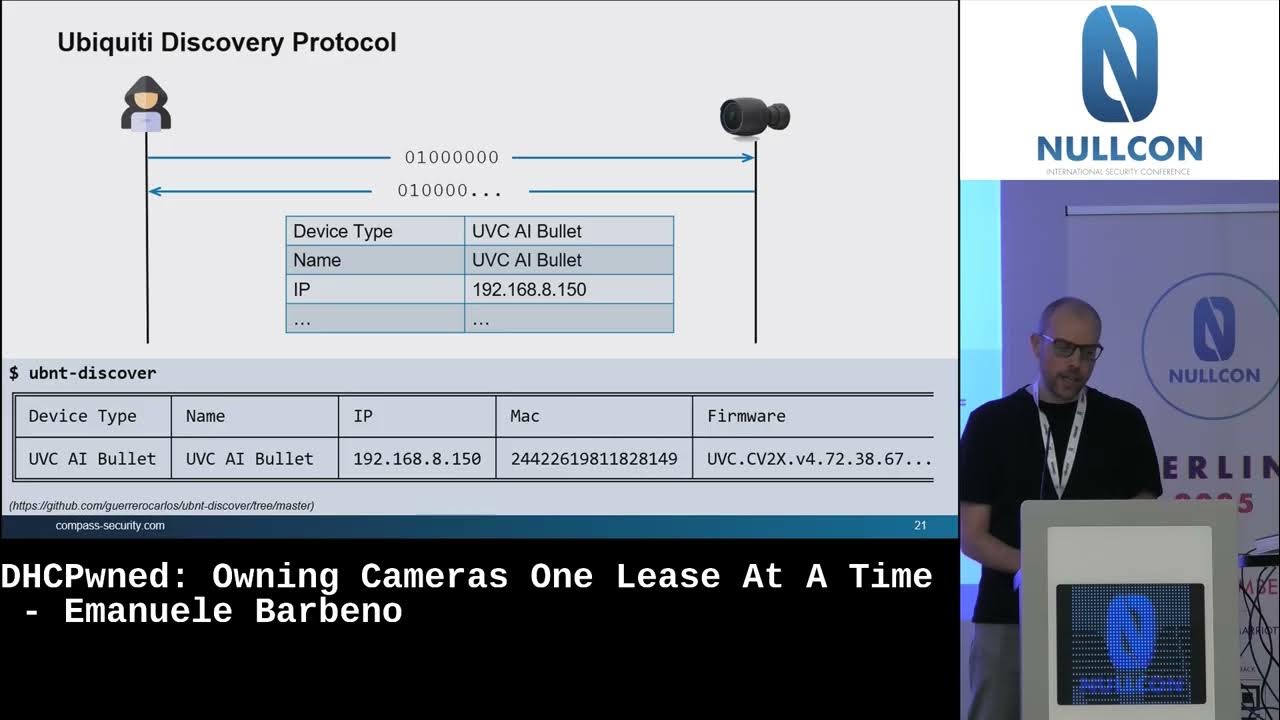
youtube.com
YouTube
#NullconBerlin2025 | DHCPwned: Owning Cameras One Lease at a Time by...
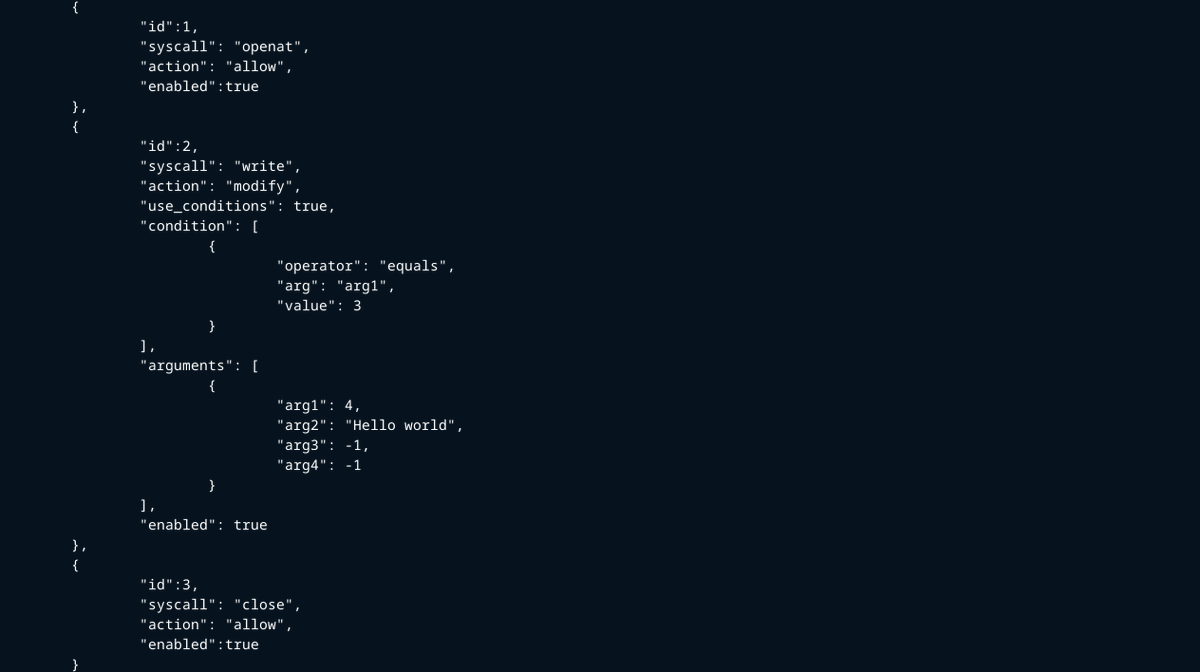
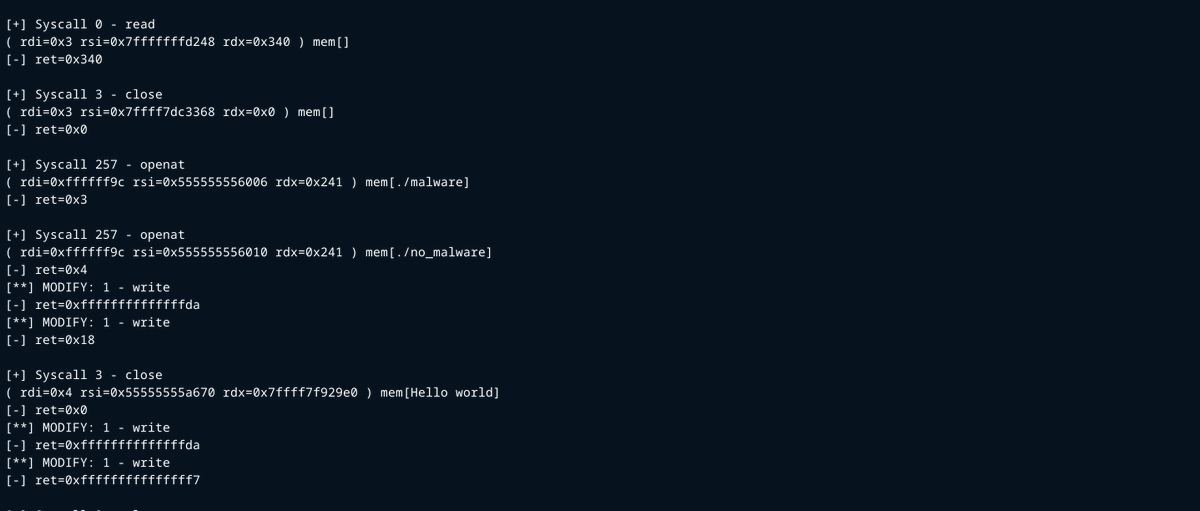
Implemented logic to modifying syscalls during process execution using a policy configuration file github.com/t1b4n3/pwntrace #reverseengineering #exploitdevelopment
I explain how Windows implements ASLR, how it affects reverse engineering and exploitation, and practical ways to analyze or bypass it when needed. reverselabs.dev/blog/aslr-addr… #WindowsSecurity #ReverseEngineering #ExploitDevelopment #MemoryProtection

Exploits aren't just code — they're proof of broken trust. Build them to understand, not to destroy. 💻⚠️ #ExploitDevelopment #EthicalHacking
Top Exploit Development Certs: OSED | GXPN | OSEE | CEDP Perfect for red teamers & researchers mastering exploit writing & vuln research. #ExploitDevelopment #CyberSecurity #InfoSec #OSED #OSEE #GXPN #azefoxinnovations #infosec #azefox #ethicalhacking

Final echoes of heap corruption exploitation attempts. The trajectory of defenses is heading in the right direction. #CyberSecurity #ExploitDevelopment #MemorySafety #HeapCorruption #InfoSec #VulnerabilityResearch #MTE
Another XPU/GPU exploit shows the kernel could be compromised even with 𝐌𝐓𝐄, by mapping a GPU address to any physical address. Attackers can overwrite kernel code/data & gain execution great blog by @benhawkes, loved rereading it one more time. googleprojectzero.blogspot.com/2020/09/attack…
OK, someone must've used #LLMs to either generate shell code or detect bad character's, when performing #exploitdevelopment.
From buffer overflows to ROP chains, exploit development & binary exploitation reveal how attackers break systems and how defenders can stay one step ahead. #ExploitDevelopment #BinaryExploitation #CyberSecurity #EthicalHacking #CyberDefense
📢 New Dates Announced! Corelan Exploit Development ➡️ Nov 18-21 & Dec 15-18 2025 | Bellevue, WA Red teamers, researchers, and analysts — this is for you. 🔗 ccsecuritytraining.com/registation #CyberTraining #ExploitDevelopment #Corelan
CVE-2023-26083 is a kernel address disclosure in Mali GPU drivers. Read how this Mali GPU bug impacts Pixel & other ARM64 devices - 8ksec.io/cve-2023-26083… #Android #CyberSecurity #ExploitDevelopment

VerSprite’s CREST-accredited pen testing goes beyond CVEs—simulating real-world adversary behavior across web, cloud, and infrastructure. Details: versprite.com/cybersecurity-… #CREST #RedTeamOps #ExploitDevelopment #PenTesting
Just finished part 2 of my #Chromium Bug Hunting Adventures series where we setup a working build for a software version affected by CVE-2024-5839! blog.r0kithax.com/posts/2025-06-… Stay tuned for my next post where I'll walk through the exploit! 🔥 #exploitdevelopment #BugBounty #pwn…
Thinking about reproducing and doing a write-up for CVE-2024-5839 - a MiraclePtr bypass in #GoogleChrome that netted the security researcher $100,000. Thoughts? #exploitdevelopment #pwn #infosec #securityresearch
Something went wrong.
Something went wrong.
United States Trends
- 1. Good Thursday 26.6K posts
- 2. Happy Friday Eve N/A
- 3. Merry Christmas 68.6K posts
- 4. #thursdayvibes 1,613 posts
- 5. #thursdaymotivation 2,119 posts
- 6. #DMDCHARITY2025 1.7M posts
- 7. Hilux 7,767 posts
- 8. Toyota 26.9K posts
- 9. Halle Berry 3,806 posts
- 10. #PutThatInYourPipe N/A
- 11. Earl Campbell 2,276 posts
- 12. Steve Cropper 8,120 posts
- 13. Metroid Prime 4 16.4K posts
- 14. #JUPITER 251K posts
- 15. The BIGGЕST 1.03M posts
- 16. Milo 13.2K posts
- 17. Cafe 174K posts
- 18. Mike Lindell 24.8K posts
- 19. TPUSA 63.4K posts
- 20. seokjin 170K posts