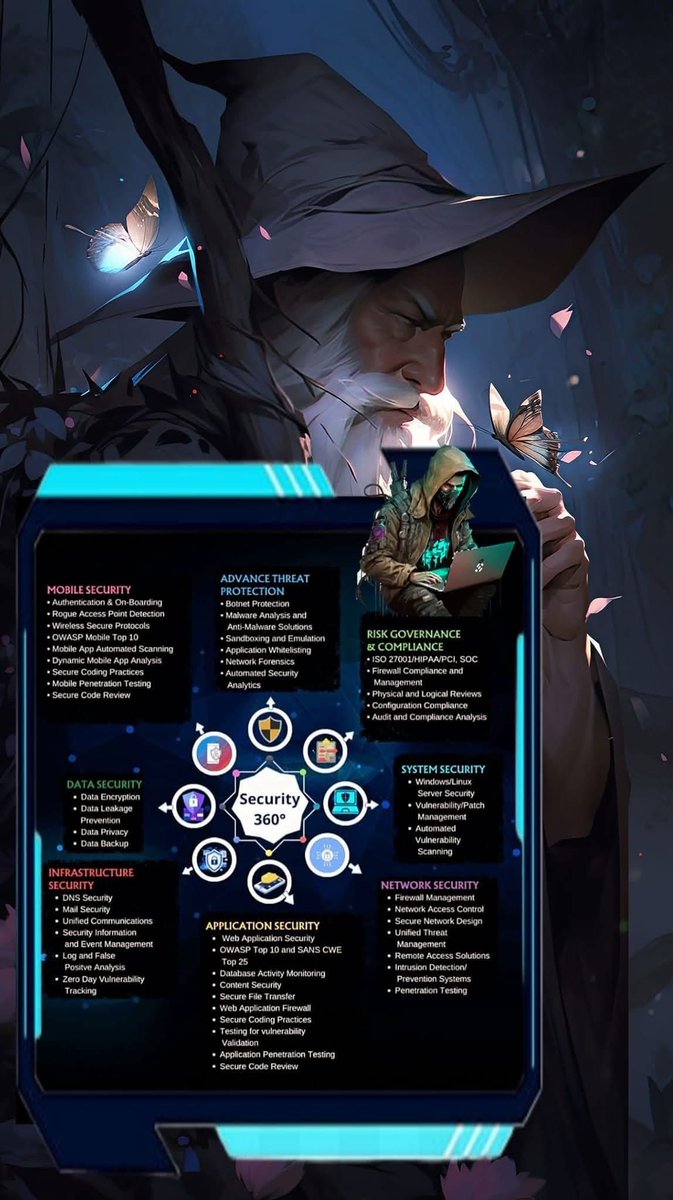
#filesystemsecurity 搜尋結果
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity
vdaey.de/e/eUuky51c vdaey.de/e/VmTY6G3c vdaey.de/a/rOLtoW8d vdaey.de/e/bap473CB vdaey.de/e/A6ee8bgk vdaey.de/e/QsFcRING vdaey.de/e/ydkmXcB7
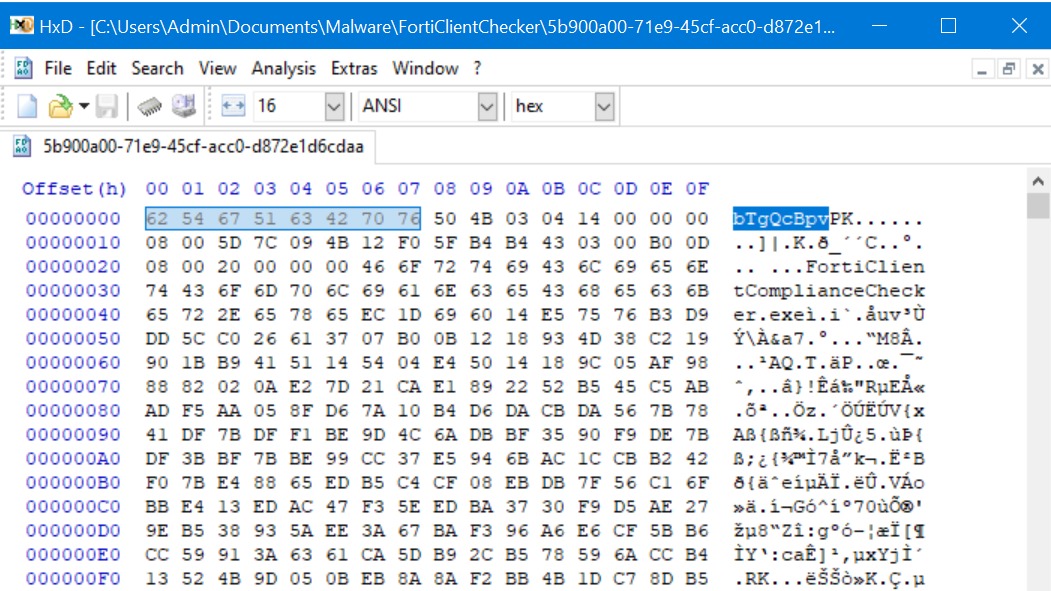
Cache smuggling: When a picture isn’t a thousand words: expel.com/blog/cache-smu… #cybersecurity #cyberattack #informationsecurity #hacking #infosec
⚠️ Critical: File upload vulnerability — Content-Disposition: filename is processed without validation, allowing RCE. #BugBounty #RCE #WebSecurity

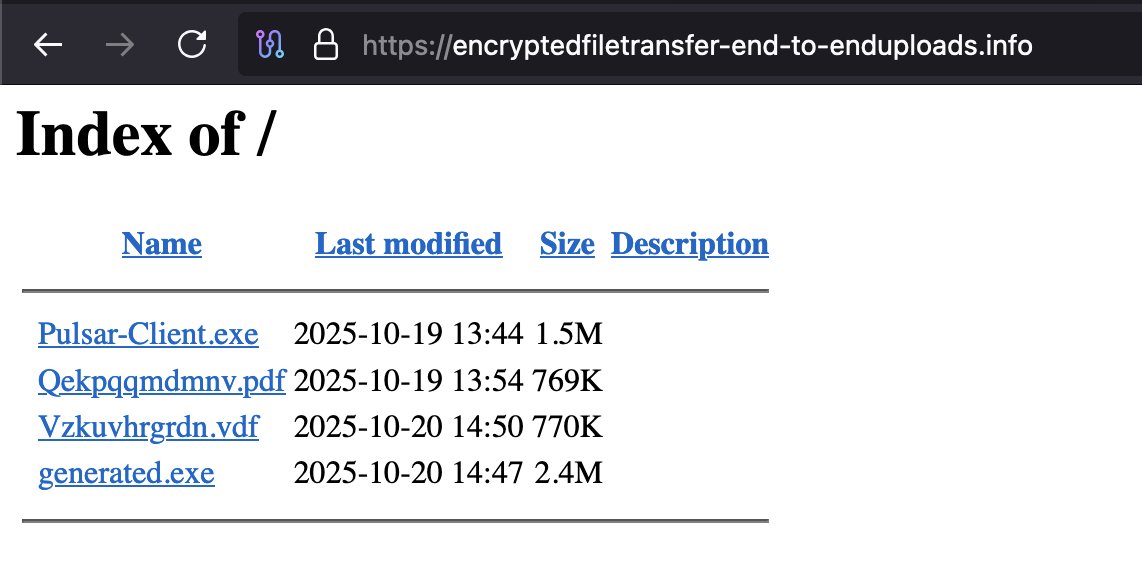
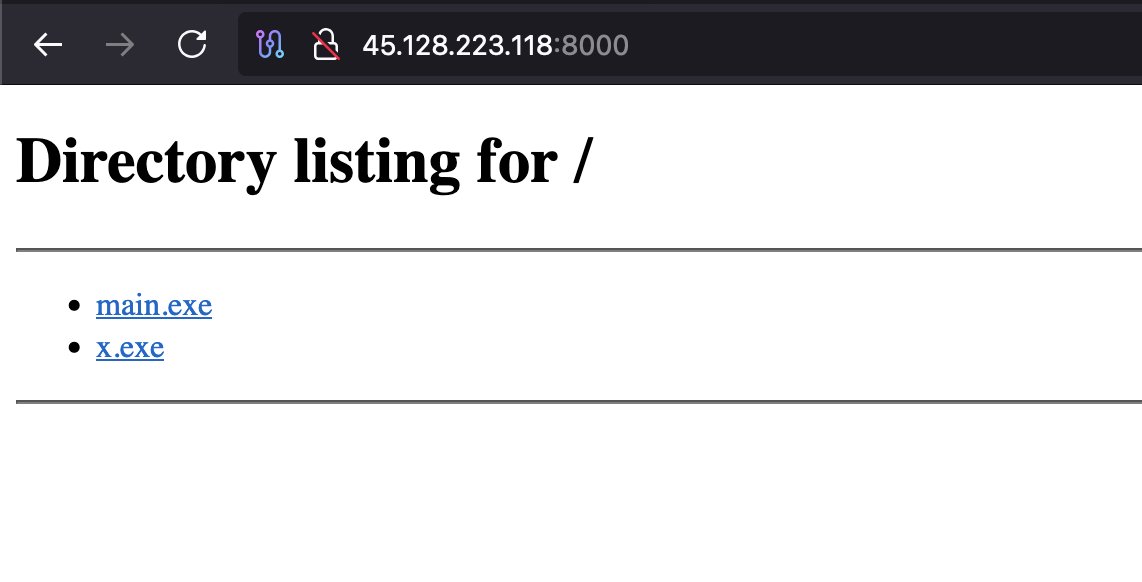
When threat actors forget to lock the door… and leave their malware stash wide open 🚪💀 🔥Found two lovely #Opendir today full of #Malware: 1⃣hxxps://encryptedfiletransfer-end-to-enduploads.info/ 2⃣htxxp://45.128.223.118:8000/ Don't be shy and analyze them 😉
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

[PTU1-X327-1 || BREACH DETECTED] Archive integrity compromised. File: Origin Operation █████. Intrusion signature: psu1sk.exe(init(destroy(f,i))). Backup image/replica purged. Original file content:
![xeonitepic's tweet image. [PTU1-X327-1 || BREACH DETECTED]
Archive integrity compromised. File: Origin Operation █████. Intrusion signature: psu1sk.exe(init(destroy(f,i))). Backup image/replica purged.
Original file content:](https://pbs.twimg.com/media/G322-y3WUAAJHam.png)
📑 Discover InstaSafe Zero Trust Access 🔐 Check out our datasheet to explore key features & benefits that strengthen security, streamline access & protect your network. Download now 👉 zurl.co/DDlG #ZeroTrust #CyberSecurity #InstaSafe #KeyFeatures

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Unlimited access to Docker Hardened Images: Because security should be affordable, always dlvr.it/TNnYPB #docker

The accuracy of any AI model depends on the quality of its data. Filecoin provides transparent, tamper-proof storage that allows anyone to verify where datasets originate and how they are preserved over time.

fidoyys.fit/e/61qrpcyvooy3 vdeyni.fun/e/DBWPIf fidoyys.fit/e/l885yv9kuq32 fidoyys.fit/e/hdf7e9dhk3bk fidoyys.fit/e/g9h3mit1fwxe fidoyys.fit/e/doknoe61gqvl fidoyys.fit/e/xs96gr8muz1v fidoyys.fit/e/xy3ac3skobfx

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Luka 72.6K posts
- 2. Lakers 95.3K posts
- 3. Good Wednesday 16.2K posts
- 4. Froot N/A
- 5. Ayton 15.8K posts
- 6. Pharos 9,878 posts
- 7. Marcus Smart 8,873 posts
- 8. #MLBS6Spoilers 8,526 posts
- 9. Talus Labs 15.8K posts
- 10. Warriors 97.2K posts
- 11. #DWTS 49.8K posts
- 12. #DubNation 13.6K posts
- 13. Steph 34.6K posts
- 14. Reaves 9,411 posts
- 15. Draymond 8,872 posts
- 16. Shai 34.5K posts
- 17. Jimmy Butler 10.1K posts
- 18. LeBron 36.8K posts
- 19. Double OT 6,993 posts
- 20. #TusksUp 1,154 posts